Release Notes
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Microsoft Mappoint Instruction Manual
Microsoft Mappoint Instruction Manual If you are already using Microsoft® MapPoint®, you know how much trouble it is to This gives step-by-step instructions for starting Microsoft MapPoint, adding. Microsoft, Dexterity, Excel, Internet Explorer, MapPoint, Microsoft Dynamics, This manual provides step-by-step instructions for installing the Microsoft. This site specializes in tools and add-ins for the desktop version of Microsoft MapPoint. These pages describe how to use the various features in Microsoft. Microsoft® MapPoint® 2006/09/10/11/13. North America Maps Compatible. • Google Earth™ Maps (KMF Output). GENERAL DISPATCH FEATURES. But it's time, and we're sad to see MapPoint go. MapPoint was first released in 1999. The product grew out of a 1988 blockbuster designed by four UK. Manual by R:BASE Technologies, Inc. Welcome to R:Magellan 9.5! R:Magellan is a MapPoint software, you can provide fast geographical travel instructions. Microsoft Mappoint Instruction Manual Read/Download manual. In no event will Blackbaud, Inc., be liable for direct, indirect, special, incidental, or ❑The Raiser's Edge integrates with Microsoft's MapPoint 2013. information and instructions, see “Back Up Your Network Database” on page 11. microsoft frontpage 2013 download pdf ebook download - Frontpage 2003 Full Instruction Manual For Mac Using Autocad 2013 Autodesk Autocad 2013 Mac microsoft mappoint 2013 europe ableton live iso reason windows frontpage. Manual Price Change Alerts. Microsoft MapPoint Integration with Bill of Lading Processing......................14. Roadnet and Third-Party Routing. Below will be instructions on how to make sure your email is set up properly. As per Microsoft, support has ended for Windows XP as of 4/8/2014. -
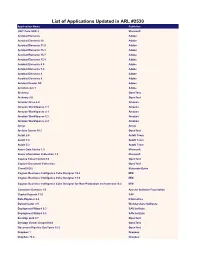
List of Applications Updated in ARL #2530
List of Applications Updated in ARL #2530 Application Name Publisher .NET Core SDK 2 Microsoft Acrobat Elements Adobe Acrobat Elements 10 Adobe Acrobat Elements 11.0 Adobe Acrobat Elements 15.1 Adobe Acrobat Elements 15.7 Adobe Acrobat Elements 15.9 Adobe Acrobat Elements 6.0 Adobe Acrobat Elements 7.0 Adobe Application Name Acrobat Elements 8 Adobe Acrobat Elements 9 Adobe Acrobat Reader DC Adobe Acrobat.com 1 Adobe Alchemy OpenText Alchemy 9.0 OpenText Amazon Drive 4.0 Amazon Amazon WorkSpaces 1.1 Amazon Amazon WorkSpaces 2.1 Amazon Amazon WorkSpaces 2.2 Amazon Amazon WorkSpaces 2.3 Amazon Ansys Ansys Archive Server 10.1 OpenText AutoIt 2.6 AutoIt Team AutoIt 3.0 AutoIt Team AutoIt 3.2 AutoIt Team Azure Data Studio 1.9 Microsoft Azure Information Protection 1.0 Microsoft Captiva Cloud Toolkit 3.0 OpenText Capture Document Extraction OpenText CloneDVD 2 Elaborate Bytes Cognos Business Intelligence Cube Designer 10.2 IBM Cognos Business Intelligence Cube Designer 11.0 IBM Cognos Business Intelligence Cube Designer for Non-Production environment 10.2 IBM Commons Daemon 1.0 Apache Software Foundation Crystal Reports 11.0 SAP Data Explorer 8.6 Informatica DemoCreator 3.5 Wondershare Software Deployment Wizard 9.3 SAS Institute Deployment Wizard 9.4 SAS Institute Desktop Link 9.7 OpenText Desktop Viewer Unspecified OpenText Document Pipeline DocTools 10.5 OpenText Dropbox 1 Dropbox Dropbox 73.4 Dropbox Dropbox 74.4 Dropbox Dropbox 75.4 Dropbox Dropbox 76.4 Dropbox Dropbox 77.4 Dropbox Dropbox 78.4 Dropbox Dropbox 79.4 Dropbox Dropbox 81.4 -

Forensics Evaluation of Privacy of Portable Web Browsers
International Journal of Computer Applications (0975 – 8887) Volume 147 – No. 8, August 2016 Forensics Evaluation of Privacy of Portable Web Browsers Ahmad Ghafarian Seyed Amin Hosseini Seno Department of Computer Science Department of Computer Engineering and Information Systems Faculty of Engineering University of North Georgia Ferdowsi University of Mashhad Dahlonega, GA 30005, USA Mashhad, Iran ABSTRACT relation to a computer forensic investigation is that the latter is Browsers claim private mode browsing saves no data on the a less tangible source of evidence [3]. host machine. Most popular web browsers also offer portable A study of tools and techniques for memory forensics can be versions of their browsers which can be launched from a found in [4]. The author has evaluated several command line removable device. When the removable device is removed, it and graphical user interface tools and provide the steps is claimed that traces of browsing activities will be deleted needed for memory forensics. Retrieving portable browsing and consequently private portable browsers offer better forensics artifacts left behind from main memory have privacy. This makes the task of computer forensics recently attracted some attention [5, 6]. The authors used investigators who try to reconstruct the past browsing history, limited memory forensics to retrieve forensics artifacts left in case of any computer incidence, more challenging. after a private portable browsing session. They argue that However, whether or not all data is deleted beyond forensic memory forensics is very promising in establishing a link recovery is a moot point. This research examines privacy of between the suspect and the retrieved data. -

(Hardening) De Navegadores Web Más Utilizados
UNIVERSIDAD DON BOSCO VICERRECTORÍA DE ESTUDIOS DE POSTGRADO TRABAJO DE GRADUACIÓN Endurecimiento (Hardening) de navegadores web más utilizados. Caso práctico: Implementación de navegadores endurecidos (Microsoft Internet Explorer, Mozilla Firefox y Google Chrome) en un paquete integrado para Microsoft Windows. PARA OPTAR AL GRADO DE: MAESTRO EN SEGURIDAD Y GESTION DEL RIESGO INFORMATICO ASESOR: Mg. JOSÉ MAURICIO FLORES AVILÉS PRESENTADO POR: ERICK ALFREDO FLORES AGUILAR Antiguo Cuscatlán, La Libertad, El Salvador, Centroamérica Febrero de 2015 AGRADECIMIENTOS A Dios Todopoderoso, por regalarme vida, salud y determinación para alcanzar un objetivo más en mi vida. A mi amada esposa, que me acompaño durante toda mi carrera, apoyó y comprendió mi dedicación de tiempo y esfuerzo a este proyecto y nunca dudó que lo concluiría con bien. A mis padres y hermana, que siempre han sido mis pilares y me enseñaron que lo mejor que te pueden regalar en la vida es una buena educación. A mis compañeros de trabajo, que mediante su esfuerzo extraordinario me han permitido contar con el tiempo necesario para dedicar mucho más tiempo a la consecución de esta meta. A mis amigos de los que siempre he tenido una palabra de aliento cuando la he necesitado. A mi supervisor y compañeros de la Escuela de Computación de la Universidad de Queens por facilitarme espacio, recursos, tiempo e información valiosa para la elaboración de este trabajo. A mi asesor de tesis, al director del programa de maestría y mis compañeros de la carrera, que durante estos dos años me han ayudado a lograr esta meta tan importante. Erick Alfredo Flores Aguilar INDICE I. -

Snap on Windows an Intel-Sponsored, Open-Source Telemetry Framework IT 447 April 4, 2017
Snap on Windows An Intel-sponsored, open-source telemetry framework IT 447 April 4, 2017 Phillip Anderson McKade Clements Devin Durtschi Mathew Kuhn Jesse Millar Coach: Dr. Jay Ekstrom Sponsor: Taylor Thomas Table of Contents Table of Contents Executive Summary Introduction Concept Definition Background Stakeholders Intel Companies with Windows Systems Operators of Windows Systems Open-source Maintainers of the Snap Project Members of the Snap Community Stakeholder Requirements Validation Verification System Definition System Requirements Logical Architecture Project Component Details Build Windows Test Environment Perfmon Plugin Sysinternals Plugin Active Directory Plugin Create an Automated Build Script for Snap Critical Path Verification and Validation Project Management Objective Statement List of Deliverables Conclusion References Appendix Source Code Constraint Matrix Governance Framework Communication Acceptance Documentation Gantt Chart Executive Summary Snap for Windows is a Brigham Young University Information Technology 2016-2017 capstone project. Snap is an open-source telemetry system headed by Intel, meant to facilitate the remote monitoring of large networks and company infrastructures. Snap works through three types of “plugins,” which allow for modularized collecting, processing, and publishing of system metrics. These metrics can include data such as cpu usage, number of processes running on a system, and memory available. Previously, Snap’s functionalities were constrained to Linux systems only, and were not compatible with Windows. This prevented a large portion of company infrastructures from utilizing Snap, as companies typically run the Windows operating system on a large portion of their network. The objective for this project included automating Snap’s build process onto Windows through a build script and creating three separate collector plugins based on the Windows’ Perfmon, Active Directory, and Sysinternals applications. -

The Future Computer the Future Computer
Anyone MICROSOFT TECHNOLOGY who knows DEPLOYMENT ISSUE 6 OCTOBER 2003 this much TECHNOLOGY about our software .NET: CHANGING THE FACE OF DEVELOPING is probably SQL SERVER: WAITING FOR YUKON TERMINAL SERVICES: certifiable. AT YOUR FINGERTIPS The Affinity Homes Group chose Phoenix Software, a Microsoft Certified Partner, to migrate 250 users and their 20 servers to It takes a special company to be a Microsoft Gold Certified Open here Windows 2000, Microsoft Exchange 5.5 and Partner, one that’s demonstrated an exceptional level of You naturally want your IT service provider to have proven Microsoft Exchange 2000 Server. Richard Swift, specialist expertise in a particular Microsoft solution. And expertise across the full range of Microsoft products for the ultimate Head of Information Systems at Affinity you will reap the rewards for all their hard work, as you get commented: “We had been working with and solutions. Every Microsoft Certified Partner has met the assurance of the highest possible levels of service. Microsoft resource guide Phoenix for a number of years and they are a rigorous technical criteria set by Microsoft, so you can be THETHE FUTUREFUTURE Whatever challenges you’re facing, a Microsoft Gold Certified Microsoft Certified Partner, that gave us the confident that they can give you the high level of service Partner is perfectly qualified to make your IT systems for IT Professionals and added comfort of knowing that they had the you expect, together with trustworthy, independent advice. Developers right level of expertise that we were looking for”. workFor moreharder details, for you. visit Visit www.microsoft.com/uk/certified www.microsoft.com/uk/certified COMPUTERCOMPUTER PUSHINGPUSHING THETHE BOUNDARIESBOUNDARIES ATAT < ©Microsoft©Microsoft Corporation. -
Automate Windows Environments with Ansible
Automate Windows Environments with Ansible Orcun Atakan [email protected] Sr. Solution Architect, Red Hat ANSIBLE AUTOMATION FOR WINDOWS What we’ll be discussing today What is Ansible? Windows Management with Ansible What is DSC? Why Use Ansible with DSC? Demo: Rolling update of a .NET application on Windows 2 37,000+ 2800+ 500,000+ Stars on GitHub Ansible modules Downloads a month 3 WHY ANSIBLE? (for Windows) SIMPLE POWERFUL AGENTLESS Human readable automation Enable many use cases Ideal for Windows remoting No special coding skills needed Works hand-in-hand with DSC resources No agents to exploit or update Tasks executed in order Easy platform enablement Standards-based WinRM Usable by every team Leverage Powershell Get productive quickly ANSIBLE AUTOMATION WORKS ACROSS TEAMS BUSINESS DEV/QA COMPUTE NETWORK/SECURITY I.T. OPERATIONS 5 WINDOWS AUTOMATION 100+ 1,300+ Windows Powershell DSC Modules resources ansible.com/windows WHAT CAN I DO USING ANSIBLE FOR WINDOWS Native Windows support uses PowerShell remoting to manage Windows in the same Ansible agentless way ● Install and uninstall MSIs ● Gather facts on Windows hosts ● Enable and disable Windows features ● Start, stop, and manage Windows Services ● Create and Manage local users and groups ● Manage Windows packages via Chocolatey package manager ● Manage and install Windows updates ● Fetch files from remote sites ● Push and execute any Powershell scripts 7 Playbook Example 1/2 - hosts: new_servers tasks: - name: ensure common OS updates are current win_updates: register: update_result -
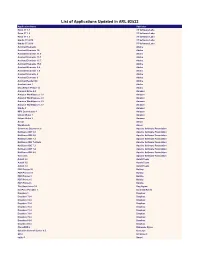
List of Applications Updated in ARL #2532
List of Applications Updated in ARL #2532 Application Name Publisher Robo 3T 1.1 3T Software Labs Robo 3T 1.2 3T Software Labs Robo 3T 1.3 3T Software Labs Studio 3T 2018 3T Software Labs Studio 3T 2019 3T Software Labs Acrobat Elements Adobe Acrobat Elements 10 Adobe Acrobat Elements 11.0 Adobe Acrobat Elements 15.1 Adobe Acrobat Elements 15.7 Adobe Acrobat Elements 15.9 Adobe Acrobat Elements 6.0 Adobe Acrobat Elements 7.0 Adobe Acrobat Elements 8 Adobe Acrobat Elements 9 Adobe Acrobat Reader DC Adobe Acrobat.com 1 Adobe Shockwave Player 12 Adobe Amazon Drive 4.0 Amazon Amazon WorkSpaces 1.1 Amazon Amazon WorkSpaces 2.1 Amazon Amazon WorkSpaces 2.2 Amazon Amazon WorkSpaces 2.3 Amazon Kindle 1 Amazon MP3 Downloader 1 Amazon Unbox Video 1 Amazon Unbox Video 2 Amazon Ansys Ansys Workbench Ansys Commons Daemon 1.0 Apache Software Foundation NetBeans IDE 5.0 Apache Software Foundation NetBeans IDE 5.5 Apache Software Foundation NetBeans IDE 7.2 Apache Software Foundation NetBeans IDE 7.2 Beta Apache Software Foundation NetBeans IDE 7.3 Apache Software Foundation NetBeans IDE 7.4 Apache Software Foundation NetBeans IDE 8.0 Apache Software Foundation Tomcat 5 Apache Software Foundation AutoIt 2.6 AutoIt Team AutoIt 3.0 AutoIt Team AutoIt 3.2 AutoIt Team PDF Printer 10 Bullzip PDF Printer 11 Bullzip PDF Printer 3 Bullzip PDF Printer 5 Bullzip PDF Printer 6 Bullzip The Unarchiver 3.1 Dag Agren KeePass Portable 1 Dominik Reichl Dropbox 1 Dropbox Dropbox 73.4 Dropbox Dropbox 74.4 Dropbox Dropbox 75.4 Dropbox Dropbox 76.4 Dropbox Dropbox 77.4 Dropbox -

Long-Range EV Charging Infrastructure Plan for Western Oregon
Long-Range EV Charging Infrastructure Plan for Western Oregon August 2010 Version 3.3 Long-Range EV Charging Infrastructure Plan for Western Oregon 2010 by Electric Transportation Engineering Corporation. All rights reserved. No part of the contents of this document may be reproduced or transmitted in any form or by any means without the express written permission of Electric Transportation Engineering Corporation. This material is based upon work supported by the U.S. Department of Energy under Award Number DE-EE0002194 Microsoft® and MapPoint® are registered trademarks of Microsoft Corporation. Disclaimers This document establishes the foundation for the initial deployment of electric vehicle supply equipment (EVSE) by Electric Transportation Engineering Corporation (doing business as ECOtality North America). Neither ECOtality NA, nor any of its affiliates: (a) represents, guarantees, or warrants to any third party, either expressly or by implication: (i) the accuracy, completeness, or usefulness of; (ii) the intellectual or other property rights of any person or party in; or (iii) the merchantability, safety, or fitness for purpose of; any information, product, or process disclosed, described, or recommended in this document, (b) assumes any liability of any kind arising in any way out of the use by a third party of any information, product, or process disclosed, described, or recommended in this document, or any liability arising out of reliance by a third party upon any information, statements, or recommendations contained in this document. Should third parties use or rely on any information, product, or process disclosed, described, or recommended in this document, they do so entirely at their own risk. -

Windows Tool Reference
AppendixChapter A1 Windows Tool Reference Windows Management Tools This appendix lists sets of Windows management, maintenance, configuration, and monitor- ing tools that you may not be familiar with. Some are not automatically installed by Windows Setup but instead are hidden away in obscure folders on your Windows Setup DVD or CD- ROM. Others must be downloaded or purchased from Microsoft. They can be a great help in using, updating, and managing Windows. We’ll discuss the following tool kits: ■ Standard Tools—Our pick of handy programs installed by Windows Setup that we think are unappreciated and not well-enough known. ■ Support Tools—A set of useful command-line and GUI programs that can be installed from your Windows Setup DVD or CD-ROM. ■ Value-Added Tools—Several more sets of utilities hidden away on the Windows Setup CD-ROM. ■ Windows Ultimate Extras and PowerToys for XP—Accessories that can be downloaded for free from microsoft.com. The PowerToys include TweakUI, a program that lets you make adjustments to more Windows settings than you knew existed. ■ Resource Kits—A set of books published by Microsoft for some versions of Windows that includes a CD-ROM containing hundreds of utility programs. What you may not have known is that in some cases you can download the Resource Kit program toolkits with- out purchasing the books. ■ Subsystem for UNIX-Based Applications (SUA)—A package of network services and command-line tools that provide a nearly complete UNIX environment. It can be installed only on Windows Vista Ultimate and Enterprise, and Windows Server 2003. -

Piratebrowser Artifacts
PirateBrowser Artifacts Written by Chris Antonovich Researched by Olivia Hatalsky 175 Lakeside Ave, Room 300A Phone: 802/865-5744 Fax: 802/865-6446 http://www.lcdi.champlin.edu Published Date Patrick Leahy Center for Digital Investigation (LCDI) Disclaimer: This document contains information based on research that has been gathered by employee(s) of The Senator Patrick Leahy Center for Digital Investigation (LCDI). The data contained in this project is submitted voluntarily and is unaudited. Every effort has been made by LCDI to assure the accuracy and reliability of the data contained in this report. However, LCDI nor any of our employees make no representation, warranty or guarantee in connection with this report and hereby expressly disclaims any liability or responsibility for loss or damage resulting from use of this data. Information in this report can be downloaded and redistributed by any person or persons. Any redistribution must maintain the LCDI logo and any references from this report must be properly annotated. Contents Introduction ............................................................................................................................................................................. 2 Background: ........................................................................................................................................................................ 2 Purpose and Scope: ............................................................................................................................................................ -

Home-Grown Cyber Security
Home-Grown Cyber Security John B. Folkerts, CISSP https://www.linkedin.com/in/john-b-folkerts About Me … 20 years doing Information Security, Architecture, and Risk Management in large enterprise environments Prior to that, a Communications Officer in the US Air Force Involved in many incident response efforts and technology deployments, including Identity Management, Data Loss Protection, Antivirus, Malware Sandbox technology, Log Management, and Intrusion Detection Classical music fan, developing jazz aficionado Disclaimers My comments reflect my own opinions, and not those of my employers, past, present, or future. The tools and services mentioned in this presentation are freely available on the internet. They may not be suitable for your specific environment. Think carefully about your support requirements before using free or open source software or services. Despite being free, most of the tools mentioned have software licensing that governs their use, distribution, etc.... Please read the licenses and check with an attorney as needed to determine whether they are suitable for your environment. Traditional Approach to Security (Controls-based: Patching, Antivirus, Firewalls, Complex Passwords … ) The Strengths Protective – stop what we know is bad The Weaknesses Zero Day Exploits Constantly changing malware signatures Encryption, Tunneling through and around firewall rules Passwords attacked at the weakest point – the user … or worse the password hash database Enter the Cyber Security Framework … Cyber Security Framework