Download Treatise
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Subcultural Appropriations of Appalachia and the Hillbilly Image, 1990-2010
Virginia Commonwealth University VCU Scholars Compass Theses and Dissertations Graduate School 2019 The Mountains at the End of the World: Subcultural Appropriations of Appalachia and the Hillbilly Image, 1990-2010 Paul L. Robertson Virginia Commonwealth University Follow this and additional works at: https://scholarscompass.vcu.edu/etd Part of the American Popular Culture Commons, Appalachian Studies Commons, Literature in English, North America Commons, and the Other Film and Media Studies Commons © Paul L. Robertson Downloaded from https://scholarscompass.vcu.edu/etd/5854 This Dissertation is brought to you for free and open access by the Graduate School at VCU Scholars Compass. It has been accepted for inclusion in Theses and Dissertations by an authorized administrator of VCU Scholars Compass. For more information, please contact [email protected]. Robertson i © Paul L. Robertson 2019 All Rights Reserved. Robertson ii The Mountains at the End of the World: Subcultural Appropriations of Appalachia and the Hillbilly Image, 1990-2010 A dissertation submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy at Virginia Commonwealth University. By Paul Lester Robertson Bachelor of Arts in English, Virginia Commonwealth University, 2000 Master of Arts in Appalachian Studies, Appalachian State University, 2004 Master of Arts in English, Appalachian State University, 2010 Director: David Golumbia Associate Professor, Department of English Virginia Commonwealth University Richmond, Virginia May 2019 Robertson iii Acknowledgement The author wishes to thank his loving wife A. Simms Toomey for her unwavering support, patience, and wisdom throughout this process. I would also like to thank the members of my committee: Dr. David Golumbia, Dr. -

The Alt-Right on Campus: What Students Need to Know
THE ALT-RIGHT ON CAMPUS: WHAT STUDENTS NEED TO KNOW About the Southern Poverty Law Center The Southern Poverty Law Center is dedicated to fighting hate and bigotry and to seeking justice for the most vulnerable members of our society. Using litigation, education, and other forms of advocacy, the SPLC works toward the day when the ideals of equal justice and equal oportunity will become a reality. • • • For more information about the southern poverty law center or to obtain additional copies of this guidebook, contact [email protected] or visit www.splconcampus.org @splcenter facebook/SPLCenter facebook/SPLConcampus © 2017 Southern Poverty Law Center THE ALT-RIGHT ON CAMPUS: WHAT STUDENTS NEED TO KNOW RICHARD SPENCER IS A LEADING ALT-RIGHT SPEAKER. The Alt-Right and Extremism on Campus ocratic ideals. They claim that “white identity” is under attack by multicultural forces using “politi- An old and familiar poison is being spread on col- cal correctness” and “social justice” to undermine lege campuses these days: the idea that America white people and “their” civilization. Character- should be a country for white people. ized by heavy use of social media and memes, they Under the banner of the Alternative Right – or eschew establishment conservatism and promote “alt-right” – extremist speakers are touring colleges the goal of a white ethnostate, or homeland. and universities across the country to recruit stu- As student activists, you can counter this movement. dents to their brand of bigotry, often igniting pro- In this brochure, the Southern Poverty Law Cen- tests and making national headlines. Their appear- ances have inspired a fierce debate over free speech ter examines the alt-right, profiles its key figures and the direction of the country. -
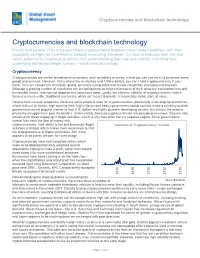
Cryptocurrencies and Blockchain Technology
Cryptocurrencies and blockchain technology Cryptocurrencies and blockchain technology Bitcoin and several of its more prominent cryptocurrency brethren have made headlines, with their popularity as high-risk investments steadily increasing. However, it’s hard to evaluate their risk and return potential as investments without first understanding their use and viability, including their underlying distributed ledger system – blockchain technology. Cryptocurrency Cryptocurrencies are similar to traditional currencies, such as dollars or euros, in that you can use them to purchase some goods and services. However, that’s where the similarities end. Unlike dollars, you can’t hold cryptocurrencies in your hand. They are completely electronic, global, generally unregulated and almost completely anonymous to transact. Although a growing number of merchants are accepting them as payment because of their attractive transaction fees and irrevocable nature, widespread adoption is a long ways away. Lastly, the extreme volatility of cryptocurrencies makes them very much unlike traditional currencies, which are meant to provide a reasonably stable store of value. Despite their unusual properties, there are some practical uses for cryptocurrencies, particularly in developing economies where distrust for banks, high banking fees, high inflation and heavy government capital controls make a currency outside government control popular (similar to how U.S. dollars are highly prized in developing nations, but without the need to physically smuggle them past the border). Unfortunately, because cryptocurrencies are pseudo-anonymous, they are also attractive for those engaging in illegal activities, which is why they often carry a negative stigma. Since governments cannot fully track the flow of money with cryptocurrencies, their ability to tax and prosecute illegal Instances of "Cryptocurrency" Articles activities is limited, which makes them more likely to limit the widespread use of digital currencies. -

A Survey on Volatility Fluctuations in the Decentralized Cryptocurrency Financial Assets
Journal of Risk and Financial Management Review A Survey on Volatility Fluctuations in the Decentralized Cryptocurrency Financial Assets Nikolaos A. Kyriazis Department of Economics, University of Thessaly, 38333 Volos, Greece; [email protected] Abstract: This study is an integrated survey of GARCH methodologies applications on 67 empirical papers that focus on cryptocurrencies. More sophisticated GARCH models are found to better explain the fluctuations in the volatility of cryptocurrencies. The main characteristics and the optimal approaches for modeling returns and volatility of cryptocurrencies are under scrutiny. Moreover, emphasis is placed on interconnectedness and hedging and/or diversifying abilities, measurement of profit-making and risk, efficiency and herding behavior. This leads to fruitful results and sheds light on a broad spectrum of aspects. In-depth analysis is provided of the speculative character of digital currencies and the possibility of improvement of the risk–return trade-off in investors’ portfolios. Overall, it is found that the inclusion of Bitcoin in portfolios with conventional assets could significantly improve the risk–return trade-off of investors’ decisions. Results on whether Bitcoin resembles gold are split. The same is true about whether Bitcoins volatility presents larger reactions to positive or negative shocks. Cryptocurrency markets are found not to be efficient. This study provides a roadmap for researchers and investors as well as authorities. Keywords: decentralized cryptocurrency; Bitcoin; survey; volatility modelling Citation: Kyriazis, Nikolaos A. 2021. A Survey on Volatility Fluctuations in the Decentralized Cryptocurrency Financial Assets. Journal of Risk and 1. Introduction Financial Management 14: 293. The continuing evolution of cryptocurrency markets and exchanges during the last few https://doi.org/10.3390/jrfm years has aroused sparkling interest amid academic researchers, monetary policymakers, 14070293 regulators, investors and the financial press. -

Luciana De Paula Soares.Pdf
UNIVERSIDADE NOVE DE JULHO FACULDADE DE DIREITO MESTRADO EM DIREITO LUCIANA DE PAULA SOARES CRIPTOMOEDA E BLOCKCHAIN: O RIGOR DAS REGRAS BRASILEIRAS FRENTE AO MERCADO TRADICIONAL São Paulo 2021 LUCIANA DE PAULA SOARES CRIPTOMOEDA E BLOCKCHAIN: O RIGOR DAS REGRAS BRASILEIRAS FRENTE AO MERCADO TRADICIONAL Dissertação de mestrado apresentada ao Programa de Pós-graduação em Direito da Universidade Nove de Julho - UNINOVE, como requisito parcial para obtenção do grau de Mestre em Direito. Orientador: Prof. Dr. Dr. h.c. João Maurício Adeodato São Paulo 2021 Soares, Luciana de Paula. Criptomoeda e Blockchain: o rigor das regras brasileiras frente ao mercado tradicional / Luciana de Paula Soares. 2021. 119 f. Dissertação (Mestrado) - Universidade Nove de Julho - UNINOVE, São Paulo, 2021. Orientador (a): Prof. Dr. João Maurício Adeodato. 1. Criptomoeda. 2. Blockchain. 3. Regulamentação. 4. Receita Federal do Brasil. 5. Banco Central do Brasil. I. Adeodato, João Maurício. II. Titulo. CDU 34 Luciana de Paula Soares CRIPTOMOEDA E BLOCKCHAIN: O RIGOR DAS Dissertação apresentada ao REGRAS BRASILEIRAS FRENTE AO MERCADO TRADICIONAL Programa Pós-Graduação Stricto Sensu Em Direito da Universidade Nove de Julho como parte das exigências para a obtenção do título de Mestre em Direito São Paulo, 04 de março de 2021. BANCA EXAMINADORA __________________________________ Prof. Dr. João Mauricio Leitão Adeodato Orientador UNINOVE ________________________________________ Prof. Dr. José Renato Nalini Examinador Interno UNINOVE ________________________________________ Profa. Dra. Alexandre Freire Pimentel Examinador Externo UNICAP AGRADECIMENTOS Agradeço primeiramente à minha família que sempre me apoiou nessa estrada sem fim e de inestimável valor, o estudo. Agradeço, ainda, a paciência dos meus filhos, ainda pequenos, em disponibilizar sua mãe para os livros em plena pandemia da Covid-19. -

A Behavioral Economics Approach to Regulating Initial Coin Offerings
A Behavioral Economics Approach to Regulating Initial Coin Offerings NATHAN J. SHERMAN* INTRODUCTION Initial coin offerings (ICOs) are an outgrowth of the cryptocurrency space in which companies raise capital by issuing their own cryptocurrency coin to investors. Although ICOs are an innovative method of raising capital, the growth of the ICO market is troubling considering no investor protection regulations govern the ICO process. Investors pour large amounts of money into these offerings, which are issued by companies that typically have no history of producing a product or revenue, and the prices of coins issued in ICOs are only rising because other investors also funnel money into them.1 This pattern is markedly similar to that of a speculative bubble. A speculative bubble occurs when there are “‘unsustainable increases’ in asset prices caused by investors trading on a pattern of price increases rather than information on fundamental values.”2 In a bubble, “smart money”—informed investors—bid up prices in anticipation of “noise traders” entering the market.3 The noise traders then enter the market due to the psychological biases they encounter in making their investment decisions.4 Eventually, the smart money investors sell their holdings and the bubble bursts. 5 Thus, regulators should create a framework that adequately protects investors in ICOs. The behavioral economics theory of bounded rationality provides insights for building this regulatory framework. Bounded rationality implies that humans make suboptimal choices.6 By understanding the psychological biases that influence investors’ choices, regulators will be able to help investors adopt habits that reduce the harmful effects of speculative bubbles. -

FUNDING HATE How White Supremacists Raise Their Money
How White Supremacists FUNDING HATE Raise Their Money 1 RESPONDING TO HATE FUNDING HATE INTRODUCTION 1 SELF-FUNDING 2 ORGANIZATIONAL FUNDING 3 CRIMINAL ACTIVITY 9 THE NEW KID ON THE BLOCK: CROWDFUNDING 10 BITCOIN AND CRYPTOCURRENCIES 11 THE FUTURE OF WHITE SUPREMACIST FUNDING 14 2 RESPONDING TO HATE How White Supremacists FUNDING HATE Raise Their Money It’s one of the most frequent questions the Anti-Defamation League gets asked: WHERE DO WHITE SUPREMACISTS GET THEIR MONEY? Implicit in this question is the assumption that white supremacists raise a substantial amount of money, an assumption fueled by rumors and speculation about white supremacist groups being funded by sources such as the Russian government, conservative foundations, or secretive wealthy backers. The reality is less sensational but still important. As American political and social movements go, the white supremacist movement is particularly poorly funded. Small in numbers and containing many adherents of little means, the white supremacist movement has a weak base for raising money compared to many other causes. Moreover, ostracized because of its extreme and hateful ideology, not to mention its connections to violence, the white supremacist movement does not have easy access to many common methods of raising and transmitting money. This lack of access to funds and funds transfers limits what white supremacists can do and achieve. However, the means by which the white supremacist movement does raise money are important to understand. Moreover, recent developments, particularly in crowdfunding, may have provided the white supremacist movement with more fundraising opportunities than it has seen in some time. This raises the disturbing possibility that some white supremacists may become better funded in the future than they have been in the past. -

Macron Leaks” Operation: a Post-Mortem
Atlantic Council The “Macron Leaks” Operation: A Post-Mortem Jean-Baptiste Jeangène Vilmer The “Macron Leaks” Operation: A Post-Mortem Jean-Baptiste Jeangène Vilmer ISBN-13: 978-1-61977-588-6 This report is written and published in accordance with the Atlantic Council Policy on Intellectual Indepen- dence. The author is solely responsible for its analysis and recommendations. The Atlantic Council and its donors do not determine, nor do they necessarily endorse or advocate for, any of this report’s conclusions. June 2019 Contents Acknowledgments iv Abstract v Introduction 1 I- WHAT HAPPENED 4 1. The Disinformation Campaign 4 a) By the Kremlin media 4 b) By the American alt-right 6 2. The Aperitif: #MacronGate 9 3. The Hack 10 4. The Leak 11 5. In Summary, a Classic “Hack and Leak” Information Operation 14 6. Epilogue: One and Two Years Later 15 II- WHO DID IT? 17 1. The Disinformation Campaign 17 2. The Hack 18 3. The Leak 21 4. Conclusion: a combination of Russian intelligence and American alt-right 23 III- WHY DID IT FAIL AND WHAT LESSONS CAN BE LEARNED? 26 1. Structural Reasons 26 2. Luck 28 3. Anticipation 29 Lesson 1: Learn from others 29 Lesson 2: Use the right administrative tools 31 Lesson 3: Raise awareness 32 Lesson 4: Show resolve and determination 32 Lesson 5: Take (technical) precautions 33 Lesson 6: Put pressure on digital platforms 33 4. Reaction 34 Lesson 7: Make all hacking attempts public 34 Lesson 8: Gain control over the leaked information 34 Lesson 9: Stay focused and strike back 35 Lesson 10: Use humor 35 Lesson 11: Alert law enforcement 36 Lesson 12: Undermine propaganda outlets 36 Lesson 13: Trivialize the leaked content 37 Lesson 14: Compartmentalize communication 37 Lesson 15: Call on the media to behave responsibly 37 5. -

December 22, 2016 RE: Table Game Rules MGL C
TO: Massachusetts Gaming Commission FROM: Carrie Torrisi, Staff Attorney DATE: December 22, 2016 RE: Table Game Rules M.G.L. c. 23K, § 2, defines “table game” as “a game, other than a slot machine, which is authorized by the commission to be played in a gaming establishment.” Table games include “standard” games such as poker, roulette, craps, and baccarat, as well as any number of more obscure games or game variations. Before Category 1 licensees begin operating casinos in the Commonwealth, it is important that the rules of each and every table game that is authorized for play are clearly defined. To that end, the Commission should establish a process by which it approves and authorizes the rules to be followed in the conduct of table games and a process by which those rules are made available to the public. The Commission should consider (1) how to proceed with respect to the initial promulgation of regulations governing table game rules; and (2) how to proceed with respect to proposed new games or game variations following the initial promulgation of the regulations. Following is a survey of processes followed with respect to table game rules in five jurisdictions: Nevada, New Jersey, Pennsylvania, Ohio, and Maryland. I. Authorization of Games for Play All states but Ohio authorize several “standard” games (e.g., poker, blackjack, craps, roulette) by way of a statutory definition of table game.1 1 Nevada: “Game” or “gambling game” means any game played with cards, dice, equipment or any mechanical, electromechanical or electronic device or machine for money, property, checks, credit or any representative of value, including, without limiting the generality of the foregoing, faro, monte, roulette, keno, bingo, fan-tan, twenty-one, blackjack, seven-and-a-half, big injun, klondike, craps, poker, chuck-a-luck, Chinese chuck-a-luck (dai shu), wheel of fortune, chemin de fer, baccarat, pai gow, beat the banker, panguingui, slot machine, any banking or percentage game or any other game or device approved by the Commission.. -

The Fringe Insurgency Connectivity, Convergence and Mainstreaming of the Extreme Right
The Fringe Insurgency Connectivity, Convergence and Mainstreaming of the Extreme Right Jacob Davey Julia Ebner About this paper About the authors This report maps the ecosystem of the burgeoning Jacob Davey is a Researcher and Project Coordinator at ‘new’ extreme right across Europe and the US, which is the Institute for Strategic Dialogue (ISD), overseeing the characterised by its international outlook, technological development and delivery of a range of online counter- sophistication, and overtures to groups outside of the extremism initiatives. His research interests include the traditional recruitment pool for the extreme-right. This role of communications technologies in intercommunal movement is marked by its opportunistic pragmatism, conflict, the use of internet culture in information seeing movements which hold seemingly contradictory operations, and the extreme-right globally. He has ideologies share a bed for the sake of achieving provided commentary on the extreme right in a range common goals. It examines points of connectivity of media sources including The Guardian, The New York and collaboration between disparate groups and Times and the BBC. assesses the interplay between different extreme-right movements, key influencers and subcultures both Julia Ebner is a Research Fellow at the Institute for online and offline. Strategic Dialogue (ISD) and author of The Rage: The Vicious Circle of Islamist and Far-Right Extremism. Her research focuses on extreme right-wing mobilisation strategies, cumulative extremism and European terrorism prevention initiatives. She advises policy makers and tech industry leaders, regularly writes for The Guardian and The Independent and provides commentary on broadcast media, including the BBC and CNN. © ISD, 2017 London Washington DC Beirut Toronto This material is offered free of charge for personal and non-commercial use, provided the source is acknowledged. -

Is It Better to Invest in Bitcoin Or Ethereum
1 Is It Better to Invest in Bitcoin or Ethereum Update [06-07-2021] The Ethereum Virtual Machine is the global virtual computer whose state every participant on the Ethereum network stores and agrees on. A blockchain is best described as a public database that is updated and shared across many computers in a network. This causes a state change in the EVM, which is committed and propagated throughout the entire network. Execution of any code causes a state change in the EVM; upon commitment, this state change is broadcast to all nodes in the network. Etc rally strength only exceeded by the rally into the end of may 2017. Cryptocurrency buy entries june 2021. Etc and eth technologies such as;. Bitcoin, ethereum, and dogecoin are plunging. Meanwhile, KODAKCoin will help photographers get paid when their content is used. 7 billion to 20. Ethereum has been a go-to alternative to Bitcoin because it typically offers shorter transaction wait times and lower transaction fees. Launched in August, Bitcoin Cash is hard fork of Bitcoin. The Ethereum Virtual Machine is the global virtual computer whose state every participant on the Ethereum network stores and agrees on. A blockchain is best described as a public database that is updated and shared across many computers in a network. This causes a state change in the EVM, which is committed and propagated throughout the entire network. Execution of any code causes a state change in the EVM; upon commitment, this state change is broadcast to all nodes in the network. Etc rally strength only exceeded by the rally into the end of may 2017. -

The Revolution a TECHNOLOGY DESTINED to CHANGE OUR LIVES
the revolution A TECHNOLOGY DESTINED TO CHANGE OUR LIVES WHAT IS A BLOCKCHAIN The impact on the financial system The Blockchain is a register. Each unit in the register is a “block”, and the blocks Although there are already those who speculate that the cryptocurrencies in are linked each other following the sequence of their creation. Blockchains are the future may replace cash, now – however - the real revolution is repre- useful for two things: recording events and making sure the recording will ne- sented in the Blockchain, destined to have on the financial system (and not ver be deleted. It is so difficult to change blocks because a Blockchain works only) an impact comparable to that of social network on interpersonal rela- through a diffused computer network, which have to approve all the changes tionships. The bank of Italy, which has been following the phenomenon for that take place. at least a couple of years with a dedicated program, explains that «the set of Since there is no a central server to tamper with or attack, hackers can’t simply informatic rules (protocol) generates the mutual trust of the partecipants in take control of a single computer and make changes. As a result, participants the stored data and is potentially able to replace the trust ensured by ‘public can trust the data contained in a blockchain without having to know or to trust registers’ managed in a centralized way by an authority recognized by the each other and without having to rely on a central authority. regulatory framework». Apllications to our daily life A simplification applicable to health The technological innovation based on Blockchain will have enormous posi- In the health sector, the Blockchain could be very useful in the management tive repercussions on the mostvaried aspects of our daily life: thanks to use and storage of the various medical documents.