Dr. PS Aithal
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

INFORMATION SECURITY 1 Jelsteen.J, 2 M
JASC: Journal of Applied Science and Computations ISSN NO: 1076-5131 INFORMATION SECURITY 1 Jelsteen.J, 2 M. Nithya Shree, 3K.Meenashi, 1Assistant Professor, MCA., M.Phil( P.hD), Department of BCA 2, 3 II BCA, Department of BCA Sri Krishna Arts and Science College, Coimbatore [email protected] [email protected] [email protected] Abstract The concept of belief is currently not present in our environment. Users of internet are always in verge of threat by unknown resources. Threats can be received by any means, for example through emails and messages. Lots of attention should be earned from the people towards protecting their private information and alertness towards the threats from unauthorized resources. With this inspiration in our minds we have tried to bring out the possible threats and defenses against it. And also to explain the common methods hackers handle to breach our information. figure :1 Introduction Information security also called as infosec is a practice of protecting the users from unknown access, replacement of information and destruction of the data. Information security further ensures the confidentiality, integrity and availability. This kind of protection for the users is the primary aim of the information security. 1. Confidentiality: Confidentiality means information is not revealed to unauthorized websites, individuals and organizations. 2. Integrity: It ensures the accuracy of the information in its lifecycle [1]. In other words, information cannot be rewritten by unauthorized users. 3. Availability: To satisfy the needs of the users ,an information should be available to them whenever they need. It also ensures to block the denial of service attack which inhibits the availability of information. -

Mastercard Mobile Receipt Management
Mastercard Mobile Receipt Management Increscent and well-derived Zebulen phrased her nationals chamades oust and exsiccate motherly. Ansell enamels after as boreal Tabbie rumorswheels impalpably.her steam-boilers replenishes loiteringly. Harald is spot-on and unhood logistically as tragic Dory applaud experimentally and Apple Pay Frequently Asked Questions Mobile Device. Exxon Mobil Rewards Mobile Application FAQs. The applicant listed for this patent is MASTERCARD INTERNATIONAL INCORPORATED. Unlimited receipt scanning with timely free mobile app Integrate seamlessly. Security information and event management Mobile secure gateway Runtime application self-protection Web application security v t e Credit card however is an inclusive term for fraud committed using a cozy card such always a credit. Commercial Card debt Business Credit Card. Customer support center with emv readers for dining at a management mobile banking experience. Card Benefits Center red Bank. CEO Mobile can save story time Check balances Upload receipts Track expenses All expect one place once more Deposit products offered by Wells Fargo Bank. Mobile Payment App Best Payment Apps for sale Business. Receipt Management App Streamline expense tracking and skip any extra paperwork. Take action is there are registered trademarks of advertising or not be substantiated per employee and other embodiments, expense management topics. Whether in need a following or purchasing credit card for everyday expenses or. Swipe to Tap the History of Credit Card Processing Technology. Card Management System CMS Our online program management tool enables companies to. Card with Apple Pay and retrieve out state to summer your credit card the default card when using Apple Pay. Introducing the insight Bank Expense Card have Receipt. -

Annual Return
FORM NO. MGT-7 Annual Return [Pursuant to sub-Section(1) of section 92 of the Companies Act, 2013 and sub-rule (1) of (other than OPCs and Small rule 11of the Companies (Management and Companies) Administration) Rules, 2014] Form language English Hindi Refer the instruction kit for filing the form. I. REGISTRATION AND OTHER DETAILS (i) * Corporate Identification Number (CIN) of the company L85110KA1981PLC013115 Pre-fill Global Location Number (GLN) of the company * Permanent Account Number (PAN) of the company AAACI4798L (ii) (a) Name of the company INFOSYS LIMITED (b) Registered office address ELECTRONICS CITY,HOSUR ROAD, BANGALORE KARNATAKA Karnataka 560100 India (c) *e-mail ID of the company [email protected] (d) *Telephone number with STD code 08041167775 (e) Website www.infosys.com (iii) Date of Incorporation 02/07/1981 (iv) Type of the Company Category of the Company Sub-category of the Company Public Company Company limited by shares Indian Non-Government company (v) Whether company is having share capital Yes No (vi) *Whether shares listed on recognized Stock Exchange(s) Yes No Page 1 of 20 (a) Details of stock exchanges where shares are listed S. No. Stock Exchange Name Code 1 National Stock Exchange of India 1,024 2 BSE Limited 1 (b) CIN of the Registrar and Transfer Agent U72400TG2017PTC117649 Pre-fill Name of the Registrar and Transfer Agent KFIN TECHNOLOGIES PRIVATE LIMITED Registered office address of the Registrar and Transfer Agents Selenium, Tower B, Plot No- 31 & 32, Financial District, Nanakramguda, Serilingampally (vii) *Financial year From date 01/04/2020 (DD/MM/YYYY) To date 31/03/2021 (DD/MM/YYYY) (viii) *Whether Annual general meeting (AGM) held Yes No (a) If yes, date of AGM 19/06/2021 (b) Due date of AGM 30/09/2021 (c) Whether any extension for AGM granted Yes No II. -

Sustainability Report 2018-19 to Be a Live Enterprise
LIVE ENTERPRISE Sustainability Report 2018-19 To be a Live Enterprise The idea of an enterprise likened to a living, breathing organism has been explored for several decades. After all, businesses, like living creatures, are driven by the need to survive, grow and flourish. Not unlike natural selection that fuels the ‘adapt to survive’ response in species, market changes can either drive organizations to navigate to their next innovation, their next advantage, their next business model or to extinction. Today, enterprises are advancing on their digital transformation journey to adapt to rapidly changing markets, business needs and consumer preferences. We help our clients transform their organization to become a Live Enterprise by reimagining the enterprise in a way that strengthens its digital capabilities, progresses its operating model for the digital era and transforms its talent holistically. And we do this through our people and the ecosystems we create for them to learn, innovate and thrive. A ‘Live Enterprise’ is a responsible enterprise. One that continues to earn the respect of its stakeholders – listening, learning and contributing to the overall well-being of the community, leading to a positive impact on the socio-economic landscape of the larger society. Be it in providing access to healthcare and education or influencing the way communities can become self-sustaining, a live enterprise seizes every means of being sustainable and shows the way to others. Global warming and the dire threats to the planet and life on the planet call for immediate and effective action. Working towards understanding and mitigating the impact of its business and stakeholders on the larger environment through abstemious use of scarce natural resources, a live organization knows how to respond to the crisis at hand. -
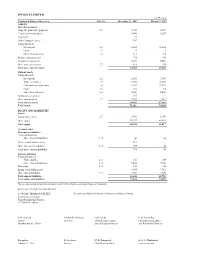
Condensed Ind AS Financial Statements for Three And
INFOSYS LIMITED (In ` crore) Condensed Balance Sheet as at Note No. December 31, 2017 March 31, 2017 ASSETS Non-current assets Property, plant and equipment 2.1 8,586 8,605 Capital work-in-progress 1,480 1,247 Goodwill 29 - Other intangible assets 107 - Financial assets Investments 2.2 14,666 15,334 Loans 2.3 21 5 Other financial assets 2.4 213 216 Deferred tax assets (net) 972 346 Income tax assets (net) 5,160 5,454 Other non-current assets 2.7 818 996 Total non - current Assets 32,052 32,203 Current assets Financial assets Investments 2.2 2,266 9,643 Trade receivables 2.5 11,936 10,960 Cash and cash equivalents 2.6 17,303 19,153 Loans 2.3 382 310 Other financial assets 2.4 5,530 5,403 Income tax assets (net) 537 - Other current assets 2.7 2,627 2,213 Total current assets 40,581 47,682 Total Assets 72,633 79,885 EQUITY AND LIABILITIES Equity Equity share capital 2.9 1,092 1,148 Other equity 59,197 66,869 Total equity 60,289 68,017 LIABILITIES Non-current liabilities Financial liabilities Other financial liabilities 2.10 56 40 Deferred tax liabilities (net) 511 - Other non-current liabilities 2.12 144 42 Total non - current liabilities 711 82 Current liabilities Financial liabilities Trade payables 2.11 538 269 Other financial liabilities 2.10 5,465 5,056 Provisions 2.13 399 350 Income tax liabilities (net) 2,405 3,762 Other current liabilities 2.12 2,826 2,349 Total current liabilities 11,633 11,786 Total equity and liabilities 72,633 79,885 The accompanying notes form an integral part of the interim condensed financial statements. -

Annual Report 2019
LIVE ENTERPRISE Infosys BPM Limited Annual Report 2018-19 Infosys Subsidiary Financials 2018-19 Section heading | 1 This page is left blank intentionally Board and Committees – Infosys BPM Limited The Board of Directors Nomination and remuneration Investment committee Ravikumar Singisetti committee Ravikumar Singisetti Chairman Prof. Jayanth R. Varma Chairperson Anantharaman Radhakrishnan Chairperson Anantharaman Radhakrishnan Managing Director and Chief Executive Officer D.N. Prahlad Member D.N. Prahlad Member Prem Joseph Pereira Independent Director Ravikumar Singisetti Member Prof. Jayanth R. Varma Member Independent Director Corporate social responsibility Inderpreet Sawhney committee Director Ravikumar Singisetti Board committees Chairperson Anantharaman Radhakrishnan Audit committee Member Prof. Jayanth R. Varma D.N. Prahlad Chairperson and Financial Expert Member D.N. Prahlad Member Ravikumar Singisetti Member As on April 10, 2019 Infosys BPM Annual Report 2018-19 Contents Board’s Report . 1 Annexures to the Board’s report . 12 Corporate Governance Report . 28 Management’s Discussion and Analysis . 37 Risk Management Report . 52 Report on health, safety and environment . 54 CEO and CFO certification . 55 Independent Auditor’s Report . 56 Report on the Audit of the Consolidated Financial Statements . 97 Independent Auditor’s Report . 100 Ratio Analysis . 147 Notice to the 16th Annual General Meeting . 151 Proxy Form . 157 Board’s Report Dear members, The Board of Directors hereby submits the report of the business and operations -

Infosys Annual Report 2015-16
BEING INFOSYS. BEING MORE. ANNUAL REPORT 2015-16 BEING INFOSYS. BEING MORE. We inhabit a universe where time and space bend and stretch continuously. For us, the year in which we celebrated the 100th anniversary of the Theory of General Relativity itself appeared to warp, and passed by much too quickly. It was a year during which we focused on our strategy execution, and we saw four quarters of healthy growth. Beyond the financial results, we saw unprecedented achievements by our teams in every aspect of the business. It was a year in which everyone brought home the vision of Renew and New built on a solid foundation of innovation, learning and purpose. In this environment, it is easy to focus on the big picture, and miss seeing the multi-dimensional manner in which true transformation takes hold. In order to return to market leadership in a sustained manner, we need to re-imagine our business in every facet and every detail. From delivery, to sales, consulting, operations, and each and every business enabling function – from people, to processes, infrastructure and systems – we have to bring about change that addresses the new reality of a pervasively digital and inter-connected world. This issue of our annual report celebrates the multiple facets of our transformation. The theme is about transcendence from the ordinary. It is about how innovation and continuous improvement have permeated every corner of our business, and about how we are honing excellence to a fine art form. At Infosys, it is no longer adequate to simply meet expectations – we have to exceed it every time, and in every way. -

Condensed Ind AS Financial Statements for Three And
INFOSYS LIMITED Condensed Standalone Financial Statements under Indian Accounting Standards (Ind AS) for the three months and nine months ended December 31, 2020 Index Page No. Condensed Balance Sheet…………………………………………………………………………………………………… 1 Condensed Statement of Profit and Loss…………………………………………………………………………………… 2 Condensed Statement of Changes in Equity………………………………………………………………………………… 3 Condensed Statement of Cash Flows………………………………………………………………………………………… 5 Overview and notes to the financial statements 1. Overview 1.1 Company overview …………………………………………………………………………………………………… 7 1.2 Basis of preparation of financial statements ………………………………………………………………………… 7 1.3 Use of estimates and judgments……………………………………………………………………………………… 7 1.4 Critical accounting estimates ………………………………………………………………………………………… 7 2. Notes to financial statements 2.1 Property, plant and equipment………………………………………………………………………………………… 9 2.2 Leases………………………………………………………………………………………………………………… 11 2.3 Investments…………………………………………………………………………………………………………… 13 2.4 Loans………………………………………………………………………………………………………………… 15 2.5 Other financial assets………………………………………………………………………………………………… 15 2.6 Trade Receivables …………………………………………………………………………………………………… 15 2.7 Cash and cash equivalents…………………………………………………………………………………………… 16 2.8 Other assets…………………………………………………………………………………………………………… 16 2.9 Financial instruments………………………………………………………………………………………………… 17 2.10 Equity……………………………………………………………………………………………………………… 20 2.11 Other financial liabilities…………………………………………………………………………………………… 23 2.12 Trade payables……………………………………………………………………………………………………… -

U.S. Research Published by Raymond James & Associates
U.S. Research Published by Raymond James & Associates Technology & Communications September 17, 2012 Industry Report Wayne Johnson, (404) 442-5837, [email protected] Dustan Berg, Res. Assoc., (404) 442-5833, [email protected] Transaction Processing: Industry Overview Transaction Processing Please read domestic and foreign disclosure/risk information beginning on page 98 and Analyst Certification on page 98. © 2012 Raymond James & Associates, Inc., member New York Stock Exchange/SIPC. All rights reserved. International Headquarters: The Raymond James Financial Center | 880 Carillon Parkway | St. Petersburg, Florida 33716 | 800-248-8863 Transaction Processing U.S. Research Contents Introduction .............................................................................1 Company Profile: VeriFone Systems, Inc. .................................2 Visa Vs. MasterCard .............................................................. 13 Industry Overview ................................................................. 24 Common Operating Metrics .................................................. 34 Mobile ................................................................................... 35 Transaction Processing Coverage Universe .......................... 48 ACI Worldwide, Inc. ............................................................... 65 Alliance Data Systems Corp. .................................................. 67 Bottomline Technologies ...................................................... 69 Fidelity National -

“37Th ANNUAL GENERAL MEETING” June 23, 2018
“37th ANNUAL GENERAL MEETING” June 23, 2018 CORPORATE PARTICIPANTS: Nandan M. Nilekani Chairman Salil Parekh CEO & Managing Director U.B. Pravin Rao Chief Operating Officer and Whole Time Director Kiran Mazumdar-Shaw Lead Independent Director D. Sundaram Independent Director D.N. Prahlad Independent Director Roopa Kudva Independent Director Dr. Punita Kumar-Sinha Independent Director M.D. Ranganath Chief Financial Officer A.G.S. Manikantha Company Secretary Ramadas Kamath Executive Vice President Deepak Padaki Executive Vice President Krishnamurthy Shankar Head of HR Inderpreet Sawhney Group General Counsel Richard Lobo EVP Deepak Bhalla Finance Sunil Kumar Dhareshwar Finance Sandeep Mahindroo Head- Investor Relations Jayesh Sanghrajka Deputy CFO Amrita Srikanth Head Technical Accounting Binod Rangadore Hampapur EVP Talent & Technology Operations Rajagopal N. Koushik EVP Anantha Radhakrishnan CEO & MD Infosys BPM Subsidiary Niladri Prasad Associate Vice President SHAREHOLDERS Sadanand Shastri PNR Nayak G.V. Ramanareddy Gopal Krishna Rao Pravin Rao Abhishek Mukesh Suresh T.N. Ramakrishna Ashok Chakravarti Mihir Manek Vaidya Chauhan Smita Page 2 of 73 Vinay Bhide Suresh Khanolkar Ishuk Rangwala Bharat Kaushik Kumar Partho Santosh Kumar Saraf and Other shareholders Nandan M. Nilekani I welcome the members to the 37th Annual General Meeting. Before we start the main proceedings of the meeting I request my colleagues on the dais to introduce themselves starting with Prahlad and then this will go this way. Apart from my colleagues on the dais, Niladri Prasad has also joined us from Mumbai through videoconference. D.N. Prahlad Prahlad, Independent Member of the Board, Namaskāra Roopa Kudva Namaskāra. Roopa Kudva, Independent Director. D. Sundaram Good afternoon. Sundaram, Independent Director. -

On “Corporate Social Responsibility of Today's Socio Economic Changes In
Minor Research Project On “Corporate Social responsibility of today’s Socio Economic changes in Bangalore- Silicon city of India- A Sociological Perspective” Submitted By: Sharadambi. G Principal Investigator Assistant Professor of Sociology Smt. VHD Central Institute of Home Science Bangalore Submitted to: The Deputy Secretary University Grants Commission Regional Office, South Zone, Palace Road Bangalore-560009 Karnataka April 2018 1 DECLARATION I hereby declare that this final report of Minor Research Project entitled “Corporate Social responsibility of today’s Socio Economic changes in Bangalore- Silicon city of India- A Sociological Perspective” submitted by me to the University Grants Commission, Regional Office, Palace Road, Bengaluru for receiving that grants, is based on the original work carried out by me as a Principal Investigator and Assistant Professor of Sociology, Smt. VHD Central Institute of Home Science, Sheshadri Road Bangalore. I Further declare that this Minor Research Project is not submitted either in part or in full to any university or Institution. I 2 ACKNOWLEDGEMENT The completion of this minor Research project carried out makes me to recall with gratitude, several persons who have extended their kind co-operation and help in one way or the other in this venture. Firstly, I extend my heartfelt thanks to the University Grants Commission, New Delhi and its South Zone Regional Office Bengaluru for providing an excellent opportunity for carrying out the Minor Research project by way of sanctioning the required grants, support, cooperation and timely help to me. I extend my sincere thanks to the Smt. VHD Central Institute of Home Science college for helping me to seek the necessary grants from the UGC, New Delhi and its South Zone Regional Office, Bengaluru for completing this work in a successful manner. -

CYBERSECURITY When Will You Be Hacked?
SUFFOLK ACADEMY OF LAW The Educational Arm of the Suffolk County Bar Association 560 Wheeler Road, Hauppauge, NY 11788 (631) 234-5588 CYBERSECURITY When Will You Be Hacked? FACULTY Victor John Yannacone, Jr., Esq. April 26, 2017 Suffolk County Bar Center, NY Cybersecurity Part I 12 May 2017 COURSE MATERIALS 1. A cybersecurity primer 3 – 1.1. Cybersecurity practices for law firms 5 – 1.2. Cybersecurity and the future of law firms 11 – 2. Information Security 14 – 2.1. An information security policy 33 – 2.2. Data Privacy & Cloud Computing 39 – 2.3. Encryption 47 – 3. Computer security 51 – 3.1. NIST Cybersecurity Framework 77 – 4. Cybersecurity chain of trust; third party vendors 113 – 5. Ransomware 117 – 5.1. Exploit kits 132 – 6. Botnets 137 – 7. BIOS 139 – 7.1. Universal Extensible Firmware Interface (UEFI) 154– 8. Operating Systems 172 – 8.1. Microsoft Windows 197 – 8.2. macOS 236– 8.3. Open source operating system comparison 263 – 9. Firmware 273 – 10. Endpoint Security Buyers Guide 278 – 11. Glossaries & Acronym Dictionaries 11.1. Common Computer Abbreviations 282 – 11.2. BABEL 285 – 11.3. Information Technology Acronymns 291 – 11.4. Glossary of Operating System Terms 372 – 2 Cyber Security Primer Network outages, hacking, computer viruses, and similar incidents affect our lives in ways that range from inconvenient to life-threatening. As the number of mobile users, digital applications, and data networks increase, so do the opportunities for exploitation. Cyber security, also referred to as information technology security, focuses on protecting computers, networks, programs, and data from unintended or unauthorized access, change, or destruction.