Role of Engineers in Nation Building VIVA Institute of Technology
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Politics of Water Contestation in the Mumbai-Thane Region of India
Western University Scholarship@Western Electronic Thesis and Dissertation Repository 4-14-2015 12:00 AM Claims of the City? Rights of the Countryside? Politics of Water Contestation in the Mumbai-Thane Region of India Bharat Khushal Punjabi The University of Western Ontario Supervisor Dr. Belinda Dodson The University of Western Ontario Graduate Program in Geography A thesis submitted in partial fulfillment of the equirr ements for the degree in Doctor of Philosophy © Bharat Khushal Punjabi 2015 Follow this and additional works at: https://ir.lib.uwo.ca/etd Part of the Asian Studies Commons, Human Geography Commons, and the Nature and Society Relations Commons Recommended Citation Punjabi, Bharat Khushal, "Claims of the City? Rights of the Countryside? Politics of Water Contestation in the Mumbai-Thane Region of India" (2015). Electronic Thesis and Dissertation Repository. 2853. https://ir.lib.uwo.ca/etd/2853 This Dissertation/Thesis is brought to you for free and open access by Scholarship@Western. It has been accepted for inclusion in Electronic Thesis and Dissertation Repository by an authorized administrator of Scholarship@Western. For more information, please contact [email protected]. Claims of the City? Rights of the Countryside? Politics of Water Contestation in the Mumbai-Thane Region of India Integrated-Article Thesis By Bharat Punjabi Graduate Program in Geography A thesis submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy The School of Graduate and Postdoctoral Studies The University of Western Ontario London, Ontario, Canada © Bharat K. Punjabi 2015 !i Abstract This dissertation comprises three papers that focus on the interplay of formal and informal institutional processes in the sharing of water between the Mumbai Metropolitan region and an agricultural area to its north and east in Thane district. -

Late Shri Vishnu Waman Thakur Charitable Trust
Late Shri Vishnu Waman Thakur Charitable Trust Instrument Amount Rating Action In Rs. Crore September 2016 Fund Based Limits rated on a long term scale Term Loan 10.41 [ICRA]BBB-(Stable) –Reaffirmed/ Suspension Revoked ICRA has revoked the suspension and re-affirmed the long-term rating outstanding on the Rs. 10.41 crore term loan of Late Shri Vishnu Waman Thakur Charitable Trust at [ICRA]BBB- (pronounced ICRA triple B Minus). The outlook on the long term rating is Stable. The rating reaffirmation takes into account the long standing experience of the trustees of Late Shri Vishnu Waman Thakur Charitable Trust (LSVWT/Trust) spanning more than two decades in the education sector, the proven track record of the school and junior college with steady increase in enrolments over the years and the diversified course offerings coupled with well established reputation of the trust in the region. The rating continues to draws comfort from the trust’s favorable financial profile characterized by healthy profit margins, lightly leverage capital structure and comfortable coverage indicators. Further, the trust’s ownership of land and building supports better operating margins and provides adequate availability of space for future expansion. The rating, however, continues to remain constrained by sub optimal occupancy levels for some of the institutes of the trust and the high level of concentration of revenues towards the school and junior college. ICRA also takes note of the intense competition from other schools and colleges in the nearby areas offering similar course also exert pressure on ability to attract and retain experienced faculty. -

Biennial Election to the Maharashtra Council
BIENNIAL ELECTION TO THE MAHARASHTRA LEGISLATIVE COUNCIL ELECTION – 2016 ---------------------------------------------------------------------------------------------------------------------------------------- THANE LOCAL AUTHORITIES LEGISLATIVE COUNCIL CONSTITUENCY ELECTORAL ROLL – 2016 BIENNAIL ELECTION TO THE MAHARASHTRA LEGISLATIVE COUNCIL FROM THANE LOCAL AUTHORITIES'S CONSTITUENCY-2016 ELECTORAL ROLL – 2016 INDEX Sr.No. Name of the Local Authority Female Male Total 1 Dahanu Municipal Council, Dahanu Taluk-Dahanu, District-Palghar 12 13 25 2 Jawhar Municipal Council, Jawhar, Taluk-Jawhar, District-Palghar 9 10 19 3 A) Zilla Parishad, Palghar Taluka Palghar District Palghar 37 28 65 B) Palghar Municipal Coucil, Palghar Taluka Palghar District Palghar 14 17 31 96 4 Shahapur Nagarpanchayt Shahapur Taluka-Shahapur, District Thane 9 10 19 5 Vasai-Virar Municipal Corporation, Vasai Taluka-Vasai, District-Palghar 58 62 120 6 Bhiwandi-Nizampur City Municipal Corporation, Bhiwandi Taluka Bhiwandi 48 47 95 District Thane 7 Kalyan Dombivali Municipal Corporation Taluka Kalyan District Thane 66 61 127 8 Murbad Nagarpanchayt Murbad, Taluka-Murbad, District Thane 10 9 19 9 Ulhasnagar Municipal Corporation, Ulhasnagar, Taluka Ulhasnagar, District Thane 42 37 79 10 Mira-Bhayandar Municipal Corporation,Bhayandar (W) Taluka District Thane 49 49 98 11 A) Zilla Parishad Thane, Taluk, District Thane 0 0 0 B) Thane Municipal Corporation, Thane Taluka District Thane 65 68 133 12 Navi Mumbai Municipal Corporation, Navi Mumbai, Taluka District Thane 63 53 116 13 A) Ambernath Municipal Council, Ambernath Taluka Ambernath District Thane 30 32 62 B) Kulgaon-Badlapur Municipal Council, Badlapur, Taluka Ambernath District 26 26 52 Thane ------------ 114 Total Electors 538 522 1060 BIENNIAL ELECTIONS TO THE MAHARASHTRA LEGISLATIVE COUNCIL FROM THANE LOCAL AUTHORITIESCONSTITUENCY ELECTORAL ROLL 2016 DISTRICT HANE NAME OF LOCAL AUTHORITY COUNCIL:- DAHANU MUNICIPAL COUNCIL ELECTORAL PART NO:-1/13 Father / Husband / Educational Name of the Council in which Sr. -

Place of Mahaparayan Maha-Recital of Shri-Sai Satcharita at Mumbai It Is Fascinating to Observe the Growth of Certain Places
Place of Mahaparayan Maha-recital of Shri-Sai Satcharita at Mumbai It is fascinating to observe the growth of certain places that has an immense significance for the Sai-Devotees, today. The land on which Samadhi Mandirat Shirdi stands, was once upon a time a cactus jungle and was used as a dumping ground. Similarly the location in Mumbai where Maha Recital of Shri - Sai Satcharita was organized recently, was also created out of a dump yard. Thanks to numerous selfless and hard working Sai-Devotees. The triangular piece of land near Canara Bank at Bandra-Kurla Complex in Mumbai was nothing but a thick jungle with marshy land when Sai Sansthan Managing Committee had visited it some years ago. The unhygienic environment filled with a foul smell was an assault on one senses and sensibilities. However in due course of time under the expert guidance of Shri Nitin Desai, a renowned art-director from Indian Film industry, the dark dungeon was transformed into a divine den .Parayandarshan and refreshment pavilions were erected. A special tent was set up for reciter's residence. Huge idols of god- goddesses were installed on the wooden platforms . Finally on 15th December the 'Parayandham' was ready to welcome all .By observing this one can not but agree with the adage that something good originates from ashes and rough stones give birth to a beautiful sculpture. Thus this place like Lendibaug in Shirdi provided bread and butter to many. The main gate reminding one about the glory of ancient palaces of India. Two statues of elephants that almost looked real , welcomed the visitors. -

City Building and Regime Creation in the Peripheries for Mumbai
Case Study City Building and Regime Creation in the Peripheries for Mumbai People, Places and Infrastructure: Countering urban violence and promoting justice in Mumbai, Rio, and Durban Lalitha Kamath Radhika Raj Maps: Nisha Kundar Photographs: Author March 25, 2016 Centre for Urban Policy and Governance School of Habitat Studies Tata Institute of Social Sciences This work was carried out with financial support from the UK Government's Department for International Development and the International Development Research Centre, Canada. The opinions expressed in this work do not necessarily reflect those of DFID or IDRC. iv Acknowledgements This work has been a long engagement with several respondents from, but not limited to, Vasai Virar who have helped us decode this complex field. We greatly benefitted from our discussions with social workers, activists, musicians, politicians, researchers, students, party members, academicians, urban planners, architects, government officials and workers. We would like to acknowledge the time they spent sharing their struggles, strategies and insights on the rapidly transforming periphery. We would also like to thank government officials at the Vasai Virar Municipal Corporation for their support through the project. Several people allowed us access to otherwise difficult-to-reach places and deserve special thanks. Sachin Marti gave us our first introduction to the emerging city. Ramanuj Pathak, our project fellow, opened up a whole new world through his music and performances on the urbanising periphery. Mahendra Jadhav, provided us with great support during fieldwork in an uncertain terrain. We are very grateful to them. Over the course of the project, we have had several interns and research officers who have contributed to building this study. -

Prouspectus 2020-2021
PROSPECTUS | 2020-21 LATE SHRI. VISHNU WAMAN THAKUR CHARITABLE TRUST'S VIVA SCHOOL OF ARCHITECTURE PROSPECTUS | 2020-21 ABOUT US Late Shri VishNu WamaN Thakur Charitable Trust was formed iN the year 1988 uNder the leadership of Shri HiteNdra Thakur, MLA of Vasai taluka. The trust was formed to haNdle several coNcerNs aNd to uplift a remote area like Vasai regioN. The provisioN of educatioN medical aNd social facilities to the resideNts of the area was the primarily focus .It is the oNly trust which ruNs the maximum Number of courses after Mumbai uNiversity. VIVA School of Architecture (VSOA) is affiliated by Mumbai UNiversity aNd approved by CouNcil of Architecture (COA). Started iN the year 2010 uNder the leadership of Prof. Dhiraj Salhotra aNd Prof. Chakor Mehta with aN iNtake of 40 studeNts. SiNce its iNceptioN, the school has beeN rapidly developiNg towards the visioN of takiNg architectural educatioN beyoNd muNdaNe curriculum aNd achieviNg higher goals of holistic approach. The discipliNed academic approach helps the pupils to iNculcate iN them the qualities of siNcerity, puNctuality aNd respoNsibility. The fraterNity focuses oN providiNg the future architects with the best possible kNowledge. The professors give persoNal atteNtioN to each aNd every iNdividual aNd help them iN moldiNg themselves iNto good humaN beiNg. The youNg miNds are eNcouraged to thiNk ratioNally aNd develop aN iNquisitive attitude towards life aNd architecture as a whole. The priNcipal aloNg with the faculty aims at NurturiNg the studeNts to become respoNsible citizeNs aNd stroNg iNdividuals with a visioN to make a differeNce while beiNg seNsitive towards the society. -

Late Shri Vishnu Waman Thakur Charitable Trust
Late Shri Vishnu Waman Thakur Charitable Trust April 09, 2018 Summary of Rated Instrument: Previous Rated Current Rated Instrument Amount Amount Rating Action (Rs. crore) (Rs. crore) Fund based-Term 10.41 10.41 [ICRA]BBB- (Stable) ISSUER NOT COOPERATING*; Loan Rating moved to the ‘Issuer Not Cooperating’ category Total 10.41 10.41 *Issuer did not co-operate; based on best available information. Rationale ICRA has moved the long term rating for the bank facilities of Late Shri Vishnu Waman Thakur Charitable Trust (LSVWT) to the ‘Issuer Not Cooperating’ category. The rating is now denoted as “[ICRA]BBB- (Stable) ISSUER NOT COOPERATING” ICRA has been trying to seek information from the entity so as to monitor its performance, but despite repeated requests by ICRA, the entity’s management has remained non-cooperative. The current rating action has been taken by ICRA basis best available/dated/ limited information on the issuers’ performance. Accordingly the lenders, investors and other market participants are advised to exercise appropriate caution while using this rating as the rating may not adequately reflect the credit risk profile of the entity. Analytical approach ICRA has applied its rating methodologies/policies as indicated below: Links to applicable criteria: Policy in respect of non-cooperation by the rated entity Higher Education Sector About the company: Late Shri Vishnu Waman Thakur Charitable Trust was established in October 1987 by MLA Hitendra Thakur along with 9 other trustees, with the view of providing education in the Vasai-Virar region of Maharashtra. The first educational institute built by the trust was Utkarsh Vidyalaya, a school which was started in 1989-90 with pre-school facilities. -
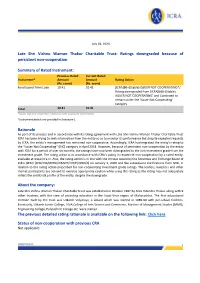
Late Shri Vishnu Waman Thakur Charitable Trust: Ratings Downgraded Because of Persistent Non-Cooperation
July 03, 2020 Late Shri Vishnu Waman Thakur Charitable Trust: Ratings downgraded because of persistent non-cooperation Summary of Rated Instrument: Previous Rated Current Rated Instrument^ Amount Amount Rating Action (Rs. crore) (Rs. crore) Fund based-Term Loan 10.41 10.41 [ICRA]BB+(Stable) ISSUER NOT COOPERATING*/ Rating downgraded from [ICRA]BBB-(Stable) ISSUER NOT COOPERATING’ and Continued to remain under the ‘Issuer Not Cooperating’ category Total 10.41 10.41 *Issuer did not cooperate; based on best available information. ^Instrument details are provided in Annexure-1 Rationale As part of its process and in accordance with its rating agreement with Late Shri Vishnu Waman Thakur Charitable Trust ICRA has been trying to seek information from the entity so as to monitor its performance But despite repeated requests by ICRA, the entity’s management has remained non-cooperative. Accordingly, ICRA had migrated the entity’s rating to the “Issuer Not Cooperating” (INC) category in April 2018. However, because of persistent non-cooperation by the entity with ICRA for a period of over six months, the ratings have now been downgraded to the non-investment grade from the investment grade. The rating action is in accordance with ICRA’s policy in respect of non-cooperation by a rated entity, available at www.icra.in. Also, the rating action is in line with the circular issued by the Securities and Exchange Board of India (SEBI) [SEBI/HO/MIRSD/CRADT/CIR/P/2020/2] on January 3, 2020 and the subsequent clarifications from SEBI, in relation to the rating action prescribed for non-cooperating investment grade ratings. -

End of the Line Jurisdiction
Living on The edge Hiranandani sees the railways Mumbai is no stranger to this kind Rachel Lopez “as important connectors to distant of arrangement. Its first suburb rose areas”, and they are. But more than a higgledy- piggledy beyond the Fort in When he was growing up bonding agent, the railway lines have Kalbadevi and Bhuleshwar in the mid- in Mumbai in the 1950s and ’60s, provided the blueprint for Mumbai’s nineteenth century, but every region that construction magnate Niranjan growth, observed architect Charles subsequently rose beyond was planned Hiranandani lived in a very different Correa in his perceptive essay Public keeping the city’s population growth kind of city. Most people agreed that Transport as DNA. “The urban structure and needs in mind. In 1866, Mumbai the city ended at Dadar and “Bandra of Bombay was not ordained by any already had east-west connectivity via the was a far-flung suburb”, he said. As city planner,” he wrote. It was “really Carnac, Masjid and Elphinstone bridges. Hiranandani grew older, Mumbai grew determined by the railway engineers” bigger. By the late 1980s, he had signed who laid down the Western and Central Thirty years later, an outbreak an agreement with the Maharashtra Railway local lines. (See Books for an of the plague would force the Bombay government, the Mumbai Metropolitan interview with Correa.) Since the end Improvement Trust to decongest the Regional Development Authority and local of the nineteenth century, Mumbai has city by doubling the number of roads, landholders to build a township in Powai, grown in the direction the train tracks led. -

Vasai ROB Thrown Open by Tribal Development Minister Savara the ROB Will Help Save Time, Fuel and Improve Environment
Vasai ROB thrown open by Tribal Development Minister Savara The ROB will help save time, fuel and improve environment Mumbai, June 25, 2016 – The Mumbai Metropolitan Region Development Authority (MMRDA), today, threw open the Rail Over Bridge that will connect eastern and western parts of Vasai at the hands of the Honourable Minister for Tribal Development and the Guardian Minister of Palghar District. The Rail Over Bridge – constructed at Rs. 48/- crore–is expected to help save time and fuel for the motorists and improve environment. “Vasai is a developing part of the metropolitan region and requires many infra facilities to be able to create job opportunities”, said Mr. Vishnuji Rama Savara, Hon. Minister for Tribal Development and Guardian Minister for Palghar District. Mr. Chintaman Vanaga, Hon. Member of Parliament appealed to the people saying, “I appeal to Vasaikars to cooperate with the government and help us provide you the commuting facilities you deserve”. “This 736-meter long and 11-meter wide ROB is an addition to the already existing ROB which is only 8-meter wide and carries water pipelines, electric cables etc. causing traffic chaos during peak hours. Now, with the new and additional arm both bridges will be able to carry one-way traffic affording much needed relief to the harried motorists”, said Mr. Hitendra Thakur, Hon. Member of the Legislative Assembly. Mr. Pravin Darade, Additional Metropolitan Commissioner, MMRDA, said “The Metropolitan Region is top on our priority list. We are aware that without the appropriate development of the Metropolitan Region, the city of Mumbai – which is the financial capital of the country – cannot be brought to its original grandeur”. -

Prospectus 2019-20
Late Shri Vishnu Waman Thakur Charitable Trust`s VIVA INSTITUTE OF PHARMACY Approved by A.I.C.T.E., PCI (New Delhi) and D.T.E. (Maharashtra State), Affiliated to University of Mumbai. DTE CODE: 3464 2019-20 At. Shirgaon, Veer Sawarkar Road, Virar (East), Taluka Vasai, District: Palghar-401305 Wbsite: www.vivapharmacy.org | Email: [email protected] Office: 7770002544 Ext; 160, Fax: 0250-2515275 PRESIDENT’S MESSAGE It has been 29 years VIVA is strong, with a vision that VIVA fosters since VIVA came into strong Values, providing an environment for being. Appreciating the Innovation, to emerge out as a Victorious, and importance of education further to aspire for the well -being of all the in nation building, we stakeholders of the society. Our consistent focus is began with the primary on development of the required competence among school in the year 1989 our students in order to be a finest resource center and Junior college in to the industry. VIVA CAMPUS provides an 1991. And, from the environment that helps them decisively to think in a academic year 2000-01 extended our vision to broader perspective. provide Degree College. Over the years, VIVA has evolved and expanded from what it was years back Shri. Hitendra Thakur so as to cater to the rising need of the time. Today, President,VIVA-Trust VIVA is providing education to over 36000 students. To put it simple, foundation of PRINCIPAL’S MESSAGE My Hearty Greetings to All!! I Institute has started NSS unit under University of welcome you to the VIVA Mumbai. -
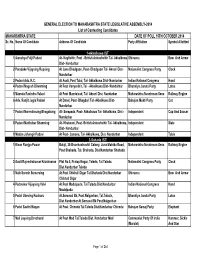
Final List of Contesting Candidates
GENERAL ELECTION TO MAHARASHTRA STATE LEGISLATIVE ASSEMBLY-2014 List of Contesting Candidates MAHARSHTRA STATE DATE OF POLL 15TH OCTOBER 2014 Sr. No. Name Of Candidate Address Of Candidate Party Affiliation Symbol Allottted 1-Akkalkuwa (ST) 1 Aamshya Fulji Padavi At- Koylivihir, Post - British Ankushvihir Tal- Akkalkuwa Shivsena Bow And Arrow Dist- Nandurbar 2 Paradake Vijaysing Rupsing At June Dhadgaon, Post- Dhadgaon Tal- Akrani Dist- Nationalist Congress Party Clock Nandurbar 3 Padavi Adv. K.C. At Asali, Post Talai, Tal- Akkalkuwa Dist- Nandurbar Indian National Congress Hand 4 Padavi Nagesh Dilwarsing At Post Vanyavihir, Tal - Akkalkuwa Dist- Nandurbar Bharatiya Janata Party Lotus 5 Mamata Ravindra Valavi At Post Mundalvad, Tal- Akrani Dist- Nandurbar Maharashtra Navnirman Sena Railway Engine 6 Adv. Ranjit Jugla Padavi At Danel, Post- Bhagdari Tal- Akkalkuwa Dist- Bahujan Mukti Party Cot Nandurbar 7 Padavi Narendrasing Bhagatsing At- Sorapada, Post- Akkalkuwa Tal- Akkalkuwa, Dist - Independent Cup And Saucer Nandurbar 8 Padavi Madhukar Shamsing At- Khatwani, Post- British Ankushvihir Tal- Akkalkuwa, Independent Slate Dist- Nandurbar 9 Madan Jahangir Padavi At Post- Jamana, Tal- Akkalkuwa, Dist- Nandurbar Independent Table 2-Sahada (ST) 1 Kisan Runjya Pawar Balaji, 35-Bramhastrushti Colony, Juna Mohida Road, Maharashtra Navnirman Sena Railway Engine Post Shahada, Tal. Shahada, Dist.Nandurbar Shahada 2 Gavit Rajendrakumar Krushnarao Plot No.5, Pratap Nagar, Taloda, Tal.Taloda Nationalist Congress Party Clock Dist.Nandurbar Taloda 3 Naik Suresh Sumersing At.Post Chikhali Digar Tal.Shahada Dist.Nandurbar Shivsena Bow And Arrow Chikhali Digar 4 Padmakar Vijaysing Valvi At.Post Modalpada, Tal.Taloda Dist.Nandurbar Indian National Congress Hand Modalpada 5 Padvi Udesing Kocharu At.Somaval Bk, Post.Nalgavhan, Tal.Taloda, Bharatiya Janata Party Lotus Dist.Nandurbar At.Somaval Bk Post.Nalgavhan 6 Padvi Savitri Magan At Post.