Authenticated Out-Of-Band Communication Over Social Links
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Use of Compressed Video for Distance Learning: from Middle School to Senior Citizens
THE USE OF COMPRESSED VIDEO FOR DISTANCE LEARNING: FROM MIDDLE SCHOOL TO SENIOR CITIZENS Al P. Mizell Nova Southeastern University 362 Fairway Circle Weston, FL 33326 [email protected] Introduction A review of a ten-year project using ISDN Compressed Video to connect middle and high schools around the world for monthly explorations of a variety of topics ranging from music concerts to joint science experiments. At the other extreme, the use of webcams over the Internet in Skype, ooVoo, Logitech, and Google Video to make free video conferencing calls by limited income senior citizens in a Quality of Life project illustrates the distance compressed video has come. Finally, the use of video conferencing in Elluminate in Blackboard for graduate online courses is described. Participants will be invited to use their desktop units to explore some of these options and video clips during the session. The SAXophone project For approximately ten years, “Students Around the World eXchanging over the phone” (SAXophone), provided middle and high school students around the world with the opportunity to meet and interact with students from other cultures and societies. The SAXophone project was sponsored by Nova Southeastern University and the Broward County, Florida BECON Distance Learning Center from 1995 until 2005. The project began at the September1995 PictureTel User Group Annual Conference in Nashville, Tennessee. Three individuals attending the conference from different parts of the world met each other at lunch for the first time and began discussing ways to use compressed video equipment that they had recently received. The project began, as described by Mizell (1997), when Colonel Bent Kroon from the Swedish Military College, Mr. -

Android (Operating System) 1 Android (Operating System)
Android (operating system) 1 Android (operating system) Android Home screen displayed by Samsung Nexus S with Google running Android 2.3 "Gingerbread" Company / developer Google Inc., Open Handset Alliance [1] Programmed in C (core), C++ (some third-party libraries), Java (UI) Working state Current [2] Source model Free and open source software (3.0 is currently in closed development) Initial release 21 October 2008 Latest stable release Tablets: [3] 3.0.1 (Honeycomb) Phones: [3] 2.3.3 (Gingerbread) / 24 February 2011 [4] Supported platforms ARM, MIPS, Power, x86 Kernel type Monolithic, modified Linux kernel Default user interface Graphical [5] License Apache 2.0, Linux kernel patches are under GPL v2 Official website [www.android.com www.android.com] Android is a software stack for mobile devices that includes an operating system, middleware and key applications.[6] [7] Google Inc. purchased the initial developer of the software, Android Inc., in 2005.[8] Android's mobile operating system is based on a modified version of the Linux kernel. Google and other members of the Open Handset Alliance collaborated on Android's development and release.[9] [10] The Android Open Source Project (AOSP) is tasked with the maintenance and further development of Android.[11] The Android operating system is the world's best-selling Smartphone platform.[12] [13] Android has a large community of developers writing applications ("apps") that extend the functionality of the devices. There are currently over 150,000 apps available for Android.[14] [15] Android Market is the online app store run by Google, though apps can also be downloaded from third-party sites. -

Polycom UC Software with Skype for Business - Deployment Guide on Polycom Voice Support
DEPLOYMENT GUIDE UC Software 5.7.0 | April 2019 | 3725-49078-020B Polycom® UC Software with Skype for Business Copyright© 2019, Polycom, Inc. All rights reserved. No part of this document may be reproduced, translated into another language or format, or transmitted in any form or by any means, electronic or mechanical, for any purpose, without the express written permission of Polycom, Inc. 6001 America Center Drive San Jose, CA 95002 USA Trademarks Polycom®, the Polycom logo and the names and marks associated with Polycom products are trademarks and/or service marks of Polycom, Inc. and are registered and/or common law marks in the United States and various other countries. All other trademarks are property of their respective owners. No portion hereof may be reproduced or transmitted in any form or by any means, for any purpose other than the recipient's personal use, without the express written permission of Polycom. Disclaimer While Polycom uses reasonable efforts to include accurate and up-to-date information in this document, Polycom makes no warranties or representations as to its accuracy. Polycom assumes no liability or responsibility for any typographical or other errors or omissions in the content of this document. Limitation of Liability Polycom and/or its respective suppliers make no representations about the suitability of the information contained in this document for any purpose. Information is provided "as is" without warranty of any kind and is subject to change without notice. The entire risk arising out of its use remains with the recipient. In no event shall Polycom and/or its respective suppliers be liable for any direct, consequential, incidental, special, punitive or other damages whatsoever (including without limitation, damages for loss of business profits, business interruption, or loss of business information), even if Polycom has been advised of the possibility of such damages. -

From the President… the International Cwops Newsletter May 2012 Issue
May 2012 The International CWops Newsletter Issue No. 28 From the president… CW Academy Our recent press release that appeared on QRZ.COM and eHam resulted in 150 new CWops “CWT” students signing up! That speaks well for the 9, 23 May 2012 interest by those wishing to learn CW or Start time: improve their skill. Now it’s time for - 1300Z members to sign up as well – as advisors. - 1900Z - 0300Z (10/24 May.) 1-hour each session Jay, W5JQ, and Jack, W0UCE, have done a Exchange name/number (members) fantastic job in organizing classes which run Exchange name/SPC (non-members) for two months. They have established a CWops “neighborhood” vehicle to allow group web chats for both Look for CWops on 1.818, 3.528, 7.028, 10.118, classes as well as support (www.oovoo.com – 14.028, 18.078, 21.028, 24.908, 28.028, 50.098 it’s free) and some excellent guidelines to help advisors. CWops Officers and Director Officers President: Pete Chamalian, W1RM Go to www.cwops.org/cwacademy2.html for Vice President: Art Suberbielle, KZ5D more details. Secretary: Jim Talens, N3JT Treasurer: Craig Thompson, K9CT Directors: If you can’t devote time to being an advisor, Bert Donn, G3XSN how about getting on the bands on the sub- Vidi La Grange, ZS1EL band suggested (3.550-3.570, 7.050-7.070, Nodir Tursoon-Zade , EY8MM 14.050-14.070, 21.050-21.070 and 28.050- Webmaster: John Miller, K6MM 28.070) and look for students. Or, just call CQ Editor/Publisher: Rob Brownstein, K6RB CWA and see who comes back. -

The Google+ Hangout: a Marketing Tool for Your Dermatology Practice
MARKETING MATTERS The Google+ Hangout: A Marketing Tool For Your Dermatology Practice Dermatology marketers can employ this tool effectively to promote their practices or simply use it as a powerful and free communication tool. BY NAREN ARULRAJAH WITH VIKAS VIJ he Google Plus social network has introduced a promising and innovative new tool for participants to virtually connect. Called the Google Hangout, it allows up to 10 people at the same time to con- nectT via Google+ to chat, share videos, and interact. AN OVERVIEW OF GOOGLE HANGOUTS Google Hangouts has emerged as a popular live stream- ing video platform over a short period of time. However, the technology is still fairly new, and many people are unaware about how to use it to their business or personal advantage. Dermatology marketers can employ this tool effectively to promote their practices or simply use it as a if they like. The quality of audio and video is superior. To powerful and free communication tool. Two primary types record private sessions on hangout, you will be required of Hangouts are Hangouts and Hangouts on Air. to use ScreenFlow or Camtasia. As a dermatologist, you Hangouts are commonly used for personal video chats can use these sessions for meetings with your staff, training with another individual or a group of people. These private new members of your team, or meeting with vendors or meetings are only visible to the people who have been other people connected to your practice. invited to them and are not recorded to YouTube. On the When you launch a hangout on air, you are in a position other hand, Hangouts on Air are open to public view and to create a group chat or give an individual presentation for get recorded automatically to the YouTube channel that the sake of your potential patients, fellow dermatologists, is connected with your Google+ account. -

Google Talk: Is It Ready for the Enterprise?
Research Publication Date: 16 April 2009 ID Number: G00166834 Google Talk: Is It Ready for the Enterprise? David Mario Smith, James Lundy This report discusses the Google Talk instant messaging product and its suitability for enterprises. This is important for companies which are looking at alternatives to IBM and Microsoft for messaging and collaboration. Key Findings • Google Talk IM is based on the Extensible Messaging and Presence Protocol (XMPP) and Jingle protocols. • To get enterprise-level support for Google Talk, companies have to purchase the full Google Apps Premier Edition (GAPE) suite. • Enterprise users are already using the Google Talk and Gmail free services. Recommendations • Enterprises making collaboration decisions should include the Google Apps portfolio as part of an effort to compare the economics of their current incumbent provider vs. similar services provisioned in the cloud. © 2009 Gartner, Inc. and/or its Affiliates. All Rights Reserved. Reproduction and distribution of this publication in any form without prior written permission is forbidden. The information contained herein has been obtained from sources believed to be reliable. Gartner disclaims all warranties as to the accuracy, completeness or adequacy of such information. Although Gartner's research may discuss legal issues related to the information technology business, Gartner does not provide legal advice or services and its research should not be construed or used as such. Gartner shall have no liability for errors, omissions or inadequacies in the information contained herein or for interpretations thereof. The opinions expressed herein are subject to change without notice. WHAT YOU NEED TO KNOW Enterprise instant messaging (IM) has emerged to become an infrastructure component in enterprises. -

DOC-370264A1.Pdf
February 24, 2021 FACT SHEET* Facilitating Shared Use in the 3.1-3.55 GHz Band Second Report and Order, Order on Reconsideration, and Order of Proposed Modification, WT Docket No. 19-348 Background The Beat China by Harnessing Important, National Airwaves for 5G Act of 2020, which was included in the Fiscal Year 2021 omnibus spending bill, requires the Commission to work with its Federal partners to bring all of the 3.45 GHz band spectrum to market for next-generation wireless use through a system of competitive bidding by December 31, 2021. Beginning the implementation of this Congressional mandate, this item reallocates 100 megahertz in the 3.45 GHz band for flexible use wireless services and adopt rules to implement the new 3.45 GHz Service, The framework adopted for the 3.45 GHz band will enable full-power commercial use and provide flexibility to future licensees in deploying their networks in this band, while also ensuring that federal incumbents are still protected where and when they require continued access to the band. What the Second Report and Order Would Do: • Make 100 megahertz of spectrum in the 3.45 GHz band available for flexible use wireless services throughout the contiguous United States; • Add a co-primary, non-federal fixed and mobile (except aeronautical mobile) allocation to the band; • Create a regime to coordinate non-federal and federal use of spectrum by adopting Cooperative Planning Areas and Periodic Use Areas and establishing coordination procedures; • Adopt a band plan and technical, licensing, and competitive -

UVP: Uncovering Wechat Voip Peers Over Time
UVP: Uncovering WeChat VoIP Peers over Time Jiazheng Wang Zhenlong Yuan Department of Automation, Tsinghua University Research Institute of Information Technology Beijing, China Tsinghua University e-mail: [email protected] Beijing, China e-mail: [email protected] Jun Li Research Institute of Information Technology, Tsinghua Tsinghua National Lab for Information Science and Technology Beijing, China e-mail: [email protected] Abstract—VoIP is pervasively used in online voice Control channel protocols, Session Initiation Protocol (SIP) conversations through internet, and WeChat has become one [2] for example, are designed to know where the caller and of the most successful VoIP applications. Any leakage of VoIP callee are, understand the network status of them before the call information will threat user confidentiality and privacy, conversation actually starts. During the conversation, control and thus may lead to a catastrophic consequence to VoIP channel protocols also monitor and adapt to network service providers. In this paper, a thorough behavior analysis changes. Based on the information acquired by the control of WeChat proprietary VoIP protocols is performed and we channel, data channel can be set up to deliver audio chucks, find the anonymity of users can be compromised by flow whether relayed by a third party server, in a so called relay correlation attacks. Hereby a new framework UVP is based model, or directly between the VoIP peers, in the so proposed. UVP works in a global monitoring manner and called peer to peer model. leverages a new, efficient flow distance metric, evolved from Dynamic Time Wrapping, to correlate traffics from caller and VoIP services are responsible to protect the anonymity of callee. -

Microsoft Skype for Business
Spectralink 84-Series Wireless Telephone Microsoft Skype for Business Interoperability Guide (Formerly Lync Server 2013) 1725-86997-000 Rev: J September 2017 Spectralink 84-Series Wireless Telephones: Microsoft Skype for Business Interoperability Guide Copyright Notice © 2013-2017 Spectralink Corporation All rights reserved. SpectralinkTM, the Spectralink logo and the names and marks associated with Spectralink’s products are trademarks and/or service marks of Spectralink Corporation and are common law marks in the United States and various other countries. All other trademarks are property of their respective owners. No portion hereof may be reproduced or transmitted in any form or by any means, for any purpose other than the recipient’s personal use, without the express written permission of Spectralink. All rights reserved under the International and pan-American Copyright Conventions. No part of this manual, or the software described herein, may be reproduced or transmitted in any form or by any means, or translated into another language or format, in whole or in part, without the express written permission of Spectralink Corporation. Do not remove (or allow any third party to remove) any product identification, copyright or other notices. Notice Spectralink Corporation has prepared this document for use by Spectralink personnel and customers. The drawings and specifications contained herein are the property of Spectralink and shall be neither reproduced in whole or in part without the prior written approval of Spectralink, nor be implied to grant any license to make, use, or sell equipment manufactured in accordance herewith. Spectralink reserves the right to make changes in specifications and other information contained in this document without prior notice, and the reader should in all cases consult Spectralink to determine whether any such changes have been made. -

Vx-170 Operating Manual
VHF FM TRANSCEIVER VX-170 OPERATING MANUAL VERTEX STANDARD CO., LTD. 4-8-8 Nakameguro, Meguro-Ku, Tokyo 153-8644, Japan VERTEX STANDARD US Headquarters 10900 Walker Street, Cypress, CA 90630, U.S.A. YAESU EUROPE B.V. P.O. Box 75525, 1118 ZN Schiphol, The Netherlands YAESU UK LTD. Unit 12, Sun Valley Business Park, Winnall Close Winchester, Hampshire, SO23 0LB, U.K. VERTEX STANDARD HK LTD. Unit 5, 20/F., Seaview Centre, 139-141 Hoi Bun Road, Kwun Tong, Kowloon, Hong Kong Contents General Description ......................................... 1 Scanning .......................................................... 36 Accessories & Options ..................................... 2 VFO Scanning .............................................. 37 Controls & Connections .................................. 3 Manual VFO Scan ................................... 37 Top & Front Panel .......................................... 3 Programmed VFO Scan ........................... 37 LCD ................................................................ 4 Memory Scanning ........................................ 38 Side Panel ....................................................... 5 How to Skip (Omit) a Channel Keypad Functions .......................................... 6 during Memory Scan Operation .............. 38 Installation of Accessories ............................... 8 Preferential Memory Scan ....................... 39 Antenna Installation ....................................... 8 Memory Bank Scan ................................. 40 Installation of FNB-83 -

The Beginners Guide to Google+
The Beginners Guide to Google+ From setting up an account to advanced tips and tricks Annette Gardner Grove Digital Marketing Specialist Contents Who we are 3 What we do 4 What is Google+? 5 Set up your Google+ account 7 The interface 9 How do you ‘Google+’? 10 Circles 12 Hangouts 15 Google+ Events 17 Ripples 19 Google+ for business 21 Company pages 23 Advanced tips & tricks 26 2 www.groveis.com | [email protected] Who we are of Exper Grove is a leading Cloud Service provider that specialises in eam ts the implementation of cloud solutions. We help businesses T to define, implement and develop their cloud strategies, providing the bridge between their on-premise and cloud- based IT solutions. By adopting leading edge technologies, our clients can drive value and benefit into their organisations which enables business agility, flexibility and mobility - delivering competitive advantage. Grove is a leading Google Apps Premier Partner and Reseller and our highly skilled team of Google Apps Deployment Specialists and 24/7 Global Network Operations Centre (GNOC) give our customers peace of mind that, through us, their cloud services are deployed and supported to the highest of standards. Established in 2005 with offices in the UK, USA and South Africa we support: 400,000 end-users globally, and our Superior Service Delivery has resulted in a 98% Retention rate of our Clients & Partners www.groveis.com | [email protected] 3 What we do Google+ Apps Devices Platform Geo Search Discovery & Planning 24/7/365 GNOC Support Design & Configuration Project Management Product Training Change Management Email Hosted Penetration ClearFormat Single Sign-on Email Ingestion Continuity Web Security Testing Email Branding Contact Us Google+ has piqued your interest and you’d like to know more about it and the Google Apps for Business product suite. -
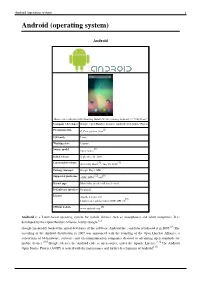
Android (Operating System) 1 Android (Operating System)
Android (operating system) 1 Android (operating system) Android Home screen displayed by Samsung Galaxy Nexus, running Android 4.1 "Jelly Bean" Company / developer Google, Open Handset Alliance, Android Open Source Project [1] Programmed in C, C++, python, Java OS family Linux Working state Current [2] Source model Open source Initial release September 20, 2008 [3] [4] Latest stable release 4.1.1 Jelly Bean / July 10, 2012 Package manager Google Play / APK [5] [6] Supported platforms ARM, MIPS, x86 Kernel type Monolithic (modified Linux kernel) Default user interface Graphical License Apache License 2.0 [7] Linux kernel patches under GNU GPL v2 [8] Official website www.android.com Android is a Linux-based operating system for mobile devices such as smartphones and tablet computers. It is developed by the Open Handset Alliance, led by Google.[2] Google financially backed the initial developer of the software, Android Inc., and later purchased it in 2005.[9] The unveiling of the Android distribution in 2007 was announced with the founding of the Open Handset Alliance, a consortium of 86 hardware, software, and telecommunication companies devoted to advancing open standards for mobile devices.[10] Google releases the Android code as open-source, under the Apache License.[11] The Android Open Source Project (AOSP) is tasked with the maintenance and further development of Android.[12] Android (operating system) 2 Android has a large community of developers writing applications ("apps") that extend the functionality of the devices. Developers write primarily in a customized version of Java.[13] Apps can be downloaded from third-party sites or through online stores such as Google Play (formerly Android Market), the app store run by Google.