The Computational Complexity of Evolutionarily Stable Strategies
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Evolutionary Stable Strategy Application of Nash Equilibrium in Biology
GENERAL ARTICLE Evolutionary Stable Strategy Application of Nash Equilibrium in Biology Jayanti Ray-Mukherjee and Shomen Mukherjee Every behaviourally responsive animal (including us) make decisions. These can be simple behavioural decisions such as where to feed, what to feed, how long to feed, decisions related to finding, choosing and competing for mates, or simply maintaining ones territory. All these are conflict situations between competing individuals, hence can be best understood Jayanti Ray-Mukherjee is using a game theory approach. Using some examples of clas- a faculty member in the School of Liberal Studies sical games, we show how evolutionary game theory can help at Azim Premji University, understand behavioural decisions of animals. Game theory Bengaluru. Jayanti is an (along with its cousin, optimality theory) continues to provide experimental ecologist who a strong conceptual and theoretical framework to ecologists studies mechanisms of species coexistence among for understanding the mechanisms by which species coexist. plants. Her research interests also inlcude plant Most of you, at some point, might have seen two cats fighting. It invasion ecology and is often accompanied with the cats facing each other with puffed habitat restoration. up fur, arched back, ears back, tail twitching, with snarls, growls, Shomen Mukherjee is a and howls aimed at each other. But, if you notice closely, they faculty member in the often try to avoid physical contact, and spend most of their time School of Liberal Studies in the above-mentioned behavioural displays. Biologists refer to at Azim Premji University, this as a ‘limited war’ or conventional (ritualistic) strategy (not Bengaluru. He uses field experiments to study causing serious injury), as opposed to dangerous (escalated) animal behaviour and strategy (Figure 1) [1]. -
![Game Theory]: Basics of Game Theory](https://docslib.b-cdn.net/cover/5981/game-theory-basics-of-game-theory-195981.webp)
Game Theory]: Basics of Game Theory
Artificial Intelligence Methods for Social Good M2-1 [Game Theory]: Basics of Game Theory 08-537 (9-unit) and 08-737 (12-unit) Instructor: Fei Fang [email protected] Wean Hall 4126 1 5/8/2018 Quiz 1: Recap: Optimization Problem Given coordinates of 푛 residential areas in a city (assuming 2-D plane), denoted as 푥1, … , 푥푛, the government wants to find a location that minimizes the sum of (Euclidean) distances to all residential areas to build a hospital. The optimization problem can be written as A: min |푥푖 − 푥| 푥 푖 B: min 푥푖 − 푥 푥 푖 2 2 C: min 푥푖 − 푥 푥 푖 D: none of above 2 Fei Fang 5/8/2018 From Games to Game Theory The study of mathematical models of conflict and cooperation between intelligent decision makers Used in economics, political science etc 3/72 Fei Fang 5/8/2018 Outline Basic Concepts in Games Basic Solution Concepts Compute Nash Equilibrium Compute Strong Stackelberg Equilibrium 4 Fei Fang 5/8/2018 Learning Objectives Understand the concept of Game, Player, Action, Strategy, Payoff, Expected utility, Best response Dominant Strategy, Maxmin Strategy, Minmax Strategy Nash Equilibrium Stackelberg Equilibrium, Strong Stackelberg Equilibrium Describe Minimax Theory Formulate the following problem as an optimization problem Find NE in zero-sum games (LP) Find SSE in two-player general-sum games (multiple LP and MILP) Know how to find the method/algorithm/solver/package you can use for solving the games Compute NE/SSE by hand or by calling a solver for small games 5 Fei Fang 5/8/2018 Let’s Play! Classical Games -

Collusion Constrained Equilibrium
Theoretical Economics 13 (2018), 307–340 1555-7561/20180307 Collusion constrained equilibrium Rohan Dutta Department of Economics, McGill University David K. Levine Department of Economics, European University Institute and Department of Economics, Washington University in Saint Louis Salvatore Modica Department of Economics, Università di Palermo We study collusion within groups in noncooperative games. The primitives are the preferences of the players, their assignment to nonoverlapping groups, and the goals of the groups. Our notion of collusion is that a group coordinates the play of its members among different incentive compatible plans to best achieve its goals. Unfortunately, equilibria that meet this requirement need not exist. We instead introduce the weaker notion of collusion constrained equilibrium. This al- lows groups to put positive probability on alternatives that are suboptimal for the group in certain razor’s edge cases where the set of incentive compatible plans changes discontinuously. These collusion constrained equilibria exist and are a subset of the correlated equilibria of the underlying game. We examine four per- turbations of the underlying game. In each case,we show that equilibria in which groups choose the best alternative exist and that limits of these equilibria lead to collusion constrained equilibria. We also show that for a sufficiently broad class of perturbations, every collusion constrained equilibrium arises as such a limit. We give an application to a voter participation game that shows how collusion constraints may be socially costly. Keywords. Collusion, organization, group. JEL classification. C72, D70. 1. Introduction As the literature on collective action (for example, Olson 1965) emphasizes, groups often behave collusively while the preferences of individual group members limit the possi- Rohan Dutta: [email protected] David K. -

Contemporaneous Perfect Epsilon-Equilibria
Games and Economic Behavior 53 (2005) 126–140 www.elsevier.com/locate/geb Contemporaneous perfect epsilon-equilibria George J. Mailath a, Andrew Postlewaite a,∗, Larry Samuelson b a University of Pennsylvania b University of Wisconsin Received 8 January 2003 Available online 18 July 2005 Abstract We examine contemporaneous perfect ε-equilibria, in which a player’s actions after every history, evaluated at the point of deviation from the equilibrium, must be within ε of a best response. This concept implies, but is stronger than, Radner’s ex ante perfect ε-equilibrium. A strategy profile is a contemporaneous perfect ε-equilibrium of a game if it is a subgame perfect equilibrium in a perturbed game with nearly the same payoffs, with the converse holding for pure equilibria. 2005 Elsevier Inc. All rights reserved. JEL classification: C70; C72; C73 Keywords: Epsilon equilibrium; Ex ante payoff; Multistage game; Subgame perfect equilibrium 1. Introduction Analyzing a game begins with the construction of a model specifying the strategies of the players and the resulting payoffs. For many games, one cannot be positive that the specified payoffs are precisely correct. For the model to be useful, one must hope that its equilibria are close to those of the real game whenever the payoff misspecification is small. To ensure that an equilibrium of the model is close to a Nash equilibrium of every possible game with nearly the same payoffs, the appropriate solution concept in the model * Corresponding author. E-mail addresses: [email protected] (G.J. Mailath), [email protected] (A. Postlewaite), [email protected] (L. -

Success Rates in Simplified Threshold Public Goods Games - a Theoretical Model
Success rates in simplified threshold public goods games - a theoretical model by Christian Feige No. 70 | JUNE 2015 WORKING PAPER SERIES IN ECONOMICS KIT – University of the State of Baden-Wuerttemberg and National Laboratory of the Helmholtz Association econpapers.wiwi.kit.edu Impressum Karlsruher Institut für Technologie (KIT) Fakultät für Wirtschaftswissenschaften Institut für Volkswirtschaftslehre (ECON) Schlossbezirk 12 76131 Karlsruhe KIT – Universität des Landes Baden-Württemberg und nationales Forschungszentrum in der Helmholtz-Gemeinschaft Working Paper Series in Economics No. 70, June 2015 ISSN 2190-9806 econpapers.wiwi.kit.edu Success rates in simplied threshold public goods games a theoretical model Christian Feigea,¦ aKarlsruhe Institute of Technology (KIT), Institute of Economics (ECON), Neuer Zirkel 3, 76131 Karlsruhe, Germany Abstract This paper develops a theoretical model based on theories of equilibrium selection in order to predict success rates in threshold public goods games, i.e., the probability with which a group of players provides enough contri- bution in sum to exceed a predened threshold value. For this purpose, a prototypical version of a threshold public goods game is simplied to a 2 ¢ 2 normal-form game. The simplied game consists of only one focal pure strat- egy for positive contributions aiming at an ecient allocation of the threshold value. The game's second pure strategy, zero contributions, represents a safe choice for players who do not want to risk coordination failure. By calculat- ing the stability sets of these two pure strategies, success rates can be put in explicit relation to the game parameters. It is also argued that this approach has similarities with determining the relative size of the strategies' basins of attraction in a stochastic dynamical system (cf. -

Monetary Policy Obeying the Taylor Principle Turns Prices Into Strategic Substitutes
A Service of Leibniz-Informationszentrum econstor Wirtschaft Leibniz Information Centre Make Your Publications Visible. zbw for Economics Cornand, Camille; Heinemann, Frank Working Paper Monetary Policy Obeying the Taylor Principle Turns Prices Into Strategic Substitutes Discussion Paper, No. 90 Provided in Cooperation with: University of Munich (LMU) and Humboldt University Berlin, Collaborative Research Center Transregio 190: Rationality and Competition Suggested Citation: Cornand, Camille; Heinemann, Frank (2018) : Monetary Policy Obeying the Taylor Principle Turns Prices Into Strategic Substitutes, Discussion Paper, No. 90, Ludwig- Maximilians-Universität München und Humboldt-Universität zu Berlin, Collaborative Research Center Transregio 190 - Rationality and Competition, München und Berlin This Version is available at: http://hdl.handle.net/10419/185760 Standard-Nutzungsbedingungen: Terms of use: Die Dokumente auf EconStor dürfen zu eigenen wissenschaftlichen Documents in EconStor may be saved and copied for your Zwecken und zum Privatgebrauch gespeichert und kopiert werden. personal and scholarly purposes. Sie dürfen die Dokumente nicht für öffentliche oder kommerzielle You are not to copy documents for public or commercial Zwecke vervielfältigen, öffentlich ausstellen, öffentlich zugänglich purposes, to exhibit the documents publicly, to make them machen, vertreiben oder anderweitig nutzen. publicly available on the internet, or to distribute or otherwise use the documents in public. Sofern die Verfasser die Dokumente unter Open-Content-Lizenzen -
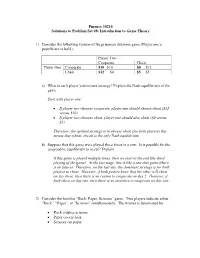
Problem Set #8 Solutions: Introduction to Game Theory
Finance 30210 Solutions to Problem Set #8: Introduction to Game Theory 1) Consider the following version of the prisoners dilemma game (Player one’s payoffs are in bold): Player Two Cooperate Cheat Player One Cooperate $10 $10 $0 $12 Cheat $12 $0 $5 $5 a) What is each player’s dominant strategy? Explain the Nash equilibrium of the game. Start with player one: If player two chooses cooperate, player one should choose cheat ($12 versus $10) If player two chooses cheat, player one should also cheat ($0 versus $5). Therefore, the optimal strategy is to always cheat (for both players) this means that (cheat, cheat) is the only Nash equilibrium. b) Suppose that this game were played three times in a row. Is it possible for the cooperative equilibrium to occur? Explain. If this game is played multiple times, then we start at the end (the third playing of the game). At the last stage, this is like a one shot game (there is no future). Therefore, on the last day, the dominant strategy is for both players to cheat. However, if both parties know that the other will cheat on day three, then there is no reason to cooperate on day 2. However, if both cheat on day two, then there is no incentive to cooperate on day one. 2) Consider the familiar “Rock, Paper, Scissors” game. Two players indicate either “Rock”, “Paper”, or “Scissors” simultaneously. The winner is determined by Rock crushes scissors Paper covers rock Scissors cut paper Indicate a -1 if you lose and +1 if you win. -

Real-Time Monitoring in a Public Goods Game*
Real-time Monitoring in a Public Goods Game* Simin He† and Xun Zhu‡ July 28, 2020 Abstract Public goods problems are prevalent in economics and are challenging to resolve. In this study, we investigate a novel continuous-time incremental commitment mecha- nism. Within a fixed time period, people can choose when to stop their contributions from increasing exogenously, and their actions are observed by others. We show both theoretically and experimentally that it is a very effective mechanism to help improve contribution. Moreover, we compare this mechanism with other mechanisms under similar real-time environment, and find that the mechanism becomes ineffective when the incremental commitment feature is absent. Our findings can be potentially extended to other social dilemma situations. Keywords: Public goods, continuous time, incremental commitment, cheap talk. JEL codes: C72, C92, D82. *The authors sincerely thank Syngjoo Choi, Bin Miao, Lan Yao, and the participants of the Nottingham CeDEx China Workshop on Behavioral and Experimental Economics and the Virtual East Asia Experimental and Behavioral Experimental Seminar Series for their helpful comments. †School of Economics, Shanghai University of Finance and Economics, 111 Wuchuan Rd, 200433 Shanghai, China. E-mail: [email protected]. ‡School of Management, Fudan University, 670 Guoshun Rd, 200433 Shanghai, China. E-mail: zhuxun [email protected]. 1 Introduction Public goods games are very prevalent in economics, and their desired outcome requires people to contribute to a public pool efficiently. For example, building a dam that benefits people living around it requires everyone to contribute; fighting global warming problem requires all countries to reduce their carbon emissions. -

Monetary Policy Obeying the Taylor Principle Turns Prices Into Strategic Substitutes Camille Cornand, Frank Heinemann
Monetary Policy obeying the Taylor Principle Turns Prices into Strategic Substitutes Camille Cornand, Frank Heinemann To cite this version: Camille Cornand, Frank Heinemann. Monetary Policy obeying the Taylor Principle Turns Prices into Strategic Substitutes. 2018. halshs-01759692 HAL Id: halshs-01759692 https://halshs.archives-ouvertes.fr/halshs-01759692 Preprint submitted on 5 Apr 2018 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. WP 1805 – April 2018 Monetary Policy obeying the Taylor Principle Turns Prices into Strategic Substitutes Camille Cornand, Frank Heinemann Abstract: Monetary policy affects the degree of strategic complementarity in firms’ pricing decisions if it responds to the aggregate price level. In normal times, when monopolistic competitive firms increase their prices, the central bank raises interest rates, which lowers consumption demand and creates an incentive for firms to reduce their prices. Thereby, monetary policy reduces the degree of strategic complementarities among firms’ pricing decisions and even turns prices into strategic substitutes if the effect of interest rates on demand is sufficiently strong. We show that this condition holds when monetary policy follows the Taylor principle. By contrast, in a liquidity trap where monetary policy is restricted by the zero lower bound, pricing decisions are strategic complements. -

Section Note 3
Section Note 3 Ariella Kahn-Lang and Guthrie Gray-Lobe∗ February 13th 2013 Agenda 1. Game Trees 2. Writing out Strategies and the Strategy Space 3. Backwards Induction 1 Game Trees Let's review the basic elements of game trees (extensive form games). Remember, we can write any game in either its normal (matrix) form or its extensive (tree) form - which representation we use is mainly a question of which solution concept we want to implement. Game trees are particularly useful for representing dynamic (sequential) games, primarily be- cause they easily allow us to implement the simple solution concept of backwards induction (see later). 1.1 Dynamic Games vs. Simultaneous Games Many important economic applications in game theory cannot be described by a simultaneous move game. Recall that a simultaneous game is one where all players were choosing their actions without any information about actions chosen by other players. A dynamic game, in contrast, is one where at least one player at some point of the game is choosing his action with some information about actions chosen previously. While dynamic games are often sequential over time, what matters is not the timing, but the information a player holds about previous moves in the game, because this is what enables them to condition their strategy on previous moves. For this reason, the `order' in which we draw a game tree matters only in getting the flow of information correctly. In simultaneous games, we can draw the game tree either way round and it represents the same game. ∗Thanks to previous years' TF's for making their section materials available for adaptation. -

Quantum Tic-Tac-Toe: a Teaching Metaphor for Superposition In
Quantum tic-tac-toe: A teaching metaphor for superposition in quantum mechanics Allan Goff Novatia Labs, 9580 Oak Ave Parkway, Suite 7-#110, Folsom, California 95630 ͑Received 28 December 2005; accepted 19 May 2006͒ Quantum tic-tac-toe was developed as a metaphor for the counterintuitive nature of superposition exhibited by quantum systems. It offers a way of introducing quantum physics without advanced mathematics, provides a conceptual foundation for understanding the meaning of quantum mechanics, and is fun to play. A single superposition rule is added to the child’s game of classical tic-tac-toe. Each move consists of a pair of marks subscripted by the number of the move ͑“spooky” marks͒ that must be placed in different squares. When a measurement occurs, one spooky mark becomes real and the other disappears. Quantum tic-tac-toe illustrates a number of quantum principles including states, superposition, collapse, nonlocality, entanglement, the correspondence principle, interference, and decoherence. The game can be played on paper or on a white board. A Web-based version provides a refereed playing board to facilitate the mechanics of play, making it ideal for classrooms with a computer projector. © 2006 American Association of Physics Teachers. ͓DOI: 10.1119/1.2213635͔ I. INTRODUCTION with hyphens, 1–3, 6–9,… Classical boards are smaller with single lines, unnumbered squares, and utilize only unsub- Quantum tic-tac-toe was developed in part to provide both scripted marks. a metaphor and an interactive activity for students to grapple Superposition in quantum systems seems to imply that an with the weirdness of the quantum world. -

Lecture Notes
Chapter 8 Further Applications This chapter is devoted to exercises that apply the ideas developed in previous chapters to various real-world problems.All of the exercises come from past exams and homework problems. The reader is recommended to solve them before studying the solutions. Many of the games in this chapter are supermodular, a class of games for which there are powerful general theorems. These theorems could be used to find the rationalizable set relatively easily. I will not use these theorems. Instead, I will explicitly apply the iterated elimination procedure and use the results from the previous chapters. This will hopefully drill the logic of rationalizability better. Moreover, the knowledge of the procedure clarifies the role of knowledge and rationality assumptions, clarifying how sensitive the solution could be to such assumptions. 8.1 Partnership Consider an employer and a worker. The employer provides the capital 0 (in terms ≥ of investment in technology, etc.) and the worker provides the labor 0 (in terms of ≥ the investment in the human capital) to produce ( )= for some (0 1) with + 1 . They share the output equally. The parties ∈ determine their investment level (the employer’s capital and the worker’s labor ) simultaneously. The per-unit costs of capital and the labor for the employer and the 119 120 CHAPTER 8. FURTHER APPLICATIONS worker are 0 and 0 respectively. The worker cannot put more than some fixed positve ¯. The payoffsfor theemployerand theworkerare 1 ( )= ( ) 2 − and 1 ( )= ( ) 2 − respectively. Everything described up to here is common knowledge. Exercise 8.1 Write this formally as a game in normal form.