An Overview of the Sender Policy Framework (SPF) As an Anti- Phishing Mechanism
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Electronic Mail Standard
IT Shared Services Standard: Electronic Mail Standard For South Carolina State Agencies Version 1.0 Effective: August 8, 2018 Revision History: Date Authored by Title Ver. Notes Recommended by the Security and Architecture 08.08.2018 Standards 1.0 Executive Oversight Group. Review Board Standard finalized. Electronic Mail Standard | 2 Contents Revision History: ................................................................................................................................... 1 Electronic Mail ...................................................................................................................................... 4 Rationale ........................................................................................................................................... 4 Agency Exception Requests ............................................................................................................... 4 Current State..................................................................................................................................... 4 Purchasing......................................................................................................................................... 4 Maintenance ..................................................................................................................................... 5 Service Level Agreements ............................................................................................................. 5 Security ............................................................................................................................................ -

What Is DMARC, SPF, and DKIM? • How to Configure • Common Mistakes • Best Practices • How Phishes Get By
How to Prevent 81% of Phishing Attacks From Sailing Right Through DMARC, SPF, and DKIM Roger A. Grimes Data-Driven Defense Evangelist [email protected] About Roger • 30 years plus in computer security • Expertise in host and network security, IdM, crypto, PKI, APT, honeypot, cloud security • Consultant to world’s largest companies and militaries for decades • Previous worked for Foundstone, McAfee, Microsoft • Written 11 books and over 1,000 magazine articles • InfoWorld and CSO weekly security columnist since 2005 • Frequently interviewed by magazines (e.g. Newsweek) and radio shows (e.g. NPR’s All Things Considered) Roger A. Grimes Certification exams passed include: Data-Driven Defense Evangelist KnowBe4, Inc. • CPA • CISSP Twitter: @RogerAGrimes • CISM, CISA LinkedIn: https://www.linkedin.com/in/rogeragrimes/ • MCSE: Security, MCP, MVP • CEH, TISCA, Security+, CHFI • yada, yada Roger’s Books 3 KnowBe4, Inc. • The world’s most popular integrated Security Awareness Training and Simulated Phishing platform • Based in Tampa Bay, Florida, founded in 2010 • CEO & employees are ex-antivirus, IT Security pros • 200% growth year over year • We help tens of thousands of organizations manage the problem of social engineering 4 Today’s Presentation • What is DMARC, SPF, and DKIM? • How to Configure • Common Mistakes • Best Practices • How Phishes Get By 5 • What is DMARC, SPF, and DKIM? § How to Configure Agenda • Best Practices • How Phishes Get By 6 DMARC, DKIM, SPF Global Phishing Protection Standards • Sender Policy Framework (SPF) • Domain -

A Security Analysis of Email Communications
A security analysis of email communications Ignacio Sanchez Apostolos Malatras Iwen Coisel Reviewed by: Jean Pierre Nordvik 2 0 1 5 EUR 28509 EN European Commission Joint Research Centre Institute for the Protection and Security of the Citizen Contact information Ignacio Sanchez Address: Joint Research Centre, Via Enrico Fermi 2749, I - 21027 Ispra (VA), Italia E-mail: [email protected] JRC Science Hub https://ec.europa.eu/jrc Legal Notice This publication is a Technical Report by the Joint Research Centre, the European Commission’s in-house science service. It aims to provide evidence-based scientific support to the European policy-making process. The scientific output expressed does not imply a policy position of the European Commission. Neither the European Commission nor any person acting on behalf of the Commission is responsible for the use which might be made of this publication. All images © European Union 2015, except: Frontpage : © bluebay2014, fotolia.com JRC 99372 EUR 28509 EN ISSN 1831-9424 ISBN 978-92-79-66503-5 doi:10.2760/319735 Luxembourg: Publications Office of the European Union, 2015 © European Union, 2015 Reproduction is authorised provided the source is acknowledged. Printed in Italy Abstract The objective of this report is to analyse the security and privacy risks of email communications and identify technical countermeasures capable of mitigating them effectively. In order to do so, the report analyses from a technical point of view the core set of communication protocols and standards that support email communications in order to identify and understand the existing security and privacy vulnerabilities. On the basis of this analysis, the report identifies and analyses technical countermeasures, in the form of newer standards, protocols and tools, aimed at ensuring a better protection of the security and privacy of email communications. -

98-367: Security Fundamentals
98-367: Security Fundamentals 1. Understand security layers (25–30%) 1.1. Understand core security principles Confidentiality; integrity; availability; how threat and risk impact principles; principle of least privilege; social engineering; attack surface analysis; threat modelling 1.2. Understand physical security Site security; computer security; removable devices and drives; access control; mobile device security; disable Log On Locally; keyloggers 1.3. Understand Internet security Browser security settings; zones; secure websites 1.4. Understand wireless security Advantages and disadvantages of specific security types; keys; service set identifiers (SSIDs); MAC filters 2. Understand operating system security (30–35%) 2.1. Understand user authentication Multifactor authentication; physical and virtual smart cards; Remote Authentication Dial- In User Service (RADIUS); Public Key Infrastructure (PKI); understand the certificate chain; biometrics; Kerberos and time skew; use Run As to perform administrative tasks; password reset procedures 2.2. Understand permissions File system permissions; share permissions; registry; Active Directory; NT file system (NTFS) versus file allocation table (FAT); enable or disable inheritance; behavior when moving or copying files within the same disk or on another disk; multiple groups with different permissions; basic permissions and advanced permissions; take ownership; delegation; inheritance 2.3. Understand password policies Password complexity; account lockout; password length; password history; time -

BOD-18-01 Original Release Date: Applies To: All Federal Executive Branch Departments and Agencies
Secretary U.S. Department of Homeland Security Washington,DC 20528 Homeland Security Binding Operational Directive BOD-18-01 Original Release Date: Applies to: All Federal Executive Branch Departments and Agencies FROM: Elaine C. Duke Acting Secretary OCT 1 6 20t7 CC: Mick Mulvaney Director, Office of Management and Budget SUBJECT: Enhance Email and Web Security A binding operational directive is a compulsory direction to federal, executive branch, departments and agencies for purposes of safeguardingfederal information and information systems. 44 U.S.C. § 3552(b)(l). The Department ofHomeland Security (DHS) develops and oversees the implementation ofbinding operational directivespursuant to the Federal InformationSecurity Modernization Act of2014 ("FISMA"). Id.§ 3553(b)(2). Federal agencies are required to comply with these DHS-developed directives. Id. § 3554(a)(l)(B)(ii). DHS binding operational directivesdo not apply to statutorily defined"National Security Systems" or to certain systems operated by the Department ofDefense orthe Intelligence Community. Id. § 3553(d)-(e). I. Background Federal agency 'cyber hygiene' greatly impacts user security. By implementing specific security standards that have been widely adopted in industry, federal agencies can ensure the integrity and confidentiality of internet-delivered data, minimize spam, and better protect users who might otherwise fall victim to a phishing email that appears to come from a government-owned system. Based on current network scandata and a clear potential forharm, this directive requires actions related to two topics: email security and web security. A. Email Security STARTTLS When enabled by a receiving mail server, STARTTLS signals to a sending mail server that the capability to encrypt an email in transit is present. -

Composition Kills: a Case Study of Email Sender Authentication
Composition Kills: A Case Study of Email Sender Authentication Jianjun Chen, Vern Paxson, and Jian Jiang Component-based software design has been widely adopted as a way to manage complexity and improve reusability. The approach divides complex systems into smaller modules that can be independently created and reused in different systems. One then combines these components together to achieve desired functionality. Modern software systems are commonly built using components made by different developers who work independently. While having wide-ranging benefits, the security research community has recognized that this practice also introduces security concerns. In particular, when faced with crafted adversarial inputs, different components can have inconsistent interpretations when operating on the input in sequence. Attackers can exploit such inconsistencies to bypass security policies and subvert the system’s operation. In this work we provide a case study of such composition issues in the context of email (SMTP) sender authentication. We present 18 attacks for widely used email services to bypass their sender authentication checks by misusing combinations of SPF, DKIM and DMARC, which are crucial defenses against email phishing and spear-phishing attacks. Leveraging these attack techniques, an attacker can impersonate arbitrary senders without breaking email authentication, and even forge DKIM-signed emails with a legitimate site’s signature. Email spoofing, commonly used in phishing attacks, poses a serious threat to both individuals and organiza- tions. Over the past years, a number of attacks used email spoofing or phishing attacks to breach enterprise networks [5] or government officials’ accounts [10]. To address this problem, modern email services and websites employ authentication protocols—SPF, DKIM, and DMARC—to prevent email forgery. -

Master Thesis Characterizing Sender Policy Framework Configurations At
Master Thesis Characterizing Sender Policy Framework Configurations at Scale Gabri¨elMathay Kahraman Monday 7th September, 2020 A thesis presented for the degree of Master of Science Computer Science Design and Analysis of Communication Systems (DACS) Chair: prof. dr. ir. Aiko Pras Supervisor: dr. ir. Mattijs Jonker Co-supervisors: ir. Olivier van der Toorn and dr. Doina Bucur Abstract Phishing involves disguising oneself as a trustworthy entity in electronic communication, for example, by pretending to send e-mail on behalf of a company. Phishing e-mails can be prevented if domains implement e-mail security techniques. One of the techniques to improve e-mail security is the Sender Policy Framework (SPF). To enable SPF, the administrator of a domain can specify an SPF policy in the DNS zone of the domain. The SPF policy determines which IP addresses are authorised to send e-mail from the administrator's domain. When an e-mail server receives an e-mail, the e-mail server retrieves the SPF policy of the sender's domain. Next, the IP address of the sender will be queried against the SPF record, and the response of this query determines how to handle the incoming e-mail. The SPF standard was released over six years ago. Even though six years have passed, the research community does not yet have a thorough understanding of the characteristics of SPF use. What we miss is an understanding of how SPF policies are configured, how SPF policies have changed over time, and what the problematic trends are of SPF use. In this Thesis, we address the missing of a large scale analysis on SPF policies over time. -
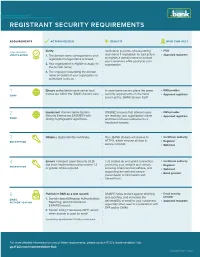
Registrant Security Requirements
REGISTRANT SECURITY REQUIREMENTS REQUIREMENTS ACTION NEEDED BENEFIT WHO CAN HELP PRELIMINARY Verify: Verification prevents cybersquatting fTLD VERIFICATION 1. The domain name corresponds to your and makes it impossible for bad actors Approved registrars organization's legal name or brand; to register a domain name or contact your customers while posing as your 2. Your organization is eligible to apply for organization. the domain name; 3. The employee requesting the domain name on behalf of your organization is authorized to do so. 1 Ensure authoritative name server host In-zone name servers place the same DNS provider ZONE names are within the .BANK domain zone. security requirements on the name Approved registrars server as the .BANK domain itself. 2 Implement Domain Name System DNSSEC ensures that internet users DNS provider Security Extensions (DNSSEC) with are reaching your organization online Approved registrars ZONE strong cryptographic algorithms. and have not been redirected to a fraudulent website. 3 Obtain a digital identity certificate. Your .BANK domain will resolve to Certificate authority ENCRYPTION HTTPS, which ensures all data is Registrar secure in transit. Web host 4 Ensure Transport Layer Security (TLS) TLS creates an encrypted connection, Certificate authority has been implemented using version 1.2 protecting your website and visitors, ENCRYPTION Registrar or greater where required. securing email communications, and Web host supporting the safe and secure Email provider transmission of information and transactions. 5 Publish in DNS as a text record: DMARC helps protect against phishing Email security and spoofing, and increases the provider EMAIL 1. Domain-based Message Authentication, Approved registrars AUTHENTICATION Reporting, and Conformance deliverability of email to your customers, (DMARC) record; especially when used in combination with SPF and/or DKIM. -

Cisa-Dmarc.Pdf
Domain-Based Message Authentication, Reporting and Conformance Domain-Based Message Authentication, Reporting and Conformance (DMARC) is an email authentication policy that protects against bad actors using fake email addresses disguised to look like legitimate emails from trusted sources. DMARC makes it easier for email senders and receivers to determine whether or not an email legitimately originated from the identified sender. Further, DMARC provides the user with instructions for handling the email if it is fraudulent. Why should State and Local Election Officials be interested in DMARC? State and local election officials face a high volume of spam and phishing attacks on their internet accessible systems. Fraudulent emails are easy to design and cheap to send, which provides malicious actors incentive to use repeated email attacks. Unfortunately, employees are often the point of failure for these attacks, when they are forced to repeatedly determine whether emails are legitimate or fake. DMARC provides an automated solution to this issue, making it easier to identify spam and phishing messages before they ever reach an employee’s inbox. How does DMARC work? DMARC removes guesswork from the receiver’s handling of failed emails, limiting or eliminating the user’s exposure to potentially fraudulent and harmful messages. A DMARC policy allows a sender to indicate that their emails are protected by Sender Policy Framework (SPF) and/or Domain Keys Identified Message (DKIM), both of which are industry-recognized email authentication techniques. DMARC also provides instructions on how the receiver should handle emails that fail to pass SPF or DKIM authentication. Options typically include sending the email to quarantine or rejecting it entirely. -
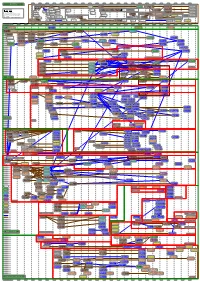
Diagram of the Descent of MAIL Rfcs
1971 1972 1973 1974 1975 1976 1977 1978 1979 1980 1981 1982 1983 1984 1985 1986 1987 1988 1989 1990 1991 1992 1993 MAILMAIL RFCs RFCs RFC 989 / Historic RFC 1113 / Historic RFC 1421 / Historic RFC 171 RFC 264 RFC 354 RFC 542 RFC 765 Privacy enhancement for Privacy enhancement for Privacy Enhancement for The Data The Data File File RFC 751 RFC 959 / STD 9 File Transfer Internet electronic mail: Part I: Internet electronic mail: Part I - Internet Electronic Mail: Part Transfer Transfer Transfer Transfer Survey of FTP File Transfer Protocol RFC 414 RFC 614 Protocol Message encipherment and message encipherment and I: Message Encryption and Protocol Protocol Protocol Protocol mail and MLFL RFC 172 RFC 265 File Transfer Response to RFC 607: FTPFTP mail mail authentication procedures authentication procedures Authentication Procedures The File The File Protocol (FTP) "Comments on the File RFC 1114 / Historic RFC 1422 / Historic RFC 524 Transfer Transfer status and further Transfer Protocol" RFC 1040 / Historic Privacy enhancement for Privacy Enhancement for Proposed Mail RFC 780 Protocol Protocol comments RFC 753 RFC 772 RFC 788 RFC 821 / STD 10 RFC 876 Privacy enhancement for Internet electronic mail: Part II Internet Electronic Mail: Part Protocol Mail RFC 640 RFC 706 Internet Message Mail Transfer Simple Mail Simple Mail Transfer Survey of SMTP MTP,MTP, SMTP SMTP Internet electronic mail: Part I: - certificate-based key II: Certificate-Based Key RFC 385 RFC 454 Revised FTP On the junk mail Transfer management Management RFC 114 Protocol -

CS 155 Final Exam
CS 155: Spring 2015 June 5, 2015 CS 155 Final Exam This exam is open book and open notes. You may use course notes and documents that you have stored on a laptop, but you may NOT use the network connection on your laptop in any way, especially not to search the web or communicate with a friend. You have 2 hours. Print your name legibly and sign and abide by the honor code written below. All of the intended answers may be written in the space provided. You may use the back of a page for scratch work. If you use the back side of a page to write part of your answer, be sure to mark your answer clearly. The following is a statement of the Stanford University Honor Code: A. The Honor Code is an undertaking of the students, individually and collectively: (1) that they will not give or receive aid in examinations; that they will not give or receive unpermitted aid in class work, in the preparation of reports, or in any other work that is to be used by the instructor as the basis of grading; (2) that they will do their share and take an active part in seeing to it that others as well as themselves uphold the spirit and letter of the Honor Code. B. The faculty on its part manifests its confidence in the honor of its students by refraining from proctoring examinations and from taking unusual and unreasonable precautions to prevent the forms of dishonesty mentioned above. The faculty will also avoid, as far as practicable, academic procedures that create temptations to violate the Honor Code. -

Draft NIST SP 800-177 Revision 1, Trustworthy Email
1 DRAFT NIST Special Publication 800-177 2 Revision 1 3 Trustworthy Email 4 5 6 Ramaswamy Chandramouli 7 Simson Garfinkel 8 Stephen Nightingale 9 Scott Rose 10 11 12 13 14 15 16 17 18 19 C O M P U T E R S E C U R I T Y 20 21 22 DRAFT NIST Special Publication 800-177 23 Revision 1 24 Trustworthy Email 25 26 Scott Rose 27 Stephen Nightingale 28 Information Technology Laboratory 29 Advanced Network Technology Division 30 31 Simson L. Garfinkel 32 US Census Bureau 33 34 Ramaswamy Chandramouli 35 Information Technology Laboratory 36 Computer Security Division 37 38 39 40 41 42 43 44 September 2017 45 46 47 48 49 U.S. Department of Commerce 50 Wilbur L. Ross, Jr., Secretary 51 52 National Institute of Standards and Technology 53 Kent Rochford, Acting NIST Director and Under Secretary of Commerce for Standards and Technology 54 55 Authority 56 This publication has been developed by NIST in accordance with its statutory responsibilities under the 57 Federal Information Security Modernization Act (FISMA) of 2014, 44 U.S.C. § 3551 et seq., Public Law 58 (P.L.) 113-283. NIST is responsible for developing information security standards and guidelines, including 59 minimum requirements for federal information systems, but such standards and guidelines shall not apply 60 to national security systems without the express approval of appropriate federal officials exercising policy 61 authority over such systems. This guideline is consistent with the requirements of the Office of Management 62 and Budget (OMB) Circular A-130, Section 8b(3), Securing Agency Information Systems, as analyzed in 63 Circular A-130, Appendix IV: Analysis of Key Sections.