In the Tcp Ip Protocol Suite
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

DE-CIX Academy Handout
Networking Basics 04 - User Datagram Protocol (UDP) Wolfgang Tremmel [email protected] DE-CIX Management GmbH | Lindleystr. 12 | 60314 Frankfurt | Germany Phone + 49 69 1730 902 0 | [email protected] | www.de-cix.net Networking Basics DE-CIX Academy 01 - Networks, Packets, and Protocols 02 - Ethernet 02a - VLANs 03 - the Internet Protocol (IP) 03a - IP Addresses, Prefixes, and Routing 03b - Global IP routing 04 - User Datagram Protocol (UDP) 05 - TCP ... Layer Name Internet Model 5 Application IP / Internet Layer 4 Transport • Data units are called "Packets" 3 Internet 2 Link Provides source to destination transport • 1 Physical • For this we need addresses • Examples: • IPv4 • IPv6 Layer Name Internet Model 5 Application Transport Layer 4 Transport 3 Internet 2 Link 1 Physical Layer Name Internet Model 5 Application Transport Layer 4 Transport • May provide flow control, reliability, congestion 3 Internet avoidance 2 Link 1 Physical Layer Name Internet Model 5 Application Transport Layer 4 Transport • May provide flow control, reliability, congestion 3 Internet avoidance 2 Link • Examples: 1 Physical • TCP (flow control, reliability, congestion avoidance) • UDP (none of the above) Layer Name Internet Model 5 Application Transport Layer 4 Transport • May provide flow control, reliability, congestion 3 Internet avoidance 2 Link • Examples: 1 Physical • TCP (flow control, reliability, congestion avoidance) • UDP (none of the above) • Also may contain information about the next layer up Encapsulation Packets inside packets • Encapsulation is like Russian dolls Attribution: Fanghong. derivative work: Greyhood https://commons.wikimedia.org/wiki/File:Matryoshka_transparent.png Encapsulation Packets inside packets • Encapsulation is like Russian dolls • IP Packets have a payload Attribution: Fanghong. -

A Secure Peer-To-Peer Web Framework
A Secure Peer-to-Peer Web Framework Joakim Koskela Andrei Gurtov Helsinki Institute for Information Technology Helsinki Institute for Information Technology PO Box 19800, 00076 Aalto PO Box 19800, 00076 Aalto Email: joakim.koskela@hiit.fi Email: andrei.gurtov@hiit.fi Abstract—We present the design and evaluation of a se- application, that can be deployed without investing in dedi- cure peer-to-peer HTTP middleware framework that enables cated infrastructure while addressing issues such as middlebox a multitude of web applications without relying on service traversal, mobility, security and identity management. providers. The framework is designed to be deployed in existing network environments, allowing ordinary users to create private II. PEER-TO-PEER HTTP services without investing in network infrastructure. Compared to previous work, scalability, NAT/firewall traversal and peer From its launch in the early 1990s, the HyperText Transfer mobility is achieved without the need for maintaining dedicated Protocol (HTTP) had grown to be one of the most popular servers by utilizing new network protocols and re-using existing protocols on the Internet today. It is used daily for everything network resources. from past-time activities, such as recreational browsing, gam- I. INTRODUCTION ing and media downloads, to business- and security-critical Peer-to-peer (P2P) systems have been popular within net- applications such as payment systems and on-line banking. work research during the past years as they have the potential The success of HTTP has clearly grown beyond its original to offer more reliable, fault-tolerant and cost-efficient network- design as a simple, easy to manage protocol for exchanging ing. -

Solutions to Chapter 2
CS413 Computer Networks ASN 4 Solutions Solutions to Assignment #4 3. What difference does it make to the network layer if the underlying data link layer provides a connection-oriented service versus a connectionless service? [4 marks] Solution: If the data link layer provides a connection-oriented service to the network layer, then the network layer must precede all transfer of information with a connection setup procedure (2). If the connection-oriented service includes assurances that frames of information are transferred correctly and in sequence by the data link layer, the network layer can then assume that the packets it sends to its neighbor traverse an error-free pipe. On the other hand, if the data link layer is connectionless, then each frame is sent independently through the data link, probably in unconfirmed manner (without acknowledgments or retransmissions). In this case the network layer cannot make assumptions about the sequencing or correctness of the packets it exchanges with its neighbors (2). The Ethernet local area network provides an example of connectionless transfer of data link frames. The transfer of frames using "Type 2" service in Logical Link Control (discussed in Chapter 6) provides a connection-oriented data link control example. 4. Suppose transmission channels become virtually error-free. Is the data link layer still needed? [2 marks – 1 for the answer and 1 for explanation] Solution: The data link layer is still needed(1) for framing the data and for flow control over the transmission channel. In a multiple access medium such as a LAN, the data link layer is required to coordinate access to the shared medium among the multiple users (1). -

I.L. 40-614A 1 1. INTRODUCTION the Basic Interface to Remote Terminal, Or BIRT, Is an INCOM Network Master. BIRT Gives Users An
I.L. 40-614A 1. INTRODUCTION 3. DESCRIPTION The Basic Interface to Remote Terminal, or BIRT, is 3.1. Power Requirements an INCOM Network Master. BIRT gives users an economical way of getting information from their Range: 48 Vdc to 250 Vdc and 120 Vac INCOM-compatible devices since it connects directly between a user’s external MODEM or personal com- Burden: 3.5 W @ 48 Vdc puter and the INCOM network. 9 W @ 250 Vdc 5 W @ 120 Vac BIRT can directly replace Westinghouse MINTs, talk- ing to all INCOM-based communication devices. 3.2. Temperature Range BIRTs also include a special high-speed mode for communicating with SADIs – allowing users to collect For Operation: 0˚ to +55˚ C data from other manufacturer’s relays more rapidly For Storage: -20˚ to +80˚ C than ever before. 3.3. Physical Dimensions BIRTs are built to handle the abuse of substation environment; their “hardened” RS-232 serial port can The BIRT enclosure dimensions are identical to the handle surges and sustained high voltages that ERNI and SADI, as shown in figure 1. would destroy ordinary serial ports, and BIRTs can run on a wide range of voltages, from 48 to 250 Vdc Dimensions and weight of chassis or even 120 Vac, with no jumpers or adjustments needed. Height: 5.26” (133.6) mm) Width: 3.32” (84.3) mm) Depth: 5.92” (150.4) mm) 2. FEATURES Weight: 2.0 lbs (0.9 kg) BIRT is designed to be very flexible in its RS-232 External Wiring: See figures 2 and 3. -

The Internet in Iot—OSI, TCP/IP, Ipv4, Ipv6 and Internet Routing
Chapter 2 The Internet in IoT—OSI, TCP/IP, IPv4, IPv6 and Internet Routing Reliable and efficient communication is considered one of the most complex tasks in large-scale networks. Nearly all data networks in use today are based on the Open Systems Interconnection (OSI) standard. The OSI model was introduced by the International Organization for Standardization (ISO), in 1984, to address this composite problem. ISO is a global federation of national standards organizations representing over 100 countries. The model is intended to describe and standardize the main communication functions of any telecommunication or computing system without regard to their underlying internal structure and technology. Its goal is the interoperability of diverse communication systems with standard protocols. The OSI is a conceptual model of how various components communicate in data-based networks. It uses “divide and conquer” concept to virtually break down network communication responsibilities into smaller functions, called layers, so they are easier to learn and develop. With well-defined standard interfaces between layers, OSI model supports modular engineering and multivendor interoperability. 2.1 The Open Systems Interconnection Model The OSI model consists of seven layers as shown in Fig. 2.1: physical (Layer 1), data link (Layer 2), network (Layer 3), transport (Layer 4), session (Layer 5), presentation (Layer 6), and application (Layer 7). Each layer provides some well-defined services to the adjacent layer further up or down the stack, although the distinction can become a bit less defined in Layers 6 and 7 with some services overlapping the two layers. • OSI Layer 7—Application Layer: Starting from the top, the application layer is an abstraction layer that specifies the shared protocols and interface methods used by hosts in a communications network. -

User Datagram Protocol - Wikipedia, the Free Encyclopedia Página 1 De 6
User Datagram Protocol - Wikipedia, the free encyclopedia Página 1 de 6 User Datagram Protocol From Wikipedia, the free encyclopedia The five-layer TCP/IP model User Datagram Protocol (UDP) is one of the core 5. Application layer protocols of the Internet protocol suite. Using UDP, programs on networked computers can send short DHCP · DNS · FTP · Gopher · HTTP · messages sometimes known as datagrams (using IMAP4 · IRC · NNTP · XMPP · POP3 · Datagram Sockets) to one another. UDP is sometimes SIP · SMTP · SNMP · SSH · TELNET · called the Universal Datagram Protocol. RPC · RTCP · RTSP · TLS · SDP · UDP does not guarantee reliability or ordering in the SOAP · GTP · STUN · NTP · (more) way that TCP does. Datagrams may arrive out of order, 4. Transport layer appear duplicated, or go missing without notice. TCP · UDP · DCCP · SCTP · RTP · Avoiding the overhead of checking whether every RSVP · IGMP · (more) packet actually arrived makes UDP faster and more 3. Network/Internet layer efficient, at least for applications that do not need IP (IPv4 · IPv6) · OSPF · IS-IS · BGP · guaranteed delivery. Time-sensitive applications often IPsec · ARP · RARP · RIP · ICMP · use UDP because dropped packets are preferable to ICMPv6 · (more) delayed packets. UDP's stateless nature is also useful 2. Data link layer for servers that answer small queries from huge 802.11 · 802.16 · Wi-Fi · WiMAX · numbers of clients. Unlike TCP, UDP supports packet ATM · DTM · Token ring · Ethernet · broadcast (sending to all on local network) and FDDI · Frame Relay · GPRS · EVDO · multicasting (send to all subscribers). HSPA · HDLC · PPP · PPTP · L2TP · ISDN · (more) Common network applications that use UDP include 1. -

Network Connectivity and Transport – Transport
Idaho Technology Authority (ITA) ENTERPRISE STANDARDS – S3000 NETWORK AND TELECOMMUNICATIONS Category: S3510 – NETWORK CONNECTIVITY AND TRANSPORT – TRANSPORT CONTENTS: I. Definition II. Rationale III. Approved Standard(s) IV. Approved Product(s) V. Justification VI. Technical and Implementation Considerations VII. Emerging Trends and Architectural Directions VIII. Procedure Reference IX. Review Cycle X. Contact Information Revision History I. DEFINITION Transport provides for the transparent transfer of data between different hosts and systems. The two (2) primary transport protocols in the Transmission Control Protocol/Internet Protocol (TCP/IP) suite are the Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP). II. RATIONALE Idaho State government must be able to easily, reliably, and economically communicate data and information to conduct State business. TCP/IP is the protocol standard used throughout the global Internet and endorsed by ITA Policy 3020 – Connectivity and Transport Protocols, for use in State government networks (LAN and WAN). III. APPROVED STANDARD(S) TCP/IP Transport: 1. Transmission Control Protocol (TCP); and 2. User Datagram Protocol (UDP). IV. APPROVED PRODUCT(S) Standards-based products and architecture S3510 – Network Connectivity and Transport – Transport Page 1 of 2 V. JUSTIFICATION TCP and UDP are the transport standards for critical State applications like electronic mail and World Wide Web services. VI. TECHNICAL AND IMPLEMENTATION CONSIDERATIONS It is also important to carefully consider the security implications of the deployment, administration, and operation of a TCP/IP network. VII. EMERGING TRENDS AND ARCHITECTURAL DIRECTIONS The use of TCP/IP (Internet) protocols and applications continues to increase. Agencies purchasing new systems may want to consider compatibility with the emerging Internet Protocol Version 6 (IPv6), which was designed by the Internet Engineering Task Force to replace IPv4 and will dramatically expand available IP addresses. -

Performance Evaluation of TCP Multihoming for IPV6 Anycast Networks and Proxy Placement
University of Central Florida STARS Electronic Theses and Dissertations, 2004-2019 2015 Performance Evaluation of TCP Multihoming for IPV6 Anycast Networks and Proxy Placement Raya Alsharfa University of Central Florida Part of the Electrical and Electronics Commons Find similar works at: https://stars.library.ucf.edu/etd University of Central Florida Libraries http://library.ucf.edu This Masters Thesis (Open Access) is brought to you for free and open access by STARS. It has been accepted for inclusion in Electronic Theses and Dissertations, 2004-2019 by an authorized administrator of STARS. For more information, please contact [email protected]. STARS Citation Alsharfa, Raya, "Performance Evaluation of TCP Multihoming for IPV6 Anycast Networks and Proxy Placement" (2015). Electronic Theses and Dissertations, 2004-2019. 1350. https://stars.library.ucf.edu/etd/1350 PERFORMANCE EVALUATION OF TCP MULTIHOMING FOR IPV6 ANYCAST NETWORKS AND PROXY PLACEMENT by RAYA MAJID ALSHARFA B.S. NAJAF TECHNICAL COLLEGE, 2010 A thesis submitted in partial fulfillment of the requirements for the degree of Master of Science in Electrical Engineering. in the Department of Electrical Engineering and Computer Science in the College of Engineering and Computer Science at the University of Central Florida Orlando, Florida Fall Term 2015 Major Professor: Mostafa Bassiouni © 2015 Raya Majid Alsharfa ii ABSTRACT In this thesis, the impact of multihomed clients and multihomed proxy servers on the performance of modern networks is investigated. The network model used in our investigation integrates three main components: the new one-to-any Anycast communication paradigm that facilitates server replication, the next generation Internet Protocol Version 6 (IPv6) that offers larger address space for packet switched networks, and the emerging multihoming trend of connecting devices and smart phones to more than one Internet service provider thereby acquiring more than one IP address. -

Ipv6-Ipsec And
IPSec and SSL Virtual Private Networks ITU/APNIC/MICT IPv6 Security Workshop 23rd – 27th May 2016 Bangkok Last updated 29 June 2014 1 Acknowledgment p Content sourced from n Merike Kaeo of Double Shot Security n Contact: [email protected] Virtual Private Networks p Creates a secure tunnel over a public network p Any VPN is not automagically secure n You need to add security functionality to create secure VPNs n That means using firewalls for access control n And probably IPsec or SSL/TLS for confidentiality and data origin authentication 3 VPN Protocols p IPsec (Internet Protocol Security) n Open standard for VPN implementation n Operates on the network layer Other VPN Implementations p MPLS VPN n Used for large and small enterprises n Pseudowire, VPLS, VPRN p GRE Tunnel n Packet encapsulation protocol developed by Cisco n Not encrypted n Implemented with IPsec p L2TP IPsec n Uses L2TP protocol n Usually implemented along with IPsec n IPsec provides the secure channel, while L2TP provides the tunnel What is IPSec? Internet IPSec p IETF standard that enables encrypted communication between peers: n Consists of open standards for securing private communications n Network layer encryption ensuring data confidentiality, integrity, and authentication n Scales from small to very large networks What Does IPsec Provide ? p Confidentiality….many algorithms to choose from p Data integrity and source authentication n Data “signed” by sender and “signature” verified by the recipient n Modification of data can be detected by signature “verification” -

Chapter 6: Chapter 6: Implementing a Border Gateway Protocol Solution Y
Chapter 6: Implementing a Border Gateway Protocol Solution for ISP Connectivity CCNP ROUTE: Implementing IP Routing ROUTE v6 Chapter 6 © 2007 – 2010, Cisco Systems, Inc. All rights reserved. Cisco Public 1 Chapter 6 Objectives . Describe basic BGP terminology and operation, including EBGP and IBGP. ( 3) . Configure basic BGP. (87) . Typical Issues with IBGP and EBGP (104) . Verify and troubleshoot basic BGP. (131) . Describe and configure various methods for manipulating path selection. (145) . Describe and configure various methods of filtering BGP routing updates. (191) Chapter 6 © 2007 – 2010, Cisco Systems, Inc. All rights reserved. Cisco Public 2 BGP Terminology, Concepts, and Operation Chapter 6 © 2007 – 2010, Cisco Systems, Inc. All rights reserved. Cisco Public 3 IGP versus EGP . Interior gateway protocol (IGP) • A routing protocol operating within an Autonomous System (AS). • RIP, OSPF, and EIGRP are IGPs. Exterior gateway protocol (EGP) • A routing protocol operating between different AS. • BGP is an interdomain routing protocol (IDRP) and is an EGP. Chapter 6 © 2007 – 2010, Cisco Systems, Inc. All rights reserved. Cisco Public 4 Autonomous Systems (AS) . An AS is a group of routers that share similar routing policies and operate within a single administrative domain. An AS typically belongs to one organization. • A singgpgyp()yle or multiple interior gateway protocols (IGP) may be used within the AS. • In either case, the outside world views the entire AS as a single entity. If an AS connects to the public Internet using an exterior gateway protocol such as BGP, then it must be assigned a unique AS number which is managed by the Internet Assigned Numbers Authority (IANA). -

Data Link Layer
Data link layer Goals: ❒ Principles behind data link layer services ❍ Error detection, correction ❍ Sharing a broadcast channel: Multiple access ❍ Link layer addressing ❍ Reliable data transfer, flow control: Done! ❒ Example link layer technology: Ethernet Link layer services Framing and link access ❍ Encapsulate datagram: Frame adds header, trailer ❍ Channel access – if shared medium ❍ Frame headers use ‘physical addresses’ = “MAC” to identify source and destination • Different from IP address! Reliable delivery (between adjacent nodes) ❍ Seldom used on low bit error links (fiber optic, co-axial cable and some twisted pairs) ❍ Sometimes used on high error rate links (e.g., wireless links) Link layer services (2.) Flow Control ❍ Pacing between sending and receiving nodes Error Detection ❍ Errors are caused by signal attenuation and noise. ❍ Receiver detects presence of errors signals sender for retrans. or drops frame Error Correction ❍ Receiver identifies and corrects bit error(s) without resorting to retransmission Half-duplex and full-duplex ❍ With half duplex, nodes at both ends of link can transmit, but not at same time Multiple access links / protocols Two types of “links”: ❒ Point-to-point ❍ PPP for dial-up access ❍ Point-to-point link between Ethernet switch and host ❒ Broadcast (shared wire or medium) ❍ Traditional Ethernet ❍ Upstream HFC ❍ 802.11 wireless LAN MAC protocols: Three broad classes ❒ Channel Partitioning ❍ Divide channel into smaller “pieces” (time slots, frequency) ❍ Allocate piece to node for exclusive use ❒ Random -
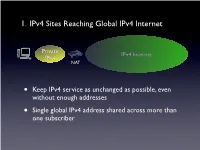
1. Ipv4 Sites Reaching Global Ipv4 Internet
1. IPv4 Sites Reaching Global IPv4 Internet Private IPv4 Internet IPv4 NAT • Keep IPv4 service as unchanged as possible, even without enough addresses • Single global IPv4 address shared across more than one subscriber SP IPv6 Network Private Tunnel for IPv4 (public, private, port-limited, etc....) IPv4 Internet IPv4 • Scenario #2 - Service Providers Running out of Private IPv4 space • IPv4 / IPv6 encapsulations/tunnels • Tunnels setup by DHCP, Routing, etc. between a GW and Router • Wherever the NAT lands, it is important that the user keeps control of it • Provides a path to delivering IPv6 SP IPv6 Network Tunnel for IPv4 (public, private, port-limited, etc....) IPv4 Internet • Scenario #3a “Wireless Greenfield” • IPv4 / IPv6 encapsulations/tunnels • Tunnels setup between a host and a Router • IPv4 binding for host applications, transport over IPv6 • Wherever the NAT lands, it is important that the user keeps control of it 3 - 5 Translation Options IPv6 Internet IPv4 Internet IPv6 IPv4 My IPv6 Network IPv6 Internet IPv4 Internet • “Scenario #3” • NAT64/DNS64.... - Stateful, DNSSEC Challenges, DNS64 location, etc. My IPv6 Network IPv6 Internet IPv4 Internet • “Scenario #5” • IVI - NAT-PT..... Expose only certain IPv6 servers, etc. MY IPv4 Network IPv6 Internet IPv4 Internet • “Scenario #4” • NAT64 - 1:1, Stateless, DNSSEC OK, no DNS64 MY IPv4 Network IPv6 Internet IPv4 Internet • Already solved by existing transition mechanisms?? (teredo, etc). Scenarios 1 - 5 1. IPv4 Sites Reaching Global IPv4 Internet Private IPv4 Internet IPv4 NAT • Keep IPv4 service as unchanged as possible, even without enough addresses • Single global IPv4 address shared across more than one subscriber 2. Service Providers Running out of Private IPv4 space ISP Private IPv4 Private Network IPv4 IPv4 Internet • Service Providers with large, privately addressed, IPv4 networks • Organic growth plus pressure to free global addresses for customer use contribute to the problem • The SP Private networks in question generally do not need to reach the Internet at large 3.