Lecture 10: File Systems File Systems, Databases, Cloud Storage
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

UKUI: a Lightweight Desktop Environment Based on Pluggable
2016 International Conference on Artificial Intelligence and Computer Science (AICS 2016) ISBN: 978-1-60595-411-0 UKUI: A Lightweight Desktop Environment Based on Pluggable Framework for Linux Distribution Jie YU1, Lu SI1,*, Jun MA1, Lei LUO1, Xiao-dong LIU1, Ya-ting KUANG2, Huan PENG2, Rui LI1, Jin-zhu KONG2 and Qing-bo WU1 1College of Computer, National University of Defense Technology, Changsha, China 2Tianjin KYLIN Information Technology Co., Ltd, Tianjin, China *[email protected] *Corresponding author Keywords: Desktop environment, Ubuntu, User interface. Abstract. Ubuntu is an operating system with Linux kernel based on Debian and distributed as free and open-source software. It uses Unity as its default desktop environment, which results in more difficulties of usage for Microsoft Windows users. In this paper, we present a lightweight desktop environment named UKUI based on UbuntuKylin, the official Chinese version of Ubuntu, for Linux distribution. It is designed as a pluggable framework and provides better user experience during human-computer interaction. In order to evaluate the performance of UKUI, a set of testing bench suits were performed on a personal computer. Overall, the results showed that UKUI has better performance compared with Unity. Introduction Linux is a freely available operating system (OS) originated by Linux Torvalds and further developed by thousands of others. Typically, Linux is packaged in a form known as a Linux distribution for both desktop and server use. Some of the most popular mainstream Linux distributions are Red Hat [1], Ubuntu [2], Arch [3], openSUSY [4], Gentoo [5], etc. There are several desktop environments available for nowadays modern Linux distributions, such as XFCE [6], GNOME [7], KDE [8] and LXDE [9]. -

Communications of the Acm
COMMUNICATIONS CACM.ACM.ORG OF THEACM 11/2014 VOL.57 NO.11 Scene Understanding by Labeling Pixels Evolution of the Product Manager The Data on Diversity On Facebook, Most Ties Are Weak Keeping Online Reviews Honest Association for Computing Machinery tvx-full-page.pdf-newest.pdf 1 11/10/2013 12:03 3-5 JUNE, 2015 BRUSSELS, BELGIUM Course and Workshop C proposals by M 15 November 2014 Y CM Paper Submissions by MY 12 January 2015 CY CMY K Work in Progress, Demos, DC, & Industrial Submissions by 2 March 2015 Welcoming Submissions on Content Production Systems & Infrastructures Devices & Interaction Techniques Experience Design & Evaluation Media Studies Data Science & Recommendations Business Models & Marketing Innovative Concepts & Media Art TVX2015.COM [email protected] ACM Books M MORGAN& CLAYPOOL &C PUBLISHERS Publish your next book in the ACM Digital Library ACM Books is a new series of advanced level books for the computer science community, published by ACM in collaboration with Morgan & Claypool Publishers. I’m pleased that ACM Books is directed by a volunteer organization headed by a dynamic, informed, energetic, visionary Editor-in-Chief (Tamer Özsu), working closely with a forward-looking publisher (Morgan and Claypool). —Richard Snodgrass, University of Arizona books.acm.org ACM Books ◆ will include books from across the entire spectrum of computer science subject matter and will appeal to computing practitioners, researchers, educators, and students. ◆ will publish graduate level texts; research monographs/overviews of established and emerging fields; practitioner-level professional books; and books devoted to the history and social impact of computing. ◆ will be quickly and attractively published as ebooks and print volumes at affordable prices, and widely distributed in both print and digital formats through booksellers and to libraries and individual ACM members via the ACM Digital Library platform. -

Linux Tutorial Last Updated: September 29 2021 for Windows Users
VLAAMS SUPERCOMPUTER Innovative Computing CENTRUM for A Smarter Flanders Linux Tutorial Last updated: September 29 2021 For Windows Users Authors: Jasper Devreker (UGent), Ewan Higgs (UGent), Kenneth Hoste (UGent) Acknowledgement: VSCentrum.be Audience: This document is a hands-on guide for using the Linux command line in the context of the UGent HPC infrastructure. The command line (sometimes called ’shell’) can seems daunting at first, but with a little understanding can be very easy to use. Everything you do startsatthe prompt. Here you have the liberty to type in any commands you want. Soon, you will be able to move past the limited point and click interface and express interesting ideas to the computer using the shell. Gaining an understanding of the fundamentals of Linux will help accelerate your research using the HPC infrastructure. You will learn about commands, managing files, and some scripting basics. Notification: In$ commands this tutorial specific commands are separated from the accompanying text: These should be entered by the reader at a command line in a terminal on the UGent-HPC. They appear in all exercises preceded by a $ and printed in bold. You’ll find those actions ina grey frame. Button are menus, buttons or drop down boxes to be pressed or selected. “Directory” is the notation for directories (called “folders” in Windows terminology) or specific files. (e.g., “/user/home/gent/vsc400/vsc40000”) “Text” Is the notation for text to be entered. Tip: A “Tip” paragraph is used for remarks or tips. They can also be downloaded from the VSC website at https://www.vscentrum.be. -

The Strange Birth and Long Life of Unix - IEEE Spectrum Page 1 of 6
The Strange Birth and Long Life of Unix - IEEE Spectrum Page 1 of 6 COMPUTING / SOFTWARE FEATURE The Strange Birth and Long Life of Unix The classic operating system turns 40, and its progeny abound By WARREN TOOMEY / DECEMBER 2011 They say that when one door closes on you, another opens. People generally offer this bit of wisdom just to lend some solace after a misfortune. But sometimes it's actually true. It certainly was for Ken Thompson and the late Dennis Ritchie, two of the greats of 20th-century information technology, when they created the Unix operating system, now considered one of the most inspiring and influential pieces of software ever written. A door had slammed shut for Thompson and Ritchie in March of 1969, when their employer, the American Telephone & Telegraph Co., withdrew from a collaborative project with the Photo: Alcatel-Lucent Massachusetts Institute of KEY FIGURES: Ken Thompson [seated] types as Dennis Ritchie looks on in 1972, shortly Technology and General Electric after they and their Bell Labs colleagues invented Unix. to create an interactive time- sharing system called Multics, which stood for "Multiplexed Information and Computing Service." Time-sharing, a technique that lets multiple people use a single computer simultaneously, had been invented only a decade earlier. Multics was to combine time-sharing with other technological advances of the era, allowing users to phone a computer from remote terminals and then read e -mail, edit documents, run calculations, and so forth. It was to be a great leap forward from the way computers were mostly being used, with people tediously preparing and submitting batch jobs on punch cards to be run one by one. -

The Strange Birth and Long Life of Unix - IEEE Spectrum
The Strange Birth and Long Life of Unix - IEEE Spectrum http://spectrum.ieee.org/computing/software/the-strange-birth-and-long-li... COMPUTING / SOFTWARE FEATURE The Strange Birth and Long Life of Unix The classic operating system turns 40, and its progeny abound By WARREN TOOMEY / DECEMBER 2011 They say that when one door closes on you, another opens. People generally offer this bit of wisdom just to lend some solace after a misfortune. But sometimes it's actually true. It certainly was for Ken Thompson and the late Dennis Ritchie, two of the greats of 20th-century information technology, when they created the Unix operating system, now considered one of the most inspiring and influential pieces of software ever written. A door had slammed shut for Thompson and Ritchie in March of 1969, when their employer, the American Telephone & Telegraph Co., withdrew from a collaborative project with the Photo: Alcatel-Lucent Massachusetts Institute of KEY FIGURES: Ken Thompson [seated] types as Dennis Ritchie looks on in 1972, shortly Technology and General Electric after they and their Bell Labs colleagues invented Unix. to create an interactive time-sharing system called Multics, which stood for "Multiplexed Information and Computing Service." Time-sharing, a technique that lets multiple people use a single computer simultaneously, had been invented only a decade earlier. Multics was to combine time-sharing with other technological advances of the era, allowing users to phone a computer from remote terminals and then read e-mail, edit documents, run calculations, and so forth. It was to be a great leap forward from the way computers were mostly being used, with people tediously preparing and submitting batch jobs on punch cards to be run one by one. -
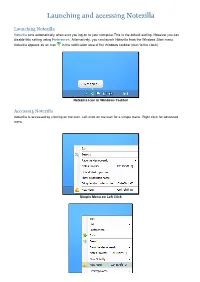
Launching and Accessing Notezilla
Launching and accessing Notezilla Launching Notezilla Notezilla runs automatically when ever you log on to your computer.This is the default setting. However you can disable this setting using Preferences. Alternatively, you can launch Notezilla from the Windows Start menu. Notezilla appears as an icon in the notification area of the Windows taskbar (next to the clock). Notezilla Icon in Windows Taskbar Accessing Notezilla Notezilla is accessed by clicking on the icon. Left click on the icon for a simple menu. Right click for advanced menu. Simple Menu on Left Click Advanced Menu on Right Click Writing your first sticky note Creating a sticky note Left click on the Notezilla icon in the Windows taskbar (next to the clock) and choose New Note from the menu to create a new sticky note. A sticky note appears on your Windows Desktop (see picture below). Right clicking on the Note Toolbar pops up the Note Menu . Sticky Note Type your tasks, appointments or a memo inside this sticky note. Setting a reminder To set a reminder, choose Due Date from the Note Menu. For faster access, use the shortcut key Ctrl+R. Positioning the sticky note You can change the position of the sticky note by simply holding the left mouse button on the note toolbar (or the note title) and dragging it to a different location on the desktop. Accessing the sticky note The sticky note that you created on the desktop may be overlapped by other program windows. You may need to access it again for viewing or editing. To view the note, left click on Notezilla icon and choose Bring Notes On Top. -

Bash Tutorial
Bash Shell Lecturer: Prof. Andrzej (AJ) Bieszczad Email: [email protected] Phone: 818-677-4954 Bash Shell The shell of Linux • Linux has a variety of different shells: – Bourne shell (sh), C shell (csh), Korn shell (ksh), TC shell (tcsh), Bour ne Again shell (bash). • Certainly the most popular shell is “bash”. Bash is an sh- compatible shell that incorporates useful features from the Korn shell (ksh) and C shell (csh). • It is intended to conform to the IEEE POSIX P1003.2/ISO 9945.2 Shell and Tools standard. • It offers functional improvements over sh for both programming and interactive use. Bash Shell Programming or Scripting ? • bash is not only an excellent command line shell, but a scripting language in itself. Shell scripting allows us to use the shell's abilities and to automate a lot of tasks that would otherwise require a lot of commands. • Difference between programming and scripting languages: – Programming languages are generally a lot more powerful and a lot faster than scriptin g languages. Programming languages generally start from source code and are compil ed into an executable. This executable is not easily ported into different operating syste ms. – A scripting language also starts from source code, but is not compiled into an executabl e. Rather, an interpreter reads the instructions in the source file and executes each inst ruction. Interpreted programs are generally slower than compiled programs. The main a dvantage is that you can easily port the source file to any operating system. bash is a s cripting language. Other examples of scripting languages are Perl, Lisp, and Tcl. -

Unix and Shell Programming
UNIX AND SHELL PROGRAMMING OBJECTIVE: UNIX – Born in the dark and somber portals of Bell Labs, it was a dream that one man nurtured and cherished. Like a parent, he reared the infant with compassion and zeal. And as the fledgling grew and spread its wings, it caught the attention of the world. This chapter will explore through the basics of UNIX, along with certain commands which itself are categorized accordingly. The File System and Some File Handling Commands: The file system is one of the its simplest and it lets users not to access files not belonging to them, You will be learning about categorization of files, the significance of HOME directory, mkdir, rmdir, and absolute, relative path name. Kenneth T. Moras 8/21/2007 BRIEF HISTORY 1966 The Multiplexed Time Sharing and Computing System or MULTICS project was a joint attempt by General Electric (GE), AT&T Bell Labs and the Massachusetts Institute of Technology (MIT) at developing a stable multiuser operating system The aim is to create an operating system that could support a lot of simultaneous users (thousands!). Multics stands for Multiplexed Information and Computer service. Left Ken Thompson, Right Dennis Ritchie The people involved in the project at this time are Ken Thompson, Dennis Ritchie, Joseph Ossanna, Stuart Feldman, Doug McIIroy and Bob Morris. Although a very simple version of MULTICS could now run on a GE645 computer, it could only support 3 people and therefore the original goals of this operating system had not been met, the research and development is just so expensive and Bell Labs withdraws their sponsorship. -

Welcome to Mac OS X 2 Installing Mac OS X
Welcome to Mac OS X 2 Installing Mac OS X 4 Aqua 6 The Dock 8 The Finder Welcome to Mac OS X, the world’s most advanced 10 Customization operating system. 12 Applications This book helps you start 14 Classic using Mac OS X. 16 Users First install the software, 18 Changing Settings then discover how easy 20 Getting Connected it is to use. 22 iTools 24 Using Mail 26 Printing 28 Troubleshooting 1 Step 1: Upgrade to Mac OS 9.1 using the CD included with Mac OS X If your computer already has Mac OS 9.1 installed, you can skip this step. Installing Step 2: Get information you need to set up Mac OS X To use your current iTools account, have your member name and password available. To use your current network settings, look in these Mac OS 9.1 control panels. Settings In Mac OS 9 TCP/IP TCP/IP control panel Internet and mail Internet control panel Dial-up connection (PPP) Remote Access and Modem control panels If you can’t find this information, look in the applications you use to get email or browse the Web. If you don’t know the information, contact your Internet service provider or system administrator. Step 3: Decide where you want to install Mac OS X On the same disk Install Mac OS X on the same disk or disk partition as Mac OS 9. ‚ Do not format the disk. Or a different disk Install Mac OS X on a different disk or disk partition from Mac OS 9. -

Apple for Newbies
Apple for Newbies While Macs are technically personal computers (PCs), the term PC is often used to describe computers that run Windows or Linux. Therefore, Macs are often referred to as personal computers, but not PCs. Unlike PCs, which are manufactured by several different companies, Apple designs and manufactures all Macintosh computers. Dock Select an item in the Dock: click its icon. When an application is running, the Dock displays an illuminated dash beneath the application's icon. To make any currently running application the active one, click its icon in the Dock to switch to it (the active application's name appears in the menu bar to the right of the Apple logo). As you open applications, their respective icons appear in the Dock, even if they weren't there originally. That means if you've got a lot of applications open, your Dock will grow substantially. If you minimize a window, the window gets pulled down into the Dock and waits until you click this icon to bring up the window again. The Dock keeps applications on its left side, while Stacks and minimized windows are kept on its right. If you look closely, you'll see a vertical separator line that separates them. If you want to rearrange where the icons appear within their line limits, just drag a docked icon to another location on the Dock and drop it. Tip: Control-click or right-click a Dock item to see a contextual menu of additional choices. Adding and removing Dock items 1. Add an item to the Dock: Click the Launchpad icon in the Dock and drag the application icon to the Dock; the icons in the Dock will move aside to make room for the new one. -

Enterprise Computing
Computing at Extreme Scale – The Challenge and Excitement of Modern Computing Stuart Feldman Unicamp, VP, Engineering Campinas, Brasil Google 11 August 2008 1 Outline Future of Computers Expanding Frontiers of Computer Science Demands of modern online information systems: search and ads Google’s unique approaches to infrastructure: hardware, software, middleware Successes and Problems The Future – Concerns and Opportunities 2 Who Am I Vice President-Engineering for Google’s “East Coast” engineering offices • includes Canada, Brazil, Chicago, Texas Also, Past President of the ACM On a number of boards and committees • US National Science Foundation (2) • Business Schools • Australia’s NICTA Past • PhD in theory of galaxies • Early member of the “Unix bunch” at Bell Labs • Wrote Make, first Fortran 77 compiler, etc. • Went to Bellcore Research – software engineering and a detour to large-scale development • Went to IBM Research – Internet, E-commerce, long-term computer science research. 3 Future of Computers 4 Scale Measures Number of users Amount of Data • Ever • Stored • Recent • New • Simultaneous • Changed Amount of Networking and Amount of computing Communication • Total operations • Messages per second • Operations per byte of data • Bytes per second • Bytes of data analyzed per second • Kilometer-bytes per second 5 Processors Hardware progress has driven field forever • Range of possibility relevant to topics, details, constraints Current state • Stuck on practical thread speed • Able to execute lots of independent threads- multicore and massive multicore • Wirth’s Law as well as Moore’s • Specialized hardware possibility 6 Other Hardware Other relevant changes • Interconnect • Network • Memory • Storage hierarchy 7 Challenges Long term bets • Quantum computing • Molecular, etc. -

Customizing Konqueror
,COPYRIGHT.16171 Page iv Wednesday, March 30, 2005 4:55 PM Test Driving Linux by David Brickner Copyright © 2005 O’Reilly Media, Inc. All rights reserved. Printed in the United States of America. Published by O’Reilly Media, Inc., 1005 Gravenstein Highway North, Sebastopol, CA 95472. O’Reilly books may be purchased for educational, business, or sales promotional use. Online editions are also available for most titles (safari.oreilly.com). For more informa- tion, contact our corporate/institutional sales department: (800) 998-9938 or [email protected]. Editor: Andy Oram Production Editor: Emily Quill Cover Designer: Mike Kohnke Interior Designer: Marcia Friedman Printing History: April 2005: First Edition. Nutshell Handbook, the Nutshell Handbook logo, and the O’Reilly logo are registered trademarks of O’Reilly Media, Inc. The Linux series designations, Test Driving Linux, and related trade dress are trademarks of O’Reilly Media, Inc. Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in this book, and O’Reilly Media, Inc. was aware of a trademark claim, the designations have been printed in caps or initial caps. While every precaution has been taken in the preparation of this book, the publisher and author assume no responsibility for errors or omissions, or for damages resulting from the use of the information contained herein. This book uses RepKover™, a durable and flexible lay-flat binding. ISBN: 0-596-00754-X [M] ,ch02.4045 Page 29 Wednesday, March 30, 2005 4:42 PM Chapter 2 2 + SURF THE ! WEB 29 ,ch02.4045 Page 30 Wednesday, March 30, 2005 4:42 PM epending on how much time you spend on the Internet, your web browser may be one of the most important programs on your Dcomputer.