Cloudlinux Documentation © 2015 Cloud Linux Inc
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Sistem Pendukung Keputusan Dalam Pemilihan Control Panel Virtual Private Server Menggunakan Metode AHP Dan SAW
Citec Journal, Vol. 5, No. 1, November 2017 – Januari 2018 ISSN: 2460-4259 14 Sistem Pendukung Keputusan Dalam Pemilihan Control Panel Virtual Private Server Menggunakan Metode AHP dan SAW Decision Support System in Selection of a Control Panel Virtual Private Server Using AHP and SAW Method Arwendra Adi Putra*1, Kusrini 2, Eko Pramono3 1,2,3Magister Teknik Informatika, Universitas Amikom Yogyakarta E-mail: [email protected], [email protected], [email protected] Abstrak Hosting dapat dibedakan menjadi berbagai macam type, salah satunya adalah Virtual Private Server (VPS). VPS merupakan sebuah cara untuk membagi sumber daya sebuah physical server menjadi server virtual. Sebuah VPS memerlukan control panel karena untuk mempermudah pengaturan seperti mengelola email, disk, database, penambahan domain, memonitor bandwidth dan backup data. Terdapat berbagai macam control panel dengan spesifikasi yang berbeda-beda. Pemilihan control panel tersebut sangat penting karena control panel tersebut harus disesuaikan dengan spesifikasi VPS. Berdasarkan permasalahan tersebut, diperlukan sistem yang dapat membantu dalam pengambilan keputusan dalam pemilihan control panel. Metode yang digunakan dalam penelitian ini adalah dengan menggunakan metode Analitical Hierarcy Process (AHP) dan Simple Additive Weighting (SAW). Metode AHP digunakan untuk mencari bobot variabel kriteria, sedangkan metode SAW digunakan untuk menentukan nilai akhir dan perangkingan. Hasil perangkingan alternatif control panel pada sistem ini menunjukkan hasil yang sama dengan hasil perangkingan dari pakar control panel, sehingga sistem ini dapat digunakan oleh pengguna sebagai dasar pengambilan keputusan dalam menentukan pemilihan alternatif control panel. Kata Kunci — control panel, VPS, AHP, SAW, sistem pendukung keputusan Abstract Hosting can be divided into various types, one of them is Virtual Private Server (VPS). -

Resin 3.2 Reference
Contents 1 Overview 3 1.1 Features - Resin and Resin Professional . .3 2 Installation 11 2.1 Resin Installation Quick Start . 11 2.2 Resin Installation . 16 2.3 Resin Web Server . 16 2.4 Resin with Apache . 22 2.5 Resin with IIS . 34 2.6 How the Plugins Dispatch to Resin . 44 3 Command-Line 47 3.1 Command-Line Configuration . 47 4 Admin Guide 51 4.1 User Guide: Administration . 51 5 Watchdog 63 5.1 Resin Watchdog . 63 6 Virtual Hosts 73 6.1 Virtual Hosting . 73 7 Clustering 89 7.1 Resin Clustering . 89 8 Web Applications 109 8.1 An Overview of Web Applications . 109 9 Logging 137 9.1 Log . 137 10 Administration 163 10.1 Resin Administration . 163 1 CONTENTS 11 Deployment 177 11.1 Packaging/Deployment . 177 12 Proxy Caching 181 12.1 Server Caching . 181 13 Quercus 193 13.1 Quercus: PHP in Java . 193 14 Security 217 14.1 Resin Security . 217 15 Inversion of Control 271 15.1 Resin IoC . 271 15.2 Scheduled Task . 308 16 Amber 327 16.1 Amber . 327 17 Embedding Resin 355 17.1 Embedding Resin . 355 18 Filters 367 18.1 Filters . 367 19 BAM 379 19.1 BAM . 379 20 Comet 405 20.1 Comet/Server-Push Servlet . 405 21 Remoting 411 21.1 Resin Remoting . 411 21.2 Hessian . 417 22 Messaging 423 22.1 Resin Messaging . 423 23 JSF - Java Server Faces 435 23.1 JSF - Java Server Faces . 435 24 Configuration Tags 445 24.1 cluster: Cluster tag configuration . -

PHP Programming Cookbook I
PHP Programming Cookbook i PHP Programming Cookbook PHP Programming Cookbook ii Contents 1 PHP Tutorial for Beginners 1 1.1 Introduction......................................................1 1.1.1 Where is PHP used?.............................................1 1.1.2 Why PHP?..................................................2 1.2 XAMPP Setup....................................................3 1.3 PHP Language Basics.................................................5 1.3.1 Escaping to PHP...............................................5 1.3.2 Commenting PHP..............................................5 1.3.3 Hello World..................................................6 1.3.4 Variables in PHP...............................................6 1.3.5 Conditional Statements in PHP........................................7 1.3.6 Loops in PHP.................................................8 1.4 PHP Arrays...................................................... 10 1.5 PHP Functions.................................................... 12 1.6 Connecting to a Database............................................... 14 1.6.1 Connecting to MySQL Databases...................................... 14 1.6.2 Connecting to MySQLi Databases (Procedurial).............................. 14 1.6.3 Connecting to MySQLi databases (Object-Oriented)............................ 15 1.6.4 Connecting to PDO Databases........................................ 15 1.7 PHP Form Handling................................................. 15 1.8 PHP Include & Require Statements......................................... -

Godaddy's Hosting Services System Description Updated
GoDaddy’s Hosting Services System Description Background GoDaddy, based in Scottsdale, Arizona, provides a broad range of internet business software and services. GoDaddy’s hosting services refer to the housing, maintenance, and provision of internet service (bandwidth) to servers. GoDaddy offers the following hosting services which are covered by this system overview: • Web Hosting including cPanel for Linux, Parallels Plesk for Windows, and legacy Shared/Grid Hosting products (4GH) • WordPress Hosting • Servers – Dedicated and Virtual Private GoDaddy’s hosting services are housed in the following domestic and international data center locations, with the breakdown of hosting services as referenced in the table below: Data cPanel Plesk Legacy WordPress Dedicated Virtual Center Shared Private Virginia √ √ √ √ √ Arizona √ √ √ √ √ √ Netherlands √ √ √ √ √ Germany √ Singapore √ √ √ √ Infrastructure Shared web hosting services and WordPress hosting house multiple customers in a single server cluster, following a multi-tenant architecture. Customers interact with their hosting environment using the applicable control panel – cPanel for Linux, Parallels Plesk for Windows, and Hosting Control Center (HCC) for the legacy shared environment. Customers manage their own content including information stored on MySQL and MSSQL customer databases. Customers are also responsible for website setup and backups. GoDaddy manages system and hardware level security and patching. Updated: December 30, 2019 Page 1 GoDaddy’s Hosting Services System Description Dedicated servers in VA and AZ provide customers with an entire single-tenant virtual server housed on a single hypervisor1. Initial configuration is performed by provisioning code on the hypervisor based on customer elections made during the setup process. The customer manages system level access and is responsible for server setup, security, patching, and backups while GoDaddy manages hardware level security for all dedicated servers. -
For Your Linux Server
cPanel // Linux Server Getting Started Guide cPanel for your Linux Server AKJZNAzsqknsxxkjnsjx Getting Started Guide Page 1 cPanel // Linux Server Getting Started Guide: cPanel, Linux Server Version 2.2 (1.6.2012) © Copyright 2012. All rights reserved. Distribution of this work or derivative of this work is prohibited unless prior written permission is obtained from the copyright holder. Trademarks used in this book Linux® is a registered trademark of Linus Torvalds. cPanel® is a registered trademark of cPanel, Inc. SSH® and Secure Shell® are trademarks of SSH Communications Security, Inc. RedHat® and Fedora® are registered trademarks of Red Hat Software, Inc. Mac® is a registered trademark of Apple Computer, Inc. UNIX® is a registered trademark of The Open Group. Windows XP®, Entourage®, and Outlook® are registered trademarks of Microsoft Corporation in the United States and/or other countries. Thunderbird™ is an unregistered trademark of the Mozilla Foundation. All other trademarks and copyrights are the property of their respective owners. AKJZNAzsqknsxxkjnsjx Getting Started Guide Page 2 cPanel // Linux Server Table of Contents Introduction 5 SECURITY INFORMATION! 5 REPROVISIONING YOUR SERVER! 6 GETTING HELP! 7 OTHER RESOURCES! 9 Setting Up Your Dedicated Server 10 CHOOSING A HOST NAME, USER ID, AND PASSWORD! 10 LOGGING IN TO YOUR MANAGER FOR THE FIRST TIME! 13 Connecting to Your Dedicated Server 14 CONNECTING TO YOUR SERVER USING WHM! 15 CONNECTING TO YOUR SERVER USING SSH! 20 GAINING ROOT ACCESS ON YOUR SERVER! 22 AKJZNAzsqknsxxkjnsjx -

How to Install Webmin/Virtualmin in Linux (Centos 7)
Advanced Network/System Administration and Security Workshop ECE Building, Building, BUET, Dhaka Date: 10-12 December 2019 How to Install Webmin/Virtualmin in Linux (CentOS 7) What Is Virtualmin? Virtualmin is a Webmin module that is typically used to manage multiple virtual hosts through a single interface, similar to cPanel. It supports multiple functions such as creating/managing Apache virtual hosts, MySQL database creation/management, generating DNS zones, managing mailboxes, and much more. How Do I Install Virtualmin On CentOS 7? This guide implies that you’re using the root account on Cloud, VPS or Dedicated Server to perform the installation and that you have a basic working knowledge of a Linux shell. We highly suggest taking a backup of your server prior to proceeding with this script. Although this document is written for CentOS 7, Virtualmin offers an automated installation script for the following distros: • CentOS/RHEL/Scientific Linux 7 on x86_64 • CentOS/RHEL/Scientific Linux 5 and 6 on i386 or x86_64 • Debian 6, 7, and 8 on i386 or amd64 • Ubuntu 12.04 LTS, 14.04 LTS, and 16.04 LTS on i386 or amd64 (non-LTS releases are not supported) The following steps can be utilized to install Virtualmin in a CentOS 7 (RHEL 7) environment on a fresh OS installation. 1. Ensure your server is up to date sudo yum update -y 2. Download the Virtualmin installer script using wget sudo wget http://software.virtualmin.com/gpl/scripts/install.sh 3. Execute the install script Md. Ariful Islam Manager (Data & Transmission Network), BdREN E-mail: [email protected] Advanced Network/System Administration and Security Workshop ECE Building, Building, BUET, Dhaka Date: 10-12 December 2019 sudo sh install.sh As per the warning when the script is executed ensure that your OS is listed and type “y” then press “Enter” to continue with the installation If prompted you may need to enter in a fully qualified hostname. -

Virtual Wishlist
Virtual Wishlist Figure 1: Welcome Page of the Virtual Wishlist Group project carried out by Josua Dietrich, Nils Braune and Tino Canziani created 2011 at D-ITET, ETH Zürich 21.12.2011 Contents 1 Introduction and Background 3 1.1 Idea . .3 1.2 Related Work . .3 1.3 Tools . .3 2 Concept 5 2.1 Core functions . .5 2.2 Website Layout . .5 2.3 Sessions & Proles . .7 3 Implementation 8 3.1 HTML/Login/Session (Welcome.html) . .8 3.2 MySQL server: creating a database . .9 3.3 setupConnection.php . 11 3.4 $.ajax(), getWishlists() .................. 12 3.5 Adding a prole picture . 14 4 Results and Future Steps 16 4.1 Results . 16 4.1.1 Welcome Page . 16 4.1.2 Prole Page . 16 4.1.3 my Wishes menu . 16 4.1.4 my Friends and Search Friends Menu . 16 4.1.5 Settings menu . 17 4.1.6 Friend Page . 17 4.1.7 Terms, Privacy, About, Help Page . 17 4.1.8 Process of fullling and getting wishes fullled . 17 4.1.9 Security . 17 4.2 Future steps . 18 A Server/PHP functions 20 B Screenshot of the prole page 21 C Setting up the Virtual Wishlist step by step 22 D Endnotes 23 1 Abstract In this group project we designed and implemented a virtual wish list as a social media service on the web. It enables its users to maintain a personal prole, create their own wish lists or opt to grant other friends their specic wishes. The use case of this virtual wish list will mostly tend to birthday and christmas events, social gatherings, leisure activities or work related events. -
Spamexperts Incoming Email Filter a Powerful Solution to Safeguard Networks from Inbound Spam and Malware, Helping Web Hosts Save Time and Money
DATASHEET SpamExperts Incoming Email Filter A powerful solution to safeguard networks from inbound spam and malware, helping web hosts save time and money. Inbound spam, ransomware, and phishing attempts can put any internet service provider at risk. N-able™ SpamExperts helps web hosts and ISPs/telcos strengthen email protection. Services include affordable inbound filtering driven by a continuously updated Intelligent Protection & Filtering Engine to meet emerging threats. The solution can be deployed in a redundant cloud environment or on premises. How it works: N-able SpamExperts incoming spam filter is an email gateway solution. Activation is done with a simple DNS adjustment. Once the MX records are changed, all inbound email goes to our system first, where it is filtered and then relayed to the unchanged destination mail servers of your clients. It provides first-level defense running in front of your mail infrastructure and separates legitimate from unsolicited email with the help of advanced filtering algorithms and spam pattern detection methods. It offers full inbox protection with a nearly 100% accuracy rate. Potentially harmful messages are queued in quarantine and can be managed by end users. Helps save resources and money • Protects networks against the latest email-based threats. • Saves network resources with an efficient first-level incoming filter defense. • Helps save money with competitive and affordable licenses. Offers dual deployment options and integrates with a broad range of tools • Cloud or on-premises deployment. • Free add-ons to integrate with the most popular control panels and other email collaboration tools. • Multiple branding options available. Global statistics Gives customers and users visibility and control over their email flows • Empowers users to manage their email flows and gain real-time visibility into threats. -

Control Panels
Control Panels cPanel Plesk Direct Admin Other Control Panels Docker cPanel Intro CrossBox for cPanel is one of our most popular control panel integrations. It's Plug-and-Play in its core, covering 95% of all cPanel setups out of the box. Our deep integration with cPanel hooks and APIs enables an automated and fine- tuned experience for both the end-user and service provider. All data and computing are 100% hosted/done on the cPanel server. Benefits End-users: Easy access either via cPanel's webmail system or direct URL No complicated IMAP/SMTP/POP3 configuration, only email address, and password are required Instant access to Email Chat Audio/video calls Conferences Files Contacts And many other features, directly integrated with a cPanel hosting account Real-time push notifications Change password within CrossBox Recover access to an email account Service Providers: Provide users with a modern communication suite that is deeply integrated with and running on a cPanel server Easier customer onboarding Better brand exposure No changes to the cPanel server, services, or configuration files needed Everything is 100% hosted on the cPanel server itself cPanel account quota support WHM Feature List support Automatic cPanel Integration MTA/Mail Server CrossBox supports Exim and Dovecot out of the box, and won't make any changes to your existing MTA/mail server configuration. From standard Exim configurations to smart external relays, CrossBox supports any configuration. Webmail cPanel users can choose CrossBox as their Webmail Application of choice when accessing cPanel's Webmail. Note that if you have a Branding Addon purchased, the cPanel Webmail interface will show your custom App Logo. -

System Requirements
System Requirements This section outlines the requirements for installing the Ushahidi platform on your computer. The "AMP" (Apache, Mysql, PHP) Stack Before installing Ushahidi, following must be installed in the target system: PHP version 5.2.3 or greater PHP 5.4 support is added in Ushahidi 2.6 Prior to Ushahidi 2.6, you must version between PHP 5.2.3 - 5.3.x MySQL version 5.0 or greater An HTTP Server. Kohana, which Ushahidi is built on, is known to work with the following web servers: Apache 1.3+ Apache2.0+ lighttpd Microsoft Internet Information Server (MS IIS) Nginx Unicode support in the operating system Required PHP Extensions The following is a list of PHP extensions that must be installed on your server in order for Ushahidi to run properly: PCRE (http://php.net/pcre) must be compiled with --enable-utf8 and --enable-unicode-properties for UTF-8 functions to work properly. iconv (http://php.net/iconv) is required for UTF-8 transliteration. mcrypt (http://php.net/mcrypt) is required for encryption. SPL (http://php.net/spl) is required for several core libraries mbstring (http://php.net/mbstring) which speeds up Kohana's UTF-8 functions. cURL (http://php.net/curl) which is used to access remote sites. MySQL (http://php.net/mysql) is required for database access. GD (http://php.net/gd) is required for image manipulation. IMAP (http://php.net/imap) is required for handling e-mails. TIP: Need to figure out what extensions you already have installed on your server? Here are instructions to do just that http://jontangerine.com/silo/ php/phpinfo/ Optional Server Requirements To use Ushahidi's "Clean URLs" feature – meaning that your deployment's URLs will not include "index.php" – on an Apache Web Server, you will need the mod_rewrite module and the ability to use local .htaccess files. -
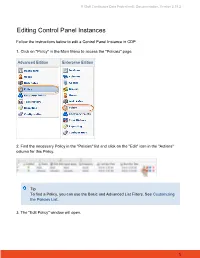
Editing Control Panel Instances
R1Soft Continuous Data Protection®, Documentation, Version 3.18.2 Editing Control Panel Instances Follow the instructions below to edit a Control Panel Instance in CDP. 1. Click on "Policy" in the Main Menu to access the "Policies" page. Advanced Edition Enterprise Edition 2. Find the necessary Policy in the "Policies" list and click on the "Edit" icon in the "Actions" column for this Policy. Tip To find a Policy, you can use the Basic and Advanced List Filters. See Customizing the Policies List. 3. The "Edit Policy" window will open. 1 R1Soft Continuous Data Protection®, Documentation, Version 3.18.2 4. Choose the "Control Panels" tab. 5. Then you will access the "Control Panel Instance" list on the "Control Panels" tab. 6. Find the necessary Instance in the "Control Panel Instance" list and click on the "Edit" icon in the "Actions" column for this Instance. 2 R1Soft Continuous Data Protection®, Documentation, Version 3.18.2 7. The "Edit Control Panel Instance" window will appear. Familiarize yourself with the introductory information and click "Next" to proceed with adding the Instance. 8. On the following "Instance Details" screen you can change options for your Control Panel Instance: Enabled - Use this checkbox to enable or disable the Control Panel Instance. If an instance is disabled, it will not be discovered during replication, and control panel users will not be able to access their data from any recovery points created while the instance is disabled. Name - Define a new name for the Control Panel Instance to identify it. A control panel instance's name must be unique to its policy, meaning no more than one instance associated with a policy can have a certain name. -

CDP 3.12.2 Release Notes
R1Soft Continuous Data Protection®, Documentation, Version 3.18.2 CDP 3.12.2 Release Notes CDP 3.12.2 (Stable) Release Notes This release includes 4 product editions: CDP Standard Edition, CDP Advanced Edition, CDP Enterprise Edition, and Data Center Console. IMPORTANT NOTE(S): Release 3.12.2 This update to 3.12.1 contains two improvements: MySQL backups on servers that have crashed tables will continue without failing. The crashed tables will be skipped and the backup process will continue. Additional data will be recorded in your disk safe which will aid in debugging if there is ever a problem with your disk safe. This update will also correct a potential issue if recovery points have been merged out of order. If you have already installed or upgraded to the 3.12.0 or 3.12.1 agent, there is no need to install the 3.12.2 agent as no changes have been made to this application. Release 3.12.1 Addresses Issues with 3.8.x Upgrade and MySQL Discovery Performance: There have been a small number of issues with customers upgrading from 3.8.x or who previously had one of these versions installed. This update will correct the problem for these customers experiencing issues upgrading or running CDP Server after upgrading to 3.12 and prevent this issue on future upgrades. This release also corrects a performance problem with discovery and backup of MySQL databases which was introduced in 3.12.0. This fix returns performance to speeds achieved in 3.10. Upgrading customers may experience a delay when starting the WebUI: Please be patient as important updates are in progress.