The Report of the International Association for Identification, Standardization II Committee
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Risk Factors for Coliform Bacteria in Backcountry Lakes & Streams in the Sierra Nevada
Wilderness and Environmental Medicine, 19, 82 90 (2008) ORIGINAL RESEARCH Risk Factors for Coliform Bacteria in Backcountry Lakes and Streams in the Sierra Nevada Mountains: A 5-Year Study Robert W. Derlet, MD; K. Ali Ger; John R. Richards, MD; James R. Carlson, PhD From the Department of Emergency Medicine, University of California, Davis, School of Medicine, Sacramento, CA (Drs Derlet and Richards); The John Muir Institute of the Environment, University of California, Davis, Sacramento, CA (Dr Derlet); the Department of Environmental Sciences and Policy, University of California, Davis, Sacramento, CA (Mr Ger); and the Department of Public Health, Microbiology Section, San Mateo County, San Mateo, CA (Dr Carlson). Category 1 Continuing Medical Education credit for WMS member physicians is available for .to access the test questions 1922؍this article. Go to http://wms.org/cme/cme.asp?whatarticle Objective.—To provide a 5-year longitudinal assessment of risk of acquiring disease from Sierra Nevada Wilderness area lakes and streams. This study examines the relative risk factors for harmful water microorganisms, using coliforms as an indicator. Methods.—Streams and lakes in the backcountry of Yosemite and Kings Canyon National Parks and neighboring wilderness areas were selected and water was analyzed each year over a 5-year period. A total of 364 samples from lakes or streams were chosen to statistically differentiate the risk cate- gories based on land usage, as follows: 1) areas rarely visited by humans (Wild), 2) human day-use- only areas (Day Hike), 3) areas used by backpackers with overnight camping allowed (Backpack), 4) areas primarily impacted by horses or pack animals (Pack Animal), and 5) cattle and sheep grazing tracts (Cattle). -
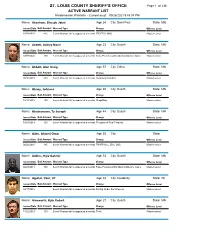
Misdemeanor Warrant List
SO ST. LOUIS COUNTY SHERIFF'S OFFICE Page 1 of 238 ACTIVE WARRANT LIST Misdemeanor Warrants - Current as of: 09/26/2021 9:45:03 PM Name: Abasham, Shueyb Jabal Age: 24 City: Saint Paul State: MN Issued Date Bail Amount Warrant Type Charge Offense Level 10/05/2020 415 Bench Warrant-fail to appear at a hearing TRAFFIC-9000 Misdemeanor Name: Abbett, Ashley Marie Age: 33 City: Duluth State: MN Issued Date Bail Amount Warrant Type Charge Offense Level 03/09/2020 100 Bench Warrant-fail to appear at a hearing False Pretenses/Swindle/Confidence Game Misdemeanor Name: Abbott, Alan Craig Age: 57 City: Edina State: MN Issued Date Bail Amount Warrant Type Charge Offense Level 09/16/2019 500 Bench Warrant-fail to appear at a hearing Disorderly Conduct Misdemeanor Name: Abney, Johnese Age: 65 City: Duluth State: MN Issued Date Bail Amount Warrant Type Charge Offense Level 10/18/2016 100 Bench Warrant-fail to appear at a hearing Shoplifting Misdemeanor Name: Abrahamson, Ty Joseph Age: 48 City: Duluth State: MN Issued Date Bail Amount Warrant Type Charge Offense Level 10/24/2019 100 Bench Warrant-fail to appear at a hearing Trespass of Real Property Misdemeanor Name: Aden, Ahmed Omar Age: 35 City: State: Issued Date Bail Amount Warrant Type Charge Offense Level 06/02/2016 485 Bench Warrant-fail to appear at a hearing TRAFF/ACC (EXC DUI) Misdemeanor Name: Adkins, Kyle Gabriel Age: 53 City: Duluth State: MN Issued Date Bail Amount Warrant Type Charge Offense Level 02/28/2013 100 Bench Warrant-fail to appear at a hearing False Pretenses/Swindle/Confidence Game Misdemeanor Name: Aguilar, Raul, JR Age: 32 City: Couderay State: WI Issued Date Bail Amount Warrant Type Charge Offense Level 02/17/2016 Bench Warrant-fail to appear at a hearing Driving Under the Influence Misdemeanor Name: Ainsworth, Kyle Robert Age: 27 City: Duluth State: MN Issued Date Bail Amount Warrant Type Charge Offense Level 11/22/2019 100 Bench Warrant-fail to appear at a hearing Theft Misdemeanor ST. -

The Legacy of INTERPOL Crime Data to Cross-National Criminology1
INTERNATIONAL JOURNAL OF COMPARATIVE AND APPLIED CRIMINAL JUSTICE FALL 2009, VOL. 33, NO. 2 The Legacy of INTERPOL Crime Data to Cross-National Criminology1 ROSEMARY BARBERET2 John Jay College of Criminal Justice, CUNY INTERPOL crime data constitute the oldest and most continuous cross-national data series available to criminologists. Recently, INTERPOL has decided to forego its data collection efforts. This paper, based on a systematic and extensive literature review, will examine how criminologists and other social scientists have used INTERPOL data to examine criti- cal issues in the description and explanation of cross-national crime. It will end with a critical reflection on the contribution of INTERPOL data to our knowledge base, as well as the possibilities that exist for using other data sources to continue research in this area. INTRODUCTION Crime data from INTERPOL are the oldest dataset of cross-national indica- tors of crime maintained by an intergovernmental organization. Thanks to these data, criminologists have created a literature that aims to explain national as well as cross-national differences and trends in crime rates. Created in 1923, the International Criminal Police Commission (ICPC, later abbreviated to ICPC-INTERPOL and now known as INTERPOL) was founded to facilitate police cooperation among countries, even where diplomatic ties do not exist. INTERPOL's International Crime Statistics were first published in 1950. In 2006, INTERPOL decided to cease collecting and disseminating crime data, and 2005 was the last -

ISIS Agent, Sterling Archer, Launches His Pirate King Theme FX Cartoon Series Archer Gets Its First Hip Hop Video Courtesy of Brooklyn Duo, Drop It Steady
ISIS agent, Sterling Archer, launches his Pirate King Theme FX Cartoon Series Archer Gets Its First Hip Hop Video courtesy of Brooklyn duo, Drop it Steady Fans of the FX cartoon series Archer do not need to be told of its genius. The show was created by many of the same writers who brought you the Fox series Arrested Development. Similar to its predecessor, Archer has built up a strong and loyal fanbase. As with most popular cartoons nowadays, hip-hop artists tend to flock to the animated world and Archer now has it's hip-hop spin off. Brooklyn-based music duo, Drop It Steady, created a fun little song and video sampling the show. The duo drew their inspiration from a series sub plot wherein Archer became a "pirate king" after his fiancée was murdered on their wedding day in front of him. For Archer fans, the song and video will definitely touch a nerve as Drop it Steady turns the story of being a pirate king into a forum for discussing recent break ups. Video & Music Download: http://www.mediafire.com/?bapupbzlw1tzt5a Official Website: http://www.dropitsteady.com Drop it Steady on Facebook: http://www.facebook.com/dropitsteady About Drop it Steady: Some say their music played a vital role in the Arab Spring of 2011. Others say the organizers of Occupy Wall Street were listening to their demo when they began to discuss their movement. Though it has yet to be verified, word that the first two tracks off of their upcoming EP, The Most Interesting EP In The World, were recorded at the ceremony for Prince William and Katie Middleton and are spreading through the internets like wild fire. -

Common Quandaries and Their Practical Solutions in Bayesian Network Modeling
Ecological Modelling 358 (2017) 1–9 Contents lists available at ScienceDirect Ecological Modelling journa l homepage: www.elsevier.com/locate/ecolmodel Common quandaries and their practical solutions in Bayesian network modeling Bruce G. Marcot U.S. Forest Service, Pacific Northwest Research Station, 620 S.W. Main Street, Suite 400, Portland, OR, USA a r t i c l e i n f o a b s t r a c t Article history: Use and popularity of Bayesian network (BN) modeling has greatly expanded in recent years, but many Received 21 December 2016 common problems remain. Here, I summarize key problems in BN model construction and interpretation, Received in revised form 12 May 2017 along with suggested practical solutions. Problems in BN model construction include parameterizing Accepted 13 May 2017 probability values, variable definition, complex network structures, latent and confounding variables, Available online 24 May 2017 outlier expert judgments, variable correlation, model peer review, tests of calibration and validation, model overfitting, and modeling wicked problems. Problems in BN model interpretation include objec- Keywords: tive creep, misconstruing variable influence, conflating correlation with causation, conflating proportion Bayesian networks and expectation with probability, and using expert opinion. Solutions are offered for each problem and Modeling problems researchers are urged to innovate and share further solutions. Modeling solutions Bias Published by Elsevier B.V. Machine learning Expert knowledge 1. Introduction other fields. Although the number of generally accessible journal articles on BN modeling has continued to increase in recent years, Bayesian network (BN) models are essentially graphs of vari- achieving an exponential growth at least during the period from ables depicted and linked by probabilities (Koski and Noble, 2011). -

Lecture Misinformation
Quote of the Day: “A lie will go round the world while truth is pulling its boots on.” -- Baptist preacher Charles H. Spurgeon, 1859 Please fill out the course evaluations: https://uw.iasystem.org/survey/233006 Questions on the final paper Readings for next time Today’s class: misinformation and conspiracy theories Some definitions of fake news: • any piece of information Donald Trump dislikes more seriously: • “a type of yellow journalism or propaganda that consists of deliberate disinformation or hoaxes spread via traditional news media (print and broadcast) or online social media.” disinformation: “false information which is intended to mislead, especially propaganda issued by a government organization to a rival power or the media” misinformation: “false or inaccurate information, especially that which is deliberately intended to deceive” Some findings of recent research on fake news, disinformation, and misinformation • False news stories are 70% more likely to be retweeted than true news stories. The false ones get people’s attention (by design). • Some people inadvertently spread fake news by saying it’s false and linking to it. • Much of the fake news from the 2016 election originated in small-time operators in Macedonia trying to make money (get clicks, sell advertising). • However, Russian intelligence agencies were also active (Kate Starbird’s research). The agencies created fake Black Lives Matter activists and Blue Lives Matter activists, among other profiles. A quick guide to spotting fake news, from the Freedom Forum Institute: https://www.freedomforuminstitute.org/first-amendment- center/primers/fake-news-primer/ Fact checking sites are also essential for identifying fake news. -

What Is the Function of Confirmation Bias?
Erkenntnis https://doi.org/10.1007/s10670-020-00252-1 ORIGINAL RESEARCH What Is the Function of Confrmation Bias? Uwe Peters1,2 Received: 7 May 2019 / Accepted: 27 March 2020 © The Author(s) 2020 Abstract Confrmation bias is one of the most widely discussed epistemically problematic cognitions, challenging reliable belief formation and the correction of inaccurate views. Given its problematic nature, it remains unclear why the bias evolved and is still with us today. To ofer an explanation, several philosophers and scientists have argued that the bias is in fact adaptive. I critically discuss three recent proposals of this kind before developing a novel alternative, what I call the ‘reality-matching account’. According to the account, confrmation bias evolved because it helps us infuence people and social structures so that they come to match our beliefs about them. This can result in signifcant developmental and epistemic benefts for us and other people, ensuring that over time we don’t become epistemically disconnected from social reality but can navigate it more easily. While that might not be the only evolved function of confrmation bias, it is an important one that has so far been neglected in the theorizing on the bias. In recent years, confrmation bias (or ‘myside bias’),1 that is, people’s tendency to search for information that supports their beliefs and ignore or distort data contra- dicting them (Nickerson 1998; Myers and DeWall 2015: 357), has frequently been discussed in the media, the sciences, and philosophy. The bias has, for example, been mentioned in debates on the spread of “fake news” (Stibel 2018), on the “rep- lication crisis” in the sciences (Ball 2017; Lilienfeld 2017), the impact of cognitive diversity in philosophy (Peters 2019a; Peters et al. -

Understanding the Qanon Conspiracy from the Perspective of Canonical Information
The Gospel According to Q: Understanding the QAnon Conspiracy from the Perspective of Canonical Information Max Aliapoulios*;y, Antonis Papasavva∗;z, Cameron Ballardy, Emiliano De Cristofaroz, Gianluca Stringhini, Savvas Zannettou◦, and Jeremy Blackburn∓ yNew York University, zUniversity College London, Boston University, ◦Max Planck Institute for Informatics, ∓Binghamton University [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected] — iDRAMA, https://idrama.science — Abstract administration of a vaccine [54]. Some of these theories can threaten democracy itself [46, 50]; e.g., Pizzagate emerged The QAnon conspiracy theory claims that a cabal of (literally) during the 2016 US Presidential elections and claimed that blood-thirsty politicians and media personalities are engaged Hillary Clinton was involved in a pedophile ring [51]. in a war to destroy society. By interpreting cryptic “drops” of A specific example of the negative consequences social me- information from an anonymous insider calling themself Q, dia can have is the QAnon conspiracy theory. It originated on adherents of the conspiracy theory believe that Donald Trump the Politically Incorrect Board (/pol/) of the anonymous im- is leading them in an active fight against this cabal. QAnon ageboard 4chan via a series of posts from a user going by the has been covered extensively by the media, as its adherents nickname Q. Claiming to be a US government official, Q de- have been involved in multiple violent acts, including the Jan- scribed a vast conspiracy of actors who have infiltrated the US uary 6th, 2021 seditious storming of the US Capitol building. -
![Archons (Commanders) [NOTICE: They Are NOT Anlien Parasites], and Then, in a Mirror Image of the Great Emanations of the Pleroma, Hundreds of Lesser Angels](https://docslib.b-cdn.net/cover/8862/archons-commanders-notice-they-are-not-anlien-parasites-and-then-in-a-mirror-image-of-the-great-emanations-of-the-pleroma-hundreds-of-lesser-angels-438862.webp)
Archons (Commanders) [NOTICE: They Are NOT Anlien Parasites], and Then, in a Mirror Image of the Great Emanations of the Pleroma, Hundreds of Lesser Angels
A R C H O N S HIDDEN RULERS THROUGH THE AGES A R C H O N S HIDDEN RULERS THROUGH THE AGES WATCH THIS IMPORTANT VIDEO UFOs, Aliens, and the Question of Contact MUST-SEE THE OCCULT REASON FOR PSYCHOPATHY Organic Portals: Aliens and Psychopaths KNOWLEDGE THROUGH GNOSIS Boris Mouravieff - GNOSIS IN THE BEGINNING ...1 The Gnostic core belief was a strong dualism: that the world of matter was deadening and inferior to a remote nonphysical home, to which an interior divine spark in most humans aspired to return after death. This led them to an absorption with the Jewish creation myths in Genesis, which they obsessively reinterpreted to formulate allegorical explanations of how humans ended up trapped in the world of matter. The basic Gnostic story, which varied in details from teacher to teacher, was this: In the beginning there was an unknowable, immaterial, and invisible God, sometimes called the Father of All and sometimes by other names. “He” was neither male nor female, and was composed of an implicitly finite amount of a living nonphysical substance. Surrounding this God was a great empty region called the Pleroma (the fullness). Beyond the Pleroma lay empty space. The God acted to fill the Pleroma through a series of emanations, a squeezing off of small portions of his/its nonphysical energetic divine material. In most accounts there are thirty emanations in fifteen complementary pairs, each getting slightly less of the divine material and therefore being slightly weaker. The emanations are called Aeons (eternities) and are mostly named personifications in Greek of abstract ideas. -

Bayesian Network Modelling with Examples
Bayesian Network Modelling with Examples Marco Scutari [email protected] Department of Statistics University of Oxford November 28, 2016 What Are Bayesian Networks? Marco Scutari University of Oxford What Are Bayesian Networks? A Graph and a Probability Distribution Bayesian networks (BNs) are defined by: a network structure, a directed acyclic graph G = (V;A), in which each node vi 2 V corresponds to a random variable Xi; a global probability distribution X with parameters Θ, which can be factorised into smaller local probability distributions according to the arcs aij 2 A present in the graph. The main role of the network structure is to express the conditional independence relationships among the variables in the model through graphical separation, thus specifying the factorisation of the global distribution: p Y P(X) = P(Xi j ΠXi ;ΘXi ) where ΠXi = fparents of Xig i=1 Marco Scutari University of Oxford What Are Bayesian Networks? How the DAG Maps to the Probability Distribution Graphical Probabilistic DAG separation independence A B C E D F Formally, the DAG is an independence map of the probability distribution of X, with graphical separation (??G) implying probabilistic independence (??P ). Marco Scutari University of Oxford What Are Bayesian Networks? Graphical Separation in DAGs (Fundamental Connections) separation (undirected graphs) A B C d-separation (directed acyclic graphs) A B C A B C A B C Marco Scutari University of Oxford What Are Bayesian Networks? Graphical Separation in DAGs (General Case) Now, in the general case we can extend the patterns from the fundamental connections and apply them to every possible path between A and B for a given C; this is how d-separation is defined. -

The Future of Sea Mines in the Indo-Pacific
Issue 18, 2020 BREACHING THE SURFACE: THE FUTURE OF SEA MINES IN THE INDO-PACIFIC Alia Huberman, The Australian National Internships Program Issue 18, 2020 EXECUTIVE SUMMARY This report argues that several dynamics of the coming few decades in the Indo-Pacific will see naval mines used once again in the region. It suggests they will form the basis of anti-access strategies for some Indo-Pacific states in a way that will be deeply transformative for the region’s strategic balance and for which Australia is thoroughly unprepared. It seeks to draw attention to the often- underappreciated nature of sea mines as a uniquely powerful strategic tool, offering the user an unparalleled asymmetric ability to engage high-value enemy targets while posing a minimal-risk, low- expense, and continuous threat. In the increasingly contested strategic environment of the contemporary Indo-Pacific - a region in which the threats to free navigation and the maritime economy are existential ones - there is considerable appetite for anti-access and sea denial weapons as defensive, offensive, and coercive tools. Naval strategists must,, prepare for the resurgence of mine warfare in the Indo-Pacific, and for the grand-scale and rapid timeline in which it can transform an operational environment. This report first seeks to collate and outline those characteristics of sea mines and of their interaction with an operational environment that make them attractive for use. It then discusses the states most likely to employ mine warfare and the different scenarios in which they might do so, presenting five individual contingencies: China, Taiwan, North Korea, non-state actors, and Southeast Asian states. -

Forwardahs Year in Review 2014
MOVING FORWARDAHS YEAR IN REVIEW 2014 1 SCIENCES OF APPLIED HEALTH COLLEGE 1 We are what we repeatedly do. Excellence,therefore, is not an act but habit. – Aristotle A MESSAGE FROM THE DEAN As I reviewed this issue of Moving Forward, I was struck by several themes that seem to tie many of the stories together. The first is how life sometimes presents opportunities that, with effort and diligence, lead us along paths we hadn’t imagined taking. Dr. Karen Iler Kirk, the head of our Department of Speech and Hearing Science and the fourth Shahid and Ann Carlson Khan Professor in the College of Applied Health Sciences, began her professional career as a school speech-language pathologist. A fateful decision to join a research institute and a lot of hard work led her on a path to becoming one of the pioneering scholars in pediatric cochlear implantation. Dr. John Greenleaf, our 2014 Distinguished Alumni Award recipient, left Illinois with a bachelor’s degree in kinesiology, fully intending to pursue a career as a physical fitness educator. His decision to pursue an opportunity that presented itself and his dedicated effort led him to a career as a pioneering research scientist with NASA. Dr. Brad Hedrick couldn’t have known when he came to the College of Applied Health Sciences as a graduate student that it would lead to a longtime association with our Division of Disability Resources and Educational Services, as a graduate assistant, coach, and eventually its director. Thirty-seven years later, we celebrated his many achievements upon his retirement.