Spyawareness
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

What Are Kernel-Mode Rootkits?
www.it-ebooks.info Hacking Exposed™ Malware & Rootkits Reviews “Accessible but not dumbed-down, this latest addition to the Hacking Exposed series is a stellar example of why this series remains one of the best-selling security franchises out there. System administrators and Average Joe computer users alike need to come to grips with the sophistication and stealth of modern malware, and this book calmly and clearly explains the threat.” —Brian Krebs, Reporter for The Washington Post and author of the Security Fix Blog “A harrowing guide to where the bad guys hide, and how you can find them.” —Dan Kaminsky, Director of Penetration Testing, IOActive, Inc. “The authors tackle malware, a deep and diverse issue in computer security, with common terms and relevant examples. Malware is a cold deadly tool in hacking; the authors address it openly, showing its capabilities with direct technical insight. The result is a good read that moves quickly, filling in the gaps even for the knowledgeable reader.” —Christopher Jordan, VP, Threat Intelligence, McAfee; Principal Investigator to DHS Botnet Research “Remember the end-of-semester review sessions where the instructor would go over everything from the whole term in just enough detail so you would understand all the key points, but also leave you with enough references to dig deeper where you wanted? Hacking Exposed Malware & Rootkits resembles this! A top-notch reference for novices and security professionals alike, this book provides just enough detail to explain the topics being presented, but not too much to dissuade those new to security.” —LTC Ron Dodge, U.S. -

Paul Collins Status Name/Startup Item Command Comments X System32
SYSINFO.ORG STARTUP LIST : 11th June 2006 (c) Paul Collins Status Name/Startup Item Command Comments X system32.exe Added by the AGOBOT-KU WORM! Note - has a blank entry under the Startup Item/Name field X pathex.exe Added by the MKMOOSE-A WORM! X svchost.exe Added by the DELF-UX TROJAN! Note - this is not the legitimate svchost.exe process which is always located in the System (9x/Me) or System32 (NT/2K/XP) folder and should not normally figure in Msconfig/Startup! This file is located in the Winnt or Windows folder X SystemBoot services.exe Added by the SOBER-Q TROJAN! Note - this is not the legitimate services.exe process which is always located in the System (9x/Me) or System32 (NT/2K/XP) folder and should not normally figure in Msconfig/Startup! This file is located in a HelpHelp subfolder of the Windows or Winnt folder X WinCheck services.exe Added by the SOBER-S WORM! Note - this is not the legitimate services.exe process which is always located in the System (9x/Me) or System32 (NT/2K/XP) folder and should not normally figure in Msconfig/Startup! This file is located in a "ConnectionStatusMicrosoft" subfolder of the Windows or Winnt folder X Windows services.exe Added by the SOBER.X WORM! Note - this is not the legitimate services.exe process which is always located in the System (9x/Me) or System32 (NT/2K/XP) folder and should not normally figure in Msconfig/Startup! This file is located in a "WinSecurity" subfolder of the Windows or Winnt folder X WinStart services.exe Added by the SOBER.O WORM! Note - this is not the legitimate -

Automated Web Patrol with Strider Honeymonkeys: Finding Web Sites That Exploit Browser Vulnerabilities
Automated Web Patrol with Strider HoneyMonkeys: Finding Web Sites That Exploit Browser Vulnerabilities Yi-Min Wang, Doug Beck, Xuxian Jiang, Roussi Roussev, Chad Verbowski, Shuo Chen, and Sam King Microsoft Research, Redmond Abstract these analyses provide very useful and detailed information about which vulnerabilities are exploited and Internet attacks that use malicious web sites to install which malware programs are installed, such efforts are not malware programs by exploiting browser vulnerabilities scalable, do not provide a comprehensive picture of the are a serious emerging threat. In response, we have problem, and are generally ineffective at efficiently developed an automated web patrol system to finding new malicious sites. automatically identify and monitor these malicious sites. To address these issues, we developed a system that We describe the design and implementation of the Strider uses a pipeline of active, client-side, Virtual Machine HoneyMonkey Exploit Detection System, which consists of (VM)-based honeypots [H,HC], called Strider a pipeline of “monkey programs” running possibly HoneyMonkeys, to perform large-scale, systematic and vulnerable browsers on virtual machines with different automated web patrol. The HoneyMonkey system uses patch levels and patrolling the Web to seek out and monkey programs1 that run within virtual machines with classify web sites that exploit browser vulnerabilities. OS’s of various patch levels to drive web browsers in an Within the first month of utilizing this system, we attempt to mimic human web browsing. Our approach identified 752 unique URLs hosted on 288 web sites that adopts a state-management methodology to cybersecurity: could successfully exploit unpatched Windows XP instead of directly detecting the acts of vulnerability machines. -

Unclassified DSTI/ICCP/IIS(2005)1/FINAL
Unclassified DSTI/ICCP/IIS(2005)1/FINAL Organisation de Coopération et de Développement Economiques Organisation for Economic Co-operation and Development 02-Dec-2005 ___________________________________________________________________________________________ _____________ English - Or. English DIRECTORATE FOR SCIENCE, TECHNOLOGY AND INDUSTRY COMMITTEE FOR INFORMATION, COMPUTER AND COMMUNICATIONS POLICY Unclassified DSTI/ICCP/IIS(2005)1/FINAL Working Party on Indicators for the Information Society SCOPING STUDY FOR THE MEASUREMENT OF TRUST IN THE ONLINE ENVIRONMENT English - Or. English JT00195481 Document complet disponible sur OLIS dans son format d'origine Complete document available on OLIS in its original format DSTI/ICCP/IIS(2005)1/FINAL FOREWORD This report was presented to the Working Party on Indicators for the Information Society (WPIIS) in April 2005 and to the Working Party on Information Security and Privacy (WPISP) in May 2005. It was recommended to be made public by the Committee for Information, Computer and Communications Policy (ICCP) in October 2005. The report was prepared by Sam Paltridge, Sheridan Roberts and Brigitte van Beuzekom of the Economic Analysis and Statistics Division of the OECD’s Directorate for Science, Technology and Industry. The authors wish to thank colleagues in the Division for Information, Computer and Communications Policy and delegates of the WPIIS and WPISP for their contributions. The report is published under the responsibility of the Secretary-General of the OECD. Copyright OECD, 2005. Applications for permission to reproduce or translate all or part of this material should be made to: Head of Publications Service, OECD, 2 rue André-Pascal, 75775 Paris Cedex 16, France. 2 DSTI/ICCP/IIS(2005)1/FINAL TABLE OF CONTENTS FOREWORD................................................................................................................................................. -
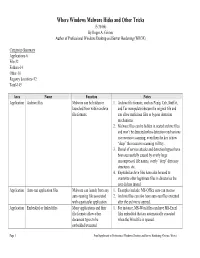
Potentially Malicious Windows Files
Where Windows Malware Hides and Other Tricks (5/30/06) By Roger A. Grimes Author of Professional Windows Desktop and Server Hardening (WROX) Categories Summary Applications-6 File-32 Folders-14 Other-10 Registry Locations-92 Total-145 Area Name Function Notes Application Archive files Malware can be hidden or 1. Archive file formats, such as Pkzip, Cab, Stuff-it, launched from within archive and Tar manipulate/obscure the original file and file formats. can allow malicious files to bypass detection mechanisms. 2. Malware files can be hidden in nested archive files, and won’t be detected unless detection mechanisms use recursive scanning; even then the key is how “deep” the recursive scanning will try. 3. Denial of service attacks and detection bypass have been successfully caused by overly large uncompressed file names, overly “deep” directory structures, etc. 4. Exploded archive files have also be used to overwrite other legitimate files in directories the user did not intend. Application Auto-run application files Malware can launch from any 1. Examples include: MS-Office auto-run macros auto-running file associated 2. Archive files can also have auto-run files executed with a particular application. after the archive is opened. Application Embedded or linked files Many applications and their 1. For instance, MS-Word files can have MS-Excel file formats allow other files embedded that are automatically executed document types to be when the Word file is opened. embedded/executed Page 1 Free Supplement to Professional Windows Desktop and Server Hardening (Grimes, Wrox) Area Name Function Notes Application Microsoft Word Embedded scripting can be 1. -

The Commercial Malware Industry (An Introductory Note)
The Commercial Malware Industry Peter Gutmann University of Auckland (An Introductory Note) For those reading the slides rather than going to the talk: The information was gathered over time and prices and offerings of malware authors change rapidly; all figures and information is/are representative only… Since this is an ongoing work, information is taken from different eras to illustrate changes in the industry and technology; this isn’t how everything works at the current time Malware as a Service Standard commercial vendors are embracing software-as-a- service, SaaS • Malware vendors have MaaS MaaS is advertised and distributed just like standard commercial software Iframe, pop under, накрутка счетчиков, постинг, спам Также я советую если у вас нет сплоита и трафа, вы можете взять в аренду у здесь Iframe exploits, pop-unders, click fraud, posting, spam If you don’t have it, you can rent it here • Online video tutorials of the malware in action Malware as a Service Try-before-you-buy offers for malware Трафик на сплоиты. Для пробы всем Бесплатно 100 посетителей!!! Цена 4 $ за 1000 посетителей - При заказе от 1000 до 5.000 3.8 $ за 1000 посетителей - При заказе от 5.000 до 10.000 3.5 $ за 1000 посетителей - При заказе от 10.000 Traffic for sploits Free trial, 100 visitors!!! Price $4 per 1000 if buying 1000 – 5000 $3.80 per 1000 if buying 5000 – 10,000 $3.50 per 1000 if buying over 10,000 Malware asaService(ctd) Companies producing malware are standard commercial IT commercial arestandard producing malware Companies Malware asaService(ctd) -

Chapter Nine Protecting Your Computer Spreading the Disease
Chapter Nine Protecting Your Computer Spreading the Disease Introduction This chapter ends our third module. The last chapter concentrated on the safety of Internet users and this chapter tidies up a few loose ends. It then moves on to concentrate on the security of our computer’s hardware. This will complete our look at computer hardware begun in module 2. Antivirus Email Plaintext Browser Hijacking Encryption Safe Mode Cipher https Secure Sites Cryptography Malware Throwaway Email Decryption Padlock Virus Email Safety Why should you not send email messages that you would not want to see on the cover of a newspaper? Are email messages archived? Why is it a good idea to have a “throwaway email account”? Why should you not open emails from people you do not know? Email can prove valuable in various circumstances; however, it also poses some threats. Unless you are encrypting your email, do not send anything in your email that you would not want to see on the front page of a newspaper. Email messages are archived on mail servers accessible to others through legal means such as a subpoena. (For more information on encryption and specific applications for email, check the cryptography section of this chapter.) Even if you do encrypt your emails, be careful what you say in them because you do not have control over what the recipient does with them. They may decide to print them out and give copies to passersby on the street. Perhaps they work for a government agency whose emails fall under the open records law, allowing the public to request copies. -

Digital Threats Unmasked Gaining a Solid Understanding of Viruses, Spyware and Spam So That YOU Will Not Fall Victim to It!
Digital Threats Unmasked Gaining a solid understanding of viruses, spyware and spam so that YOU will not fall victim to it! By David Risley Founder/Publisher, PC Mechanic, www.pcmech.com With contribution by: Adam Deutschmann Copyright 2007 PC Media, Inc. All Rights Reserved. www.pcmech.com Page 2 Table of Contents Introduction..................................................................................................5 Computer Viruses.........................................................................................7 What is a computer virus?.......................................................................7 Who Programs Computer Viruses? .........................................................9 Types of Viruses ....................................................................................16 Virus Examples .....................................................................................19 How To Tell If You're Infected..............................................................22 Virus Prevention....................................................................................25 Virus Removal.......................................................................................29 A Word on Hoaxes ................................................................................31 Additional Resources ............................................................................32 Spyware......................................................................................................34 Types of Spyware..................................................................................37 -

Trend Micro™ Client Server Security™ Administrator's Guide
CS4SMB-v36-AG.book Page 1 Monday, April 23, 2007 10:28 AM Client Server Security3 for Small and Medium Business Administrator’s Guide CS4SMB-v36-AG.book Page 2 Monday, April 23, 2007 10:28 AM CS4SMB-v36-AG.book Page 1 Monday, April 23, 2007 10:28 AM Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files, release notes and the latest version of the Getting Started Guide, which are available from Trend Micro's Web site at: http://www.trendmicro.com/download/default.asp NOTE: A license to the Trend Micro Software includes the right to product updates, pattern file updates, and basic technical support for one (1) year from the date of purchase only. Thereafter, you must renew Maintenance on an annual basis by paying Trend Micro’s then-current Maintenance fees to have the right to continue receiving product updates, pattern updates, and basic technical support. To order renewal Maintenance, you may download and complete the Trend Micro Maintenance Agreement at the following site: http://www.trendmicro.com/en/purchase/license/overview.htm Trend Micro, the Trend Micro t-ball logo, TrendLabs, Damage Cleanup Services, OfficeScan, PC-cillin, and ScanMail are trademarks of Trend Micro Incorporated and are registered in certain jurisdictions. All other brand and product names are trademarks or registered trademarks of their respective companies or organizations. Copyright © 1998-2007 Trend Micro Incorporated. All rights reserved. No part of this publication may be reproduced, photocopied, stored in a retrieval system, or transmitted without the express prior written consent of Trend Micro Incorporated. -

Contents in This Issue
SEPTEMBER 2005 The International Publication on Computer Virus Prevention, Recognition and Removal CONTENTS IN THIS ISSUE 2 COMMENT A NEW BREED What’s coming? Windows XP 64-bit In the last year or two, an increasing number of Symbian threats have been reported. While there are 3 NEWS not yet many malware writers who are interested in More hash woes the Symbian OS, this may soon change. Robert Wang The naming game asks: is the Symbian OS in danger of further attacks? page 6 Addendum: NetWare 6.5 comparative review A RIGHT PAIR 3 VIRUS PREVALENCE TABLE Although one always hears about ‘Black Hat and DEFCON’, they FEATURES are in fact two very different 4 The trouble with rootkits events. VB’s intrepid reporter 6 Symbian OS – mysterious playground for (aka AV industry miscreant) has new malware a report on each. 9 New malware distribution methods threaten page 11 signature-based AV A NEW NAMING INITIATIVE 11 CONFERENCE REPORT The Common Malware Enumeration (CME) Black Hat and DEFCON – too hot for many initiative is a new effort headed by the US-CERT, which aims to match a unique identifier to each threat. Jimmy Kuo and Desiree Beck explain how it 14 SPOTLIGHT is hoped this initiative will help alleviate the The Common Malware Enumeration (CME) ‘virus-naming mess’. initiative page 14 16 PRODUCT REVIEW McAfee VirusScan Online 20 END NOTES & NEWS This month: anti-spam news and events, and Sorin Mustaca provides VB’s first phishing analysis. ISSN 0956-9979 COMMENT ‘Support for 16-bit designed after this operating system. -

Symantec Internet Security Threat Report Trends for January 05–June
SYMANTEC ENTERPRISE SECURITY SYMANTEC Symantec Internet Security Threat Report Trends for January 05–June 05 Volume VIII, Published September 2005 Dean Turner Executive Editor Symantec Security Response Stephen Entwisle Editor Symantec Security Response Oliver Friedrichs Technical Advisor Symantec Security Response David Ahmad Manager, Development Symantec Security Response Joseph Blackbird Assoc. Software Engineer Symantec Security Response Marc Fossi DeepSight Threat Analyst Symantec Security Response Daniel Hanson DeepSight Threat Analyst Symantec Security Response Sarah Gordon Sr. Principal Research Engineer Symantec Security Response David Cole Director, Product Management Symantec Security Response David Cowings Sr. Business Intelligence Manager Symantec Business Intelligence Dylan Morss Principal Business Intelligence Analyst Symantec Business Intelligence Brad Bradley Sr. Business Intelligence Analyst Symantec Business Intelligence Peter Szor Security Architect Symantec Security Response Eric Chien Security Researcher Symantec Security Response Jeremy Ward Systems Engineer Mgr. U.K. Sales Communications Jesse Gough DeepSight Threat Analyst Symantec Security Response Josh Talbot DeepSight Threat Analyst Symantec Security Response Volume VIII, Published September 2005 Symantec Internet Security Threat Report Contents Internet Security Threat Report Volume VIII—The Changing Threat Landscape . 4 Internet Security Threat Report Overview . .8 Attack Trends . 20 Vulnerability Trends . 34 Malicious Code Trends . 51 Additional Security Risks Report . 65 Future Watch . 83 Appendix A—Symantec Best Practices . 89 Appendix B—Attack Trends Methodology . 91 Appendix C—Vulnerability Trends Methodology . 95 Appendix D—Malicious Code Trends Methodology . 100 Appendix E—Additional Security Risks Methodology . 101 Symantec Internet Security Threat Report Internet Security Threat Report Volume VIII—The Changing Threat Landscape This edition of the Symantec Internet Security Threat Report marks a shift in the threat landscape. -

Transcript.Pdf (401.82
1 2 3 4 FEDERAL TRADE COMMISSION 5 6 7 8 9 10 MONITORING SOFTWARE ON YOUR PC: 11 SPYWARE, ADWARE, AND OTHER SOFTWARE 12 13 14 15 16 17 Monday, April 19, 2004 18 9:00 a.m. 19 20 21 22 Federal Trade Commission 23 Sixth and Pennsylvania Avenue, N.W. 24 Washington, D.C. 25 26 For The Record, Inc. Waldorf, Maryland (301)870-8025 2 1 2 3 For The Record, Inc. Waldorf, Maryland (301)870-8025 3 1 I N D E X 2 3 Opening Remarks - J. Howard Beales, Director, Bureau of 4 Consumer Protection, FTC 10 5 6 PANEL ONE: DEFINING, UNDERSTANDING, AND 7 DISSEMINATING SPYWARE 8 Moderator: Thomas B. Pahl, Assistant 9 Director, FTC 13 10 Panelists: 11 Ari Schwartz, Associate Director, Center 12 for Democracy and Technology 16 13 Ed Black, President and CEO, Computer 14 and Communications Industry 15 Association 17 16 Mark Bohannon, General Counsel and 17 Senior Vice President for Public 18 Policy, Software and Information 19 Industry Association 18 20 Marty Lafferty, Chief Executive Officer, 21 Distributed Computing Industry 22 Association 19 23 Avi Naider, President and CEO, WhenU.com, 24 Inc. 20 25 For The Record, Inc. Waldorf, Maryland (301)870-8025 4 1 Remarks Concerning Risks of Spyware - 2 Orson Swindle, Commissioner, FTC 62 3 4 PANEL TWO: SECURITY RISKS AND PC FUNCTIONALITY 1 Moderator: David K. Koehler 67 2 Panelists: 3 Maureen Cushman, Legal Counsel, U.S. 4 Consumers, Dell 69 5 Bryson Gordon, Senior Manager, Product 6 Management Group, McAfee Security, 7 Consumer Division 71 8 Roger Thompson, Vice President, Product 9 Development, Pest Patrol 75 10 Michael Wood, Vice President of Sales, USA 11 and Canada, Lavasoft 75 12 John Gilroy, Technology Contributor for The 13 Washington Post and Co-Host, WAMU's 14 "The Computer Guys" program 77 15 Austin Hill, Co-Founder and Chief Privacy 16 Expert, Zero-Knowledge Systems 94 17 18 PANEL THREE: PRIVACY RISKS 19 Moderator: Dean C.