Palmist: a Tool to Log Palm System Activity (Under the Direction of SURENDAR CHANDRA)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
PDA Users Guide
130 Family of Seismic Recorders PFC_130 Users Guide (Version 1.2.4.40) Refraction Technology PFC_130 Users Guide 130-PFC-001-K December 18, 2006 Refraction Technology, Inc. 1600 Tenth Street, Suite A Plano, Texas 75074 USA Voice: 214-440-1265 Fax: 972-578-0045 EMAIL: [email protected] FTP: ftp.reftek.com WWW: http://reftek.com ©Copyright 2003-2006 Refraction Technology, Inc. All rights reserved. Printed in USA ii 130-PFC-001-K PFC_130 Users Guide Preface All references to a PDA in this guide refer to any type of device that is compatible with the Palm™ operating system (OS) with RS232 (i.e., Palm IIIe™, Palm IIIxe™, Palm V™, Palm VII™, Palm M105™, Handspring Visor™, TRG Pro™, etc.) REF TEK Support and update notifications As a valued user of REF TEK equipment we would like to provide the best support possible by keeping you up to date with our product updates. If you would like to be notified of any REF TEK product updates please spend a couple of minutes to register with the reftek customer support team. To Register, either send an email to [email protected] giving us your name and REF TEK product you currently have or fill out our online registration form at www.reftek.com/registration Once we register your contact we will only send necessary notifications via email. The same notifications will be shown on our website’s www.reftek.com/support page Thanks, Your REF TEK support team PFC_130 Users Guide 130-PFC-001-K iii Revision History Rev Date Reason for change Affected Pages 0.1 1/12/02 Initial release A 10/04/02 Release of 1.0 130 -

Die Meilensteine Der Computer-, Elek
Das Poster der digitalen Evolution – Die Meilensteine der Computer-, Elektronik- und Telekommunikations-Geschichte bis 1977 1977 1978 1979 1980 1981 1982 1983 1984 1985 1986 1987 1988 1989 1990 1991 1992 1993 1994 1995 1996 1997 1998 1999 2000 2001 2002 2003 2004 2005 2006 2007 2008 2009 2010 2011 2012 2013 2014 2015 2016 2017 2018 2019 2020 und ... Von den Anfängen bis zu den Geburtswehen des PCs PC-Geburt Evolution einer neuen Industrie Business-Start PC-Etablierungsphase Benutzerfreundlichkeit wird gross geschrieben Durchbruch in der Geschäftswelt Das Zeitalter der Fensterdarstellung Online-Zeitalter Internet-Hype Wireless-Zeitalter Web 2.0/Start Cloud Computing Start des Tablet-Zeitalters AI (CC, Deep- und Machine-Learning), Internet der Dinge (IoT) und Augmented Reality (AR) Zukunftsvisionen Phasen aber A. Bowyer Cloud Wichtig Zählhilfsmittel der Frühzeit Logarithmische Rechenhilfsmittel Einzelanfertigungen von Rechenmaschinen Start der EDV Die 2. Computergeneration setzte ab 1955 auf die revolutionäre Transistor-Technik Der PC kommt Jobs mel- All-in-One- NAS-Konzept OLPC-Projekt: Dass Computer und Bausteine immer kleiner, det sich Konzepte Start der entwickelt Computing für die AI- schneller, billiger und energieoptimierter werden, Hardware Hände und Finger sind die ersten Wichtige "PC-Vorläufer" finden wir mit dem werden Massenpro- den ersten Akzeptanz: ist bekannt. Bei diesen Visionen geht es um die Symbole für die Mengendarstel- schon sehr früh bei Lernsystemen. iMac und inter- duktion des Open Source Unterstüt- möglichen zukünftigen Anwendungen, die mit 3D-Drucker zung und lung. Ägyptische Illustration des Beispiele sind: Berkley Enterprice mit neuem essant: XO-1-Laptops: neuen Technologien und Konzepte ermöglicht Veriton RepRap nicht Ersatz werden. -

1 Star Trac Pro Partner – Training Partner Operations Manual Table of Contents I. Introduction II. Selecting Workout Partner
Star Trac Pro Partner – Training Partner Operations Manual Table of Contents I. Introduction II. Selecting Workout Partner a. Creating a Custom Workout III. Creating a Pro or Elite Treadmill Custom Workout a. Naming Your Workout b. Entering Weight/Time c. Designing Your Incline Profile d. Designing Your Speed Profile IV. Creating a Pro Bike Custom Workout a. Naming Your Workout b. Entering Weight/Time c. Designing Your Resistance Profile V. Accessing a Custom Workout VI. Beaming a Custom Workout a. Beaming to a Pro or Elite Treadmill b. Beaming to a Pro Bike c. Beaming to a PDA Device VII. Editing a Custom Workout VIII. Deleting a Custom Workout IX. Reviewing a Completed Workout X. Collecting an Existing Workout from a Pro or Elite Treadmill or Pro Bike XI. Appendix A: List of PDAs Compatible with Pro Partner 1 I. Introduction Thank you for choosing Star Trac for your fitness needs. Are you ready to take your clients’ workout to a new level? The Star Trac Pro Partner software program will make your Palm-powered PDA (Personal Digital Assistant) an integral part of your personal training experience when using a Star Trac Pro or Elite Treadmill or Pro Bike. Personalized workouts and tracking client workout data are now all in the palm of your hand! In this manual you will learn how to use the Training Partner application to design custom workouts and track workout information for your clients for a more personal approach. It’s simple! Just follow the steps in this user manual and you’re one step closer to making your personal training more efficient. -

Palm Covers4
ANNUAL REPORT 2002 < leadership, strength and commitment > the palm economy Through the success of our Palm OS® platform, Palm has created a large ecosystem of companies that create and sell a variety of software applications, peripherals and accessories for Palm OS based devices. This thriving community offers a wealth of solutions for consumer, professional and enterprise users and remains one of the key components in our value proposition to our present and future customers. < 225,000+ developers* and 14,000+ applications* > *As of 7/2002 Peripherals and expansion cards sold separately. As Palm started FY ’02, we faced three fundamental • We continued to enhance pro forma operating results challenges: throughout the year with two consecutive quarters of gross margini improvements and four consecutive • Competing business strategies: While we had begun quarters of operating expenseii improvements. Pro forma the process of licensing our Palm OS software to hand- gross margini grew from a low of 20% in Q2 FY ‘02 to held manufacturers to expand the Palm Economy, the 35% in Q4 FY ‘02, while pro forma operating expensesii perceived lack of independence and the opportunistic have declined by 36% from the end of Q4 FY ’01 to nature of our licensing activities limited the potential of the end of Q4 FY ’02. both our Palm Solutions business and our Palm OS software business and blurred the focus and clarity of We made the strategic decision to commit ourselves fully purpose of each; to the operating system software licensing business. This decision was anchored in the fundamental belief that • Operational problems: We needed to improve supply handheld devices will become part of our daily life, much chain management and product development. -
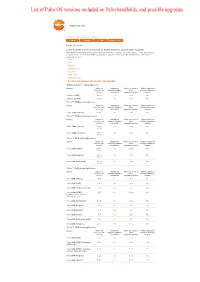
List of Palm OS Versions Included on Palm Handhelds, and Possible Upgrades
List of Palm OS versions included on Palm handhelds, and possible upgrades www.palm.com < Home < Support < Knowledge Library Article ID: 10714 List of Palm OS versions included on Palm handhelds, and possible upgrades Palm OS® is the operating system that drives Palm devices. In some cases, it may be possible to update your device with ROM upgrades or patches. Find your device below to see what's available for you: Centro Treo LifeDrive Tungsten, T|X Zire, Z22 Palm (older) Handspring Visor Questions & Answers about Palm OS upgrades Palm Centro™ smartphone Device Palm OS Handheld Palm OS version Palm Desktop & version (out- Upgrade/Update after HotSync Manager of-box) available? upgrade/update update Centro (AT&T) 5.4.9 No N/A No Centro (Sprint) 5.4.9 No N/A No Treo™ 755p smartphone Device Palm OS Handheld Palm OS version Palm Desktop & version (out- Upgrade/Update after HotSync Manager of-box) available? upgrade/update update Treo 755p (Sprint) 5.4.9 No N/A No Treo™ 700p smartphones Device Palm OS Handheld Palm OS version Palm Desktop & version (out- Upgrade/Update after HotSync Manager of-box) available? upgrade/update update Treo 700p (Sprint) Garnet Yes N/A No 5.4.9 Treo 700p (Verizon) Garnet No N/A No 5.4.9 Treo™ 680 smartphones Device Palm OS Handheld Palm OS version Palm Desktop & version (out- Upgrade/Update after HotSync Manager of-box) available? upgrade/update update Treo 680 (AT&T) Garnet Yes 5.4.9 No 5.4.9 Treo 680 (Rogers) Garnet No N/A No 5.4.9 Treo 680 (Unlocked) Garnet No N/A No 5.4.9 Treo™ 650 smartphones Device Palm OS -

Quartus Handheld Software: Discussion Forum: General
This document holds all the Quartus Handheld Software discussion forum messages from March 17, 2000 to 6:31pm, December 17, 2000. The links in the document all work -- but please don't try and post new messages to the Forum via the buttons in this document, as the subject threads may eventually be archived from the web site. Enjoy! Neal Bridges Quartus Handheld Software http://www.quartus.net Discussion Forum General December 17 - 06:31 pm [236] Quartus Forth (PalmOS version) December 17 - 04:20 pm [2833] Questions and discussion about the Quartus Forth on-board compiler for Palm/Visor/WorkPad handhelds. Quartus Forth (Royal daVinci version) April 11 - 09:15 pm [19] Questions and discussion about the Royal daVinci version of the Quartus Forth on-board compiler. Other Quartus Products December 17 - 02:12 pm [25] All other (non-Forth) Quartus products. Everything else! December 5 - 02:37 pm [105] Anything you'd like to talk about! Back to the Quartus Home Page NOTE: When posting Forth source code, to preserve indentation, format it using the "\pre{}" tag like this: \pre{ : hello \ A simple message: ." Hello World!" 10 0 do i . loop cr ; } If you wish to include a } character, enter it as: \} General Quartus Handheld Software: Discussion Forum: General ● Archive of the forum 12/17 06:31pm [2] ● Manual in Doc or TealDoc format 12/14 04:23pm [3] ● Starting New Project 12/10 06:59am [2] ● PalmSource 2000 12/14 12:38am [8] ● Easy Data Input From Paper 12/12 03:56pm [11] ● IBM Palm Devices 12/7 03:44am [3] ● Message Archives temporarily unavailable -

Forensic Analysis of Digital Evidence from Palm Personal Digital Assistants
Graduate Theses, Dissertations, and Problem Reports 2004 Forensic analysis of digital evidence from Palm Personal Digital Assistants Christopher M. McNemar West Virginia University Follow this and additional works at: https://researchrepository.wvu.edu/etd Recommended Citation McNemar, Christopher M., "Forensic analysis of digital evidence from Palm Personal Digital Assistants" (2004). Graduate Theses, Dissertations, and Problem Reports. 1550. https://researchrepository.wvu.edu/etd/1550 This Thesis is protected by copyright and/or related rights. It has been brought to you by the The Research Repository @ WVU with permission from the rights-holder(s). You are free to use this Thesis in any way that is permitted by the copyright and related rights legislation that applies to your use. For other uses you must obtain permission from the rights-holder(s) directly, unless additional rights are indicated by a Creative Commons license in the record and/ or on the work itself. This Thesis has been accepted for inclusion in WVU Graduate Theses, Dissertations, and Problem Reports collection by an authorized administrator of The Research Repository @ WVU. For more information, please contact [email protected]. Forensic Analysis of Digital Evidence from Palm Personal Digital Assistants Christopher M. McNemar Thesis submitted to the College of Engineering and Mineral Resources at West Virginia University in partial fulfillment of the requirements for the degree of Master of Science In Computer Science With Emphasis On Computer Forensics Roy S. Nutter, Jr., Ph.D., Chair John M. Atkins, Ph.D. Bojan Cukic, Ph.D. Lane Department of Computer Science and Electrical Engineering Morgantown, West Virginia 2004 Keywords: PDA Forensics, Palm Forensics, Digital Forensics, Digital Image Analysis, Digital Evidence Copyright 2004 Christopher M. -

OAG.Com Launches Wireless Travel Access Submitted By: Outrider Monday, 20 November 2000
OAG.com launches Wireless Travel Access Submitted by: Outrider Monday, 20 November 2000 News- Free trial of new mobile information service, OAG Mobile Register Today for a free 90 day trial at http://www.oag.com OAG Mobile Fact Sheet Overview "OAG Mobile offers wireless access to up-to-date travel information via wireless web-enabled phones and personal digital assistants (PDAs). The overall vision of OAG Mobile is to empower the frequent traveler to fully manage their travel arrangements while out of the office using the OAG travel application, via the mobile device of their choice. "OAG Mobile offers wireless device users access to the most comprehensive and independent flight schedule information available - including millions of direct and connecting flights from over 800 airlines. * OAG, the world leader in independent business travel information, offers a complete and authoritative bank of airline and travel information which can be accessed by the frequent business traveler through the new OAG Mobile service supported by OAG.com. * OAG Mobile offers travelers access to OAG airline schedules via web-enabled mobile phones, and personal digital assistants (PDAs). * Unlike other travel notification services, any registered OAG.com vistior can use the OAG E-Notification service, regardless of where or how the flight is booked. * Key Messages for OAG Mobile : OAG is a visionary leader in providing portable, comprehensive travel information that empowers travelers to make better travel decisions around the clock. OAG Mobile is a critical tool for frequent complex travelers, giving them unparalleled power over their travel choices. How to Access OAG Mobile Page 1 Mobile Devices * All wireless web enabled phones and PDAs. -

Palm/Palm Pilot: Personal Experiences and Tips
Palm/Palm Pilot: Personal Experiences and Tips http://www.faughnan.com/palm.html Faughnan Home | FP Web Starter | Contact Info | Glossaries and Links | Site Contents Palm/Palm Pilot: Personal Experiences and Tips Contents Introduction Palm m515 Problems Impressions Palm IIIxe: A Sad Story Installation Bugs SONY Clie PEG-SL10 Using COM3 for Synching Dot Commands IR HotSync with Windows 2000 Synchronizing a Palm Vx with an OS X Security iBook Software Synchronizing with Outlook/Exchange Backups and User File Versioning Input Palm Desktop 4.0 Styli Keyboard Palm Security WWAN Communication and Cell Phones Graffiti Withdrawal and TealScript What went wrong? The Tungsten E: My Impressions Repairs, Service and Support Palm V/Vx and its Problems Links (links) Palm Vx Lithium Battery Life Expectancy Digitizer Drift History Cannot Hot Sync: No User Identified Footnotes Palm V/Vx Travel Kit Problems: Defective Design Palm V/Vx (and m500/505?) Power Switch Failure (EasyLaunch) Broken Vx Cradle Tabs rev: 13 December, 2003 Introduction A resource page for Palm OS based devices (device formerly known as the PalmPilot[11]) based on my personal experience. It will be of most interest to non-developer heavy users of the Palm and licensee devices. Older versions of this page are archived in 020822_PalmPageArchive.pdf. This is a page of useful fragments, not a unified document. It will most often be found during Google searches. Impressions The Palm III, made in the USA, was a groundbreaking devices. It was reliable, relatively inexpensive, the right size (actually the Palm Vx is the right size, the Palm III is close), and had market share. -

Palmfahrschule
PalmFahrSchule Anhang A - Geräteliste verschiedener Hersteller Palm (Handhelds) OS Version Speicher Kompatibel Palm Pilot 1000 Palm OS 1.0 128 Kb nein Palm Pilot 5000 Palm OS 1.0 512 Kb nein Palm Pilot Personal Palm OS 1.0 512 Kb nein Palm Pilot Professional Palm OS 2.0 2 Mb nein Palm III Palm OS 3.0 2 Mb nein Palm IIIc Palm OS 3.5 8 Mb Palm IIIe Palm OS 3.3 2 Mb nein Palm IIIx Palm OS 3.1 4 Mb nein Palm IIIxe Palm OS 3.5 8 Mb Palm V Palm OS 3.0.1 / 3.1 2 Mb nein Palm Vx Palm OS 3.5 8 Mb Palm VII Palm OS 3.2 2 Mb nein Palm VIIx Palm OS 3.3 / 3.5 / 3.5.3 8 Mb nein Palm m100 Palm OS 3.5 2 Mb Palm m105 Palm OS 3.5.1 8 Mb Palm m125 Palm OS 4.0 8 Mb Palm m130 Palm OS 4.0/4.1 8 Mb Palm m500 Palm OS 4.0 8 Mb Palm m505 Palm OS 4.0 / 4.1 8 Mb Palm m515 Palm OS 4.1 16 Mb Palm i705 Palm OS 4.1 8 Mb Zire Palm OS 4.1 2 Mb Zire 119 ? Zire m150 Palm OS 4.1 2 Mb Zire 21 Palm OS 5.2.8 8 Mb Zire 31 Palm OS 5.2.8 16 Mb Zire 71 Palm OS 5.2.1 16 Mb (14 Mb nutzbare Kapazität) Zire 72 Palm OS 5.2.8 32 Mb (24 Mb nutzbare Kapazität) Palm Z22 Palm OS Garnet 5.4.9 32 Mb (20 Mb nutzbare Kapazität) Palm T|X Handheld (tx) Palm OS 5.4.9 128 Mb Flash-RAM, ca. -

Die Geschichte Der Digitalen Evolution Bezugsquelle
Die Geschichte der digitalen Evolution Bezugsquelle: www.computerposter.ch 1994 1995 1996 1997 1998 1999 2000 2001 2002 2003 2004 2005 2006 2007 2008 2009 2010 2011 2012 2013 2014 2015 2016 2017 und ... Phasen Online-Zeitalter Internet-Hype Wireless-Zeitalter Web 2.0/Start Cloud Computing Start des Tablet-Zeitalters Cognitive Computing und Internet der Dinge (IoT) Zukunftsvisionen Jobs mel- All-in-One- NAS-Konzept OLPC-Projekt: A. Bowyer Cloud Wichtig Dass Computer und Bausteine immer kleiner, det sich Konzepte Start der entwickelt Computing für die AI- schneller, billiger und energieoptimierter werden, Hardware mit dem werden Massenpro- den ersten Akzeptanz: ist bekannt. Bei diesen Visionen geht es um iMac und inter- duktion des Open Source Unterstüt- mögliche zukünftige Anwendungen, welche sich mit neuem essant: XO-1-Laptops: 3D-Drucker zung und mit neuen Technologien und Konzepten realisie- Veriton RepRap nicht Ersatz ren lassen. Diese basieren auf Resultaten aus Logo Millennium Bug (Datumfehler): Ver- Haupteinsatz: Apple Watch: Jetzt kaufbar (April). FP2 (Acer), (Replicating von Spezia- Forschung und Entwicklung, welche man in den zurück. Uruguay, Peru, Sensoren: Herzfrequenz, Lage, IBM lanciert die Aptiva-Linie für PC im hinderung des IT-Horrorszenario Rapid-Pro- AI (Artificial Intelligence) wird immer listen. weltweiten Labors erarbeitet. iMac wird verschlingt 800 bis 1’000 Mia $. Mexico, Ruan- Beschleunigung. Wi-Fi, Bluetooth - Systeme den Heimmarkt. Compaq beherrscht als Markt- Bildschirm totyper) als wichtiger: Computer-Magazine 1. kommerzieller Einsatz von Watson Cognitive Computing als Ergänzung IBM ThinkPad TransNote: 27.1.2010: Steve Jobs präsentiert Das IBM-Programm Watson 4.0, NFC, S1-CPU, 10’000 Apps. leader das PC-Business. -

Handbook for the Palm III™ Organizer Copyright
Handbook for the Palm III™ Organizer Copyright Copyright © 1998 3Com Corporation or its subsidiaries. All rights reserved. 3Com, the 3Com logo, Palm Computing, Palm Modem, Graffiti, and HotSync are registered trade- marks, and PalmPilot, Palm III, Palm OS, Palm, the Palm Computing Platform logo, the Palm III logo, and the HotSync logo are trademarks of Palm Computing, Inc., 3Com Corporation or its subsidiaries. Other product and brand names may be trademarks or registered trademarks of their respective owners. Disclaimer and Limitation of Liability 3Com Corporation and its subsidiaries assume no responsibility for any damage or loss resulting from the use of this handbook. 3Com Corporation and its subsidiaries assume no responsibility for any loss or claims by third parties which may arise through the use of this software. 3Com Corporation and its subsidiaries assume no responsibility for any damage or loss caused by deletion of data as a result of malfunction, dead battery, or repairs. Be sure to make backup cop- ies of all important data on other media to protect against data loss. Important: Please read the 3Com End User Software License Agreement contained in this handbook before using the accompanying software program(s). Using any part of the software indicates that you accept the terms of the 3Com End User Software License Agreement. 3.5" Software Diskettes Available Palm™ Desktop software is supplied on a CD-ROM disc. If you do not have access to a CD-ROM drive for your computer, you may download the Palm Desktop software from http://www.palm.com. Alternatively, you can order 3.5" diskettes by completing and mailing the diskette order card supplied in the Palm III™ organizer product package, or call to order the diskettes.