Barcode Localization and Decoding Using a Modified Scanline Approach for Industrial Nameplate Verification
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Useful Facts About Barcoding
Useful Facts about Barcoding When Did Barcodes Begin? (Part 1) A barcode is an optical machine-readable representation of data relating to the object to which it is attached. Originally barcodes represented data by varying the widths and spacing’s of parallel lines and may be referred to as linear or one-dimensional (1D). Later they evolved into rectangles, dots, hexagons and other geometric patterns in two dimensions (2D). Although 2D systems use a variety of symbols, they are generally referred to as barcodes as well. Barcodes originally were scanned by special optical scanners called barcode readers; later, scanners and interpretive software became available on devices including desktop printers and smartphones. Barcodes are on the leading edge of extraordinary things. They have given humans the ability to enter and extract large amounts of data in relatively small images of code. With some of the latest additions like Quick Response (QR) codes and Radio-frequency identification (RFID), it’s exciting to see how these complex image codes are being used for business and even personal use. The original idea of the barcode was first introduced in 1948 by Bernard Silver and Norman Joseph Woodland after Silver overheard the President of a local food chain talking about their need for a system to automatically read product information during checkout. Silver and Woodland took their inspiration from recognizing this rising need and began development on this product so familiar to the world now. After several attempts to create something usable, Silver and Woodland finally came up with their ”Classifying Apparatus and Method” which was patented on October 07, 1952. -

CR5000 Retail Data Sheet Specifications Subject to Change Without Notice
® www.codecorp.com Performance Characteristics Physical Characteristics Focal Point Approximately 100 mm CR5000 Dimensions 5.95” H x 2.80” L x 3.55” W (151.14 mm H x 71.23 mm L x 90.30 mm W) Target Beam Single, blue targeting bar CR5000 Weight 11.2 oz (318 g) Field of View High Density Field: 30° horizontal by 20° vertical Wide Field: 50° horizontal by 33.5° vertical IP Rating 52 Optical Resolution High Density Field: 960 x 640, Wide Field: 960 x 640 Shock Withstands multiple drops of 6’ (1.8 Meters to concrete) User Environment Communication Interfaces RS232, USB 2.0 (Generic HID, HID Keyboard, Virtual Com Port) Memory Capacity 128MB Flash ROM, 32MB RAM Decode Capability 1D: Codabar, Code 11, Code 32, Code 39, Code 93, Code 128, Warranty 3 years Interleaved 2 of 5, GS1 DataBar (RSS), Hong Kong 2 of 5, Maxtrix 2 of 5, MSI Plessey, Pharmacode, Plessey, Straight 2 of 5, Telepen, Trioptic, UPC/EAN/JAN Stacked 1D: GS1 Composite (CC-A/CC-B/CC-C), MicroPDF, PDF417 2D: Aztec Code, Data Matrix, Micro QR Code, QR Code, Han Xin Accessories Proprietary 2D: GoCode® (Additional License Required) Postal Codes: Australian Post, Intelligent Mail, Japan Post, KIX • Various Cable Options Available. Visit Code, PLANET, POSTNET, UK Royal Mail www.codecorp.com/cables.php for a list of compatible cables Field Selection High Density or Wide Field Data Editing JavaScript ® * Warranty period is specific to North America and EMEA CR5000 Retail Data Sheet Specifications subject to change without notice. Copyright © 2015 Code Corporation. -

Introduction to Industrial Barcode Reading
Back to Basics: Introduction to Industrial Barcode Reading 1 Agenda . What is a barcode? . History . 1-D codes . Types and terminology . 2-D codes . Types and terminology . Marking Methods . Laser Scanning . Image-Based Reading . Hardware and Software . Communication . How to select a reader 2 2 | © 2014 Cognex Corporation What is barcode reading? . A barcode is a machine readable representation of data related to the object it is attached to. A barcode reader is used to read these codes in order to track the object throughout its lifecycle. 3 3 | © 2014 Cognex Corporation Where are barcodes used? . The first product to ever be scanned was in 1974. By the 1980s, scanning for retail became worldwide. Today, codes can be both 1-D and 2-D. Where can I find barcodes? 4 4 | © 2014 Cognex Corporation Where are barcodes used? Food Medical & Packaging Pharmaceutical Automotive Aerospace Electronics 5 5 | © 2014 Cognex Corporation 1-D Barcodes Different types Industry terminology Common uses 6 6 | © 2014 Cognex Corporation Common 1-D Barcode Types UPC-A Code 39 Code 128 Interleaved 2 of 5 Codabar Pharmacode 7 7 | © 2014 Cognex Corporation Linear Barcode Terminology . Quiet Zone . Guard Pattern . Narrow Bar Width 8 8 | © 2014 Cognex Corporation 2-D Barcodes Different types Industry terminology Marking methods Common uses 9 9 | © 2014 Cognex Corporation Common 2-D Codes DataMatrix QR-Code Aztec Code MaxiCode 10 10 | © 2014 Cognex Corporation 2-D Code Terminology . 24 square and 6 rectangular formats . 3,116 numeric or 2,335 alphanumeric characters . Cell presence/absence check tolerates poor printing . Error correction improves read rates . -

Dataman Configuration Codes
DataMan® Configuration Codes 9/22/2015 Version 5.6.0 Legal Notices Legal Notices The software described in this document is furnished under license, and may be used or copied only in accordance with the terms of such license and with the inclusion of the copyright notice shown on this page. Neither the software, this document, nor any copies thereof may be provided to, or otherwise made available to, anyone other than the licensee. Title to, and ownership of, this software remains with Cognex Corporation or its licensor. Cognex Corporation assumes no responsibility for the use or reliability of its software on equipment that is not supplied by Cognex Corporation. Cognex Corporation makes no warranties, either express or implied, regarding the described software, its merchantability, non-infringement or its fitness for any particular purpose. The information in this document is subject to change without notice and should not be construed as a commitment by Cognex Corporation. Cognex Corporation is not responsible for any errors that may be present in either this document or the associated software. Companies, names, and data used in examples herein are fictitious unless otherwise noted. No part of this document may be reproduced or transmitted in any form or by any means, electronic or mechanical, for any purpose, nor transferred to any other media or language without the written permission of Cognex Corporation. Copyright © 2015. Cognex Corporation. All Rights Reserved. Portions of the hardware and software provided by Cognex may be covered by one or more U.S. and foreign patents, as well as pending U.S. -

2Xfield of View Depth of Field Speed
NEW 1D/2D Code Reader SR-2000 Series HIGH RESOLUTION READING NOW POSSIBLE Field of view Depth of field 2x Speed One reader for any code, anywhere, any speed SR-2000 Series Breaking the stigma of code readers Just install and go! Obtain a wider field of view and greater depth of field at a longer range. Work as fast as the targets can move. No experience is required to master the SR-2000 Series. Just install the reader for vastly improved reading range and achieve even better reading stability. NEW 1D/2D Code Reader SR-2000 Series 2× greater than conventional models The wide field of view allows for reading of multiple codes even if Ultra-wide field of view they are far apart. • No need to check code positions • Read multiple codes all at once P. 4 2× greater than conventional models Greater depth of field at longer ranges • No code position controllers or tooling changes required • Read minute codes at long distances P. 6 2× greater than conventional models Read objects on the move • Read codes without having to stop the target • Read codes on rotating targets without trouble P. 8 Fully automatic calibration • No expert imaging knowledge required, and no need to select additional external equipment (lenses, lighting, etc.) P. 1 0 2 The wider range of focus allows for reading of codes at different heights. 3 Ultra-wide field of view At least twice as wide a field of view compared to conventional models for easy reading of multiple codes and varying code positions. Read codes on When it comes to codes on tire rims, the position varies according to the tire size. -

PC-6015 Barcode Verifier
PC-6015 Barcode Verifier Point of Sale Barcode Verifier Product Summary Independently tested & certified to meet international standards, the Axicon 6015 has been specifically designed to read all linear barcodes with a width of up to 68mm (2.6”) including quiet zones. The system consists of a state of the art CCD read head and application software. Our development program means that not only will your verifier always meet the latest ISO/ ANSI standard, but also a wide range of application standards including GS1- 128 & ISBN/ISSN. A wide range of additional reporting tools is also provided with every verifier. Typical Application Smaller barcodes including all Benefits retail point of sale barcodes whether printed on labels, ISO/ANSI Verification flexible packaging, cartons, bags, Standards cans or jars. Static Scan Reflectance Installation Measurement Simply Install the software on AI Data Content Checker KFM 10F, 6-9, Koyo-cho Naka, your computer, plug in the verifier Higashinada-ku, Kobe 658-0032 and you can be confident that (For GS1-128 & GS1 Japan. your barcodes are being checked DataBar etc.) to the highest standards. Tel: +81-78-857-5447 Multi Language User Fax: +81-78-857-5443 Interface email: [email protected] http://en.munazo.us USB Connectivity Axicon 6015 Barcode Verifier SOFTWARE SPECIFICATIONS Symbologies Verified: GS1 SYMBOLOGIES: EAN-8, EAN-13 (with or without addons), ITF-14/Case Code, GS1-DataBar (all symbologies), GS1- 128, UPC-A, UPC-E (with or without addons). OTHER SYMBOLOGIES: Code 39, Code 93, Code 128, Codabar, ITF, MSI Plessey, Pharmacode (Laetus: optional extra). Application Standards: AIAG, Belgian Pharmacode (MSI), Belgian Pharmacode (Unique), CIP39, Coupon Codes (UK, USA, Euro), Code Vignette, GS1 AI Check, HIBC, ISBN/ISSN, Italian Pharmacode (IMH), LPPR, M&S, PZN, SISAC, Variable Measure Codes (Branded, Instore, Australian). -

Leuze BCL8 Series Barcode Readers
BCL 8 Barcode Reader with Integrated Decoder GB 02-08/07 50040581 TECHNICALBuy: www.ValinOnline.com DESCRIPTION | Phone 844-385-3099 | Email: [email protected] Table of contents 1 General information........................................................................................................... 4 1.1 Explanation of symbols ........................................................................................................ 4 1.2 Declaration of conformity ..................................................................................................... 4 2 Safety notices..................................................................................................................... 5 2.1 Safety standards .................................................................................................................. 5 2.2 Approved purpose................................................................................................................ 5 2.3 Working safely ..................................................................................................................... 6 3 Description ......................................................................................................................... 8 3.1 The BCL 8 barcode reader .................................................................................................. 8 3.2 Stand alone operation.......................................................................................................... 9 3.3 Daisy chain network............................................................................................................ -
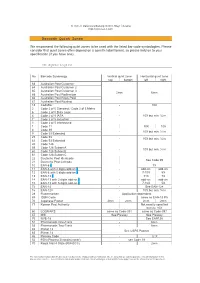
Barcode Quiet Zones 1D Symbologies
© TEC-IT Datenverarbeitung GmbH, Steyr / Austria http://www.tec-it.com Barcode Quiet Zones We recommend the following quiet zones to be used with the listed bar code symbologies. Please consider that quiet zones often depend on a specific label format, so please hold on to your specification (if you have one). 1D Symbologies No. Barcode Symbology Vertical quiet zone Horizontal quiet zone top bottom left right 63 Australian Post Customer 64 Australian Post Customer 2 65 Australian Post Customer 3 2mm 6mm 68 Australian Post Redirection 66 Australian Post Reply Paid 67 Australian Post Routing 18 CodaBar - 10X 2 Code 2 of 5 Standard / Code 2 of 5 Matrix 6 Code 2 of 5 Data Logic 4 Code 2 of 5 IATA - 10X but min. ¼ in 7 Code 2 of 5 Industrial 3 Code 2 of 5 Interleaved 1 Code 11 10X 10X 8 Code 39 - 10X but min. ¼ in 9 Code 39 Extended 25 Code 93 - 10X but min. ¼ in 62 Code 93 Extended 20 Code 128 59 Code 128 Subset A - 10X but min. ¼ in 60 Code 128 Subset B 61 Code 128 Subset C 22 Deutsche Post Identcode See Code 39 21 Deutsche Post Leitcode 10 EAN-8 * 7X 11 EAN-8 with 2 digits add-on * - add-on: add-on: 12 EAN-8 with 5 digits add-on * 7-10X 5X 13 EAN-13 * 11X 7X 14 EAN-13 with 2 digits add-on * - add-on: add-on: 15 EAN-13 with 5 digits add-on * 7-10X 5X 72 EAN-14 - See EAN-128 16 EAN-128 - 10X but min. -

Axicon 7025-S Barcode Verifier the Axicon ‘S’ Range -For Enhanced Accuracy
Axicon 7025-S Barcode Verifier The Axicon ‘S’ Range -For enhanced accuracy Product Summary The Axicon 7025-S is designed for all barcodes where an 8, 10 or 20mil aperture is mandatory (such as GS1-128 and ITF- 14), up to 195mm width including quiet zones. The simple to use design reduces user error and eliminates product damage whilst providing the highest level of accuracy achievable for verification. Typical Application Traded Pack level (Warehouse) barcodes whether being verified on cartons, labels, corrugated board, shrink wrap film etc plus all pallet labels and linear barcodes of a similar size. Benefits Enhanced Accuracy ISO/ANSI verification The “S” range of Axicon standards verifiers have a “Continuous Over 150 scans per Scan” feature. second Just place the verifier over the Ideal for GS1 Databar Church Road barcode (or slightly above or Stacked Codes Weston on the Green, below the barcode), press the Multi Language user Oxford, OX25 3QP, U.K. trigger and slide the verifier Tel +44 (0)1869 351 155 interface over the code – in less than a email: [email protected] Ideal for barcodes with www.axicon.com second you can have results averaged over more than 150 small height scans of the code at different USB2 Connectivity points in the bar height Axicon 7025- S Barcode Verifier SOFTWARE SPECIFICATIONS Symbologies Verified: GS1 SYMBOLOGIES: EAN-8, EAN-13 (with or without addons), ITF-14/Case Code, GS1-DataBar (all symbologies), GS1-128, UPC-A, UPC-E (with or without addons). OTHER SYMBOLOGIES: Code 39, Code 93, Code 128, Codabar, ITF, MSI Plessey, Pharmacode (Laetus: optional extra). -

Axicon 6515 Barcode Verifier
Axicon 6515 Barcode Verifier Axicon 6515 Mid-Range Barcode Verifier Product Summary Independently tested & certified to meet International Standards, the Axicon 6515 has been specifically designed to read all linear barcodes with a width of up to 125mm (4.9”) including quiet zones. Our development program means that not only will your verifier always meet the latest ISO/ ANSI standard, but also a wide range of application standards including GS1-128 & ISBN/ISSN. An extensive array of additional reporting tools is also provided. Typical Application Accuracy, Repeatability and Reliability. Axicon has been The Axicon 6515 is capable of verifing linear involved with barcode verification for 30 years and barcodes up to 125mm (4.9”) wide making pioneered the use of CCD imaging for verification. With it ideal for both point of sale and traded time comes experience and insight and we’re not short unit barcodes – typically those printed on of either! Actively listening to our clients suggestions, thermal/thermal transfer printers. For this we constantly enhance and improve our system. The reason it is widely regarded as the industry result? The most comprehensive and flexible standard across many business sectors. verification system on the market. Installation Simply install the software on your Benefits computer, plug in the verifier and you can be confident that your barcodes are being ISO/ANSI Verification checked to the highest standards. The Standards standard software includes everything you Automatic variable aperture could ever need from a barcode verifier. Traceability features include automatic Static Scan Reflectance saving of files, reports in a variety of Measurement formats, data content checks against a wide range of application standards as well as AI Data Content Checker (For the product look-up function - helping you GS1-128 & GS1 DataBar) to ensure that your barcodes are fit for Multi Language User Interface purpose. -

PC-6000 Data Sheet
PC-6000 Range PC Based Bar Code Verifiers Features/Benefits ANSI/ISO/CEN Verification Standards · Traditional Verification Standards · USB or Serial Connectivity · CEN Class A Verifier (EN 12647) · Symbology Auto-Discrimination · Automatic Variable Aperture (4, 5, 6, 10 & 20 mil) · Scan Storage & Replay · Static Reflectance Meter · Display of X Dimension/Magnification · Product Look-up Option · Individual Bar/Space Dimensional Analysis Product Summary The CodeMaster PC-6000 range comprises CCD based verifier hardware and Windows™ software, to the latest ANSI/ISO verification standards. They conform to ANSI x3.182, CEN EN1635 and ISO/IEC 15416-1 verification methodology. All our equipment complies with ISO/IEC15426-1 and, as measured by EN12647, meets the most stringent CEN Class A standard. The PC-6000 range is designed for the verification of all barcodes up to 2.84” width including quiet zones. The simple to use, non contact design eliminates user error and product damage whilst providing the highest level of accuracy achievable for verification. The CodeMaster range of PC verifiers provides highly sophisticated, yet easy to use barcode quality control information. They check all aspects of the printed barcode symbol and present the verification data in a clear comprehensive manner. Simply install the software on your PC, plug in the verifier and rest assured that your barcodes are being checked to the highest standards. Exclusive software upgrade features including CSV/Scan DB, AI Checker and Product Look Up can either be supplied as part of the package or as field upgrades to the standard unit. The CodeMaster PC Verifer, when used in conjunction with our accurately produced calibration sheet, can form an integral part of your ISO9000 quality control procedures. -

CR5200 Data Sheet
codecorp.com CODE READER 5200 More for Your Application • High-speed, omnidirectional reading of 1D and 2D barcode symbologies • Presentation reader with easy hands-free operation and enhanced motion detection • User feedback with LED and audible tone • Compact footprint with adjustable reading direction • Quickly reads barcodes on mobile device screens • Data parsing/formatting eases system Unparalleled reading perfomance for your compatibility POS and ID scanning workflows. • Customizable driver license data Barcode reading needs to be extremely easy, especially at the point formatting for loyalty and credit applications of sale. A positive consumer experience is paramount to drive repeat business, and one of the drivers of a good buying experience is • Extended read ranges speed at checkout. The CR5200 aids in checkout speed by providing • Optional age verification fast reading of a variety of barcodes on a variety of media, including • Efficient power consumption consumer packaged goods, driver licenses, loyalty cards, receipts, and even dim smartphone screens. All of this speed comes with hands-free operation so cashiers can quickly present items to the scanner with both hands, in any orientation. No need to lose efficiency picking up the reader to point and shoot...the CR5200 can stay on the counter and still facilitate efficiency at point of sale. Despite all of this power, the CR5200 has a small footprint to leave space for sale items that might lead to last minute purchases and increased revenue for retailers or quick service restaurants. As an added customer engagement tool, the CR5200 can parse driver license data. Easily capture consumer information for credit applications, loyalty registration, or marketing lists without the need for additional hardware.