Gl120 Linux Fundamentals Rhel7 Sles12 U16.04
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Linux on a Stick Everyone Knows You Can Boot Linux from a Live CD, but Have You Thought About Putting Linux on a Compact and Highly Portable USB
KNOW HOW Memory Stick Linux Booting Linux from a USB Memory Stick Linux on a Stick Everyone knows you can boot Linux from a live CD, but have you thought about putting Linux on a compact and highly portable USB memory stick? BY FABRIZIO CIACCHI bootable “live” CD like Knoppix much more common. Part of our pur- ent from DSL, but it includes more [1] or Kanotix [2] gives the user a pose is to create an inexpensive system, software (about 14 MB plus), and it Afully portable operating environ- so I will base this discussion on the stan- has already been refined and tested for ment. You can carry your system with dard and very common 128 MB size. USB devices. you and boot it from anywhere. However, the procedure I describe in this • Flonix [8]: Flonix is also based on Your tools, your files, and your work- article can also be used to put a larger DSL, but it uses some different pro- space will follow you wherever you go – Knoppix-based distribution on a larger grams (for instance, IceWM instead even to another PC with a different USB memory stick. of Fluxbox). The Flonix project also operating system. Live CDs are also used Assuming you want room to work and introduced a useful web install by system administrators for trouble- store documents, it is a good idea to only process. Ultimately, Flonix was so shooting computers that won’t boot use half of the available space (64 MB) successful that it become a commer- normally. for the Linux system and related tools. -

Migration System for Zoe Microservices
Computer Science Department BACHELOR THESIS Migration system for Zoe microservices Author: Rafael Medina García Supervisor: David Expósito Singh Madrid, June 2016 Copyright ©2016. Rafael Medina García This work is licensed under the Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License. To view a copy of this license, visit http://creativecommons.org/licenses/by-nc-sa/4.0/. Esta obra está sujeta a la licencia Reconocimiento-NoComercial-CompartirIgual 4.0 Internacional de Creative Commons. Para ver una copia de esta licencia, visite http://creativecommons.org/licenses/by-nc-sa/4.0/. i Título: Migration system for Zoe microservices Autor: Rafael Medina García Tutor: David Expósito Singh EL TRIBUNAL Presidente: José Manuel Sánchez Pena Secretario: Pedro Peris López Vocal: María Paula de Toledo Heras Realizado el acto de defensa y lectura del Trabajo Fin de Grado el día 7 de julio de 2016 en Leganés, en la Escuela Politécnica Superior de la Universidad Carlos III de Madrid, acuerda otorgarle la CALIFICACIÓN de: VOCAL SECRETARIO PRESIDENTE ii Agradecimientos Agradezco: A mis padres y hermano, por vuestro apoyo, siempre; a Dorito-senpai y sus increíbles amigos: Jaime y Nacho; a Adrián, por esas interminables tardes trabajando en el despacho; al Grupo de Usuarios de Linux de la Universidad Carlos III de Madrid, verdaderamente habéis hecho que aproveche mi tiempo en la universidad; a David Expósito. iv "Ryuu ga waga teki wo kurau" Hanzo Shimada vi Abstract The Zoe virtual assistant developed by the Linux User Group from Carlos III University is a project that aims to automate various tedious tasks of the association. -

Ubuntu Kung Fu
Prepared exclusively for Alison Tyler Download at Boykma.Com What readers are saying about Ubuntu Kung Fu Ubuntu Kung Fu is excellent. The tips are fun and the hope of discov- ering hidden gems makes it a worthwhile task. John Southern Former editor of Linux Magazine I enjoyed Ubuntu Kung Fu and learned some new things. I would rec- ommend this book—nice tips and a lot of fun to be had. Carthik Sharma Creator of the Ubuntu Blog (http://ubuntu.wordpress.com) Wow! There are some great tips here! I have used Ubuntu since April 2005, starting with version 5.04. I found much in this book to inspire me and to teach me, and it answered lingering questions I didn’t know I had. The book is a good resource that I will gladly recommend to both newcomers and veteran users. Matthew Helmke Administrator, Ubuntu Forums Ubuntu Kung Fu is a fantastic compendium of useful, uncommon Ubuntu knowledge. Eric Hewitt Consultant, LiveLogic, LLC Prepared exclusively for Alison Tyler Download at Boykma.Com Ubuntu Kung Fu Tips, Tricks, Hints, and Hacks Keir Thomas The Pragmatic Bookshelf Raleigh, North Carolina Dallas, Texas Prepared exclusively for Alison Tyler Download at Boykma.Com Many of the designations used by manufacturers and sellers to distinguish their prod- ucts are claimed as trademarks. Where those designations appear in this book, and The Pragmatic Programmers, LLC was aware of a trademark claim, the designations have been printed in initial capital letters or in all capitals. The Pragmatic Starter Kit, The Pragmatic Programmer, Pragmatic Programming, Pragmatic Bookshelf and the linking g device are trademarks of The Pragmatic Programmers, LLC. -

Linux on the Road
Linux on the Road Linux with Laptops, Notebooks, PDAs, Mobile Phones and Other Portable Devices Werner Heuser <wehe[AT]tuxmobil.org> Linux Mobile Edition Edition Version 3.22 TuxMobil Berlin Copyright © 2000-2011 Werner Heuser 2011-12-12 Revision History Revision 3.22 2011-12-12 Revised by: wh The address of the opensuse-mobile mailing list has been added, a section power management for graphics cards has been added, a short description of Intel's LinuxPowerTop project has been added, all references to Suspend2 have been changed to TuxOnIce, links to OpenSync and Funambol syncronization packages have been added, some notes about SSDs have been added, many URLs have been checked and some minor improvements have been made. Revision 3.21 2005-11-14 Revised by: wh Some more typos have been fixed. Revision 3.20 2005-11-14 Revised by: wh Some typos have been fixed. Revision 3.19 2005-11-14 Revised by: wh A link to keytouch has been added, minor changes have been made. Revision 3.18 2005-10-10 Revised by: wh Some URLs have been updated, spelling has been corrected, minor changes have been made. Revision 3.17.1 2005-09-28 Revised by: sh A technical and a language review have been performed by Sebastian Henschel. Numerous bugs have been fixed and many URLs have been updated. Revision 3.17 2005-08-28 Revised by: wh Some more tools added to external monitor/projector section, link to Zaurus Development with Damn Small Linux added to cross-compile section, some additions about acoustic management for hard disks added, references to X.org added to X11 sections, link to laptop-mode-tools added, some URLs updated, spelling cleaned, minor changes. -

Part II, Window Managers and Desktop Environments
Part II Window Managers and Desktop Environments The window manager is responsible for managing application windows and application- independent behavior, such as pop-up menus appearing in the background. The window manager manages the placement, borders, and decorations of all windows, and is responsible for the look and feel of your particular X session. Desktop environments typically include an integrated window manager, some sort of control panel, applications, and a consistent look and feel across applications. The chapters in Part II, Window Managers and Desktop Environments, are: Overview This chapter provides a conceptual introduction to window managers and desktop environments and briefly surveys some of the many window managers and desktop environments available for Linux. FVWM FVWM is a traditional window manager for Linux systems. It is now into its second major version, FVWM2. Window Maker Window Maker is an elegant X11 window manager designed to give integration support to GNUstep-based applications. It emulates the look and feel of OpenStep, the NeXTSTEP GUI. Enlightenment Enlightenment, often shortened to just E, may be the most elaborate and bizarre window manager available. Enlightenment’s motto, “time to rethink everything,” provides a good indication of the uniqueness and flashiness behind Enlightenment. Using GNOME GNOME, which stands for GNU Network Object Model Environment, is a freely available desktop environment that can be used with any of several window managers, including Enlightenment and Sawfish. Using KDE KDE, the K Desktop Environment, is another freely available desktop environment. KDE includes an assortment of games and utilities, as well as an integrated suite of office productivity applications.. -

Introduction to the Enlightenment Foundation Libraries
Introduction to the Enlightenment foundation libraries. An overview of EFL Kostis Kapelonis Introduction to the Enlightenment foundation libraries.: An overview of EFL Kostis Kapelonis Abstract The target audience of this document are UNIX programmers who are interested in the Enlightenment Foundation Libraries (EFL). You must already know C programming. You will not however learn how to program using the EFL. Instead, you will learn why you should program with the EFL. If you ever wanted to evaluate the EFL but did not see any advantages over previous graphic libraries then this document is for you! Table of Contents 1. Introduction ............................................................................................................................1 A little History ...................................................................................................................1 Related documentation ......................................................................................................... 2 Obtaining the EFL libraries ................................................................................................... 2 2. The EFL structure .................................................................................................................... 4 Organization of the Libraries ................................................................................................. 4 Brief description of each EFL library ...................................................................................... 5 3. -

Christian Grothoff
Curriculum Vitae Christian Grothoff February 19, 2021 Contents 1 General Information2 1.1 Contact..............................2 1.2 Brief Biography..........................2 1.3 Education and Employment History..............2 1.4 Honors and Awards.......................3 1.5 Professional Associations.....................3 2 Research3 2.1 Publications............................3 2.2 Software Systems......................... 12 2.3 Talks and Panels......................... 14 2.4 Funding.............................. 18 3 Teaching 21 3.1 Teaching at the University of Denver.............. 21 3.2 Teaching at Technische Universit¨atM¨unchen......... 21 3.3 Teaching at BFH......................... 21 3.4 Theses supervision........................ 22 1 Christian Grothoff 2 1 General Information 1.1 Contact Bern University of Applied Sciences [email protected] Room N.474 http://grothoff.org/christian/ H¨oheweg 80 Phone (priv): +41-786926894 CH-2502 Biel-Bienne Phone (work): +41-323216488 Born February 28, 1977 in Germany. Citizen of Germany. 1.2 Brief Biography Christian Grothoff is a professor for computer network security at the Bern University of Applied Sciences, researching future Internet architectures. His research interests include compilers, programming languages, software engineering, networking, security and privacy. Previously, he was on the faculty of the Technische Universit¨atM¨unchen leading an Emmy-Noether research group in the area of computer net- works. He earned his PhD in computer science from UCLA, an M.S. in computer science from Purdue University, and both a Diplom II in mathe- matics and the first Staatsexamen in chemistry from the Bergische Univer- sit¨atGesamthochschule (BUGH) Wuppertal. 1.3 Education and Employment History 1996{2000 Diplom II (≈ M.S) in mathematics at BUGH Wuppertal 1996{2001 1. -

Linux Day 2014
INFORMAZIONE PUBBLICITARIA “Linux Day 2014”: Confartigianato sostiene l’evento Appuntamento all’Istituto Alberghetti di Imola sabato 25 ottobre Anche quest’anno Confartigianato anche nella maggior parte dei tele- Assimprese di Imola e Bologna foni cellulari e dei tablet, e in modo sostiene il “Linux Day”, in pro- meno visibile in quasi tutti i gramma sabato 25 ottobre a Imola, momenti della nostra vita, in quan- nell’aula Verde dell’Iis “Francesco to è il sistema operativo delle auto- Alberghetti”. L’evento imolese, che mobili, dei navigatori satellitari, si svolge in contemporanea in oltre delle televisioni e di moltissimi 100 diverse città a livello nazionale, elettrodomestici. è organizzato da “ImoLUG – Imola Il suo sviluppo è sostenuto da & Faenza Linux User Group” e sarà un’associazione senza fini di lucro, l’occasione per fare il punto sul la “Linux Foundation”. I “LUG”, tema dell’open source (software gruppi di persone che osservano e con codice sorgente aperto) e su diffondono i principi del software altri argomenti di informatica. Il libero, organizzano ogni anno. tema di quest’anno è “Libertà digi- tale”. L’ingresso è gratuito e aperto Programma della giornata a tutti. Mattina “Il Linux Day esiste dal 2001 e il 09:00 - “GNU/GPL v2 vs. v3” nostro intento principale resta a cura di Riccardo Corrado sempre lo stesso, avvicinare le per- 10:00 - “BackBox: WiFi Libero? sone all’informatica e ridurre il Il direttivo dell’ImoLUG, da sinistra: Riccardo Dal Fiume, Amilcare Renzi, Segretario Ti spio!” a cura di Andrea digital divide – spiega Stefano Riccardo De Luna, Paride Balestri, Stefano Ballardini. -

The GNOME Desktop Environment
The GNOME desktop environment Miguel de Icaza ([email protected]) Instituto de Ciencias Nucleares, UNAM Elliot Lee ([email protected]) Federico Mena ([email protected]) Instituto de Ciencias Nucleares, UNAM Tom Tromey ([email protected]) April 27, 1998 Abstract We present an overview of the free GNU Network Object Model Environment (GNOME). GNOME is a suite of X11 GUI applications that provides joy to users and hackers alike. It has been designed for extensibility and automation by using CORBA and scripting languages throughout the code. GNOME is licensed under the terms of the GNU GPL and the GNU LGPL and has been developed on the Internet by a loosely-coupled team of programmers. 1 Motivation Free operating systems1 are excellent at providing server-class services, and so are often the ideal choice for a server machine. However, the lack of a consistent user interface and of consumer-targeted applications has prevented free operating systems from reaching the vast majority of users — the desktop users. As such, the benefits of free software have only been enjoyed by the technically savvy computer user community. Most users are still locked into proprietary solutions for their desktop environments. By using GNOME, free operating systems will have a complete, user-friendly desktop which will provide users with powerful and easy-to-use graphical applications. Many people have suggested that the cause for the lack of free user-oriented appli- cations is that these do not provide enough excitement to hackers, as opposed to system- level programming. Since most of the GNOME code had to be written by hackers, we kept them happy: the magic recipe here is to design GNOME around an adrenaline response by trying to use exciting models and ideas in the applications. -

Titans and Trolls of the Open Source Arena
Titans and Trolls Enter the Open-Source Arena * by DEBRA BRUBAKER BURNS I. Introduction .................................................................................... 34 II. Legal Theories for Open Source Software License Enforcement ................................................................................... 38 A. OSS Licensing .......................................................................... 38 B. Legal Theories and Remedies for OSS Claims .................... 40 1. Legal Protections for OSS under Copyright and Contract Law ..................................................................... 40 Stronger Protections for OSS License under Copyright Law ................................................................... 40 2. Copyright-Ownership Challenges in OSS ....................... 42 3. Potential Legal Minefields for OSS under Patent Law ...................................................................................... 45 4. Added Legal Protection for OSS under Trademark Law ...................................................................................... 46 5. ITC 337 Action as Uncommon Legal Protection for OSS ..................................................................................... 49 III. Enforcement Within the OSS Community .................................. 49 A. Software Freedom Law Center Enforces OSS Licenses .... 50 B. Federal Circuit Finds OSS License Enforceable Under Copyright Law ......................................................................... 53 C. Commercial OSS -

Fedora Core Works--Without the Fluff That Bogs Down Other Books and Help/How-To Web Sites
Fedora Linux By Chris Tyler ............................................... Publisher: O'Reilly Pub Date: October 01, 2006 ISBN-10: 0-596-52682-2 ISBN-13: 978-0-596-52682-5 Pages: 504 Table of Contents | Index "Neither a "Starting Linux" book nor a dry reference manual, this book has a lot to offer to those coming to Fedora from other operating systems or distros." -- Behdad Esfahbod, Fedora developer This book will get you up to speed quickly on Fedora Linux, a securely-designed Linux distribution that includes a massive selection of free software packages. Fedora is hardened out-of-the-box, it's easy to install, and extensively customizable - and this book shows you how to make Fedora work for you. Fedora Linux: A Complete Guide to Red Hat's Community Distribution will take you deep into essential Fedora tasks and activities by presenting them in easy-to-learn modules. From installation and configuration through advanced topics such as administration, security, and virtualization, this book captures the important details of how Fedora Core works--without the fluff that bogs down other books and help/how-to web sites. Instead, you can learn from a concise task-based approach to using Fedora as both a desktop and server operating system. In this book, you'll learn how to: Install Fedora and perform basic administrative tasks Configure the KDE and GNOME desktops Get power management working on your notebook computer and hop on a wired or wireless network Find, install, and update any of the thousands of packages available for Fedora Perform backups, increase reliability with RAID, and manage your disks with logical volumes Set up a server with file sharing, DNS, DHCP, email, a Web server, and more Work with Fedora's security features including SELinux, PAM, and Access Control Lists (ACLs) Whether you are running the stable version of Fedora Core or bleeding-edge Rawhide releases, this book has something for every level of user. -
Debian 1 Debian
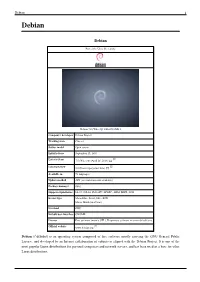
Debian 1 Debian Debian Part of the Unix-like family Debian 7.0 (Wheezy) with GNOME 3 Company / developer Debian Project Working state Current Source model Open-source Initial release September 15, 1993 [1] Latest release 7.5 (Wheezy) (April 26, 2014) [±] [2] Latest preview 8.0 (Jessie) (perpetual beta) [±] Available in 73 languages Update method APT (several front-ends available) Package manager dpkg Supported platforms IA-32, x86-64, PowerPC, SPARC, ARM, MIPS, S390 Kernel type Monolithic: Linux, kFreeBSD Micro: Hurd (unofficial) Userland GNU Default user interface GNOME License Free software (mainly GPL). Proprietary software in a non-default area. [3] Official website www.debian.org Debian (/ˈdɛbiən/) is an operating system composed of free software mostly carrying the GNU General Public License, and developed by an Internet collaboration of volunteers aligned with the Debian Project. It is one of the most popular Linux distributions for personal computers and network servers, and has been used as a base for other Linux distributions. Debian 2 Debian was announced in 1993 by Ian Murdock, and the first stable release was made in 1996. The development is carried out by a team of volunteers guided by a project leader and three foundational documents. New distributions are updated continually and the next candidate is released after a time-based freeze. As one of the earliest distributions in Linux's history, Debian was envisioned to be developed openly in the spirit of Linux and GNU. This vision drew the attention and support of the Free Software Foundation, who sponsored the project for the first part of its life.