Free and Open Source Software (FOSS) Usage in Military Computing
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Implementing Cisco Cyber Security Operations
2019 CLUS Implementing Cisco Cyber Security Operations Paul Ostrowski / Patrick Lao / James Risler Cisco Security Content Development Engineers LTRCRT-2222 2019 CLUS Cisco Webex Teams Questions? Use Cisco Webex Teams to chat with the speaker after the session How 1 Find this session in the Cisco Live Mobile App 2 Click “Join the Discussion” 3 Install Webex Teams or go directly to the team space 4 Enter messages/questions in the team space Webex Teams will be moderated cs.co/ciscolivebot#LTRCRT-2222 by the speaker until June 16, 2019. 2019 CLUS © 2019 Cisco and/or its affiliates. All rights reserved. Cisco Public 3 Agenda • Goals and Objectives • Prerequisite Knowledge & Skills (PKS) • Introduction to Security Onion • SECOPS Labs and Topologies • Access SECFND / SECOPS eLearning Lab Training Environment • Lab Evaluation • Cisco Cybersecurity Certification and Education Offerings 2019 CLUS LTRCRT-2222 © 2019 Cisco and/or its affiliates. All rights reserved. Cisco Public 4 Goals and Objectives: • Today's organizations are challenged with rapidly detecting cybersecurity breaches in order to effectively respond to security incidents. Cybersecurity provides the critical foundation organizations require to protect themselves, enable trust, move faster, add greater value and grow. • Teams of cybersecurity analysts within Security Operations Centers (SOC) keep a vigilant eye on network security monitoring systems designed to protect their organizations by detecting and responding to cybersecurity threats. • The goal of Cisco’s CCNA Cyber OPS (SECFND / SECOPS) courses is to teach the fundamental skills required to begin a career working as an associate/entry-level cybersecurity analyst within a threat centric security operations center. • This session will provide the student with an understanding of Security Onion as an open source network security monitoring tool (NSM). -
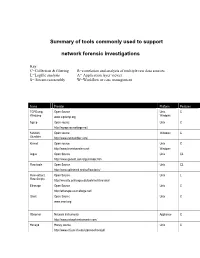
Network Forensic Tools Sidebar
Summary of tools commonly used to support network forensic investigations Key: C=Collection & filtering R=correlation and analysis of multiple raw data sources L=Logfile analysis A= Application layer viewer S= Stream reassembly W=Workflow or case management Name Provider Platform Features TCPDump, Open Source Unix, C Windump www.tcpdump.org Windows Ngrep Open source Unix C http://ngrep.sourceforge.net/ Network Open source Windows C Stumbler http://www.netstumbler.com/ Kismet Open source Unix C http://www.kismetwireless.net Windows Argus Open Source Unix CL http://www.qosient.com/argus/index.htm Flow-tools Open Source Unix CL http://www.splintered.net/sw/flow-tools/ Flow-extract, Open Source Unix L Flow Scripts http://security.uchicago.edu/tools/net-forensics/ Etherape Open Source Unix C http://etherape.sourceforge.net/ Snort Open Source Unix C www.snort.org Observer Network Instruments Appliance C http://www.networkinstruments.com/ Honeyd Honey source Unix C http://www.citi.umich.edu/u/provos/honeyd/ Ethereal Open Source Windows CLS www.Ethereal.com Unix Etherpeek Wild Packets, Inc. Windows CLS www.wildpackets.com SecureNet Intrusion Inc. Windows with CS http://www.intrusion.com collector appliance FLAG Open Source Unix L Forensic and http://www.dsd.gov.au/library/software/flag/ Log Analysis GUI ACID Analysis Console for Intrusion Databases Unix L http://www.andrew.cmu.edu/~rdanyliw/snort/snortacid.html Shadow http://www.nswc.navy.mil/ISSEC/CID/index.html Unix LS DeepNines and http://www.deepnines.com/sleuth9.html Unix CSR Sleuth9 Infinistream -

Solaris 10 End of Life
Solaris 10 end of life Continue Oracle Solaris 10 has had an amazing OS update, including ground features such as zones (Solaris containers), FSS, Services, Dynamic Tracking (against live production operating systems without impact), and logical domains. These features have been imitated in the market (imitation is the best form of flattery!) like all good things, they have to come to an end. Sun Microsystems was acquired by Oracle and eventually, the largest OS known to the industry, needs to be updated. Oracle has set a retirement date of January 2021. Oracle indicated that Solaris 10 systems would need to raise support costs. Oracle has never provided migratory tools to facilitate migration from Solaris 10 to Solaris 11, so migration to Solaris has been slow. In September 2019, Oracle decided that extended support for Solaris 10 without an additional financial penalty would be delayed until 2024! Well its March 1 is just a reminder that Oracle Solaris 10 is getting the end of life regarding support if you accept extended support from Oracle. Combined with the fact gdpR should take effect on May 25, 2018 you want to make sure that you are either upgraded to Solaris 11.3 or have taken extended support to obtain any patches for security issues. For more information on tanningix releases and support dates of old and new follow this link ×Sestive to abort the Unix Error Operating System originally developed by Sun Microsystems SolarisDeveloperSun Microsystems (acquired by Oracle Corporation in 2009)Written inC, C'OSUnixWorking StateCurrentSource ModelMixedInitial release1992; 28 years ago (1992-06)Last release11.4 / August 28, 2018; 2 years ago (2018-08-28)Marketing targetServer, PlatformsCurrent: SPARC, x86-64 Former: IA-32, PowerPCKernel typeMonolithic with dynamically downloadable modulesDefault user interface GNOME-2-LicenseVariousOfficial websitewww.oracle.com/solaris Solaris is the own operating system Of Unix, originally developed by Sunsystems. -

Support for Mobile Augmented and Synthesized Worlds
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Illinois Digital Environment for Access to Learning and Scholarship Repository Support for Mobile Augmented and Synthesized Worlds December 17, 2007 Won J. Jeon and Roy H. Campbell {wonjeon, rhc}@uiuc.edu Department of Computer Science University of Illinois at Urbana-Champaign Abstract Virtual worlds provide 3D-immersive experiences to users and some of them already have already launched commercial service to users. As computing environment becomes more heterogeneous, more mobile users are anticipated to access the virtual world with their mobile devices. However, still there are challenges and problems to be addressed for mobile users. In this report, state-of-art virtual world platforms are presented and their key features are compared. We compare possible approaches to tackle these problems to support virtual worlds for mobile devices. Transcoding scheme at the proxy is presented and evaluated for a given computing and networking environment. 1. Introduction A virtual world is a computer-simulated or synthesized environment where multiple users inhabit and interact to each other via avatars. The world mimics the real world via simulated real world physics and the persistence of the world comes from maintaining and updating the state of the world around the clock. Historically this concept is rooted from distributed interactive simulation (DIS) and massively multiplayer online role- playing game (MMORPG). DIS is used mainly by military organizations whereas MMORPG has gained huge popularity among general users or gamers. The world is typically represented as 2D or 3D graphics to multiple users. -

Titans and Trolls of the Open Source Arena
Titans and Trolls Enter the Open-Source Arena * by DEBRA BRUBAKER BURNS I. Introduction .................................................................................... 34 II. Legal Theories for Open Source Software License Enforcement ................................................................................... 38 A. OSS Licensing .......................................................................... 38 B. Legal Theories and Remedies for OSS Claims .................... 40 1. Legal Protections for OSS under Copyright and Contract Law ..................................................................... 40 Stronger Protections for OSS License under Copyright Law ................................................................... 40 2. Copyright-Ownership Challenges in OSS ....................... 42 3. Potential Legal Minefields for OSS under Patent Law ...................................................................................... 45 4. Added Legal Protection for OSS under Trademark Law ...................................................................................... 46 5. ITC 337 Action as Uncommon Legal Protection for OSS ..................................................................................... 49 III. Enforcement Within the OSS Community .................................. 49 A. Software Freedom Law Center Enforces OSS Licenses .... 50 B. Federal Circuit Finds OSS License Enforceable Under Copyright Law ......................................................................... 53 C. Commercial OSS -

Guide to Computer Forensics and Investigations Fourth Edition
Guide to Computer Forensics and Investigations Fourth Edition Chapter 11 Virtual Machines, Network Forensics, and Live Acquisitions Objectives • Describe primary concerns in conducting forensic examinations of virtual machines • Describe the importance of network forensics • Explain standard procedures for performing a live acquisition • Explain standard procedures for network forensics • Describe the use of network tools Guide to Computer Forensics and Investigations 2 Virtual Machines Overview • Virtual machines are important in today’s networks. • Investigators must know how to detect a virtual machine installed on a host, acquire an image of a virtual machine, and use virtual machines to examine malware. Virtual Machines Overview (cont.) • Check whether virtual machines are loaded on a host computer. • Check Registry for clues that virtual machines have been installed or uninstalled. Network Forensics Overview • Network forensics – Systematic tracking of incoming and outgoing traffic • To ascertain how an attack was carried out or how an event occurred on a network • Intruders leave trail behind • Determine the cause of the abnormal traffic – Internal bug – Attackers Guide to Computer Forensics and Investigations 5 Securing a Network • Layered network defense strategy – Sets up layers of protection to hide the most valuable data at the innermost part of the network • Defense in depth (DiD) – Similar approach developed by the NSA – Modes of protection • People • Technology • Operations Guide to Computer Forensics and Investigations -

Changing Java Applications
Menu Topics Archives Downloads Subscribe The code underpinning the Brazilian CODING healthcare system—and other world- changing Java applications The code underpinning the Brazilian Thanks for the memories healthcare system—and other world- Developer software for the win changing Java applications Banking on financial software Games and visualization Your reactions to the list of the 25 greatest Efficient communication Java apps ever written Science and AI applications by Alexa Morales August 28, 2020 It was with a smidge of trepidation that I offered my list of the 25 greatest Java applications, frameworks, platforms, and libraries ever written. After all, developers are a demanding audience. But the article received hundreds of comments on Reddit, Slashdot, Hacker News, and Twitter, and it inspired many letters to the editor. The piece even received happy social media posts from those who made the list, including the US National Security Agency and a.i. solutions. The US National Security Agency was secretly pleased we noticed its Ghidra binary decompilation tool. The team from a.i. solutions was happy its DSTE trajectory design tool made the list. The tenor of conversation was both positive and polite. That speaks volumes about the excellent character of Java developers, don’t you think? But, developers being who they are, opinions on what should have made the list abounded. The good news is, Java has transformed the world. The bad news is, my list didn’t represent enough of the world beyond the United States. For example, there’s the Java code written to manage the Brazilian Healthcare Information System and the Brazilian tax system (Duke’s Choice Award winner in 2005). -

Linux Networking Cookbook.Pdf
Linux Networking Cookbook ™ Carla Schroder Beijing • Cambridge • Farnham • Köln • Paris • Sebastopol • Taipei • Tokyo Linux Networking Cookbook™ by Carla Schroder Copyright © 2008 O’Reilly Media, Inc. All rights reserved. Printed in the United States of America. Published by O’Reilly Media, Inc., 1005 Gravenstein Highway North, Sebastopol, CA 95472. O’Reilly books may be purchased for educational, business, or sales promotional use. Online editions are also available for most titles (safari.oreilly.com). For more information, contact our corporate/institutional sales department: (800) 998-9938 or [email protected]. Editor: Mike Loukides Indexer: John Bickelhaupt Production Editor: Sumita Mukherji Cover Designer: Karen Montgomery Copyeditor: Derek Di Matteo Interior Designer: David Futato Proofreader: Sumita Mukherji Illustrator: Jessamyn Read Printing History: November 2007: First Edition. Nutshell Handbook, the Nutshell Handbook logo, and the O’Reilly logo are registered trademarks of O’Reilly Media, Inc. The Cookbook series designations, Linux Networking Cookbook, the image of a female blacksmith, and related trade dress are trademarks of O’Reilly Media, Inc. Java™ is a trademark of Sun Microsystems, Inc. .NET is a registered trademark of Microsoft Corporation. Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in this book, and O’Reilly Media, Inc. was aware of a trademark claim, the designations have been printed in caps or initial caps. While every precaution has been taken in the preparation of this book, the publisher and author assume no responsibility for errors or omissions, or for damages resulting from the use of the information contained herein. -

Safeguarding the Future of Linux Through Standards
Safeguarding the Future of Linux Through Standards “ Through the defi nition and testing of operating system interfaces, the LSB creates a stable platform that benefi ts Safeguarding Key Facts the Future of bo th developers and users.” - Linus Torvalds Linux Through Standards • The FSG is a non-profi t organization devoted to the ongoing success of Linux The Free Standards Group is an independent nonprofi t organization dedicated to accelerating the use and acceptance of free and open source • Growing membership includes all leading Linux vendors software by developing and promoting standards. Supported by leaders and many infl uential non-profi ts in the IT industry as well as the open source development community, the in the Linux community Free Standards Group fulfi lls a critical need to have common behavioral • Workgroups cover key specifi cations, tools and ABIs across Linux platforms. The Linux Standard Base Linux standards issues such as a binary standard and offers an answer to the most pressing issue facing Linux today: fragmentation. internationalization • Board members include an A well supported standard for Linux is the neccesary component to Linux’s assortment of Linux experts continued success. Without a commonly adopted standard, Linux will fragment, and senior representatives of the Linux community thus proving costly for ISVs to port their applications to the operating system and making it diffi cult for end users and Linux vendors alike. By adopting the • Headquartered in San Francisco Linux Standard Base, the Linux community provides this crucial portability so that applications can be used on more than one distribution of Linux with little or no change. -

Wireshark & Ethereal Network Protocol Analyzer
377_Eth2e_FM.qxd 11/14/06 1:23 PM Page i Visit us at www.syngress.com Syngress is committed to publishing high-quality books for IT Professionals and delivering those books in media and formats that fit the demands of our cus- tomers. We are also committed to extending the utility of the book you purchase via additional materials available from our Web site. SOLUTIONS WEB SITE To register your book, visit www.syngress.com/solutions. Once registered, you can access our [email protected] Web pages. There you may find an assortment of value-added features such as free e-books related to the topic of this book, URLs of related Web sites, FAQs from the book, corrections, and any updates from the author(s). ULTIMATE CDs Our Ultimate CD product line offers our readers budget-conscious compilations of some of our best-selling backlist titles in Adobe PDF form. These CDs are the perfect way to extend your reference library on key topics pertaining to your area of exper- tise, including Cisco Engineering, Microsoft Windows System Administration, CyberCrime Investigation, Open Source Security, and Firewall Configuration, to name a few. DOWNLOADABLE E-BOOKS For readers who can’t wait for hard copy, we offer most of our titles in download- able Adobe PDF form. These e-books are often available weeks before hard copies, and are priced affordably. SYNGRESS OUTLET Our outlet store at syngress.com features overstocked, out-of-print, or slightly hurt books at significant savings. SITE LICENSING Syngress has a well-established program for site licensing our e-books onto servers in corporations, educational institutions, and large organizations. -

Carrier Grade Linux Requirements Definition
Carrier Grade Linux Requirements Definition The Linux Foundation Version 5.0 1796 18th Street S u i t e C Prepared by the Carrier Grade Linux Working Group San Francisco CA 94107, USA Copyright (c) 2005, 2006, 2007, 2011 by The Linux +1 (415) 723 - 9 7 0 9 Foundation. This material may be distributed only subject to the terms and conditions set forth in the Open Publication License, v1.0 or later (the latest version is available at http://www.opencontent.org/opl.shtml/). Distribution of substantively modified versions of this document is prohibited without the explicit permission of the copyright holder. Linux is a Registered Trademark of Linus Torvalds. Other company, product, or service names may be the trademarks of others. CONTRIBUTORS TO THE CGL 5.0 REQUIREMENTS DEFINITION INCLUDE (IN ALPHABETICAL ORDER): Last Name First Name Company Anderson Matt HP Anderson Tim MontaVista Software Awad Majid Intel Aziz Khalid HP Badovinatz Peter IBM Bozarth Brad Cisco Cauchy Dan MontaVista Software Chacron Eric Alcatel Chen Terence Intel Cherry John OSDL Christopher Johnson Sun Microsystems Cihula Jospeh Intel Cress Andrew Intel Dague Sean IBM Dake Steven MontaVista Software Flaxa Ralf Novell Fleischer Julie Intel Fleischer Julie OSDL Fox Kevin Sun Microsystems Gross Mark Intel Haddad Ibrahim Ericsson Heber Troy HP Howell David P. Intel Hu Michael Radisys Ikebe Takashi NTT Ishitsuka Seiichi NEC Jagana Venkata IBM Johnson Christopher P. Sun Microsystems Kevin Fox Sun Microsystems Kimura Masato NTT Comware Krauska Joel Cisco Kukkonen Mika Nokia La Monte.H.P Yarrol Timesys Lavonius Ville Nokia Liu Bing Wei Intel Lynch Rusty Intel * MacDonald Joe Wind River Systems Manas Saksena Timesys Nakayama Mitsuo NEC Peter-Gonzalez Inaky Intel Pourzandi Makan Ericsson Rossi Frederic Eicsson Saksena Manas Timesys Sakuma Junichi OSDL Saskena Manas Timesys Seiler Glenn Wind River Systems Smarduch Mario Motorola Takamiya Noriaki NTT Software Weijers Gé Witham Timothy D. -

Wireless Networking in the Developing World
Wireless Networking in the Developing World Second Edition A practical guide to planning and building low-cost telecommunications infrastructure Wireless Networking in the Developing World For more information about this project, visit us online at http://wndw.net/ First edition, January 2006 Second edition, December 2007 Many designations used by manufacturers and vendors to distinguish their products are claimed as trademarks. Where those designations appear in this book, and the authors were aware of a trademark claim, the designations have been printed in all caps or initial caps. All other trademarks are property of their respective owners. The authors and publisher have taken due care in preparation of this book, but make no expressed or implied warranty of any kind and assume no responsibility for errors or omissions. No liability is assumed for incidental or consequential damages in connection with or arising out of the use of the information contained herein. © 2007 Hacker Friendly LLC, http://hackerfriendly.com/ This work is released under the Creative Commons Attribution-ShareAlike 3.0 license. For more details regarding your rights to use and redistribute this work, see http://creativecommons.org/licenses/by-sa/3.0/ Contents Where to Begin 1 Purpose of this book........................................................................................................................... 2 Fitting wireless into your existing network.......................................................................................... 3 Wireless