Avaya Aura® Solution for Midsize Enterprise Release Notes
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Livecycle ES 2
LiveCycle ES2 Readme The contents of this file are subject to the Mozilla Public License Version 1.1 (the "License"); you may not use this file except in compliance with the License. You may obtain a copy of the License at http://www.mozilla.org/MPL/ Software distributed under the License is distributed on an "AS IS" basis, WITHOUT WARRANTY OF ANY KIND, either express or implied. See the License for the specific language governing rights and limitations under the License. Portions licensed under the Mozilla Public License Version 1.1, available at www.mozilla.org. Recipients can obtain a copy of the Adobe modifications in source form. The contents of this file are subject to the Netscape Public License Version 1.1 (the "License"); you may not use this file except in compliance with the License. You may obtain a copy of the License at http://www.mozilla.org/NPL/ Software distributed under the License is distributed on an "AS IS" basis, WITHOUT WARRANTY OF ANY KIND, either express or implied. See the License for the specific language governing rights and limitations under the License. The Original Code is Mozilla Communicator client code, released March 31, 1998. The Initial Developer of the Original Code is Netscape Communications Corporation. Portions created by Netscape are Copyright (C) 1998-1999 Netscape Communications Corporation. All Rights Reserved. This product contains either BSAFE and/or TIPEM software by RSA Security Inc. Copyright (C) 1995-1997 Eric Young ([email protected]) All rights reserved. This package is an SSL implementation written by Eric Young ([email protected]). -
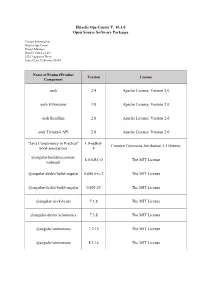
Open Source Software Packages
Hitachi Ops Center V. 10.3.0 Open Source Software Packages Contact Information: Hitachi Ops Center Project Manager Hitachi Vantara LLC 2535 Augustine Drive Santa Clara, California 95054 Name of Product/Product Version License Component aesh 2.4 Apache License, Version 2.0 aesh Extensions 1.8 Apache License, Version 2.0 aesh Readline 2.0 Apache License, Version 2.0 aesh Terminal API 2.0 Apache License, Version 2.0 "Java Concurrency in Practice" 1.0-redhat- Creative Commons Attribution 2.5 Generic book annotations 4 @angular-builders/custom- 8.0.0-RC.0 The MIT License webpack @angular-devkit/build-angular 0.800.0-rc.2 The MIT License @angular-devkit/build-angular 0.803.25 The MIT License @angular-devkit/core 7.3.8 The MIT License @angular-devkit/schematics 7.3.8 The MIT License @angular/animations 7.2.15 The MIT License @angular/animations 8.2.14 The MIT License Name of Product/Product Version License Component @angular/cdk 7.3.7 The MIT License @angular/cli 8.0.0 The MIT License @angular/cli 8.3.25 The MIT License @angular/common 7.2.15 The MIT License @angular/common 8.2.14 The MIT License @angular/compiler 7.2.15 The MIT License @angular/compiler 8.2.14 The MIT License @angular/compiler-cli 8.2.14 The MIT License @angular/core 7.2.15 The MIT License @angular/forms 7.2.13 The MIT License @angular/forms 7.2.15 The MIT License @angular/forms 8.2.14 The MIT License @angular/forms 8.2.7 The MIT License @angular/language-service 8.2.14 The MIT License @angular/platform-browser 7.2.15 The MIT License Name of Product/Product Version License -
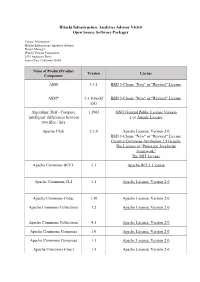
Hitachi Infrastructure Analytics Advisor V4.0.0 Open Source Software Packages
Hitachi Infrastructure Analytics Advisor V4.0.0 Open Source Software Packages Contact Information: Hitachi Infrastructure Analytics Advisor Project Manager Hitachi Vantara Corporation 2535 Augustine Drive Santa Clara, California 95054 Name of Product/Product Version License Component ASM 3.3.1 BSD 3-Clause "New" or "Revised" License ASM* 3.3.1(modif BSD 3-Clause "New" or "Revised" License ied) Algorithm::Diff - Compute 1.1903 GNU General Public License Version `intelligent' differences between 1 or Artistic License two files / lists Apache Click 2.3.0 Apache License, Version 2.0 BSD 3-Clause "New" or "Revised" License Creative Commons Attribution 2.5 Generic The License of "Prototype JavaScript framework" The MIT License Apache Commons BCEL 5.1 Apache BCEL License Apache Commons CLI 1.1 Apache License, Version 2.0 Apache Commons Codec 1.10 Apache License, Version 2.0 Apache Commons Collections 3.2 Apache License, Version 2.0 Apache Commons Collections 4.1 Apache License, Version 2.0 Apache Commons Compress 1.0 Apache License, Version 2.0 Apache Commons Compress 1.1 Apache License, Version 2.0 Apache Commons Email 1.4 Apache License, Version 2.0 Name of Product/Product Version License Component Apache HTTP Server 2.4.28 Apache License, Version 2.0 GNU General Public License, Version 3 with Autoconf exception The License by "Bell Communications Research, Inc. (Bellcore)" The License by "Carnegie Mellon University" The License by "Ian F. Darwin" The License by "Massachusetts Institute of Technology" The License by "RSA Data Security, Inc." The License of "RSA Data Security, Inc. MD4 Message-Digest Algorithm" The License of "RSA Data Security, Inc. -

Lifesize Clearsea Third Party Licenses
LifeSize® ClearSeaTM Third Party Licenses This is the product of LifeSize Communications, Inc. a division of Logitech © 2010 - 2012. All rights reserved. LifeSize, the LifeSize logo and other LifeSize marks are owned by Logitech and may be registered. All other trademarks are the property of their respective owners. LifeSize ClearSea systems are shipped with certain software that is licensed to LifeSize Communications from other parties. Following is a list of some of that software. Portions of this product are covered by patents owned and licensed by Polycom®, Inc. "Siren" is a trademark of Polycom, Inc. This product is licensed under the AVC patent portfolio license for the personal and non- commercial use of a consumer to (I) encode video in compliance with the AVC Standard ("AVC Video") and/or (ii) decode AVC video that was encoded by a consumer engaged in a personal and non-commercial activity and/or was obtained from a video provider licensed to provide AVC video. No license is granted or shall be implied for any other use. Additional information may be obtained from MPEG, L.L.C. See http://www.MPEGLA.com. April 2012 1 Additional Software In addition to the software listed above, the following is a list of certain additional software programs that are shipped with this product, where you may access such software, and the licenses accompanying such software. Component URL License License URL 7zip http://www.7-zip.org/ GNU Lesser General http://www.opensource.org/licenses/lgpl- Public License (LGPL) license.php Apache HTTP http://www.apache.org/ -

“Infectious” Open Source Software: Spreading Incentives Or Promoting Resistance?
“INFECTIOUS” OPEN SOURCE SOFTWARE: SPREADING INCENTIVES OR PROMOTING RESISTANCE? Greg R. Vetter* ABSTRACT Some free or open source software infects other software with its licensing terms. Popularly, this is called a viral license, but the software is not a computer virus. Free or open source software is a copyright-based licensing system. It typically allows modification and distribution on conditions such as source code availability, royalty free use and other requirements. Some licenses require distribution of modifications under the same terms. A license is infectious when it has a strong scope for the modifications provision. The scope arises from a broad conception of software derivative works. A strong infectious ambit would apply itself to modified software, and to software intermixed or coupled with non-open-source software. Popular open source software, including the * Assistant Professor of Law, University of Houston Law Center (UHLC); Co-Director, Institute for Intellectual Property and Information Law (IPIL) at UHLC; biography and additional background available at: www.law.uh.edu/faculty/gvetter. Relevant to this Article is that my background includes a Master’s degree in Computer Science and full-time work experience in the business-to-business software industry from 1987 to 1996. Research for this Article was supported by summer research grants from the University of Houston Law Foundation and a grant from the University of Houston’s New Faculty Research Program. I also thank UHLC’s IPIL Institute and its sponsors for support of my endeavors at UHLC. My thanks to UHLC students Jason Williams, Cuong Lam Nguyen, Stacey R. Vause and Nivine Zakhari for research assistance. -

Storage Foundation 4.1 for Oracle RAC Release Notes
VERITAS Storage Foundation 4.1 for Oracle RAC Release Notes Linux August 2005 Disclaimer The information contained in this publication is subject to change without notice. VERITAS Software Corporation makes no warranty of any kind with regard to this manual, including, but not limited to, the implied warranties of merchantability and fitness for a particular purpose. VERITAS Software Corporation shall not be liable for errors contained herein or for incidental or consequential damages in connection with the furnishing, performance, or use of this manual. VERITAS Legal Notice Copyright © 2002-2005 VERITAS Software Corporation. All rights reserved. VERITAS and the VERITAS Logo are trademarks or registered trademarks of VERITAS Software Corporation or its affiliates in the U.S. and other countries. Other names may be trademarks of their respective owners. VERITAS Software Corporation 350 Ellis Street Mountain View, CA 94043 USA Phone 650–527–8000 Fax 650–527–2901 www.veritas.com Third-Party Legal Notices Certain third-party software may be distributed, embedded, or bundled with this VERITAS product, or recommended for use in conjunction with VERITAS product installation and operation. Such third-party software is separately licensed by its copyright holder. See the Third-Party Legal Notice appendix in the Release Notes for the licenses that govern the use of the third-party software and for proprietary notices of the copyright holders. ii Storage Foundation for Oracle RAC VERITAS Storage Foundation 4.1 for Oracle RAC Release Notes This document provides important information regarding Storage Foundation for Oracle RAC (SFRAC) version 4.1 for Red Hat Enterprise Linux 4.0 (on x86 architecture) and SUSE Linux Enterprise Server 9 (on x86_64 and IA 64 architectures). -

USC8050 Enterprise Small Cell Management System R4 1 Open Source
Open Source Used In USC8050 Enterprise Small Cell Management System R4.1 Cisco Systems, Inc. www.cisco.com Cisco has more than 200 offices worldwide. Addresses, phone numbers, and fax numbers are listed on the Cisco website at www.cisco.com/go/offices. Open Source Used In USC8050 Enterprise Small Cell Management System R4.1 1 Text Part Number: 78EE117C99-87528265 Open Source Used In USC8050 Enterprise Small Cell Management System R4.1 2 This document contains licenses and notices for open source software used in this product. With respect to the free/open source software listed in this document, if you have any questions or wish to receive a copy of any source code to which you may be entitled under the applicable free/open source license(s) (such as the GNU Lesser/General Public License), please contact us at [email protected]. In your requests please include the following reference number 78EE117C99-87528265 Contents 1.1 bsh 2.0b4 1.1.1 Available under license 1.2 commons-codec 1.3 1.2.1 Available under license 1.3 Commons-logging 1.1.1 1.3.1 Available under license 1.4 freemarker-webapp 2.3.20 1.4.1 Available under license 1.5 jackson-annotations 2.2.0 1.5.1 Available under license 1.6 jdom 2.0.4 1.6.1 Notifications 1.6.2 Available under license 1.7 jetty 9.0.7 1.7.1 Available under license 1.8 jfreechart 1.0.13 1.8.1 Available under license 1.9 log4j 1.2.14 1.9.1 Available under license 1.10 slf4j-jdk14 1.7.5 1.10.1 Available under license 1.11 SNMP4J 1.8.1 1.11.1 Available under license 1.12 spring-core 3.2.1.RELEASE 1.12.1 Available under license 1.13 sshd 0.7.0 Open Source Used In USC8050 Enterprise Small Cell Management System R4.1 3 1.13.1 Available under license 1.14 swagger 1.2.5 1.14.1 Available under license 1.15 syslog4j 0.9.42 1.15.1 Available under license 1.1 bsh 2.0b4 1.1.1 Available under license : /***************************************************************************** * * * This file is part of the BeanShell Java Scripting distribution. -

README for Siemens Micropad Controller Version 6.1.9
Infrastructure and Cities Building Technologies Division Other Component Agreement README for Siemens Micropad Controller version 6.1.9 Embedded in, or bundled with, this product are open source software (OSS) components and other third party components identified below. You may receive a copy of,distribute and/or modify any open source code for the OSS component under the terms of their respective licenses,which may be GNU General Public License, the GNU Lesser General Public License, the modified BSD license and the MIT license. In the event of conflicts between Siemens license conditions and the Open Source Software license conditions, the Open Source Software conditions shall prevail with respect to the Open Source Software portions of the software. You are permitted to modify proprietary components originating from Siemens and to engage in reverse engineering for purposes of debugging such modifications, to the extent such components are linked to libraries licensed under the GNU Lesser General Public License. You are not permitted to distribute information resulting from such reverse engineering or to distribute the modified proprietary components. Your rights to modify proprietary components originating from parties other than Siemens are governed by the respective third party´s license conditions. On written request within three years from the date of product purchase and against payment of our expenses, Siemens will supply source code for any OSS component identified below in linewith the terms of the applicable license. For this, please contact us at: Siemens Schweiz AG Building Technologies Group Intellectual Property Gubelstraße 22 CH 6300 Zug Switzerland Generally, the identified OSS components are distributed in the hope that they will be useful, but WITHOUT ANY WARRANTY, without even implied warranty such as for MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE, and without liability for any Siemens entity other than as explicitely documented in your purchase contract. -

Unifier Third-Party Notices and Disclosures Release 9.14
Unifier Third-Party Notices and Disclosures Release 9.14 December 2013 Contents Notices and Disclosures ...................................................................................................... 7 Annogen ............................................................................................................................ 7 Ant ..................................................................................................................................... 7 Antelope ............................................................................................................................ 7 ANTLR 3 ............................................................................................................................ 7 Apache Software License, Version 1.1 .............................................................................. 8 Apache Software License, Version 2.0 .............................................................................. 9 ASM ................................................................................................................................. 12 Axiom .............................................................................................................................. 12 Axis .................................................................................................................................. 12 Base64 encoding ............................................................................................................. 12 Bean Scripting Framework .............................................................................................. -
BUFR Software License
A free software license for the BUFR software H. Paulitsch / TU-Graz At the first OPERA-III meeting the need for a license for the BUFR software has been discussed in WG2 and TU-Graz has been asked to prepare such a license. There are a lot of different free software licenses available (see the list), with the GNU General Public License (GPL) the best known. There is one condition of the GPL, which makes it inappropriate for use with the BUFR software: it requires, that every derived or combined work also has to be released under GPL. This would mean, that commercial (radar) software could not use a BUFR library, if it were released under GPL. The Lesser GPL (LGPL) does not have this requirement, so this seems to be the better choice (reference: LGPL Terms and Conditions, §2 and §5). The way to apply the LGPL is by including a short notice in each source file and provide the full LGPL license text as a separate file in the software distribution. TU-Graz has prepared such a notice based on the LGPL recommendations. For reference also included in this document is the full license text of both the LGPL and the GPL. Notice to be included in the source files BUFR encoding and decoding software/library Copyright (c) 2007, Institute of Broadband Communication, TU-Graz on behalf of EUMETNET OPERA, http://www.knmi.nl/opera This library is free software; you can redistribute it and/or modify it under the terms of the GNU Lesser General Public License as published by the Free Software Foundation; version 2.1 of the License. -

By Frank Cohen © 2002 Sun Microsystems, Inc. All Rights Reserved
Building an Application Using NetBeansTM Framework By Frank Cohen © 2002 Sun Microsystems, Inc. All rights reserved. Abstract The NetBeansTM platform is more than the basis for the SunTM ONE Studio (previously ForteTM for JavaTM) integrated development environment ("IDE"). With this powerful toolset, any software developer may build powerful desktop application software, including commercial applications that have nothing to do with Java technology development. In this article, Frank Cohen describes how to create your own NetBeans modules and how to create your own branded application using the NetBeans platform. Introduction to NetBeans Who could have imagined the tremendous effect on software development made by combining Java software development technology with open-source development methodologies? From the start, Java technology's theme has been to maximize the utility of writing software once and running everywhere Java technology runs. NetBeans technology's theme has been to focus a software developer's attention on writing the core logic in desktop application software and to let the NetBeans platform worry about the mundane issues of file editing, pluggable and downloadable tools, file management, and desktop integration. The combination of Java technology and open-source methodologies gives little reason to write a desktop application today without building it on the NetBeans platform. The NetBeans platform is a software framework for building desktop application software in the Java programming language. Sun Microsystems was the first company to build a commercial application based on the NetBeans platform, but many others have followed. For example, Project XEMO is a music composition environment built on NetBeans1. Companies building application software with NetBeans take advantage of the MozillaTM-style open-source license. -

ETSI-OSS Standards
European Telecommunications Standards Institute Open Source impacts on ICT standardization Final Report – Analysis Part - VA6 December 12, 2005 Hervé Rannou Jean-Baptiste Soufron ITEMS International 46 ave Pierre Brossolette 92240 MALAKOFF Tel: +33 (0)1 4985 0326 Fax: +33 (0)1 4985 1407 [email protected] www.items.fr - ETSI - SOMMAIRE 1 Introduction ........................................................................................... 5 2 Open Source Software............................................................................ 6 2.1 Definitions ..................................................................................................... 6 2.2 SUN, MICROSOFT, BSD, GPL and others .......................................................... 10 2.3 Open Source Business Models ........................................................................ 12 2.4 Typology of Open Source Licenses .................................................................. 13 2.5 Typology of SDO IPR..................................................................................... 13 2 3 Copyright Open Source and IPR ........................................................... 15 3.1 Open Source is Copyright IPR......................................................................... 15 3.2 Open Source IPR or Patents IPR...................................................................... 16 3.3 Open Source IPR and Patents IPR ................................................................... 17 4 Open Standards...................................................................................