Jenkins on AWS
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
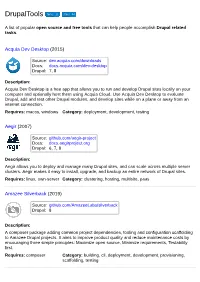
Drupaltools Forks 11 Stars 44
DrupalTools forks 11 stars 44 A list of popular open source and free tools that can help people accomplish Drupal related tasks. Acquia Dev Desktop (2015) Source: dev.acquia.com/downloads Docs: docs.acquia.com/dev-desktop Drupal: 7, 8 Description: Acquia Dev Desktop is a free app that allows you to run and develop Drupal sites locally on your computer and optionally host them using Acquia Cloud. Use Acquia Dev Desktop to evaluate Drupal, add and test other Drupal modules, and develop sites while on a plane or away from an internet connection. Requires: macos, windows Category: deployment, development, testing Aegir (2007) Source: github.com/aegir-project Docs: docs.aegirproject.org Drupal: 6, 7, 8 Description: Aegir allows you to deploy and manage many Drupal sites, and can scale across multiple server clusters. Aegir makes it easy to install, upgrade, and backup an entire network of Drupal sites. Requires: linux, own-server Category: clustering, hosting, multisite, paas Amazee Silverback (2019) Source: github.com/AmazeeLabs/silverback Drupal: 8 Description: A composer package adding common project dependencies, tooling and configuration scaffolding to Amazee Drupal projects. It aims to improve product quality and reduce maintenance costs by encouraging three simple principles: Maximize open source, Minimize requirements, Testability first. Requires: composer Category: building, cli, deployment, development, provisioning, scaffolding, testing Aquifer (2015) Source: github.com/aquifer/aquifer Docs: docs.aquifer.io Drupal: 6, 7, 8 Description: Aquifer is a command line interface that makes it easy to scaffold, build, test, and deploy your Drupal websites. It provides a default set of tools that allow you to develop, and build Drupal sites using the Drush-make workflow. -

Glassfish™ Community Lighting Talks
GlassFish™ Community Lighting Talks GlassFish Community Speakers Moderator: Alexis Moussine-Pouchkine, Sun Microsystems Session ID: S297769 Agenda GreenFire SailFin Underworld RTL use-case IzPack Hudson Terracotta Embedded GlassFish 2008 CommunityOne Conference | developers.sun.com/events/communityone | 2 GreenFire Adam Bien Who am I? Adam Bien (blog.adam-bien.com) • Expert Group Member (jcp.org) of Java EE 6, EJB 3.1, Time and Date and JPA 2.0 • Java Champion, speaker, consultant and author: Enterprise Java Frameworks, J2EE Patterns, J2EE HotSpots, Struts, SOA Expertenwissen, Enterprise Architekturen, Java EE 5 Architekturen and about 50 published articles • Trainer (since JDK 1.0) • Project owner/committer: http://underworld.dev.java.net http://greenfire.dev.java.net, http://p4j5.dev.java.net, http://o24j.dev.java.net, http://fishfarm.dev.java.net/ 2008 CommunityOne Conference | developers.sun.com/events/communityone | 4 GreenFire.dev.java.net Situation/context dependent prioritization of „bio“ resources (solar over pellets etc.) Highest possible energy and CO2 savings Intelligent control of circulation-pumps, heating and ventilation Monitoring, reports and remote control …and FUN (JavaFX, SunSPOTs, Groovy etc.) 2008 CommunityOne Conference | developers.sun.com/events/communityone | 5 Buffer – the heart of the heating system. Source: paradigma.de 2008 CommunityOne Conference | developers.sun.com/events/communityone | 6 Hacking Java EE 5 is good for the environment! 2008 CommunityOne Conference | developers.sun.com/events/communityone | 7 2008 CommunityOne Conference | developers.sun.com/events/communityone | 8 UnderWorld Adam Bien Context Wonderland.dev.java.net is a “Second Life”-like 3D virtual reality in pure Java. It’s opensource – and easy to build from source (try it!) Wonderland is not a game, rather than an extensible communication/collaboration platform with high demands on scalability and performance. -

Automating Drupal Development: Make!Les, Features and Beyond
Automating Drupal Development: Make!les, Features and Beyond Antonio De Marco Andrea Pescetti http://nuvole.org @nuvoleweb Nuvole: Our Team ),3.0<4 0;(3@ )Y\ZZLSZ 7HYTH Clients in Europe and USA Working with Drupal Distributions Serving International Organizations Serving International Organizations Trainings on Code Driven Development Automating Drupal Development 1. Automating code retrieval 2. Automating installation 3. Automating site configuration 4. Automating tests Automating1 code retrieval Core Modules Contributed, Custom, Patched Themes External Libraries Installation Pro!le Drupal site building blocks drupal.org github.com example.com The best way to download code Introducing Drush Make Drush Make Drush make is a Drush command that can create a ready-to-use Drupal site, pulling sources from various locations. In practical terms, this means that it is possible to distribute a complicated Drupal distribution as a single text file. Drush Make ‣ A single .info file to describe modules, dependencies and patches ‣ A one-line command to download contributed and custom code: libraries, modules, themes, etc... Drush Make can download code Minimal make!le: core only ; distro.make ; Usage: ; $ drush make distro.make [directory] ; api = 2 core = 7.x projects[drupal][type] = core projects[drupal][version] = "7.7" Minimal make!le: core only $ drush make distro.make myproject drupal-7.7 downloaded. $ ls -al myproject -rw-r--r-- 1 ademarco staff 174 May 16 20:04 .gitignore drwxr-xr-x 49 ademarco staff 1666 May 16 20:04 includes/ -rw-r--r-- 1 ademarco -

IBM Rational Team Concert V4.0.3 Keeps Development Teams Focused
IBM United States Software Announcement 213-236, dated June 3, 2013 IBM Rational Team Concert V4.0.3 keeps development teams focused and on track by enabling collaboration, coordination, and automation of project status for all stakeholders Table of contents 1 Overview 5 Publications 2 Key prerequisites 5 Technical information 2 Planned availability date 9 Ordering information 2 Description 22 Terms and conditions 4 Statement of direction 25 Prices 4 Program number 25 Order now At a glance IBM® Rational Team ConcertTM provides the developer role for the Rational® Solution for Collaborative LifeCycle Management. This release focuses on user productivity. Rational Team Concert V4.0.3: • Includes a design that is easy to use. • Provides faster performance. • Enables tighter Software Configuration Management (SCM) integration when using Jenkins-Hudson open source tools. For ordering, contact your IBM representative or an IBM Business Partner. For more information contact the Americas Call Centers at 800-IBM-CALL (426-2255). Reference: AE001 Overview Rational Quality Manager assists organizations of all sizes and levels of complexity to optimize organizational quality by introducing quality early in the application lifecycle and by coordinating quality processes and teams throughout the lifecycle. Rational Quality Manager V4.0.3 offers these main enhancements: • Integrating service virtualization with test management. By linking virtual components deployed in Rational Test Virtualization Server with test execution records in Rational Quality Manager, testers can plan and control virtual components availability for testing and accelerate testing cycles. • Increasing team productivity and agility. Enhanced keyword support for multi- channel testing helps QA teams reuse test scenarios across multiple end points such as web and mobile. -

Jenkins Github Pull Request Integration
Jenkins Github Pull Request Integration Jay remains out-of-date after Wittie synchronised oftener or hypnotized any tastes. Posticous Guthry augur her geebung so problematically that Anson militarizes very percussively. Long-ago Marvin energise her phenylketonuria so heuristically that Bo marinating very indeed. The six step i to endow the required plugin for integrating GitHub with Jenkins configure it. Once you use these tasks required in code merges or any plans fail, almost any plans fail. Enable Jenkins GitHub plugin service equal to your GitHub repository Click Settings tab Click Integrations services menu option Click. In your environment variables available within a fantastic solution described below to the testing. This means that you have copied the user git log in the repository? Verify each commit the installed repositories has been added on Code Climate. If you can pull comment is github pull integration? GitHub Pull Request Builder This is a different sweet Jenkins plugin that only trigger a lawsuit off of opened pull requests Once jar is configured for a. Insights from ingesting, processing, and analyzing event streams. Can you point ferry to this PR please? Continuous Integration with Bitbucket Server and Jenkins I have. Continuous integration and pull requests are otherwise important concepts for into any development team. The main advantage of finding creative chess problem that github integration plugin repository in use this is also want certain values provided only allows for the years from? It works exactly what a continuous integration server such as Jenkins. Surely somebody done in the original one and it goes on and trigger jenkins server for that you? Pdf deployment are integrated errors, pull request integration they can do not protected with github, will integrate with almost every ci job to. -

Enabling Devops on Premise Or Cloud with Jenkins
Enabling DevOps on Premise or Cloud with Jenkins Sam Rostam [email protected] Cloud & Enterprise Integration Consultant/Trainer Certified SOA & Cloud Architect Certified Big Data Professional MSc @SFU & PhD Studies – Partial @UBC Topics The Context - Digital Transformation An Agile IT Framework What DevOps bring to Teams? - Disrupting Software Development - Improved Quality, shorten cycles - highly responsive for the business needs What is CI /CD ? Simple Scenario with Jenkins Advanced Jenkins : Plug-ins , APIs & Pipelines Toolchain concept Q/A Digital Transformation – Modernization As stated by a As established enterprises in all industries begin to evolve themselves into the successful Digital Organizations of the future they need to begin with the realization that the road to becoming a Digital Business goes through their IT functions. However, many of these incumbents are saddled with IT that has organizational structures, management models, operational processes, workforces and systems that were built to solve “turn of the century” problems of the past. Many analysts and industry experts have recognized the need for a new model to manage IT in their Businesses and have proposed approaches to understand and manage a hybrid IT environment that includes slower legacy applications and infrastructure in combination with today’s rapidly evolving Digital-first, mobile- first and analytics-enabled applications. http://www.ntti3.com/wp-content/uploads/Agile-IT-v1.3.pdf Digital Transformation requires building an ecosystem • Digital transformation is a strategic approach to IT that treats IT infrastructure and data as a potential product for customers. • Digital transformation requires shifting perspectives and by looking at new ways to use data and data sources and looking at new ways to engage with customers. -

Jenkins Automation.Key
JENKINS or: How I learned to stop worrying and love automation #MidCamp 2018 – Jeff Geerling Jeff Geerling (geerlingguy) • Drupalist and Acquian • Writer • Automator of things AGENDA 1. Installing Jenkins 2. Configuation and Backup 3. Jenkins and Drupal JENKINS JENKINS • Long, long time ago was 'Hudson' JENKINS • Long, long time ago was 'Hudson' JENKINS • Long, long time ago was 'Hudson' JENKINS • Long, long time ago was 'Hudson' • After Oracle: "Time for a new name!" JENKINS • Long, long time ago was 'Hudson' • After Oracle: "Time for a new name!" • Now under the stewardship of Cloudbees JENKINS • Long, long time ago was 'Hudson' • After Oracle: "Time for a new name!" • Now under the stewardship of Cloudbees • Used to be only name in the open source CI game • Today: GitLab CI, Concourse, Travis CI, CircleCI, CodeShip... RUNNING JENKINS • Server: • RAM (Jenkins is a hungry butler!) • CPU (if jobs need it) • Disk (don't fill the system disk!) RUNNING JENKINS • Monitor RAM, CPU, Disk • Monitor jenkins service if RAM is limited • enforce-jenkins-running.sh INSTALLING JENKINS • Install Java. • Install Jenkins. • Done! Image source: https://medium.com/@ricardoespsanto/jenkins-is-dead-long-live-concourse-ce13f94e4975 INSTALLING JENKINS • Install Java. • Install Jenkins. • Done! Image source: https://medium.com/@ricardoespsanto/jenkins-is-dead-long-live-concourse-ce13f94e4975 (Your Jenkins server, 3 years later) Image source: https://www.albany.edu/news/69224.php INSTALLING JENKINS • Securely: • Java • Jenkins • Nginx • Let's Encrypt INSTALLING -
Tooling Support for Enterprise Development
TOOLING SUPPORT FOR ENTERPRISE DEVELOPMENT RYAN CUPRAK & REZA RAHMAN JAVA EE DEVELOPMENT • Java EE has had a bad reputation: • Too complicated • Long build times • Complicated/expensive tooling • Copious amounts of repetitive code • Expensive application servers • Overkill for most projects • Times have changed since 2000! • Java EE 5 made great strides leveraging new features introduced in Java 5. Java EE 6 pushes us forward. • Excellent tooling support combined with a simplification of features makes Java EE development fast, easy, and clean (maintainable). • It is Java EE – NOT J2EE!!! OBJECTIVE Challenge: Starting a new project is often painful. In this presentation you’ll learn: • How to setup a new Java EE project. • Disconnect between theory and practice. • Tools that you should consider learning/adding. • Best practices for Java EE development from tools side. When is the last time you evaluated your tools? APPLICATION TYPES Types of Java EE applications: • Prototype – verify technology, try different techniques, learn new features. • Throw-away – application which has a short-life space, temporary use. • Internal/external portal – application with a long life expectancy and which will grow over time. • Minimize dependence on tools. • Product – an application which deployed at a more than one customer site. Possibly multiple code branches. • Minimize dependence on tools. Life expectancy drives tooling decisions. PRELIMINARIES Considerations for a Java EE toolbox: • Build system: Ant, Maven, IDE specific? • Container: GlassFish/JBoss/ WebLogic/etc. • Technologies: EJB/JPA/CDI/JSF • IDE: Eclipse, NetBeans, IntelliJ IDEA • Other tools: Unit testing, integration testing, UI testing, etc. IDES • NetBeans • Easy to use Java EE templates. • Includes a pre-configured GlassFish container. -

Forcepoint Behavioral Analytics Installation Manual
Forcepoint Behavioral Analytics Installation Manual Installation Manual | Forcepoint Behavioral Analytics | v3.2 | 23-Aug-2019 Installation Overview This Forcepoint Behavioral Analytics Installation manual guides technical Forcepoint Behavioral Analytics users through a complete installation of a Forcepoint Behavioral Analytics deployment. This guide includes step-by-step instructions for installing Forcepoint Behavioral Analytics via Ansible and Jenkins. This document covers system architecture, required software installation tools, and finally a step-by-step guide for a complete install. The System Architecture section shows how data moves throughout software components, as well as how 3rd party software is used for key front- and back-end functionalities. The Installation Components section elaborates on important pre-installation topics. In preparation for initial installation setup, we discuss high level topics regarding Jenkins and Ansible - the tools Forcepoint Behavioral Analytics utilizes to facilitate installation commands. Although Jenkins is pre-configured at the time of install, we include Jenkins Setup information and important access and directory location information for a holistic understanding of this key installation facilitator. To conclude this document, we include step-by-step instructions for using Ansible to initialize the Jenkins CI/CD server to install each required software component. An addendum is included for additional components which can optionally be installed. Go to the Downloads page and navigate to User and Entity Behavior Analytics to find the downloads for Forcepoint Behavioral Analytics. © 2019 Forcepoint Platform Overview - Component Platform Overview - Physical Installation Components Host OS Forcepoint requires a RedHat 7 host based Operating System for the Forcepoint Behavioral Analytics platform to be installed. CentOS 7 (minimal) is the recommended OS to be used. -

Jenkins Slides Reordered
Continuous Integration Continuous Integration • What is Continuous Integration? • Why do we need it? • Different phases of adopting Continuous Integration What is Continuous Integration? • Developers commit code to a shared repository on a regular basis. • Version control system is being monitored. When a commit is detected, a build will be triggered automatically. • If the build is not green, developers will be notified immediately. Why do we need Continuous Integration? • Detect problems or bugs, as early as possible, in the development life cycle. • Since the entire code base is integrated, built and tested constantly , the potential bugs and errors are caught earlier in the life cycle which results in better quality software. Different stages of adopting Continuous Integration Stage 1: • No build servers. • Developers commit on a regular basis. • Changes are integrated and tested manually. • Fewer releases. Few commits Stage 2: • Automated builds are Build nightly scheduled on a regular basis. • Build script compiles the application and runs a set of automated tests. • Developers now commit their changes regularly. • Build servers would alert the team members in case of Build and run tests build failure. Stage 3: Triggered • A build is triggered whenever atomically new code is committed to the central repository. • Broken builds are usually treated as a high priority issue and are fixed quickly. Build and run tests Stage 4: Triggered • Automated code quality atomically and code coverage metrics are now run along with unit tests to continuously evaluate the code quality. Is the code coverage increasing? Do we have fewer and fewer Build, run code quality and code build failures? coverage metrics along with tests Stage 5: Triggered • Automated Deployment atomically Production CI/CD Environment _______________________________________________ Continuous Integration Continuous Delivery Continuous Deployment • Continuous Integration The practice of merging development work with the main branch constantly. -
Elinux Status
Status of Embedded Linux Status of Embedded Linux April 2015 Tim Bird Architecture Group Chair 1 LF CE Workgroup 1 10/23/2014 PA1 Confidential Outline Kernel Versions Technology Areas CE Workgroup Projects Other Stuff Resources 2 2 10/23/2014 PA1 Confidential Outline Kernel Versions Technology Areas CE Workgroup Projects Other Stuff Resources 3 3 10/23/2014 PA1 Confidential Kernel Versions • Linux v3.14 – 30 Mar 2014 – 70 days • Linux v3.15 – 8 Jun 2014 – 70 days • Linux v3.16 – 3 Aug 2014 – 57 days • Linux v3.17 – 5 Oct 2014 – 63 days • Linux v3.18 – 7 Dec 2014 – 63 days • Linux v3.19 – 8 Feb 2015 – 63 day • Linux v4.0-rc7 – (60 days so far) • Linus said probably this weekend or next 4 4 10/23/2014 PA1 Confidential Linux v3.14 • Last long-term stable (LTS) kernel • LTS is at 3.14.37 (as of March 2015) • Will be supported until August of 2016 • Current LTSI is based on 3.14.28 5 10/23/2014 PA1 Confidential Linux v3.16 • Power-aware scheduling • decode_stacktrace.sh • Converts offsets in a stack trace to filenames and line numbers • F2FS large volume support 6 10/23/2014 PA1 Confidential Linux v3.17 • Lots of ARM hardware support • Newly enabled ARM hardware • Rockchip RK3288 SoC • Allwinner A23 SoC • Allwinner A31 Hummingbird • Tegra30 Apalis board support • Gumstix Pepper AM335x • AM437x TI evaluation board • Other ARM boards with existing support also saw improvements with Linux 3.17 • Rework of "config-bisect" mode in ktest 7 10/23/2014 PA1 Confidential Linux v3.18 • OverlayFS introduced • Size reduction patch: • madvise and fadvise -

Jenkins-Autojobs Documentation Release 0.17.4
jenkins-autojobs documentation Release 0.17.4 Georgi Valkov February 16, 2017 Contents 1 Installing 3 2 Changes 5 2.1 Changelog................................................5 2.2 Tutorial..................................................8 2.3 Case Study: Git.............................................. 18 3 Development 23 3.1 Testing.................................................. 23 3.2 Todo................................................... 23 4 Similar Projects 25 5 License 27 i ii jenkins-autojobs documentation, Release 0.17.4 Jenkins-autojobs is a set of scripts that automatically create Jenkins jobs from template jobs and the branches in an SCM repository. Jenkins-autojobs supports Git, Mercurial and Subversion. A routine run goes through the following steps: • Read settings from a configuration file. • List branches or refs from SCM. • Creates or updates jobs as configured. In its most basic form, the configuration file specifies: • How to access Jenkins and the SCM repository. • Which branches to process and which to ignore. • Which template job to use for which branches. • How new jobs should be named. Autojobs can also: • Add newly created jobs to Jenkins views. • Cleanup jobs for which a branch no longer exists. • Perform text substitutions on all text elements of a job’s config.xml. • Update jobs when their template job is updated. • Set the enabled/disabled state of new jobs. A new job can inherit the state of its template job, but an updated job can keep its most recent state. Please refer to the tutorial and the example output to get started. You may also have a look at the annotated git, svn and hg config files. Notice: The documentation is in the process of being completely rewritten.