Protocol-Aware Reactive LTE Signal Overshadowing and Its Applications in Dos Attacks
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

America's Best Deserve Our Best
Teachers and their Families America’s Best Deserve our best 25% Discount for Eligible Educators Certified/licensed K-12 classroom teachers/educators are eligible Existing customers qualify and it is for ALL the lines on your plan No Purchase Necessary Bring your Own devices to AT&T & get up to $500 in pre-paid Visa cards! Call - Text - Email Additional Promotions Authorized AT&T Retailer JP Stork *FREE Devices 720-635-6119 *FREE Wireless Charging [email protected] Pads w /3+ new phones AT&T April Promotional Pricing *No purchase necessary for 25% discount Eligible Devices: • Eligible Purchased Smartphones o iPhone XS 64GB ($900), 256GB ($1050), 512GB ($1250) o iPhone XR 64GB ($500), 128GB ($550) o iPhone 11 Pro 64GB ($900), 256GB ($1050), 512GB ($1250) o iPhone 11 Pro Max 64GB ($1000), 256GB ($1150), 512GB ($1350) o iPhone 12 mini 64GB ($700), 128GB ($750), 256GB ($850) o iPhone 12 64GB ($800), 128GB ($850), 256GB ($950) o iPhone 12 Pro 128GB ($1000), 256GB ($1100), 512GB ($1300) o iPhone 12 Pro Max 128GB ($1100), 256GB ($1200), 512GB ($1400) • Eligible Trade-in Smartphones: o To qualify for $700 credit, minimum Trade-In value must be $95 or higher after device condition questions have been answered o Eligible devices: ▪ Apple: 8, 8 Plus, X, XR, XS, XS Max, 11, 11 Pro, 11 Pro Max, 12, 12 mini, 12 Pro, 12 Pro Max ▪ Samsung: A71, A71 5G, Fold, Z Fold2 5G, Galaxy S9, Galaxy S9+, Galaxy S9+ Duos, Galaxy S10, Galaxy S10+, Galaxy S10 5G, Galaxy S10e, Galaxy S10 Lite, Galaxy S20, Galaxy S20 Ultra 5G, Galaxy S20+ 5G, Note9, Note10, Note10+, -
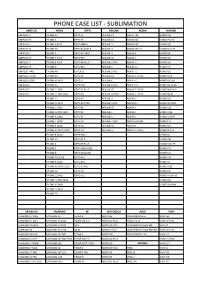
Qikink Product & Price List
PHONE CASE LIST - SUBLIMATION ONEPLUS APPLE OPPO REALME NOKIA HUAWEI ONEPLUS 3 IPHONE SE OPPO F3 REALME C1 NOKIA 730 HONOR 6X ONEPLUS 3T IPHONE 6 OPPO F5 REALME C2 NOKIA 640 HONOR 9 LITE ONEPLUS 5 IPHONE 6 PLUS OPPO FIND X REALME 3 NOKIA 540 HONOR Y9 ONEPLUS 5T IPHONE 6S OPPO REALME X REALME 3i NOKIA 7 PLUS HONOR 10 LITE ONEPLUS 6 IPHONE 7 OPPO F11 PRO REALME 5i NOKIA 8 HONOR 8C ONEPLUS 6T IPHONE 7 PLUS OPPO F15 REALME 5S NOKIA 6 HONOR 8X ONEPLUS 7 IPHONE 8 PLUS OPPO RENO 2F REALME 2 PRO NOKIA 3.1 HONOR 10 ONEPLUS 7T IPHONE X OPPO F11 REALME 3 NOKIA 2.1 HONOR 7C ONEPLUS 7PRO IPHONE XR OPPOF13 REALME 3 PRO NOKIA 7.1 HONOR 5C ONEPLUS 7T PRO IPHONE XS OPPO F1 REALME C3 NOKIA 3.1 PLUS HONOR P20 ONEPLUS NORD IPHONE XS MAX OPPO F7 REALME 6 NOKIA 5.1 HONOR 6PLUS ONEPLUS X IPHONE 11 OPPO A57 REALME 6 PRO NOKIA 7.2 HONOR PLAY 8A ONEPLUS 2 IPHONE 11 PRO OPPO F1 PLUS REALME X2 NOKIA 7.1 PLUS HONOR NOVA 3i ONEPLUS 1 IPHONE 11 PRO MAX OPPO F9 REALME X2 PRO NOKIA 6.1 PLUS HONOR PLAY IPHONE 12 OPPO A7 REALME 5 NOKIA 6.1 HONOR 8X IPHONE 12 MINI OPPO R17 PRO REALME 5 PRO NOKIA 8.1 HONOR 8X MAX IPHONE 12 PRO OPPO K1 REALME XT NOKIA 2 HONOR 20i IPHONE 12 PRO MAX OPPO F9 REALME 1 NOKIA 3 HONOR V20 IPHONE X LOGO OPPO F3 REALME X NOKIA 5 HONOR 6 PLAY IPHONE 7 LOGO OPPO A3 REALME 7 PRO NOKIA 6 (2018) HONOR 7X IPHONE 6 LOGO OPPO A5 REALME 5S NOKIA 8 HONOR 5X IPHONE XS MAX LOGO OPPO A9 REALME 5i NOKIA 2.1 PLUS HONOR 8 LITE IPHONE 8 LOGO OPPO R98 HONOR 8 IPHONE 5S OPPO F1 S HONOR 9N IPHONE 4 OPPO F3 PLUS HONOR 10 LITE IPHONE 5 OPPO A83 (2018) HONOR 7S IPHONE 8 -
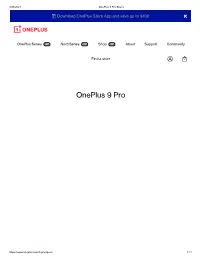
Oneplus 9 Pro Specs
3/23/2021 OnePlus 9 Pro Specs Download OnePlus Store App and save up to $100. OnePlus Series New Nord Series New Shop New About Support Community Find a store OnePlus 9 Pro https://www.oneplus.com/9-pro/specs 1/11 3/23/2021 OnePlus 9 Pro Specs Pine Green $1,069 Buy now Height: 163.2 mm Dimensions Width: 73.6 mm Thickness: 8 7 mm https://www.oneplus.com/9-pro/specs 2/11 3/23/2021 Thickness: 8.7 mm OnePlus 9 Pro Specs Weight: 197g Display Parameters Size: 6.7 inches (Measured diagonally from corner to corner.) esolution: 3216 X 1440 pixels 525 ppi Aspect atio: 20.1:9 Type: 120 Hz Fluid AMOLED with LTPO Support sGB, Display P3, 10-bit Color Depth Cover Glass: Corning® Gorilla® Glass Features Hyper Touch eading Mode Night Mode Vibrant Color Effect Pro Motion Graphics Smoothing Ultra-high Video esolution Adaptive Display Performance Operating System: OxygenOS based on Android™ 11 CPU: Qualcomm® Snapdragon™888 5G Chipset: X60 GPU: Adreno 660 AM: 8GB/12GB LPDD5 Storage: 128GB/256GB UFS 3.1 2-LANE B tt 4 500 Ah (2S1P 2 250 Ah bl ) https://www.oneplus.com/9-pro/specs 3/11 3/23/2021 OnePlus 9 Pro Specs Battery: 4,500 mAh (2S1P 2,250 mAh, non-removable) Warp Charge 65T (10V/6.5A) 50W Wireless Charging Camera Main Camera Sensor: Sony IMX789 Sensor Size: 1/1.43" Megapixels: 48 Pixel Size: 1.12µm OIS: Yes Lens Quantity: 7P Focal Length: 23mm equivalent Aperture: ƒ/1,8 Ultra-Wide Camera Sensor: Sony IMX766 Sensor Size: 1/1.56" Megapixels: 50 Lens Quantity: 7P Focal Length: 14mm equivalent Aperture: ƒ/2,2 Lens: Freeform Lens Telephoto Camera Megapixels: -

Case 2:20-Cv-00385 Document 1 Filed 12/15/20 Page 1 of 26 Pageid #: 1
Case 2:20-cv-00385 Document 1 Filed 12/15/20 Page 1 of 26 PageID #: 1 IN THE UNITED STATES DISTRICT COURT FOR THE EASTERN DISTRICT OF TEXAS MARSHALL DIVISION § NORTHSTAR SYSTEMS LLC, § § Case No. Plaintiff, § § JURY TRIAL DEMANDED v. § § SHENZHEN ONEPLUS SCIENCE & § TECHNOLOGY CO., LTD., § § Defendant § COMPLAINT FOR PATENT INFRINGEMENT Plaintiff NorthStar Systems LLC (“NorthStar” or “Plaintiff”) for its Complaint against Defendant Shenzhen OnePlus Science & Technology Co., Ltd. (“OnePlus” or “Defendant”) alleges as follows: THE PARTIES 1. NorthStar is a limited liability company organized and existing under the laws of the State of Texas, with its principal place of business located at 203 East Travis Street, Marshall, Texas 75670 2. Upon information and belief, Defendant OnePlus is a corporation organized and existing under the laws of China, with its principal place of business located at 18F, Tairan Building, Block C, Tairan 8th Road, Chegongmiao, Futian District, Shenzhen, Guangdong 518040, China, and may be served pursuant to the provisions of the Hague Convention. OnePlus is a leading manufacturer and seller of smartphones in the world and in the United States. Upon information and belief, OnePlus does business in Texas and in the Eastern District of Texas, directly or through its subsidiaries. Case 2:20-cv-00385 Document 1 Filed 12/15/20 Page 2 of 26 PageID #: 2 JURISDICTION 3. This is an action for patent infringement arising under the patent laws of the United States, 35 U.S.C. §§ 1, et seq. This Court has jurisdiction over this action pursuant to 28 U.S.C. §§ 1331 and 1338(a). -

Get Additional ₹ 3000 on Exchange. Kind Offer
Offer Title: Get Additional ₹3000 on Exchange Kind Offer: Exchange price is subject to physical check. Offer Description: Upgrade to the latest Galaxy A72 and get additional ₹3000 on exchange of your old Samsung smartphone device. Offer available on select Samsung devices only and availability of the Offer is subject to area pin codes of customers. Exchange for devices purchased via Samsung.com - Important Information: 1. You can exchange your old select Samsung smartphone device with Galaxy A72. 2. The Exchange Offer is provided to you by Samsung in collaboration with “Manak Waste Management Pvt Ltd., (“Cashify”)” and the evaluation and exchange of your old Samsung smartphone device shall be subject to the terms and conditions of Cashify, for details refer https://www.cashify.in/terms-of-use & https://www.cashify.in/terms-conditions. 3. Exchange can be done on "Samsung Shop". Galaxy A72 Galaxy A72 (8/128 GB) (8/256 GB) ₹ 3000 ₹ 3000 4. Please give correct inputs, with regards to screen condition & availability of accessories, at the time of evaluating your old Smartphone. Any incorrect information provided by you shall result in cancellation/rejection of the Exchange Offer. In such scenario, you shall not be eligible to receive the exchange value and/or any benefit/Offer from Samsung or the exchange partner in lieu of the Exchange Offer or exchange value and no claims shall be entertained in this regard. 5. Exchange Price shown is the Maximum Price subject to physical check at the time of exchange. 6. The screen condition and accessories declared by you will be verified at the time of exchange. -

Terms & Conditions
Terms & Conditions — Galaxy S10 Lite Upgrade Offer — The Additional Exchange on Upgrade Offer ("Offer") is provided by Samsung India Electronics Pvt. Ltd. at its sole discretion on purchase of Samsung Galaxy S10 Lite (all variants) (hereinafter referred to as "Product"). This offer is valid in selected outlets and in select cities only or online through Samsung Shop at www.samsung.com/in or the Samsung Shop app and shall be available for all customers who purchase & activate the product till February 29, 2020. This Offer shall be available on exchange of select smartphones only with a new Samsung Galaxy S10 Lite (All variants). Offer can be availed by visiting select Samsung Outlets in select cities ("Outlet") or online through Samsung Shop at www.samsung.com/in. With selected old eligible Device ₹3000 For details of the online journey, please read complete instructions on Samsung Shop by visiting the respective product page. Samsung reserves the right to withdraw, extend, annul or modify the Offer at any point of time without any prior intimation. Any disputes arising out of and in connection with this Offer shall be subject to the exclusive jurisdiction of the courts in the state of New Delhi only. Other terms and conditions of My Galaxy Upgrade program shall continue to apply. Eligible Old Device Model Name iPhone 6 iPhone 6 Plus iPhone 6s iPhone 6s Plus iPhone 7 iPhone 7 Plus iPhone 8 iPhone 8 Plus iPhone X iPhone SE iPhone XR iPhone Xs iPhone Xs Max iPhone 11 iPhone 11 Pro iPhone 11 Max Google Pixel Google Pixel Google Pixel 2 Google -
7/10/2020 AXP Internal 1 American Express® Terms and Conditions
American Express® Terms and Conditions • This offer is open to all American Express Card members whose accounts are valid and in good standing. An American Express Cardmember ("Cardmember") for the purpose of this offer means a person holding a card issued by American Express® in India. • This offer is not valid for American Express Corporate Cards issued by American Express Banking Corp. in India and/or Cards issued by a third party bearing the name or trademark or service mark or logo of American Express ("Network Cards ") issued in India. The offer in this program will be fulfilled at the merchant’s end only. • The offer would be valid on above mentioned cards issued in India only • This offer is being made purely on a “best effort” basis. Cardmembers are not bound in any manner to participate in this offer and any such participation is purely voluntary. • American Express is neither responsible for availability of services nor guarantees the quality of the goods/services and is not liable for any defect or deficiency of goods or services so obtained/availed of by the Cardmembers under this offer. Any disputes with regard to the quality of goods/services availed shall be taken up with the merchant/service establishment directly. American Express shall have no liability whatsoever with regard to the same. • American Express shall not be liable whatsoever for any loss/damage/claims that may arise out of use or non-use of any goods or services availed by Cardmember under this offer. American Express reserves its absolute right to withdraw and/or alter any of the terms and conditions of the offer at any time without prior notice. -

Oneplus 7T – Manuel Utilisateur
OnePlus 7T – Manuel utilisateur En raison de mises à jour logicielles, votre connaissance de l'interface (y compris, mais sans s'y limiter, les fonctionnalités logicielles, les expériences utilisateur et d'interaction) peut différer de celle présentée dans ce manuel. L'interface du logiciel est susceptible d'être modifiée. Installation et désinstallation d'applications 23 Table des matières Utilisation des applications 24 Écran d'accueil 26 PREMIERS PAS 11 Panneau de notifications 28 Vue avant 12 Assistant Google 31 Vue arrière 13 Configuration de votre appareil 14 PARAMETRES 33 Batterie et charge 15 Wi-Fi et Internet 34 Boutons physiques 17 Wi-Fi 34 Transfert de données vers l'appareil OnePlus 7T 19 SIM et réseau 35 NOTIONS DE BASE 21 Point d'accès et connexion 36 Gestes de base 22 Bluetooth et connexion de l'appareil 37 Bluetooth 37 Mode Écouteur 45 NFC 38 Sonneries et vibrations 45 Android Beam 39 Système 46 Paiement sans contact 39 Boutons et gestes 46 Écran 40 Curseur d'alerte 46 Barre de navigation et gestes 47 Personnalisation 42 Gestes rapides 48 Sons et vibrations 43 Activation rapide de l'appareil photo 49 Volume 43 Activation rapide de l'assistant 49 Dolby Atmos 44 Utilitaires 49 Ne pas déranger 44 Sécurité et écran de verrouillage 51 Système 59 État de la sécurité 51 Accessibilité 59 Sécurité de l'appareil 52 Langues et saisie 59 Sécurité personnelle 55 Date et heure 60 Sauvegarde 61 Localisation 56 Options de réinitialisation 61 Confidentialité 56 Stockage OTG 62 Gestionnaire de permissions 56 Programmes d'amélioration de -
Barometer of Mobile Internet Connections in Poland
Barometer of Mobile Internet Connections in Poland Publication of July 21, 2020 First half 2020 nPerf is a trademark owned by nPerf SAS, 87 rue de Sèze 69006 LYON – France. Contents 1 Summary of results ...................................................................................................................... 2 1.1 nPerf score, all technologies combined ............................................................................... 2 1.2 Our analysis ........................................................................................................................... 3 2 Overall results 2G/3G/4G ............................................................................................................. 3 2.1 Data amount and distribution ............................................................................................... 3 2.2 Success rate 2G/3G/4G ........................................................................................................ 4 2.3 Download speed 2G/3G/4G .................................................................................................. 4 2.4 Upload speed 2G/3G/4G ....................................................................................................... 5 2.5 Latency 2G/3G/4G ................................................................................................................ 5 2.6 Browsing test 2G/3G/4G....................................................................................................... 6 2.7 Streaming test 2G/3G/4G .................................................................................................... -

Manufacturer Model Asus ROG Phone Asus ROG Phone II
Manufacturer Model Notes Asus ROG Phone Asus ROG Phone II Asus ROG Phone III Supports Depth API Asus Zenfone 6 Asus Zenfone 7/7 Pro Asus Zenfone AR Asus Zenfone ARES Fujitsu Arrows 5G Supports Depth API Fujitsu Arrows NX9 F-52A Supports Depth API General Mobile GM 9 Plus Requires Android 8.0 or later Not currently included in the CSV file provided by the Google GooGle Nexus 5X Play Console GooGle Nexus 6P Requires Android 8.0 or later GooGle Pixel GooGle Pixel XL Supports 60 fps camera capture frame rate on the rear-facing camera Supports multiple GPU texture resolutions - 1080p, 720p, 480p GooGle Pixel 2 Supports Depth API Supports 60 fps camera capture frame rate on the rear-facing camera Supports multiple GPU texture resolutions - 1080p, 720p, 480p GooGle Pixel 2 XL Supports Depth API Supports 60 fps camera capture frame rate on the rear-facing camera When 60 fps camera capture mode is active, the camera uses fixed focus Supports multiple GPU texture resolutions - 1080p, 720p, 480p GooGle Pixel 3 Supports Depth API Supports 60 fps camera capture frame rate on the rear-facing camera When 60 fps camera capture mode is active, the camera uses fixed focus Supports multiple GPU texture resolutions - 1080p, 720p, 480p GooGle Pixel 3 XL Supports Depth API Supports multiple GPU texture resolutions - 1080p, 720p, 480p GooGle Pixel 3a Supports Depth API Supports multiple GPU texture resolutions - 1080p, 720p, 480p GooGle Pixel 3a XL Supports Depth API Supports 60 fps camera capture frame rate on the rear-facing camera on Android 10 Dec 2019 OTA -

Galaxy Tab S7+ (LTE). 2
Offer Title: Get Additional ₹5000 on Exchange Kind Offer: Exchange price is subject to physical check. Offer Description: Upgrade to the latest Galaxy Tab S7+ (LTE) and get additional ₹5000 on exchange of your old Samsung smartphone device. Offer available on select Samsung devices only and availability of the Offer is subject to area pin codes of customers. Exchange for devices purchased via Samsung.com - Important Information: 1. You can exchange your old select Samsung smartphone device with Galaxy Tab S7+ (LTE). 2. The Exchange Offer is provided to you by Samsung in collaboration with “Manak Waste Management Pvt Ltd., (“Cashify”) and the evaluation and exchange of your old Samsung smartphone device shall be subject to the terms and conditions of Cashify, for details refer https://www.cashify.in/terms-of-use & https://www.cashify.in/terms-conditions. 3. Exchange can be done on "Samsung Shop". Galaxy Tab S7+ (LTE) (6/128) ₹5000 4. Please give correct inputs, with regards to screen condition & availability of accessories, at the time of evaluating your old Smartphone. Any incorrect information provided by you shall result in cancellation/rejection of the Exchange Offer. In such scenario, you shall not be eligible to receive the exchange value and/or any benefit/Offer from Samsung or the exchange partner in lieu of the Exchange Offer or exchange value and no claims shall be entertained in this regard. 5. Exchange Price shown is the Maximum Price subject to physical check at the time of exchange. 6. The screen condition and accessories declared by you will be verified at the time of exchange. -

IN the UNITED STATES DISTRICT COURT for the EASTERN DISTRICT of TEXAS MARSHALL DIVISION § LONGHORN HD LLC., § Case No
Case 2:21-cv-00082-JRG Document 1 Filed 03/10/21 Page 1 of 10 PageID #: 1 IN THE UNITED STATES DISTRICT COURT FOR THE EASTERN DISTRICT OF TEXAS MARSHALL DIVISION § LONGHORN HD LLC., § Case No. § Plaintiff, § JURY TRIAL DEMANDED § v. § § ONEPLUS TECHNOLOGY (SHENZHEN) § CO., LTD., § Defendant. § § COMPLAINT FOR PATENT INFRINGEMENT Plaintiff Longhorn HD LLC. (“LHD” or “Plaintiff”) for its Complaint against Defendant OnePlus Technology (Shenzhen) Co., Ltd. (“OnePlus” or “Defendant”) alleges as follows: THE PARTIES 1. LHD is a limited liability company organized and existing under the laws of the State of Texas, with its principal place of business located at 203 East Travis Street, Marshall, Texas 75670 2. Upon information and belief, Defendant OnePlus is a corporation organized and existing under the laws of China, with its principal place of business located at 18F, Tairan Building, Block C, Tairan 8th Road, Chegongmiao, Futian District, Shenzhen, Guangdong 518040, China, and may be served pursuant to the provisions of the Hague Convention. OnePlus is a leading manufacturer and seller of smartphones in the world and in the United States. Upon information and belief, OnePlus does business in Texas and in the Eastern District of Texas, directly or through its subsidiaries. Case 2:21-cv-00082-JRG Document 1 Filed 03/10/21 Page 2 of 10 PageID #: 2 3. Defendant has authorized sellers and sales representatives that offer and sell products pertinent to this Complaint through the State of Texas, including in this Judicial District, and to consumers