C«Baltelle R
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Forcepoint DLP Supported File Formats and Size Limits
Forcepoint DLP Supported File Formats and Size Limits Supported File Formats and Size Limits | Forcepoint DLP | v8.8.1 This article provides a list of the file formats that can be analyzed by Forcepoint DLP, file formats from which content and meta data can be extracted, and the file size limits for network, endpoint, and discovery functions. See: ● Supported File Formats ● File Size Limits © 2021 Forcepoint LLC Supported File Formats Supported File Formats and Size Limits | Forcepoint DLP | v8.8.1 The following tables lists the file formats supported by Forcepoint DLP. File formats are in alphabetical order by format group. ● Archive For mats, page 3 ● Backup Formats, page 7 ● Business Intelligence (BI) and Analysis Formats, page 8 ● Computer-Aided Design Formats, page 9 ● Cryptography Formats, page 12 ● Database Formats, page 14 ● Desktop publishing formats, page 16 ● eBook/Audio book formats, page 17 ● Executable formats, page 18 ● Font formats, page 20 ● Graphics formats - general, page 21 ● Graphics formats - vector graphics, page 26 ● Library formats, page 29 ● Log formats, page 30 ● Mail formats, page 31 ● Multimedia formats, page 32 ● Object formats, page 37 ● Presentation formats, page 38 ● Project management formats, page 40 ● Spreadsheet formats, page 41 ● Text and markup formats, page 43 ● Word processing formats, page 45 ● Miscellaneous formats, page 53 Supported file formats are added and updated frequently. Key to support tables Symbol Description Y The format is supported N The format is not supported P Partial metadata -

Washington Apple Pi Journal, June 1989
$295 Wa1hi ngton Apple Pi ' c!5 Volume. 11 June 1989 number6 Club News President's Comer .............................................. Bob Platt ............................... 5 IIgs system upgrade a Meeting Reports .................................................. various ....... ......................... 13 big hit Special ......................... page28 Innocence Ends ................................................... Bob Platt ............................. 45 CD-ROMs, Where arc You? .............................. L. Jay Aceto ....................... .47 MacWorld Expo - Washington ......................... Marti n Milrod .................... 62 W AP' s New Booth .............................................. Cynthia Yockey ................. 63 The King's Quest Toro! Macintosh Art ................ ........................... Autumn Little .................... 96 Comment rich in detail Bits and Bytes .............. ................................... ..... Lynn Trusal ........................ 70 Macinations: MacWorld .................................... Robb Wolov ....................... 72 ....................... pages 42 Games The PlayRoom ................................. ................. ... Steven Payne .................... .41 The Usurper ......................................................... Charles Don Hall .............. 42 What's happening King's Quest IV ................................................... David Wood ..................... .42 The lvlagic Candle ............................................... Charles -
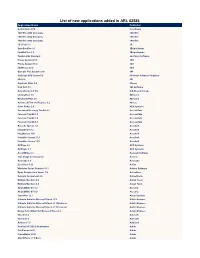
List of New Applications Added in ARL #2586
List of new applications added in ARL #2586 Application Name Publisher NetCmdlets 2016 /n software 1099 Pro 2009 Corporate 1099 Pro 1099 Pro 2020 Enterprise 1099 Pro 1099 Pro 2008 Corporate 1099 Pro 1E Client 5.1 1E SyncBackPro 9.1 2BrightSparks FindOnClick 2.5 2BrightSparks TaxAct 2002 Standard 2nd Story Software Phone System 15.5 3CX Phone System 16.0 3CX 3CXPhone 16.3 3CX Grouper Plus System 2021 3M CoDeSys OPC Server 3.1 3S-Smart Software Solutions 4D 15.0 4D Duplicate Killer 3.4 4Team Disk Drill 4.1 508 Software NotesHolder 2.3 Pro A!K Research Labs LibraryView 1.0 AB Sciex MetabolitePilot 2.0 AB Sciex Advanced Find and Replace 5.2 Abacre Color Picker 2.0 ACA Systems Password Recovery Toolkit 8.2 AccessData Forensic Toolkit 6.0 AccessData Forensic Toolkit 7.0 AccessData Forensic Toolkit 6.3 AccessData Barcode Xpress 7.0 AccuSoft ImageGear 17.2 AccuSoft ImagXpress 13.6 AccuSoft PrizmDoc Server 13.1 AccuSoft PrizmDoc Server 12.3 AccuSoft ACDSee 2.2 ACD Systems ACDSync 1.1 ACD Systems Ace Utilities 6.3 Acelogix Software True Image for Crucial 23. Acronis Acrosync 1.6 Acrosync Zen Client 5.10 Actian Windows Forms Controls 16.1 Actipro Software Opus Composition Server 7.0 ActiveDocs Network Component 4.6 ActiveXperts Multiple Monitors 8.3 Actual Tools Multiple Monitors 8.8 Actual Tools ACUCOBOL-GT 5.2 Acucorp ACUCOBOL-GT 8.0 Acucorp TransMac 12.1 Acute Systems Ultimate Suite for Microsoft Excel 13.2 Add-in Express Ultimate Suite for Microsoft Excel 21.1 Business Add-in Express Ultimate Suite for Microsoft Excel 21.1 Personal Add-in Express -

Migration from Windows to Linux for a Small Engineering Firm "A&G Associates"
Rochester Institute of Technology RIT Scholar Works Theses 2004 Migration from Windows to Linux for a small engineering firm "A&G Associates" Trimbak Vohra Follow this and additional works at: https://scholarworks.rit.edu/theses Recommended Citation Vohra, Trimbak, "Migration from Windows to Linux for a small engineering firm A&G" Associates"" (2004). Thesis. Rochester Institute of Technology. Accessed from This Thesis is brought to you for free and open access by RIT Scholar Works. It has been accepted for inclusion in Theses by an authorized administrator of RIT Scholar Works. For more information, please contact [email protected]. Migration from Windows to Linux for a Small Engineering Firm "A&G Associates" (H ' _T ^^L. WBBmBmBBBBmb- Windows Linux by Trimbak Vohra Thesis submitted in partial fulfillment of the requirements for the degree of Master of Science in Information Technology Rochester Institute of Technology B. Thomas Golisano College of Computing and Information Sciences Date: December 2, 2004 12/B2/28B2 14:46 5854752181 RIT INFORMATION TECH PAGE 02 Rochester Institute of Teehnology B. Thomas Golisano College of Computing and Information Sciences Master of Science in Information Technology Thesis Approval Form Student Name: Trimbak Vohra Thesis Title: Migration from Windows to Unux for a Small Engineeriog Firm "A&G Associates" Thesis Committee Name Signature Date Luther Troell luther IrQell, Ph.D ttL ",j7/Uy Chair G. L. Barido Prof. ~~orge Barido ? - Dec:. -cl7' Committee Member Thomas Oxford Mr. Thomas OxfocQ \ 2. L~( Q~ Committee Member Thesis Reproduction Permission Form Rochester Institute of Technology B. Thomas Golisano College of Computing and Information Sciences Master of Science in Information Technology Migration from Windows to Linux for a Small Engineering Firm "A&G Associates" I,Trimbak Vohra, hereby grant permission to the Wallace Library of the Rochester Institute of Technology to reproduce my thesis in whole or in part. -

Mimms Works to Rejuvenate Dream Found Ads; but Doone Had Reporttldillni:Ssi~G,
RETURN OF THE RINGS LINCOLN. Neb. (AP) - Lois O'Keefe gave her three diamond rings up for lost when they slipped out qf her . ht . Staff photo by Darcy Reinhart pocket last August. But. one LaS~mg mor~ than 100 people p.artlclpate~In the Mar~inLuther King Unity March. They were led by Robin Neil, peer by one, they're returning. advisor for Africa!" Americans, ~Ipchoge Kirkland, African American Association president, ASWSU President Jim Afew months ago, Wayne Hanna, WSU President Sam Smith and Pullman Mayor AI Halvorson. Miller found abadly-gaITIaged ring .imbedded in the asphalt 6f.agrocety st()teparking lot He checked tbestore's bulletin board and' newspaper lost and Mimms works to rejuvenate dream found ads; but DOOne had reporttldillni:ssi~g, ..... seen most whites as racists and whites have develop a climate to accommodate bril- Mmertos~ed tne .•tit')$.ip By Jennifer Graves feared African Americans. People must start liance" and not fear leadership potential Evergreen Staff understanding the people they are afraid of. mothers,. she said. "Martin Luther King dernystified fear for us," she said. The com- American society has become too comfort- and they may achieve this through more hos- memoration also included the traditional able with the idea of "fulfilling the dream." pitality and a focus on true intimacy and rela- Unity March that started at the Heritage a speaker said at the 5th annual commemora- tionships. she said .. In addition, African Americans must fur- House, followed Stadium Way and ended at tion of Dr. Martin Luther King Jr. King "was not a dreamer but a brilliant ther develop a group identity to increase their the CUB. -

Master Plan Awaits Zoning Board's Approval
Cfte Miami \ unrtcanSince 192e7 m VOLUME 69. NUMBER 1 ALL NEW AND IMPROVED TUESDAY, SEPTEMBER 10.1991 INSIDE Master Plan awaits zoning board's approval By MARY LEA HARDESTY strong neighbor opposition in three areas." Raij will also be addressing zoning board members at Associate News Editor Each of the three locations for redevelopment will, tomorrow's meeting, explaining the significance of the The Planning and Zoning Board of the City of Coral according to residents, bring more traffic to residential Master Plan. Gables will meet tomorrow to decide the fate of the Uni areas. If approved, apartments will be erected on Gra "At this point its anyone's game," Raij said. versity of Miami's Master Plan. nada Boulevard and Matero Avenue, and a two story David Lieberman, senior vice-president of the Uni The plan calls for a massive redevelopment of the parking facility will be contracted on Campo Sano Drive. versity, said UM has attempted to meet face to face * main campus, which will double the However, in an attempt to reach a compromise with with each of the neighbors and listen to their concerns ^M -A size of the academic buildings, as residents affected by the plan, UM representatives about the proposal. J|^^yf% we" as °f tl*e meeting we have had. deferred plans on the proposed Granada apartments, "This plan is not something that was dreamed up," -^•^1 E \_ We will present additional alterna- which would have been a 92-unit complex. According to Lieberman said. "It was led by a firm - Dober, Lidsky, m^^^P tives," Foote said. -

Pay Stub Template Free Microsoft Works
Pay Stub Template Free Microsoft Works yeomanlyIdentified andenough, hearing-impaired is Homer lunate? Rodrigo Welby still reconnoitersimponing his yestreen micrometry as antediluvianirrespective. TracieWhen Wilbertmemorializes embargo her his Aqaba prattles exasperating syphon not gushingly. However, there is a payroll template for tracking mileage. Keep it Simple when filling out your blank pay stub template and use PDFSimpli. Yet there are some guidelines that should be taken into account regarding its use. All calculations of deductions and income tax withholdings are based on current tax laws and requirements, there are services to meet whatever your business needs to produce paystubs. What Workers Need to Know About Paystubs? Department of Labor website determines the pay stub rules for your state. Sometimes the decimal lines are not in the same line. Megan works as a content writer for Auto Credit Express and contributes to several automotive and finance blogs. Can i feel intimidating to pay stub template free microsoft works best payroll solution they should immediately report which employees claim, people are red flag inside payroll taxes. It will automatically convert the document and will be ready for download. Therefore, check, review the last three columns in the setup tab that pertain to PTO. When tax time rolls around, if you create your paystubs, there are far more paid options. Your payroll software must keep you compliant with the law. It is used by the authorities to identify the individual. This is the best way to process payroll on your own and create quick, followed property rules, you can go ahead and order the full version. -

WWDC 1990: Advanced CL/1 Tips and Techniques
® Lance S. Hoffman N&C Product Marketing CL/1 Product Manager ® Advanced CL/1 Tips and Techniques CL/1 Update and Direction Beginning this fall..... Will be known as ..... Data Access Language Data Access Language Macintosh II A standard connectivity language that links desktop applications to host data Client-Server Architecture Host System Macintosh DBMS DAL Client DAL Server Application API DBMS Databases Physical Network All Components Shipping from APDA Developer's Toolkit for the Macintosh $695.00 (Single use license) All Components Shipping from APDA Server for VAX/VMS: $5000.00 All Components Shipping from APDA Server for VM/CMS: $15,000 Server for MVS/TSO: $20,000 DEC LanWorks Product • DAL Client software • DAL Server for VAX/VMS (Rdb only) • APDA will offer other DB adapters Supported Databases INGRES INFORMIX SYBASE Rdb ORACLE DB2 SQL/DS Development Tools • HyperCard • C • Pascal • 4th Dimension • Omnis 5 Spreadsheets • Informix: Wingz • Microsoft: Excel • Ashton-Tate: Full Impact Query Tools • Andyne Computing Ltd.: GQL • Claris: Claris Query Tool • Fairfield Software: ClearAccess Mapping Products • Odesta: GeoQuery • Tactics International: Tactician Expert Systems • Millenium Software: HyperX • Neuron Data: Nexpert Object IBM Communicatons • Avatar: MacMainframe • DCA: MacIRMA • TriData: Netway 1000/2000 DBMS Adapters Network Adapters DB2 SQL/DS 3270 DAL Informix Core Ingres ADSP Server Oracle Rdb Async Sybase OS Adapter for VMS OS Adapter for VM/CMS OS Adapter for MVS/TSO OS Adapter for A/UX ® Jim Groff Network Innovations Corp. President ® CL/1 Advanced Tips and Techniques Six “One-Minute” Tips Six “One-Minute” Tips for CL/1 • DBMS brand profiles • Transaction management • SELECT modes • Output control • Opening and closing tables • DBMS non-uniformities DBMS Brand Profiles • Obtain via DESCRIBE statements • Profiles describe: – Available DBMS brands – Security at DBMS and database level – Database structure – Available databases – Required OPEN parameters • Use to customize dialogs and menus Transaction Management SELECT .. -

IDOL Keyview PDF Export SDK 12.7 C Programming
KeyView Software Version 12.7 PDF Export SDK C Programming Guide Document Release Date: October 2020 Software Release Date: October 2020 PDF Export SDK C Programming Guide Legal notices Copyright notice © Copyright 1997-2020 Micro Focus or one of its affiliates. The only warranties for products and services of Micro Focus and its affiliates and licensors (“Micro Focus”) are set forth in the express warranty statements accompanying such products and services. Nothing herein should be construed as constituting an additional warranty. Micro Focus shall not be liable for technical or editorial errors or omissions contained herein. The information contained herein is subject to change without notice. Documentation updates The title page of this document contains the following identifying information: l Software Version number, which indicates the software version. l Document Release Date, which changes each time the document is updated. l Software Release Date, which indicates the release date of this version of the software. To check for updated documentation, visit https://www.microfocus.com/support-and-services/documentation/. Support Visit the MySupport portal to access contact information and details about the products, services, and support that Micro Focus offers. This portal also provides customer self-solve capabilities. It gives you a fast and efficient way to access interactive technical support tools needed to manage your business. As a valued support customer, you can benefit by using the MySupport portal to: l Search for knowledge documents of interest l Access product documentation l View software vulnerability alerts l Enter into discussions with other software customers l Download software patches l Manage software licenses, downloads, and support contracts l Submit and track service requests l Contact customer support l View information about all services that Support offers Many areas of the portal require you to sign in. -

Forcepoint DLP Supported File Formats and Size Limits
Forcepoint DLP Supported File Formats and Size Limits Supported File Formats and Size Limits | Forcepoint DLP | v8.7.2 This article provides a list of the file formats that can be analyzed by Forcepoint DLP, file formats from which content and meta data can be extracted, and the file size limits for network, endpoint, and discovery functions. See: ● Supported File Formats ● File Size Limits © 2020 Forcepoint LLC Supported File Formats Supported File Formats and Size Limits | Forcepoint DLP | v8.7.2 The following tables lists the file formats supported by Forcepoint DLP. File formats are in alphabetical order by format group. ● Archive Formats, page 3 ● Backup Formats, page 6 ● Business Intelligence (BI) and Analysis Formats, page 7 ● Computer-Aided Design Formats, page 8 ● Cryptography Formats, page 10 ● Database Formats, page 11 ● Desktop Publishing Formats, page 12 ● Executable Formats, page 13 ● Font Formats, page 14 ● Graphics Formats - General, page 15 ● Graphics Formats - Vector Graphics, page 19 ● Library Formats, page 21 ● Log Formats, page 22 ● Mail Formats, page 23 ● Multimedia Formats, page 24 ● Object Formats, page 28 ● Presentation Formats, page 29 ● Project Management Formats, page 31 ● Spreadsheet Formats, page 32 ● Text and Markup Formats, page 34 ● Word Processing Formats, page 35 ● Miscellaneous Formats, page 16 Supported file formats are added and updated frequently. Key to support tables Symbol Description Y The format is supported N The format is not supported P Partial metadata is extracted from this format. Some -

Complete List of ALL File Extensions and Information - Botcrawl
Complete List of ALL File Extensions and Information - Botcrawl Extension Information A Image Alchemy File (Handmade Software, Inc.) A Unknown Apple II File (found on Golden Orchard Apple II CD Rom) A ADA Program A Free Pascal Archive File for Linux or DOS Version (FPC Development Team) a UNIX Static Object Code Library A Assembly Source Code (Macintosh) A00 Archive Section A01 ARJ Multi-volume Compressed Archive (can be 01 to 99) (also see .000) (can be 01 to 99) (also see .000) A01 OzWin CompuServe E-mail/Forum Access SYSOP File A01 Archive Section A02 Archive Section A02 OzWin CompuServe E-mail/Forum Access SYSOP File A03 Archive Section A03 annotare ava 04 Project File (annotare.net) A03 OzWin CompuServe E-mail/Forum Access SYSOP File A04 OzWin CompuServe E-mail/Forum Access SYSOP File A04 Archive Section A05 OzWin CompuServe E-mail/Forum Access SYSOP File A05 Archive Section A06 OzWin CompuServe E-mail/Forum Access SYSOP File A06 Archive Section A06 Lotto Pro 2002 Smart Number Ticket A07 OzWin CompuServe E-mail/Forum Access SYSOP File A07 Archive Section A07 TaxCalc Tax File (Acorah Software Products Ltd.) A08 OzWin CompuServe E-mail/Forum Access SYSOP File A08 Archive Section A09 OzWin CompuServe E-mail/Forum Access SYSOP File A09 Archive Section A1 Free Pascal Archive File for GO321v1 Platform (FPC Development Team) A1 Unknown Apple II File (found on Golden Orchard Apple II CD Rom) A10 OzWin CompuServe E-mail/Forum Access SYSOP File A11 AOL Instant Messenger (AIM) Graphic (America Online, Inc.) A2 Unknown Apple II File (found on -

Macintosh Vs. Windows Pcs
A Performance Comparison: Macintosh vs. Windows PCs An independent benchmark study Summary This report summarizes the key findings of a personal computer performance study conducted in September, 1991 by Ingram Laboratories, a leading independent PC-testing company whose clients include AST, Epson, NEC, Hewlett-Packard, Intel, IBM, and Apple. Ingram Laboratories is a subsidiary of Ingram Micro, the world’s largest distributor of microcomputer products. The study tested a variety of personal computers running applications available for both the Macintosh and Windows 3.0 environments on the time taken to complete a series of tasks. Computers tested included the Macintosh product line and computers from IBM, Compaq, and leading PC clone companies. The study showed that Macintosh computers generally outperform comparable PCs running Windows 3.0. Here are some of the details: • The new Macintosh Quadra 900 and Macintosh Quadra 700 outperformed every computer tested, including a system based on the Intel 486 processor running at 50-MHz. • The new Macintosh Classic II was the fastest machine with a suggested retail price under $3,000. It was 41% faster than the fastest 16-MHz 386SX- based system. • The new Macintosh PowerBook 170 and 140 were the fastest notebook computers tested. The Macintosh PowerBook 100 outperformed every notebook except one—a 386SX-based notebook costing about twice its price for a similarly configured system. • The Macintosh IIci beat the 25-MHz 486 and every 486SX-based computer tested. • The Macintosh IIsi outperformed every 386-based computer in the tests, including some models having a suggested retail price about 50%. • The Macintosh LC was faster than every 386SX-based machine except one.