Lecture Notes on the Lambda Calculus
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Lecture Notes on the Lambda Calculus 2.4 Introduction to Β-Reduction
2.2 Free and bound variables, α-equivalence. 8 2.3 Substitution ............................. 10 Lecture Notes on the Lambda Calculus 2.4 Introduction to β-reduction..................... 12 2.5 Formal definitions of β-reduction and β-equivalence . 13 Peter Selinger 3 Programming in the untyped lambda calculus 14 3.1 Booleans .............................. 14 Department of Mathematics and Statistics 3.2 Naturalnumbers........................... 15 Dalhousie University, Halifax, Canada 3.3 Fixedpointsandrecursivefunctions . 17 3.4 Other data types: pairs, tuples, lists, trees, etc. ....... 20 Abstract This is a set of lecture notes that developed out of courses on the lambda 4 The Church-Rosser Theorem 22 calculus that I taught at the University of Ottawa in 2001 and at Dalhousie 4.1 Extensionality, η-equivalence, and η-reduction. 22 University in 2007 and 2013. Topics covered in these notes include the un- typed lambda calculus, the Church-Rosser theorem, combinatory algebras, 4.2 Statement of the Church-Rosser Theorem, and some consequences 23 the simply-typed lambda calculus, the Curry-Howard isomorphism, weak 4.3 Preliminary remarks on the proof of the Church-Rosser Theorem . 25 and strong normalization, polymorphism, type inference, denotational se- mantics, complete partial orders, and the language PCF. 4.4 ProofoftheChurch-RosserTheorem. 27 4.5 Exercises .............................. 32 Contents 5 Combinatory algebras 34 5.1 Applicativestructures. 34 1 Introduction 1 5.2 Combinatorycompleteness . 35 1.1 Extensionalvs. intensionalviewoffunctions . ... 1 5.3 Combinatoryalgebras. 37 1.2 Thelambdacalculus ........................ 2 5.4 The failure of soundnessforcombinatoryalgebras . .... 38 1.3 Untypedvs.typedlambda-calculi . 3 5.5 Lambdaalgebras .......................... 40 1.4 Lambdacalculusandcomputability . 4 5.6 Extensionalcombinatoryalgebras . 44 1.5 Connectionstocomputerscience . -

Functional Languages
Functional Programming Languages (FPL) 1. Definitions................................................................... 2 2. Applications ................................................................ 2 3. Examples..................................................................... 3 4. FPL Characteristics:.................................................... 3 5. Lambda calculus (LC)................................................. 4 6. Functions in FPLs ....................................................... 7 7. Modern functional languages...................................... 9 8. Scheme overview...................................................... 11 8.1. Get your own Scheme from MIT...................... 11 8.2. General overview.............................................. 11 8.3. Data Typing ...................................................... 12 8.4. Comments ......................................................... 12 8.5. Recursion Instead of Iteration........................... 13 8.6. Evaluation ......................................................... 14 8.7. Storing and using Scheme code ........................ 14 8.8. Variables ........................................................... 15 8.9. Data types.......................................................... 16 8.10. Arithmetic functions ......................................... 17 8.11. Selection functions............................................ 18 8.12. Iteration............................................................. 23 8.13. Defining functions ........................................... -

Category Theory and Lambda Calculus
Category Theory and Lambda Calculus Mario Román García Trabajo Fin de Grado Doble Grado en Ingeniería Informática y Matemáticas Tutores Pedro A. García-Sánchez Manuel Bullejos Lorenzo Facultad de Ciencias E.T.S. Ingenierías Informática y de Telecomunicación Granada, a 18 de junio de 2018 Contents 1 Lambda calculus 13 1.1 Untyped λ-calculus . 13 1.1.1 Untyped λ-calculus . 14 1.1.2 Free and bound variables, substitution . 14 1.1.3 Alpha equivalence . 16 1.1.4 Beta reduction . 16 1.1.5 Eta reduction . 17 1.1.6 Confluence . 17 1.1.7 The Church-Rosser theorem . 18 1.1.8 Normalization . 20 1.1.9 Standardization and evaluation strategies . 21 1.1.10 SKI combinators . 22 1.1.11 Turing completeness . 24 1.2 Simply typed λ-calculus . 24 1.2.1 Simple types . 25 1.2.2 Typing rules for simply typed λ-calculus . 25 1.2.3 Curry-style types . 26 1.2.4 Unification and type inference . 27 1.2.5 Subject reduction and normalization . 29 1.3 The Curry-Howard correspondence . 31 1.3.1 Extending the simply typed λ-calculus . 31 1.3.2 Natural deduction . 32 1.3.3 Propositions as types . 34 1.4 Other type systems . 35 1.4.1 λ-cube..................................... 35 2 Mikrokosmos 38 2.1 Implementation of λ-expressions . 38 2.1.1 The Haskell programming language . 38 2.1.2 De Bruijn indexes . 40 2.1.3 Substitution . 41 2.1.4 De Bruijn-terms and λ-terms . 42 2.1.5 Evaluation . -

(Pdf) of from Push/Enter to Eval/Apply by Program Transformation
From Push/Enter to Eval/Apply by Program Transformation MaciejPir´og JeremyGibbons Department of Computer Science University of Oxford [email protected] [email protected] Push/enter and eval/apply are two calling conventions used in implementations of functional lan- guages. In this paper, we explore the following observation: when considering functions with mul- tiple arguments, the stack under the push/enter and eval/apply conventions behaves similarly to two particular implementations of the list datatype: the regular cons-list and a form of lists with lazy concatenation respectively. Along the lines of Danvy et al.’s functional correspondence between def- initional interpreters and abstract machines, we use this observation to transform an abstract machine that implements push/enter into an abstract machine that implements eval/apply. We show that our method is flexible enough to transform the push/enter Spineless Tagless G-machine (which is the semantic core of the GHC Haskell compiler) into its eval/apply variant. 1 Introduction There are two standard calling conventions used to efficiently compile curried multi-argument functions in higher-order languages: push/enter (PE) and eval/apply (EA). With the PE convention, the caller pushes the arguments on the stack, and jumps to the function body. It is the responsibility of the function to find its arguments, when they are needed, on the stack. With the EA convention, the caller first evaluates the function to a normal form, from which it can read the number and kinds of arguments the function expects, and then it calls the function body with the right arguments. -

Plurals and Mereology
Journal of Philosophical Logic (2021) 50:415–445 https://doi.org/10.1007/s10992-020-09570-9 Plurals and Mereology Salvatore Florio1 · David Nicolas2 Received: 2 August 2019 / Accepted: 5 August 2020 / Published online: 26 October 2020 © The Author(s) 2020 Abstract In linguistics, the dominant approach to the semantics of plurals appeals to mere- ology. However, this approach has received strong criticisms from philosophical logicians who subscribe to an alternative framework based on plural logic. In the first part of the article, we offer a precise characterization of the mereological approach and the semantic background in which the debate can be meaningfully reconstructed. In the second part, we deal with the criticisms and assess their logical, linguistic, and philosophical significance. We identify four main objections and show how each can be addressed. Finally, we compare the strengths and shortcomings of the mereologi- cal approach and plural logic. Our conclusion is that the former remains a viable and well-motivated framework for the analysis of plurals. Keywords Mass nouns · Mereology · Model theory · Natural language semantics · Ontological commitment · Plural logic · Plurals · Russell’s paradox · Truth theory 1 Introduction A prominent tradition in linguistic semantics analyzes plurals by appealing to mere- ology (e.g. Link [40, 41], Landman [32, 34], Gillon [20], Moltmann [50], Krifka [30], Bale and Barner [2], Chierchia [12], Sutton and Filip [76], and Champollion [9]).1 1The historical roots of this tradition include Leonard and Goodman [38], Goodman and Quine [22], Massey [46], and Sharvy [74]. Salvatore Florio [email protected] David Nicolas [email protected] 1 Department of Philosophy, University of Birmingham, Birmingham, United Kingdom 2 Institut Jean Nicod, Departement´ d’etudes´ cognitives, ENS, EHESS, CNRS, PSL University, Paris, France 416 S. -

Computational Lambda-Calculus and Monads
Computational lambda-calculus and monads Eugenio Moggi∗ LFCS Dept. of Comp. Sci. University of Edinburgh EH9 3JZ Edinburgh, UK [email protected] October 1988 Abstract The λ-calculus is considered an useful mathematical tool in the study of programming languages, since programs can be identified with λ-terms. However, if one goes further and uses βη-conversion to prove equivalence of programs, then a gross simplification1 is introduced, that may jeopardise the applicability of theoretical results to real situations. In this paper we introduce a new calculus based on a categorical semantics for computations. This calculus provides a correct basis for proving equivalence of programs, independent from any specific computational model. 1 Introduction This paper is about logics for reasoning about programs, in particular for proving equivalence of programs. Following a consolidated tradition in theoretical computer science we identify programs with the closed λ-terms, possibly containing extra constants, corresponding to some features of the programming language under con- sideration. There are three approaches to proving equivalence of programs: • The operational approach starts from an operational semantics, e.g. a par- tial function mapping every program (i.e. closed term) to its resulting value (if any), which induces a congruence relation on open terms called operational equivalence (see e.g. [Plo75]). Then the problem is to prove that two terms are operationally equivalent. ∗On leave from Universit`a di Pisa. Research partially supported by the Joint Collaboration Contract # ST2J-0374-C(EDB) of the EEC 1programs are identified with total functions from values to values 1 • The denotational approach gives an interpretation of the (programming) lan- guage in a mathematical structure, the intended model. -

Continuation Calculus
Eindhoven University of Technology MASTER Continuation calculus Geron, B. Award date: 2013 Link to publication Disclaimer This document contains a student thesis (bachelor's or master's), as authored by a student at Eindhoven University of Technology. Student theses are made available in the TU/e repository upon obtaining the required degree. The grade received is not published on the document as presented in the repository. The required complexity or quality of research of student theses may vary by program, and the required minimum study period may vary in duration. General rights Copyright and moral rights for the publications made accessible in the public portal are retained by the authors and/or other copyright owners and it is a condition of accessing publications that users recognise and abide by the legal requirements associated with these rights. • Users may download and print one copy of any publication from the public portal for the purpose of private study or research. • You may not further distribute the material or use it for any profit-making activity or commercial gain Continuation calculus Master’s thesis Bram Geron Supervised by Herman Geuvers Assessment committee: Herman Geuvers, Hans Zantema, Alexander Serebrenik Final version Contents 1 Introduction 3 1.1 Foreword . 3 1.2 The virtues of continuation calculus . 4 1.2.1 Modeling programs . 4 1.2.2 Ease of implementation . 5 1.2.3 Simplicity . 5 1.3 Acknowledgements . 6 2 The calculus 7 2.1 Introduction . 7 2.2 Definition of continuation calculus . 9 2.3 Categorization of terms . 10 2.4 Reasoning with CC terms . -

Making a Faster Curry with Extensional Types
Making a Faster Curry with Extensional Types Paul Downen Simon Peyton Jones Zachary Sullivan Microsoft Research Zena M. Ariola Cambridge, UK University of Oregon [email protected] Eugene, Oregon, USA [email protected] [email protected] [email protected] Abstract 1 Introduction Curried functions apparently take one argument at a time, Consider these two function definitions: which is slow. So optimizing compilers for higher-order lan- guages invariably have some mechanism for working around f1 = λx: let z = h x x in λy:e y z currying by passing several arguments at once, as many as f = λx:λy: let z = h x x in e y z the function can handle, which is known as its arity. But 2 such mechanisms are often ad-hoc, and do not work at all in higher-order functions. We show how extensional, call- It is highly desirable for an optimizing compiler to η ex- by-name functions have the correct behavior for directly pand f1 into f2. The function f1 takes only a single argu- expressing the arity of curried functions. And these exten- ment before returning a heap-allocated function closure; sional functions can stand side-by-side with functions native then that closure must subsequently be called by passing the to practical programming languages, which do not use call- second argument. In contrast, f2 can take both arguments by-name evaluation. Integrating call-by-name with other at once, without constructing an intermediate closure, and evaluation strategies in the same intermediate language ex- this can make a huge difference to run-time performance in presses the arity of a function in its type and gives a princi- practice [Marlow and Peyton Jones 2004]. -
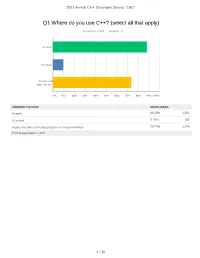
Q1 Where Do You Use C++? (Select All That Apply)
2021 Annual C++ Developer Survey "Lite" Q1 Where do you use C++? (select all that apply) Answered: 1,870 Skipped: 3 At work At school In personal time, for ho... 0% 10% 20% 30% 40% 50% 60% 70% 80% 90% 100% ANSWER CHOICES RESPONSES At work 88.29% 1,651 At school 9.79% 183 In personal time, for hobby projects or to try new things 73.74% 1,379 Total Respondents: 1,870 1 / 35 2021 Annual C++ Developer Survey "Lite" Q2 How many years of programming experience do you have in C++ specifically? Answered: 1,869 Skipped: 4 1-2 years 3-5 years 6-10 years 10-20 years >20 years 0% 10% 20% 30% 40% 50% 60% 70% 80% 90% 100% ANSWER CHOICES RESPONSES 1-2 years 7.60% 142 3-5 years 20.60% 385 6-10 years 20.71% 387 10-20 years 30.02% 561 >20 years 21.08% 394 TOTAL 1,869 2 / 35 2021 Annual C++ Developer Survey "Lite" Q3 How many years of programming experience do you have overall (all languages)? Answered: 1,865 Skipped: 8 1-2 years 3-5 years 6-10 years 10-20 years >20 years 0% 10% 20% 30% 40% 50% 60% 70% 80% 90% 100% ANSWER CHOICES RESPONSES 1-2 years 1.02% 19 3-5 years 12.17% 227 6-10 years 22.68% 423 10-20 years 29.71% 554 >20 years 34.42% 642 TOTAL 1,865 3 / 35 2021 Annual C++ Developer Survey "Lite" Q4 What types of projects do you work on? (select all that apply) Answered: 1,861 Skipped: 12 Gaming (e.g., console and.. -

Semantic Theory Week 4 – Lambda Calculus
Semantic Theory Week 4 – Lambda Calculus Noortje Venhuizen University of Groningen/Universität des Saarlandes Summer 2015 1 Compositionality The principle of compositionality: “The meaning of a complex expression is a function of the meanings of its parts and of the syntactic rules by which they are combined” (Partee et al.,1993) Compositional semantics construction: • compute meaning representations for sub-expressions • combine them to obtain a meaning representation for a complex expression. Problematic case: “Not smoking⟨e,t⟩ is healthy⟨⟨e,t⟩,t⟩” ! 2 Lambda abstraction λ-abstraction is an operation that takes an expression and “opens” specific argument positions. Syntactic definition: If α is in WEτ, and x is in VARσ then λx(α) is in WE⟨σ, τ⟩ • The scope of the λ-operator is the smallest WE to its right. Wider scope must be indicated by brackets. • We often use the “dot notation” λx.φ indicating that the λ-operator takes widest possible scope (over φ). 3 Interpretation of Lambda-expressions M,g If α ∈ WEτ and v ∈ VARσ, then ⟦λvα⟧ is that function f : Dσ → Dτ M,g[v/a] such that for all a ∈ Dσ, f(a) = ⟦α⟧ If the λ-expression is applied to some argument, we can simplify the interpretation: • ⟦λvα⟧M,g(A) = ⟦α⟧M,g[v/A] Example: “Bill is a non-smoker” ⟦λx(¬S(x))(b’)⟧M,g = 1 iff ⟦λx(¬S(x))⟧M,g(⟦b’⟧M,g) = 1 iff ⟦¬S(x)⟧M,g[x/⟦b’⟧M,g] = 1 iff ⟦S(x)⟧M,g[x/⟦b’⟧M,g] = 0 iff ⟦S⟧M,g[x/⟦b’⟧M,g](⟦x⟧M,g[x/⟦b’⟧M,g]) = 0 iff VM(S)(VM(b’)) = 0 4 β-Reduction ⟦λv(α)(β)⟧M,g = ⟦α⟧M,g[v/⟦β⟧M,g] ⇒ all (free) occurrences of the λ-variable in α get the interpretation of β as value. -

CSE 341 : Programming Languages
CSE 341 : Programming Languages Lecture 10 Closure Idioms Zach Tatlock Spring 2014 More idioms • We know the rule for lexical scope and function closures – Now what is it good for A partial but wide-ranging list: • Pass functions with private data to iterators: Done • Combine functions (e.g., composition) • Currying (multi-arg functions and partial application) • Callbacks (e.g., in reactive programming) • Implementing an ADT with a record of functions (optional) 2 Combine functions Canonical example is function composition: fun compose (f,g) = fn x => f (g x) • Creates a closure that “remembers” what f and g are bound to • Type ('b -> 'c) * ('a -> 'b) -> ('a -> 'c) but the REPL prints something equivalent • ML standard library provides this as infix operator o • Example (third version best): fun sqrt_of_abs i = Math.sqrt(Real.fromInt(abs i)) fun sqrt_of_abs i = (Math.sqrt o Real.fromInt o abs) i val sqrt_of_abs = Math.sqrt o Real.fromInt o abs 3 Left-to-right or right-to-left val sqrt_of_abs = Math.sqrt o Real.fromInt o abs As in math, function composition is “right to left” – “take absolute value, convert to real, and take square root” – “square root of the conversion to real of absolute value” “Pipelines” of functions are common in functional programming and many programmers prefer left-to-right – Can define our own infix operator – This one is very popular (and predefined) in F# infix |> fun x |> f = f x fun sqrt_of_abs i = i |> abs |> Real.fromInt |> Math.sqrt 4 Another example • “Backup function” fun backup1 (f,g) = fn x => case -

Labelled Λ-Calculi with Explicit Copy and Erase
Labelled λ-calculi with Explicit Copy and Erase Maribel Fern´andez, Nikolaos Siafakas King’s College London, Dept. Computer Science, Strand, London WC2R 2LS, UK [maribel.fernandez, nikolaos.siafakas]@kcl.ac.uk We present two rewriting systems that define labelled explicit substitution λ-calculi. Our work is motivated by the close correspondence between L´evy’s labelled λ-calculus and paths in proof-nets, which played an important role in the understanding of the Geometry of Interaction. The structure of the labels in L´evy’s labelled λ-calculus relates to the multiplicative information of paths; the novelty of our work is that we design labelled explicit substitution calculi that also keep track of exponential information present in call-by-value and call-by-name translations of the λ-calculus into linear logic proof-nets. 1 Introduction Labelled λ-calculi have been used for a variety of applications, for instance, as a technology to keep track of residuals of redexes [6], and in the context of optimal reduction, using L´evy’s labels [14]. In L´evy’s work, labels give information about the history of redex creation, which allows the identification and classification of copied β-redexes. A different point of view is proposed in [4], where it is shown that a label is actually encoding a path in the syntax tree of a λ-term. This established a tight correspondence between the labelled λ-calculus and the Geometry of Interaction interpretation of cut elimination in linear logic proof-nets [13]. Inspired by L´evy’s labelled λ-calculus, we define labelled λ-calculi where the labels attached to terms capture reduction traces.