Kerberos with ADFS 2.0 for End User SAML SSO for Jabber Configuration Example
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

System Requirements
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files, release notes, and the latest version of the applicable user documentation, which are available from the Trend Micro website at: http://docs.trendmicro.com/en-us/enterprise/officescan.aspx Trend Micro, the Trend Micro t-ball logo, and OfficeScan are trademarks or registered trademarks of Trend Micro Incorporated. All other product or company names may be trademarks or registered trademarks of their owners. Copyright © 2017 Trend Micro Incorporated. All rights reserved. Release Date: October 2017 Protected by U.S. Patent No. 5,623,600; 5,889,943; 5,951,698; 6,119,165 Table of Contents Chapter 1: OfficeScan Server Installations Fresh Installations on Windows Server 2008 R2 Platforms .............................................................................................................................................................................. 1-2 Fresh Installations on Windows Server 2012 Platforms ..................................................................................................................................................................................... 1-3 Fresh Installations on Windows Server 2016 Platforms ..................................................................................................................................................................................... 1-4 Fresh Installations -

Migrating Active Directory to Windows Server 2012 R2
Windows Server 2012 R2 Migrating Active Directory to Windows Server 2012 R2 Hands-on lab In this lab, you will complete a migration of a Windows Server 2008 R2 domain environment to Windows Server 2012 R2 with no downtime to clients. All roles currently held including FSMO, DHCP and DNS will be transferred to enable the Windows Server 2008 R2 domain controller to be retired. Produced by HynesITe, Inc. Version 1.0 12/15/2013 This document supports a preliminary release of a software product that may be changed substantially prior to final commercial release. This document is provided for informational purposes only and Microsoft makes no warranties, either express or implied, in this document. Information in this document, including URL and other Internet Web site references, is subject to change without notice. The entire risk of the use or the results from the use of this document remains with the user. Unless otherwise noted, the companies, organizations, products, domain names, e-mail addresses, logos, people, places, and events depicted in examples herein are fictitious. No association with any real company, organization, product, domain name, e-mail address, logo, person, place, or event is intended or should be inferred. Complying with all applicable copyright laws is the responsibility of the user. Without limiting the rights under copyright, no part of this document may be reproduced, stored in or introduced into a retrieval system, or transmitted in any form or by any means (electronic, mechanical, photocopying, recording, or otherwise), or for any purpose, without the express written permission of Microsoft Corporation. -
![Chapter 15-70-411FINAL[1]](https://docslib.b-cdn.net/cover/6294/chapter-15-70-411final-1-646294.webp)
Chapter 15-70-411FINAL[1]
Lesson 15: Configuring Service Authentication MOAC 70-411: Administering Windows Server 2012 Overview • Exam Objective 5.1: Configure Service Authentication • Configuring Service Authentication • Managing Service Accounts © 2013 John Wiley & Sons, Inc. 2 Configuring Service Authentication Lesson 15: Configuring Service Authentication © 2013 John Wiley & Sons, Inc. 3 Authentication • Authentication is the act of confirming the identity of a user or system and is an essential part used in authorization when the user or system tries to access a server or network resource. • Two types of authentication that Windows supports are NT LAN Manager (NTLM) and Kerberos. • Kerberos is the default authentication protocol for domain computers. • NTLM is the default authentication protocol for Windows NT, standalone computers that are not part of a domain, and situations in which you authenticate to a server using an IP address. © 2013 John Wiley & Sons, Inc. 4 Understanding NTLM Authentication • NT LAN Manager (NTLM) is a suite of Microsoft security protocols that provides authentication, integrity, and confidentiality to users. • NTLM is an integrated single sign-on mechanism. • NTLM uses a challenge-response mechanism for authentication in which clients are able to prove their identities without sending a password to the server. © 2013 John Wiley & Sons, Inc. 5 Managing Kerberos Kerberos: • Is a computer network authentication protocol, which allows hosts to prove their identity over a non-secure network in a secure manner. • Can provide mutual authentication -

Starburn CD/DVD/Blu-Ray/HD-DVD Toolkit: Getting Started
StarBurn Software Technical Reference Series StarBurn CD/DVD/Blu-Ray/HD-DVD Toolkit: Getting Started April 18, 2016 StarBurn Software www.starburnsoftware.com Copyright © Rocket Division Software 2001-2016. All rights reserved. Copyright © StarBurn Software 2009-2016. All rights reserved. StarBurn CD/DVD/Blu-Ray/HD-DVD Toolkit: Getting Started Page 1 of 13 StarBurn Software Technical Reference Series INTRODUCTION .................................................................................................. 4 KEY BENEFITS ..................................................................................................... 5 KEY FEATURES .................................................................................................... 7 SUPPORTED PLATFORMS .................................................................................. 11 SYSTEM REQUIREMENTS................................................................................... 12 CONTACTS........................................................................................................ 13 StarBurn CD/DVD/Blu-Ray/HD-DVD Toolkit: Getting Started Page 2 of 13 StarBurn Software Technical Reference Series COPYRIGHT Copyright © Rocket Division Software 2001-2016. All rights reserved. Copyright © StarBurn Software 2009-2016. All rights reserved. All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, electronic, mechanical, photocopying, recording or otherwise, without the prior written -

Windows Server Update Services 3.0 SP2 Release Notes
Windows Server Update Services 3.0 SP2 Release Notes These release notes describe the Windows Server Update Services 3.0 Service Pack 2 (WSUS 3.0 SP2) release. This document contains the following sections: 1. What‟s New in This Release 2. System Requirements for the WSUS 3.0 SP2 Server Installation 3. Configuration Prerequisites and Best Practice Recommendations for the WSUS Server 4. Windows Small Business Server Prerequisites 5. System Requirements for the WSUS 3.0 SP2 Remote Console Installation 6. System Requirements for Client Installation 7. Upgrade Requirements and Recommendations 8. Installing WSUS 3.0 SP2 9. Setup Command-line Parameters for Unattended WSUS 3.0 SP2 Installations 10. Known Issues What’s New In This Release Integration with Windows Server 2008 R2. Support for the BranchCache feature in Windows Server 2008 R2. Support for Windows 7 clients. Windows Update Agent (WUA) client improvements. The new WUA client offers a collection of performance enhancements, user experience improvements, plus an array of bug fixes based on customer feedback. Client scan time is faster than previous versions. Computers managed by WSUS servers can now run „scoped‟ scans against those same WSUS servers, instead of performing a full scan. This will result in order-of-magnitude faster scans for applications using Microsoft Update APIs such as Windows Defender. Windows Update Agent (WUA) user experience improvements help users better organize updates and provide greater clarity on update value and behavior. Imaged machines will be more clearly displayed in the WSUS console. For more information, see article titled A Windows 2000-based, Windows Server 2003-based, or Windows XP-based computer that was set up by using a Windows 2000, Windows Server 2003, or Windows XP image does not appear in the WSUS console. -

Installation and Upgrade on Windows Server 2008/2012 When the Secondary Server Is Physical Vmware Vcenter Server Heartbeat 6.6
Installation and Upgrade on Windows Server 2008/2012 When the Secondary Server is Physical VMware vCenter Server Heartbeat 6.6 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of this document, see http://www.vmware.com/support/pubs. EN-001234-00 Installation and Upgrade on Windows Server 2008/2012 When the Secondary Server is Physical You can find the most up-to-date technical documentation on the VMware Web site at: http://www.vmware.com/support/ The VMware Web site also provides the latest product updates. If you have comments about this documentation, submit your feedback to: [email protected] Copyright © 2013 VMware, Inc. All rights reserved. This product is protected by U.S. and international copyright and intellectual property laws. VMware products are covered by one or more patents listed at http://www.vmware.com/go/patents. VMware is a registered trademark or trademark of VMware, Inc. in the United States and/or other jurisdictions. All other marks and names mentioned herein may be trademarks of their respective companies. VMware, Inc. 3401 Hillview Ave. Palo Alto, CA 94304 www.vmware.com 2 VMware, Inc. Contents About This Book 5 1 Introduction 9 vCenter Server Heartbeat Concepts 9 vCenter Server Heartbeat Protection 11 vCenter Server Heartbeat Communications 14 vCenter Server Heartbeat Failover Processes 16 2 Implementation 21 vCenter Server Heartbeat Implementation 21 Environmental Prerequisites -

Microsoft Update Testing
Microsoft Update Testing Microsoft provides the Windows Update Service that distributes bug fixes in the form of patches. Normally, Microsoft release patches via Windows Update every second Tuesday of each month and this has unofficially become known as 'Patch Tuesday'. To assure end users they can install Microsoft patches without adversely affecting existing installations of ClearSCADA, a set of regression tests are run on selected operating systems with released versions of ClearSCADA. Date: 11-06-2015 Operating Systems • Windows 7 SP1 (x64) • Windows Server 2008 R2 (x64) • Windows Server 2012 R2 • Windows 8.1 ClearSCADA 2010 R3.2 (72.5373), ClearSCADA 2013 R1.2 (73.4955), ClearSCADA 2013 R2.1 (RC Build 74.5213), ClearSCADA 2014 R1 (75.5387) and ClearSCADA 2015 R1 (76.5640) Installed Patches/Updates on Windows 7 (x64) Security Update for Windows 7, Windows Server 2008 R2, Windows Server 2008, and Windows Vista (KB3063858) https://support.microsoft.com/kb/3063858 Security Update for Windows 7, Windows Server 2008 R2, Windows Server 2008, and Windows Vista (KB3059317) https://support.microsoft.com/kb/3059317 Cumulative Security Update for Internet Explorer (KB3058515) https://support.microsoft.com/kb/3058515 Security Update for Windows 7, Windows Server 2008 R2, Windows Server 2008, Windows Vista, Windows Server 2003, and Windows XP Embedded (KB3057839) https://support.microsoft.com/kb/3057839 Security Update for Windows 7, Windows Server 2008 R2, Windows Server 2008, Windows Vista, Windows Server 2003, and Windows XP Embedded (KB3033890) -

System Requirements
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files, release notes, and the latest version of the applicable user documentation, which are available from the Trend Micro website at: http://docs.trendmicro.com/en-us/enterprise/trend-micro-apex-one.aspx Trend Micro, the Trend Micro t-ball logo, and Trend Micro Apex One are trademarks or registered trademarks of Trend Micro Incorporated. All other product or company names may be trademarks or registered trademarks of their owners. Copyright © 2019 Trend Micro Incorporated. All rights reserved. Release Date: March 2019 Protected by U.S. Patent No. 5,623,600; 5,889,943; 5,951,698; 6,119,165 Table of Contents Chapter 1: Apex One Server Installations Fresh Installations on Windows Server 2012 Platforms ..................................................................................................................................................................................... 1-2 Fresh Installations on Windows Server 2016 Platforms ..................................................................................................................................................................................... 1-3 Fresh Installations on Windows Server 2019 Platforms .................................................................................................................................................................................... -

Windows Server 2003 R2, Windows Server 2008 R2, and Windows Server 2012
Feature Comparison Windows Server 2003 R2, Windows Server 2008 R2, and Windows Server 2012 Contents Introduction ............................................................................... 3 Top Ten Features ...................................................................... 4 General Features Overview .................................................... 8 © 2012 Microsoft Corporation. All rights reserved. This document is provided "as-is." Information and views expressed in this document, including URL and other Internet Web site references, may change without notice. You bear the risk of using it. Feature Comparison: Windows Server 2003 R2, Windows Server 2008 R2, and Windows Server 2012 2 Introduction This feature comparison guide compares selected features of Windows Server 2003 R2, Windows Server 2008 R2, and Windows Server 2012. The “Top Ten Features” section provides an overview of some of the most important features of Windows Server 2012, and the “General Features Overview” section compares a wider-range of features across all three releases. The comparison tables in both sections include comments in regard to each release, as well as notation about how well each feature is supported. The legend for this notation is as follows: Level of Feature Support Feature is supported Feature is only partially supported Feature is not supported Feature Comparison: Windows Server 2003 R2, Windows Server 2008 R2, and Windows Server 2012 3 Top Ten Features This section provides an overview of the top ten features of Windows Server 2003 -

Powershell 5 Preview April 2015
Gold partner: Generální partner: Windows PowerShell 5 Preview April 2015 Michael Grafnetter www.dsinternals.com Agenda . About PowerShell 4 . PowerShell ISE 4 . New Syntax . Desired State Configuration . New Cmdlets Where to get it . Built-in – Windows 10 Preview . Windows Management Framework 5.0 Preview April 2015 – Windows Server 2012 R2 – Windows 8.1 Pro – Windows 8.1 Enterprise – Windows Server 2012 – Windows 7 SP1 – Windows Server 2008 R2 SP1 Installing PowerShell 5 Checking PowerShell Version Known incompatibilities . System Center 2012 Configuration Manager (without SP1) . Windows Small Business Server 2011 Standard Missing Documentation BLACK is BACK! Windows 10 Command Line ISE Remote Debugging Advanced Debugging . Attach to process – Enter-PSHostProcess – Exit-PSHostProcess . Break All – Console: Ctrl+Break – ISE: Ctrl+B or Debug->Break All Cortana and ISE Context Menu PowerShell Transcription PowerShell Transcription PowerShell Script Block Logging PowerShell Script Block Logging Symlink and Hardlink Support . New-Item -ItemType SymbolicLink -Name MySymLinkDir -Target $pshome . New-Item -ItemType HardLink -Path C:\Temp -Name MyHardLinkFile.txt -Value $pshome\profile.ps1 . New-Item -ItemType Junction -Path C:\Temp\MyJunctionDir -Value $pshome . Get-ChildItem DEMO Managing .ZIP Files . Compress-Archive [-Path] <String[]> [-DestinationPath] <String> [-CompressionLevel <Microsoft.PowerShell.Commands.CompressionLevel>] [-Update] . Expand-Archive [-Path] <String> [-DestinationPath] <String> DEMO New-TemporaryFile Recursion Depth -

Dell Openmanage IT Assistant Version 8.9 Release Notes
Dell OpenManage IT Assistant Version 8.9 Release Notes What’s New New major features Now, you can launch the warranty support site and view the current warranty information. In addition to the Express Service Code for PowerEdge servers; now, IT Assistant displays Chassis Express Service code and Chassis Service Tag for PowerEdge Blade servers running OpenManage Server administrator version 6.5 or later. You can also see Enclosure specific Express service code in the Details tab. New OS Support Microsoft Windows 2008 Standard Server NOTE: These operating systems must be WoW64 enabled. Deprecated features The following features are not supported in IT Assistant: Topology view Volume Information Report—As IT Assistant does not support Volume Info Report, this will be removed if you upgrade from previous version to IT Assistant 8.9. Installation For information on Installation, see the Dell OpenManage IT Assistant version 8.9 on support.dell.com/manuals Prerequisites For more information on Operating system, Browser & Consoles, and Minimum hardware Configuration see the Dell Systems Software Support Matrix Version 6.5 on support.dell.com/manuals Database (SQL Server) SQL Server 2008 R2 (This is part of IT Assistant install). Also supports: SQL Server 2000 SQL Server 2005 SP1/SP2 Additional Softwares Navisphere(R) Secure CLI For Dell/EMC storage arrays inventory, ensure your array is FLARE(R) version 19 or above. You should also install Navisphere(R) Secure CLI (version 19 or above) on your management station. NOTE: This CLI software -
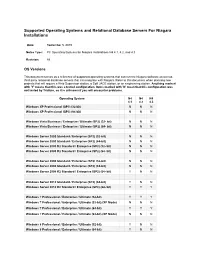
Supported Operating Systems for Niagara 4.1, 4.2
Supported Operating Systems and Relational Database Servers For Niagara Installations Date: September 5, 2019 Notes Type: PC Operating Systems for Niagara Installations N4 4.1, 4.2, and 4.3 Revision: All OS Versions This document serves as a reference of supported operating systems that can run the Niagara software as well as third party relational database servers that can integrate with Niagara. Refer to this document when planning new projects that will require a Web Supervisor station, a Soft JACE station, or an engineering station. Anything marked with 'Y' means that this was a tested configuration. Items marked with 'N' mean that this configuration was not tested by Tridium, so it is unknown if you will encounter problems. Operating System N4 N4 N4 4.1 4.2 4.3 Windows XP Professional (SP3) (32-bit) N N N Windows XP Professional (SP3) (64-bit) N N N Windows Vista Business / Enterprise / Ultimate (SP2) (32- bit) N N N Windows Vista Business / Enterprise / Ultimate (SP2) (64- bit) N N N Windows Server 2003 Standard / Enterprise (SP2) (32-bit) N N N Windows Server 2003 Standard / Enterprise (SP2) (64-bit) N N N Windows Server 2003 R2 Standard / Enterprise (SP2) (32- bit) N N N Windows Server 2003 R2 Standard / Enterprise (SP2) (64- bit) N N N Windows Server 2008 Standard / Enterprise (SP2) (32-bit) N N N Windows Server 2008 Standard / Enterprise (SP2) (64-bit) N N N Windows Server 2008 R2 Standard / Enterprise (SP2) (64- bit) Y N N Windows Server 2012 Standard / Enterprise (SP2) (64-bit) Y N N Windows Server 2012 R2 Standard / Enterprise