An Introduction to Coding Theory: Lecture Notes
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
![A [49 16 6 ]-Linear Code As Product of the [7 4 2 ] Code Due to Aunu and the Hamming [7 4 3 ] Code](https://docslib.b-cdn.net/cover/2633/a-49-16-6-linear-code-as-product-of-the-7-4-2-code-due-to-aunu-and-the-hamming-7-4-3-code-232633.webp)
A [49 16 6 ]-Linear Code As Product of the [7 4 2 ] Code Due to Aunu and the Hamming [7 4 3 ] Code
General Letters in Mathematics, Vol. 4, No.3 , June 2018, pp.114 -119 Available online at http:// www.refaad.com https://doi.org/10.31559/glm2018.4.3.4 A [49 16 6 ]-Linear Code as Product Of The [7 4 2 ] Code Due to Aunu and the Hamming [7 4 3 ] Code CHUN, Pamson Bentse1, IBRAHIM Alhaji Aminu2, and MAGAMI, Mohe'd Sani3 1 Department Of Mathematics, Plateau State University Bokkos, Jos Nigeria [email protected] 2 Department Of Mathematics, Usmanu Danfodiyo University Sokoto, Sokoto Nigeria [email protected] 3 Department Of Mathematics, Usmanu Danfodiyo University Sokoto, Sokoto Nigeria [email protected] Abstract: The enumeration of the construction due to "Audu and Aminu"(AUNU) Permutation patterns, of a [ 7 4 2 ]- linear code which is an extended code of the [ 6 4 1 ] code and is in one-one correspondence with the known [ 7 4 3 ] - Hamming code has been reported by the Authors. The [ 7 4 2 ] linear code, so constructed was combined with the known Hamming [ 7 4 3 ] code using the ( u|u+v)-construction method to obtain a new hybrid and more practical single [14 8 3 ] error- correcting code. In this paper, we provide an improvement by obtaining a much more practical and applicable double error correcting code whose extended version is a triple error correcting code, by combining the same codes as in [1]. Our goal is achieved through using the product code construction approach with the aid of some proven theorems. Keywords: Cayley tables, AUNU Scheme, Hamming codes, Generator matrix,Tensor product 2010 MSC No: 97H60, 94A05 and 94B05 1. -

Coding Theory: Linear Error-Correcting Codes Coding Theory Basic Definitions Error Detection and Correction Finite Fields Anna Dovzhik
Coding Theory: Linear Error- Correcting Codes Anna Dovzhik Outline Coding Theory: Linear Error-Correcting Codes Coding Theory Basic Definitions Error Detection and Correction Finite Fields Anna Dovzhik Linear Codes Hamming Codes Finite Fields Revisited BCH Codes April 23, 2014 Reed-Solomon Codes Conclusion Coding Theory: Linear Error- Correcting 1 Coding Theory Codes Basic Definitions Anna Dovzhik Error Detection and Correction Outline Coding Theory 2 Finite Fields Basic Definitions Error Detection and Correction 3 Finite Fields Linear Codes Linear Codes Hamming Codes Hamming Codes Finite Fields Finite Fields Revisited Revisited BCH Codes BCH Codes Reed-Solomon Codes Reed-Solomon Codes Conclusion 4 Conclusion Definition A q-ary word w = w1w2w3 ::: wn is a vector where wi 2 A. Definition A q-ary block code is a set C over an alphabet A, where each element, or codeword, is a q-ary word of length n. Basic Definitions Coding Theory: Linear Error- Correcting Codes Anna Dovzhik Definition If A = a ; a ;:::; a , then A is a code alphabet of size q. Outline 1 2 q Coding Theory Basic Definitions Error Detection and Correction Finite Fields Linear Codes Hamming Codes Finite Fields Revisited BCH Codes Reed-Solomon Codes Conclusion Definition A q-ary block code is a set C over an alphabet A, where each element, or codeword, is a q-ary word of length n. Basic Definitions Coding Theory: Linear Error- Correcting Codes Anna Dovzhik Definition If A = a ; a ;:::; a , then A is a code alphabet of size q. Outline 1 2 q Coding Theory Basic Definitions Error Detection Definition and Correction Finite Fields A q-ary word w = w1w2w3 ::: wn is a vector where wi 2 A. -

Mceliece Cryptosystem Based on Extended Golay Code
McEliece Cryptosystem Based On Extended Golay Code Amandeep Singh Bhatia∗ and Ajay Kumar Department of Computer Science, Thapar university, India E-mail: ∗[email protected] (Dated: November 16, 2018) With increasing advancements in technology, it is expected that the emergence of a quantum computer will potentially break many of the public-key cryptosystems currently in use. It will negotiate the confidentiality and integrity of communications. In this regard, we have privacy protectors (i.e. Post-Quantum Cryptography), which resists attacks by quantum computers, deals with cryptosystems that run on conventional computers and are secure against attacks by quantum computers. The practice of code-based cryptography is a trade-off between security and efficiency. In this chapter, we have explored The most successful McEliece cryptosystem, based on extended Golay code [24, 12, 8]. We have examined the implications of using an extended Golay code in place of usual Goppa code in McEliece cryptosystem. Further, we have implemented a McEliece cryptosystem based on extended Golay code using MATLAB. The extended Golay code has lots of practical applications. The main advantage of using extended Golay code is that it has codeword of length 24, a minimum Hamming distance of 8 allows us to detect 7-bit errors while correcting for 3 or fewer errors simultaneously and can be transmitted at high data rate. I. INTRODUCTION Over the last three decades, public key cryptosystems (Diffie-Hellman key exchange, the RSA cryptosystem, digital signature algorithm (DSA), and Elliptic curve cryptosystems) has become a crucial component of cyber security. In this regard, security depends on the difficulty of a definite number of theoretic problems (integer factorization or the discrete log problem). -

The Witt Designs, Golay Codes and Mathieu Groups
The Witt designs, Golay codes and Mathieu groups 1 The Golay codes Let V be a vector space over Fq with fixed basis e1, ..., en. A code C is a subset of V .A linear code is a subspace of V . The vector with all coordinates equal to zero (resp. one) will be denoted by 0 (resp. 1). The Hamming distance dH (u, v) between two vectors u, v ∈ V is the number P P of coordinates where they differ: when u = uiei, v = viei then dH (u, v) = |{i | ui 6= vi}|. The weight of a vector u is its number of nonzero coordinates, i.e., dH (u, 0). The minimum distance d(C) of a code C is min{dH (u, v) | u, v ∈ C, u 6= v}. The support of a vector is the set of coordinate positions where it has a nonzero coordinate. Theorem 1.1 There exist codes, unique up to isomorphism, with the indicated values of n, q, |C| and d(C): n q |C| d(C) name of C (i) 23 2 4096 7 binary Golay code (ii) 24 2 4096 8 extended binary Golay code (iii) 11 3 729 5 ternary Golay code (iv) 12 3 729 6 extended ternary Golay code Let us assume that the codes have been chosen such as to contain 0. Then each of these codes is linear. (The dimensions are 12, 12, 6, 6.) 1 The codes (i) and (iii) are perfect, i.e., the balls with radius 2 (d(C) − 1) around the code words partition the vector space. -

Hamming Code - Wikipedia, the Free Encyclopedia Hamming Code Hamming Code
Hamming code - Wikipedia, the free encyclopedia Hamming code Hamming code From Wikipedia, the free encyclopedia In telecommunication, a Hamming code is a linear error-correcting code named after its inventor, Richard Hamming. Hamming codes can detect and correct single-bit errors, and can detect (but not correct) double-bit errors. In contrast, the simple parity code cannot detect errors where two bits are transposed, nor can it correct the errors it can find. Contents [hide] • 1 History • 2 Codes predating Hamming ♦ 2.1 Parity ♦ 2.2 Two-out-of-five code ♦ 2.3 Repetition • 3 Hamming codes • 4 Example using the (11,7) Hamming code • 5 Hamming code (7,4) ♦ 5.1 Hamming matrices ♦ 5.2 Channel coding ♦ 5.3 Parity check ♦ 5.4 Error correction • 6 Hamming codes with additional parity • 7 See also • 8 References • 9 External links History Hamming worked at Bell Labs in the 1940s on the Bell Model V computer, an electromechanical relay-based machine with cycle times in seconds. Input was fed in on punch cards, which would invariably have read errors. During weekdays, special code would find errors and flash lights so the operators could correct the problem. During after-hours periods and on weekends, when there were no operators, the machine simply moved on to the next job. Hamming worked on weekends, and grew increasingly frustrated with having to restart his programs from scratch due to the unreliability of the card reader. Over the next few years he worked on the problem of error-correction, developing an increasingly powerful array of algorithms. -

The Theory of Error-Correcting Codes the Ternary Golay Codes and Related Structures
Math 28: The Theory of Error-Correcting Codes The ternary Golay codes and related structures We have seen already that if C is an extremal [12; 6; 6] Type III code then C attains equality in the LP bounds (and conversely the LP bounds show that any ternary (12; 36; 6) code is a translate of such a C); ear- lier we observed that removing any coordinate from C yields a perfect 2-error-correcting [11; 6; 5] ternary code. Since C is extremal, we also know that its Hamming weight enumerator is uniquely determined, and compute 3 3 3 3 3 3 12 6 6 3 9 12 WC (X; Y ) = (X(X + 8Y )) − 24(Y (X − Y )) = X + 264X Y + 440X Y + 24Y : Here are some further remarkable properties that quickly follow: A (5,6,12) Steiner system. The minimal words form 132 pairs fc; −cg with the same support. Let S be the family of these 132 supports. We claim S is a (5; 6; 12) Steiner system; that is, that any pentad (5-element 12 6 set of coordinates) is a subset of a unique hexad in S. Because S has the right size 5 5 , it is enough to show that no two hexads intersect in exactly 5 points. If they did, then we would have some c; c0 2 C, both of weight 6, whose supports have exactly 5 points in common. But then c0 would agree with either c or −c on at least 3 of these points (and thus on exactly 4, because (c; c0) = 0), making c0 ∓ c a nonzero codeword of weight less than 5 (and thus exactly 3), which is a contradiction. -

Geometry of the Mathieu Groups and Golay Codes
Proc. Indian Acad. Sci. (Math. Sci.), Vol. 98, Nos 2 and 3, December 1988, pp. 153-177. 9 Printed in India. Geometry of the Mathieu groups and Golay codes ERIC A LORD Centre for Theoretical Studies and Department of Applied Mathematics, Indian Institute of Science, Bangalore 560012, India MS received 11 January 1988 Abstraet. A brief review is given of the linear fractional subgroups of the Mathieu groups. The main part of the paper then deals with the proj~x-~tiveinterpretation of the Golay codes; these codes are shown to describe Coxeter's configuration in PG(5, 3) and Todd's configuration in PG(11, 2) when interpreted projectively. We obtain two twelve-dimensional representations of M24. One is obtained as the coUineation group that permutes the twelve special points in PC,(11, 2); the other arises by interpreting geometrically the automorphism group of the binary Golay code. Both representations are reducible to eleven-dimensional representations of M24. Keywords. Geometry; Mathieu groups; Golay codes; Coxeter's configuration; hemi- icosahedron; octastigms; dodecastigms. 1. Introduction We shall first review some of the known properties of the Mathieu groups and their linear fractional subgroups. This is mainly a brief resum6 of the first two of Conway's 'Three Lectures on Exceptional Groups' [3] and will serve to establish the notation and underlying concepts of the subsequent sections. The six points of the projective line PL(5) can be labelled by the marks of GF(5) together with a sixth symbol oo defined to be the inverse of 0. The symbol set is f~ = {0 1 2 3 4 oo}. -

Review of Binary Codes for Error Detection and Correction
` ISSN(Online): 2319-8753 ISSN (Print): 2347-6710 International Journal of Innovative Research in Science, Engineering and Technology (A High Impact Factor, Monthly, Peer Reviewed Journal) Visit: www.ijirset.com Vol. 7, Issue 4, April 2018 Review of Binary Codes for Error Detection and Correction Eisha Khan, Nishi Pandey and Neelesh Gupta M. Tech. Scholar, VLSI Design and Embedded System, TCST, Bhopal, India Assistant Professor, VLSI Design and Embedded System, TCST, Bhopal, India Head of Dept., VLSI Design and Embedded System, TCST, Bhopal, India ABSTRACT: Golay Code is a type of Error Correction code discovered and performance very close to Shanon‟s limit . Good error correcting performance enables reliable communication. Since its discovery by Marcel J.E. Golay there is more research going on for its efficient construction and implementation. The binary Golay code (G23) is represented as (23, 12, 7), while the extended binary Golay code (G24) is as (24, 12, 8). High speed with low-latency architecture has been designed and implemented in Virtex-4 FPGA for Golay encoder without incorporating linear feedback shift register. This brief also presents an optimized and low-complexity decoding architecture for extended binary Golay code (24, 12, 8) based on an incomplete maximum likelihood decoding scheme. KEYWORDS: Golay Code, Decoder, Encoder, Field Programmable Gate Array (FPGA) I. INTRODUCTION Communication system transmits data from source to transmitter through a channel or medium such as wired or wireless. The reliability of received data depends on the channel medium and external noise and this noise creates interference to the signal and introduces errors in transmitted data. -

Reed-Solomon Error Correction
R&D White Paper WHP 031 July 2002 Reed-Solomon error correction C.K.P. Clarke Research & Development BRITISH BROADCASTING CORPORATION BBC Research & Development White Paper WHP 031 Reed-Solomon Error Correction C. K. P. Clarke Abstract Reed-Solomon error correction has several applications in broadcasting, in particular forming part of the specification for the ETSI digital terrestrial television standard, known as DVB-T. Hardware implementations of coders and decoders for Reed-Solomon error correction are complicated and require some knowledge of the theory of Galois fields on which they are based. This note describes the underlying mathematics and the algorithms used for coding and decoding, with particular emphasis on their realisation in logic circuits. Worked examples are provided to illustrate the processes involved. Key words: digital television, error-correcting codes, DVB-T, hardware implementation, Galois field arithmetic © BBC 2002. All rights reserved. BBC Research & Development White Paper WHP 031 Reed-Solomon Error Correction C. K. P. Clarke Contents 1 Introduction ................................................................................................................................1 2 Background Theory....................................................................................................................2 2.1 Classification of Reed-Solomon codes ...................................................................................2 2.2 Galois fields............................................................................................................................3 -

Linear Block Codes
Linear Block codes (n, k) Block codes k – information bits n - encoded bits Block Coder Encoding operation n-digit codeword made up of k-information digits and (n-k) redundant parity check digits. The rate or efficiency for this code is k/n. 푘 푁푢푚푏푒푟 표푓 푛푓표푟푚푎푡표푛 푏푡푠 퐶표푑푒 푒푓푓푐푒푛푐푦 푟 = = 푛 푇표푡푎푙 푛푢푚푏푒푟 표푓 푏푡푠 푛 푐표푑푒푤표푟푑 Note: unlike source coding, in which data is compressed, here redundancy is deliberately added, to achieve error detection. SYSTEMATIC BLOCK CODES A systematic block code consists of vectors whose 1st k elements (or last k-elements) are identical to the message bits, the remaining (n-k) elements being check bits. A code vector then takes the form: X = (m0, m1, m2,……mk-1, c0, c1, c2,…..cn-k) Or X = (c0, c1, c2,…..cn-k, m0, m1, m2,……mk-1) Systematic code: information digits are explicitly transmitted together with the parity check bits. For the code to be systematic, the k-information bits must be transmitted contiguously as a block, with the parity check bits making up the code word as another contiguous block. Information bits Parity bits A systematic linear block code will have a generator matrix of the form: G = [P | Ik] Systematic codewords are sometimes written so that the message bits occupy the left-hand portion of the codeword and the parity bits occupy the right-hand portion. Parity check matrix (H) Will enable us to decode the received vectors. For each (kxn) generator matrix G, there exists an (n-k)xn matrix H, such that rows of G are orthogonal to rows of H i.e., GHT = 0, where HT is the transpose of H. -

A Parallel Algorithm for Query Adaptive, Locality Sensitive Hash
A CUDA Based Parallel Decoding Algorithm for the Leech Lattice Locality Sensitive Hash Family A thesis submitted to the Division of Research and Advanced Studies of the University of Cincinnati in partial fulfillment of the requirements for the degree of MASTER OF SCIENCE in the School of Electric and Computing Systems of the College of Engineering and Applied Sciences November 03, 2011 by Lee A Carraher BSCE, University of Cincinnati, 2008 Thesis Advisor and Committee Chair: Dr. Fred Annexstein Abstract Nearest neighbor search is a fundamental requirement of many machine learning algorithms and is essential to fuzzy information retrieval. The utility of efficient database search and construction has broad utility in a variety of computing fields. Applications such as coding theory and compression for electronic commu- nication systems as well as use in artificial intelligence for pattern and object recognition. In this thesis, a particular subset of nearest neighbors is consider, referred to as c-approximate k-nearest neighbors search. This particular variation relaxes the constraints of exact nearest neighbors by introducing a probability of finding the correct nearest neighbor c, which offers considerable advantages to the computational complexity of the search algorithm and the database overhead requirements. Furthermore, it extends the original nearest neighbors algorithm by returning a set of k candidate nearest neighbors, from which expert or exact distance calculations can be considered. Furthermore thesis extends the implementation of c-approximate k-nearest neighbors search so that it is able to utilize the burgeoning GPGPU computing field. The specific form of c-approximate k-nearest neighbors search implemented is based on the locality sensitive hash search from the E2LSH package of Indyk and Andoni [1]. -
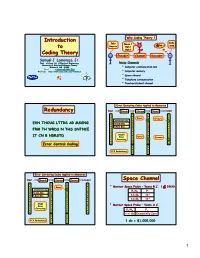
Introduction to Coding Theory
Introduction Why Coding Theory ? Introduction Info Info Noise ! Info »?# Sink to Source Heh ! Sink Heh ! Coding Theory Encoder Channel Decoder Samuel J. Lomonaco, Jr. Dept. of Comp. Sci. & Electrical Engineering Noisy Channels University of Maryland Baltimore County Baltimore, MD 21250 • Computer communication line Email: [email protected] WebPage: http://www.csee.umbc.edu/~lomonaco • Computer memory • Space channel • Telephone communication • Teacher/student channel Error Detecting Codes Applied to Memories Redundancy Input Encode Storage Detect Output 1 1 1 1 0 0 0 0 1 1 Error 1 Erasure 1 1 31=16+5 Code 1 0 ? 0 0 0 0 EVN THOUG LTTRS AR MSSNG 1 16 Info Bits 1 1 1 0 5 Red. Bits 0 0 0 0 0 0 0 FRM TH WRDS N THS SNTNCE 1 1 1 1 0 0 0 0 1 1 1 Double 1 IT CN B NDRSTD 0 0 0 0 1 Error 1 Error 1 Erasure 1 1 Detecting 1 0 ? 0 0 0 0 1 1 1 1 Error Control Coding 0 0 1 1 0 0 31% Redundancy 1 1 1 1 Error Correcting Codes Applied to Memories Input Encode Storage Correct Output Space Channel 1 1 1 1 0 0 0 0 Mariner Space Probe – Years B.C. ( ≤ 1964) 1 1 Error 1 1 • 1 31=16+5 Code 1 0 1 0 0 0 0 Eb/N0 Pe 16 Info Bits 1 1 1 1 -3 0 5 Red. Bits 0 0 0 6.8 db 10 0 0 0 0 -5 1 1 1 1 9.8 db 10 0 0 0 0 1 1 1 Single 1 0 0 0 0 Error 1 1 • Mariner Space Probe – Years A.C.