Computer Forensics: Permanent Erasing
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

CERIAS Tech Report 2017-5 Deceptive Memory Systems by Christopher N
CERIAS Tech Report 2017-5 Deceptive Memory Systems by Christopher N. Gutierrez Center for Education and Research Information Assurance and Security Purdue University, West Lafayette, IN 47907-2086 DECEPTIVE MEMORY SYSTEMS ADissertation Submitted to the Faculty of Purdue University by Christopher N. Gutierrez In Partial Fulfillment of the Requirements for the Degree of Doctor of Philosophy December 2017 Purdue University West Lafayette, Indiana ii THE PURDUE UNIVERSITY GRADUATE SCHOOL STATEMENT OF DISSERTATION APPROVAL Dr. Eugene H. Spa↵ord, Co-Chair Department of Computer Science Dr. Saurabh Bagchi, Co-Chair Department of Computer Science Dr. Dongyan Xu Department of Computer Science Dr. Mathias Payer Department of Computer Science Approved by: Dr. Voicu Popescu by Dr. William J. Gorman Head of the Graduate Program iii This work is dedicated to my wife, Gina. Thank you for all of your love and support. The moon awaits us. iv ACKNOWLEDGMENTS Iwould liketothank ProfessorsEugeneSpa↵ord and SaurabhBagchi for their guidance, support, and advice throughout my time at Purdue. Both have been instru mental in my development as a computer scientist, and I am forever grateful. I would also like to thank the Center for Education and Research in Information Assurance and Security (CERIAS) for fostering a multidisciplinary security culture in which I had the privilege to be part of. Special thanks to Adam Hammer and Ronald Cas tongia for their technical support and Thomas Yurek for his programming assistance for the experimental evaluation. I am grateful for the valuable feedback provided by the members of my thesis committee, Professor Dongyen Xu, and Professor Math ias Payer. -

UKUI: a Lightweight Desktop Environment Based on Pluggable
2016 International Conference on Artificial Intelligence and Computer Science (AICS 2016) ISBN: 978-1-60595-411-0 UKUI: A Lightweight Desktop Environment Based on Pluggable Framework for Linux Distribution Jie YU1, Lu SI1,*, Jun MA1, Lei LUO1, Xiao-dong LIU1, Ya-ting KUANG2, Huan PENG2, Rui LI1, Jin-zhu KONG2 and Qing-bo WU1 1College of Computer, National University of Defense Technology, Changsha, China 2Tianjin KYLIN Information Technology Co., Ltd, Tianjin, China *[email protected] *Corresponding author Keywords: Desktop environment, Ubuntu, User interface. Abstract. Ubuntu is an operating system with Linux kernel based on Debian and distributed as free and open-source software. It uses Unity as its default desktop environment, which results in more difficulties of usage for Microsoft Windows users. In this paper, we present a lightweight desktop environment named UKUI based on UbuntuKylin, the official Chinese version of Ubuntu, for Linux distribution. It is designed as a pluggable framework and provides better user experience during human-computer interaction. In order to evaluate the performance of UKUI, a set of testing bench suits were performed on a personal computer. Overall, the results showed that UKUI has better performance compared with Unity. Introduction Linux is a freely available operating system (OS) originated by Linux Torvalds and further developed by thousands of others. Typically, Linux is packaged in a form known as a Linux distribution for both desktop and server use. Some of the most popular mainstream Linux distributions are Red Hat [1], Ubuntu [2], Arch [3], openSUSY [4], Gentoo [5], etc. There are several desktop environments available for nowadays modern Linux distributions, such as XFCE [6], GNOME [7], KDE [8] and LXDE [9]. -

Linux Tutorial Last Updated: September 29 2021 for Windows Users
VLAAMS SUPERCOMPUTER Innovative Computing CENTRUM for A Smarter Flanders Linux Tutorial Last updated: September 29 2021 For Windows Users Authors: Jasper Devreker (UGent), Ewan Higgs (UGent), Kenneth Hoste (UGent) Acknowledgement: VSCentrum.be Audience: This document is a hands-on guide for using the Linux command line in the context of the UGent HPC infrastructure. The command line (sometimes called ’shell’) can seems daunting at first, but with a little understanding can be very easy to use. Everything you do startsatthe prompt. Here you have the liberty to type in any commands you want. Soon, you will be able to move past the limited point and click interface and express interesting ideas to the computer using the shell. Gaining an understanding of the fundamentals of Linux will help accelerate your research using the HPC infrastructure. You will learn about commands, managing files, and some scripting basics. Notification: In$ commands this tutorial specific commands are separated from the accompanying text: These should be entered by the reader at a command line in a terminal on the UGent-HPC. They appear in all exercises preceded by a $ and printed in bold. You’ll find those actions ina grey frame. Button are menus, buttons or drop down boxes to be pressed or selected. “Directory” is the notation for directories (called “folders” in Windows terminology) or specific files. (e.g., “/user/home/gent/vsc400/vsc40000”) “Text” Is the notation for text to be entered. Tip: A “Tip” paragraph is used for remarks or tips. They can also be downloaded from the VSC website at https://www.vscentrum.be. -

File Scavenger User Guide
File Scavenger® Version 3.2 Comprehensive Data Recovery Tool For Microsoft® Windows® 7, Vista, XP, 2008, 2003, 2000 and NT User’s Guide Revision: 4 Date: September 2010 QueTek® Consulting Corporation COPYRIGHT © Copyright 1998-2010. This document contains materials protected by International Copyright Laws. All rights reserved. No part of this manual may be reproduced, transmitted or transcribed in any form and for any purpose without the express written permission of QueTek® Consulting Corporation. TRADEMARKS Companies and products mentioned in this manual are for identification purpose only. Product names or brand names appearing in this manual may or may not be registered trademarks or copyrights of their respective companies. NOTICE Reasonable effort has been made to ensure that the information in this manual is accurate. QueTek® Consulting Corporation assumes no liability for technical inaccuracies, typographical, or other errors contained herein. QueTek® Consulting Corporation provides this manual “as is” without warranty of any kind, either express or implied, including, but not limited to the implied warranties or conditions of merchantability or fitness for a particular purpose. In no event shall QueTek® Consulting Corporation be liable for any loss of profits, or for direct, indirect, special, incidental or consequential damages arising from any defect or error in QueTek® Consulting Corporation’s products or manuals. Information in this manual is subject to change without notice and does not represent a commitment on the part of QueTek® Consulting Corporation. User Guide - ii LICENSE AGREEMENT AND LIMITED WARRANTY READ THE FOLLOWING TERMS AND CONDITIONS CAREFULLY PRIOR TO PURCHASING THE LICENSE CODE TO UNLOCK FILE SCAVENGER®. -

User's Manual Undelete® for Windows
User’s Manual Undelete® for Windows® Up-to-the-minute Data Protection® July 2007 This document describes the installation and operation of the Undelete file recovery solutions. It applies to the Server, Desktop Client, Professional and Home Editions of Undelete and is intended for Windows users and system managers. Revision/Update Information: This is a revised manual Software Versions: Undelete 5.0 Server Edition Undelete 5.0 Professional Edition Undelete 5.0 Home Edition Undelete 5.0 Desktop Client Operating Systems: Windows Server 2003 Windows XP Windows 2000 Diskeeper Corporation, Burbank, California ________________________ July 2007 _________ © 2000 — 2007 by Diskeeper Corporation The Software described in this document is owned by Diskeeper Corporation and is protected by United States copyright laws and international treaty provisions. Therefore, you must treat the Software like any other copyrighted material (e.g. a book or musical recording) except that you may either (a) make one copy of the Software solely for backup or archival purposes, or (b) transfer the Software to a single hard disk provided you keep the original solely for backup or archival purposes. You may not copy the user documentation provided with the Software, except for your own authorized use. RESTRICTED RIGHTS LEGEND The software and documentation are provided with RESTRICTED RIGHTS. Use, duplication, or disclosure by the Government is subject to restrictions as set forth in subparagraph (c)(1)(ii) of the Rights in Technical Data and Computer Software clause at DFARS 252.227-7013 or subparagraphs (c)(1) and (2) of the Commercial Computer Software-Restricted Rights at 48 CFR 52.227-19 as applicable. -
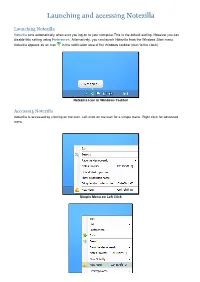
Launching and Accessing Notezilla
Launching and accessing Notezilla Launching Notezilla Notezilla runs automatically when ever you log on to your computer.This is the default setting. However you can disable this setting using Preferences. Alternatively, you can launch Notezilla from the Windows Start menu. Notezilla appears as an icon in the notification area of the Windows taskbar (next to the clock). Notezilla Icon in Windows Taskbar Accessing Notezilla Notezilla is accessed by clicking on the icon. Left click on the icon for a simple menu. Right click for advanced menu. Simple Menu on Left Click Advanced Menu on Right Click Writing your first sticky note Creating a sticky note Left click on the Notezilla icon in the Windows taskbar (next to the clock) and choose New Note from the menu to create a new sticky note. A sticky note appears on your Windows Desktop (see picture below). Right clicking on the Note Toolbar pops up the Note Menu . Sticky Note Type your tasks, appointments or a memo inside this sticky note. Setting a reminder To set a reminder, choose Due Date from the Note Menu. For faster access, use the shortcut key Ctrl+R. Positioning the sticky note You can change the position of the sticky note by simply holding the left mouse button on the note toolbar (or the note title) and dragging it to a different location on the desktop. Accessing the sticky note The sticky note that you created on the desktop may be overlapped by other program windows. You may need to access it again for viewing or editing. To view the note, left click on Notezilla icon and choose Bring Notes On Top. -

Lecture 10: File Systems File Systems, Databases, Cloud Storage
Lecture 10: File systems File systems, databases, cloud storage • file: a sequence of bytes stored on a computer – content is arbitrary (just bytes); any structure is imposed by the creator of the file, not by the operating system • file system: software that provides hierarchical storage and organization of files, usually on a single computer (or nearby) – a significant part of the operating system • database: an integrated collection of logically related records – data is organized and structured for efficient systematic access – may be distributed across lots of machines & geographically dispersed • database system: software that provides efficient access to information in a database – not usually part of the operating system • cloud storage: the same thing, but on someone else's computer(s) File systems: managing stored information • logical structure: users and programs see a hierarchy of folders (or directories) and files – a folder contains references to folder and files – "root" folder ultimately leads to all others – a file is just a sequence of bytes contents determined and interpreted by programs, not the operating system – a folder is a special file that contains names of other folders & files plus other information like size, time of change, etc. contents are completely controlled by the operating system • physical structure: disk drives operate in tracks, sectors, etc. – other storage devices have other physical properties • the operating system converts between these two views – does whatever is necessary to maintain the file/folder -

Bash Tutorial
Bash Shell Lecturer: Prof. Andrzej (AJ) Bieszczad Email: [email protected] Phone: 818-677-4954 Bash Shell The shell of Linux • Linux has a variety of different shells: – Bourne shell (sh), C shell (csh), Korn shell (ksh), TC shell (tcsh), Bour ne Again shell (bash). • Certainly the most popular shell is “bash”. Bash is an sh- compatible shell that incorporates useful features from the Korn shell (ksh) and C shell (csh). • It is intended to conform to the IEEE POSIX P1003.2/ISO 9945.2 Shell and Tools standard. • It offers functional improvements over sh for both programming and interactive use. Bash Shell Programming or Scripting ? • bash is not only an excellent command line shell, but a scripting language in itself. Shell scripting allows us to use the shell's abilities and to automate a lot of tasks that would otherwise require a lot of commands. • Difference between programming and scripting languages: – Programming languages are generally a lot more powerful and a lot faster than scriptin g languages. Programming languages generally start from source code and are compil ed into an executable. This executable is not easily ported into different operating syste ms. – A scripting language also starts from source code, but is not compiled into an executabl e. Rather, an interpreter reads the instructions in the source file and executes each inst ruction. Interpreted programs are generally slower than compiled programs. The main a dvantage is that you can easily port the source file to any operating system. bash is a s cripting language. Other examples of scripting languages are Perl, Lisp, and Tcl. -

(Electronic) Trash: True Deletion Would Soothe E-Discovery Woes
Minnesota Journal of Law, Science & Technology Volume 7 Issue 2 Article 13 2006 Throwing Out the (Electronic) Trash: True Deletion Would Soothe E-Discovery Woes Andrew Moerke Mason Follow this and additional works at: https://scholarship.law.umn.edu/mjlst Recommended Citation Andrew M. Mason, Throwing Out the (Electronic) Trash: True Deletion Would Soothe E-Discovery Woes, 7 MINN. J.L. SCI. & TECH. 777 (2006). Available at: https://scholarship.law.umn.edu/mjlst/vol7/iss2/13 The Minnesota Journal of Law, Science & Technology is published by the University of Minnesota Libraries Publishing. MASON_FINAL_UPDATED 6/7/2006 6:39:12 PM Throwing Out the (Electronic) Trash: True Deletion Would Soothe E-Discovery Woes * Andrew Moerke Mason Electronic discovery (e-discovery) consumes time, money, and resources like few other aspects of modern-day litigation. Deleted data, metadata, backup data, and other intangible forms of information make e-discovery more complex and contentious than traditional discovery.1 Computer users generate and retain electronic documents with ease, leading to significantly greater amounts of data than in a paper-only world.2 E-discovery’s volume and complexity increase litigation costs and complicate discovery disputes between parties, draining both party and judicial resources. More vexing than other areas of e-discovery, e-discovery of deleted data demands expensive forensic techniques, dampens business productivity, and holds no guarantee of yielding evidence. Parties anguish over whether deleted files on a computer hard drive could contain information critical to a © 2006 Andrew Moerke Mason. * J.D. expected 2007, University of Minnesota Law School; B.S. 1999, University of California, Berkeley. -

Encase Forensic Version 6.18.0.59
EnCase Forensic Version 6.18.0.59 Test Results for Deleted File Recovery and Active File Listing Tool (Revised) June 23, 2014 This report was prepared for the Department of Homeland Security Science and Technology Directorate Cyber Security Division by the Office of Law Enforcement Standards of the National Institute of Standards and Technology. For additional information about the Cyber Security Division and ongoing projects, please visit www.cyber.st.dhs.gov. June 2014 Test Results for Deleted File Recovery and Active File Listing Tool: EnCase Forensic Version 6.18.0.59 Revised Contents Introduction ......................................................................................................................... 1 How to Read This Report ................................................................................................... 1 1 Results Summary .......................................................................................................... 2 1.1 FAT ........................................................................................................................ 3 1.2 ExFat ...................................................................................................................... 3 1.3 NTFS ...................................................................................................................... 3 1.4 ext ........................................................................................................................... 3 1.5 HFS+ ..................................................................................................................... -

Welcome to Mac OS X 2 Installing Mac OS X
Welcome to Mac OS X 2 Installing Mac OS X 4 Aqua 6 The Dock 8 The Finder Welcome to Mac OS X, the world’s most advanced 10 Customization operating system. 12 Applications This book helps you start 14 Classic using Mac OS X. 16 Users First install the software, 18 Changing Settings then discover how easy 20 Getting Connected it is to use. 22 iTools 24 Using Mail 26 Printing 28 Troubleshooting 1 Step 1: Upgrade to Mac OS 9.1 using the CD included with Mac OS X If your computer already has Mac OS 9.1 installed, you can skip this step. Installing Step 2: Get information you need to set up Mac OS X To use your current iTools account, have your member name and password available. To use your current network settings, look in these Mac OS 9.1 control panels. Settings In Mac OS 9 TCP/IP TCP/IP control panel Internet and mail Internet control panel Dial-up connection (PPP) Remote Access and Modem control panels If you can’t find this information, look in the applications you use to get email or browse the Web. If you don’t know the information, contact your Internet service provider or system administrator. Step 3: Decide where you want to install Mac OS X On the same disk Install Mac OS X on the same disk or disk partition as Mac OS 9. ‚ Do not format the disk. Or a different disk Install Mac OS X on a different disk or disk partition from Mac OS 9. -

Apple for Newbies
Apple for Newbies While Macs are technically personal computers (PCs), the term PC is often used to describe computers that run Windows or Linux. Therefore, Macs are often referred to as personal computers, but not PCs. Unlike PCs, which are manufactured by several different companies, Apple designs and manufactures all Macintosh computers. Dock Select an item in the Dock: click its icon. When an application is running, the Dock displays an illuminated dash beneath the application's icon. To make any currently running application the active one, click its icon in the Dock to switch to it (the active application's name appears in the menu bar to the right of the Apple logo). As you open applications, their respective icons appear in the Dock, even if they weren't there originally. That means if you've got a lot of applications open, your Dock will grow substantially. If you minimize a window, the window gets pulled down into the Dock and waits until you click this icon to bring up the window again. The Dock keeps applications on its left side, while Stacks and minimized windows are kept on its right. If you look closely, you'll see a vertical separator line that separates them. If you want to rearrange where the icons appear within their line limits, just drag a docked icon to another location on the Dock and drop it. Tip: Control-click or right-click a Dock item to see a contextual menu of additional choices. Adding and removing Dock items 1. Add an item to the Dock: Click the Launchpad icon in the Dock and drag the application icon to the Dock; the icons in the Dock will move aside to make room for the new one.