Parameterized Algorithms for Network Design
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
![Arxiv:2006.06067V2 [Math.CO] 4 Jul 2021](https://docslib.b-cdn.net/cover/6166/arxiv-2006-06067v2-math-co-4-jul-2021-416166.webp)
Arxiv:2006.06067V2 [Math.CO] 4 Jul 2021
Treewidth versus clique number. I. Graph classes with a forbidden structure∗† Cl´ement Dallard1 Martin Milaniˇc1 Kenny Storgelˇ 2 1 FAMNIT and IAM, University of Primorska, Koper, Slovenia 2 Faculty of Information Studies, Novo mesto, Slovenia [email protected] [email protected] [email protected] Treewidth is an important graph invariant, relevant for both structural and algo- rithmic reasons. A necessary condition for a graph class to have bounded treewidth is the absence of large cliques. We study graph classes closed under taking induced subgraphs in which this condition is also sufficient, which we call (tw,ω)-bounded. Such graph classes are known to have useful algorithmic applications related to variants of the clique and k-coloring problems. We consider six well-known graph containment relations: the minor, topological minor, subgraph, induced minor, in- duced topological minor, and induced subgraph relations. For each of them, we give a complete characterization of the graphs H for which the class of graphs excluding H is (tw,ω)-bounded. Our results yield an infinite family of χ-bounded induced-minor-closed graph classes and imply that the class of 1-perfectly orientable graphs is (tw,ω)-bounded, leading to linear-time algorithms for k-coloring 1-perfectly orientable graphs for every fixed k. This answers a question of Breˇsar, Hartinger, Kos, and Milaniˇc from 2018, and one of Beisegel, Chudnovsky, Gurvich, Milaniˇc, and Servatius from 2019, respectively. We also reveal some further algorithmic implications of (tw,ω)- boundedness related to list k-coloring and clique problems. In addition, we propose a question about the complexity of the Maximum Weight Independent Set prob- lem in (tw,ω)-bounded graph classes and prove that the problem is polynomial-time solvable in every class of graphs excluding a fixed star as an induced minor. -

Vertex Cover Reconfiguration and Beyond
algorithms Article Vertex Cover Reconfiguration and Beyond † Amer E. Mouawad 1,*, Naomi Nishimura 2, Venkatesh Raman 3 and Sebastian Siebertz 4,‡ 1 Department of Informatics, University of Bergen, PB 7803, N-5020 Bergen, Norway 2 School of Computer Science, University of Waterloo, Waterloo, ON N2L 3G1, Canada; [email protected] 3 Institute of Mathematical Sciences, Chennai 600113, India; [email protected] 4 Institute of Informatics, University of Warsaw, 02-097 Warsaw, Poland; [email protected] * Correspondence: [email protected] † This paper is an extended version of our paper published in the 25th International Symposium on Algorithms and Computation (ISAAC 2014). ‡ The work of Sebastian Siebertz is supported by the National Science Centre of Poland via POLONEZ Grant Agreement UMO-2015/19/P/ST6/03998, which has received funding from the European Union’s Horizon 2020 research and innovation programme (Marie Skłodowska-Curie Grant Agreement No. 665778). Received: 11 October 2017; Accepted: 7 Febuary 2018; Published: 9 Febuary 2018 Abstract: In the Vertex Cover Reconfiguration (VCR) problem, given a graph G, positive integers k and ` and two vertex covers S and T of G of size at most k, we determine whether S can be transformed into T by a sequence of at most ` vertex additions or removals such that every operation results in a vertex cover of size at most k. Motivated by results establishing the W[1]-hardness of VCR when parameterized by `, we delineate the complexity of the problem restricted to various graph classes. In particular, we show that VCR remains W[1]-hard on bipartite graphs, is NP-hard, but fixed-parameter tractable on (regular) graphs of bounded degree and more generally on nowhere dense graphs and is solvable in polynomial time on trees and (with some additional restrictions) on cactus graphs. -

Masters Thesis: an Approach to the Automatic Synthesis of Controllers with Mixed Qualitative/Quantitative Specifications
An approach to the automatic synthesis of controllers with mixed qualitative/quantitative specifications. Athanasios Tasoglou Master of Science Thesis Delft Center for Systems and Control An approach to the automatic synthesis of controllers with mixed qualitative/quantitative specifications. Master of Science Thesis For the degree of Master of Science in Embedded Systems at Delft University of Technology Athanasios Tasoglou October 11, 2013 Faculty of Electrical Engineering, Mathematics and Computer Science (EWI) · Delft University of Technology *Cover by Orestis Gartaganis Copyright c Delft Center for Systems and Control (DCSC) All rights reserved. Abstract The world of systems and control guides more of our lives than most of us realize. Most of the products we rely on today are actually systems comprised of mechanical, electrical or electronic components. Engineering these complex systems is a challenge, as their ever growing complexity has made the analysis and the design of such systems an ambitious task. This urged the need to explore new methods to mitigate the complexity and to create sim- plified models. The answer to these new challenges? Abstractions. An abstraction of the the continuous dynamics is a symbolic model, where each “symbol” corresponds to an “aggregate” of states in the continuous model. Symbolic models enable the correct-by-design synthesis of controllers and the synthesis of controllers for classes of specifications that traditionally have not been considered in the context of continuous control systems. These include qualitative specifications formalized using temporal logics, such as Linear Temporal Logic (LTL). Be- sides addressing qualitative specifications, we are also interested in synthesizing controllers with quantitative specifications, in order to solve optimal control problems. -

Efficient Graph Reachability Query Answering Using Tree Decomposition
Efficient Graph Reachability Query Answering using Tree Decomposition Fang Wei Computer Science Department, University of Freiburg, Germany Abstract. Efficient reachability query answering in large directed graphs has been intensively investigated because of its fundamental importance in many application fields such as XML data processing, ontology rea- soning and bioinformatics. In this paper, we present a novel indexing method based on the concept of tree decomposition. We show analytically that this intuitive approach is both time and space efficient. We demonstrate empirically the efficiency and the effectiveness of our method. 1 Introduction Querying and manipulating large scale graph-like data has attracted much atten- tion in the database community, due to the wide application areas of graph data, such as GIS, XML databases, bioinformatics, social network, and ontologies. The problem of reachability test in a directed graph is among the fundamental operations on the graph data. Given a digraph G = (V; E) and u; v 2 V , a reachability query, denoted as u ! v, ask: is there a path from u to v? One of the fundamental queries on biological networks is for instance, to find all genes whose expressions are directly or indirectly influenced by a given molecule [15]. Given the graph representation of the genes and regulation events, the question can also be reduced to the reachability query in a directed graph. Recently, tree decomposition methodologies have been successfully applied to solving shortest path query answering over undirected graphs [17]. Briefly stated, the vertices in a graph G are decomposed into a tree in which each node contains a set of vertices in G. -

A Tight Extremal Bound on the Lovász Cactus Number in Planar Graphs
A Tight Extremal Bound on the Lovász Cactus Number in Planar Graphs Parinya Chalermsook Aalto University, Espoo, Finland parinya.chalermsook@aalto.fi Andreas Schmid Max Planck Institute for Informatics, Saarbrücken, Germany [email protected] Sumedha Uniyal Aalto University, Espoo, Finland sumedha.uniyal@aalto.fi Abstract A cactus graph is a graph in which any two cycles are edge-disjoint. We present a constructive proof of the fact that any plane graph G contains a cactus subgraph C where C contains at least 1 a 6 fraction of the triangular faces of G. We also show that this ratio cannot be improved by showing a tight lower bound. Together with an algorithm for linear matroid parity, our bound implies two approximation algorithms for computing “dense planar structures” inside any graph: (i) 1 A 6 approximation algorithm for, given any graph G, finding a planar subgraph with a maximum 1 number of triangular faces; this improves upon the previous 11 -approximation; (ii) An alternate (and 4 arguably more illustrative) proof of the 9 approximation algorithm for finding a planar subgraph with a maximum number of edges. Our bound is obtained by analyzing a natural local search strategy and heavily exploiting the exchange arguments. Therefore, this suggests the power of local search in handling problems of this kind. 2012 ACM Subject Classification Mathematics of computing → Graph theory Keywords and phrases Graph Drawing, Matroid Matching, Maximum Planar Subgraph, Local Search Algorithms Digital Object Identifier 10.4230/LIPIcs.STACS.2019.19 Related Version Full Version: https://arxiv.org/abs/1804.03485. Funding Parinya Chalermsook: Part of this work was done while PC and AS were visiting the Simons Institute for the Theory of Computing. -

Depth-First Search & Directed Graphs
Depth-first Search and Directed Graphs Story So Far • Breadth-first search • Using breadth-first search for connectivity • Using bread-first search for testing bipartiteness BFS (G, s): Put s in the queue Q While Q is not empty Extract v from Q If v is unmarked Mark v For each edge (v, w): Put w into the queue Q The BFS Tree • Can remember parent nodes (the node at level i that lead us to a given node at level i + 1) BFS-Tree(G, s): Put (∅, s) in the queue Q While Q is not empty Extract (p, v) from Q If v is unmarked Mark v parent(v) = p For each edge (v, w): Put (v, w) into the queue Q Spanning Trees • Definition. A spanning tree of an undirected graph G is a connected acyclic subgraph of G that contains every node of G . • The tree produced by the BFS algorithm (with (( u, parent(u)) as edges) is a spanning tree of the component containing s . • The BFS spanning tree gives the shortest path from s to every other vertex in its component (we will revisit shortest path in a couple of lectures) • BFS trees in general are short and bushy Spanning Trees • Definition. A spanning tree of an undirected graph G is a connected acyclic subgraph of G that contains every node of G . • The tree produced by the BFS algorithm (with (( u, parent(u)) as edges) is a spanning tree of the component containing s . • The BFS spanning tree gives the shortest path from s to every other vertex in its component (we will revisit shortest path in a couple of lectures) • BFS trees in general are short and bushy Generalizing BFS: Whatever-First If we change how we store -

Maximum Bounded Rooted-Tree Problem: Algorithms and Polyhedra
Maximum Bounded Rooted-Tree Problem : Algorithms and Polyhedra Jinhua Zhao To cite this version: Jinhua Zhao. Maximum Bounded Rooted-Tree Problem : Algorithms and Polyhedra. Combinatorics [math.CO]. Université Clermont Auvergne, 2017. English. NNT : 2017CLFAC044. tel-01730182 HAL Id: tel-01730182 https://tel.archives-ouvertes.fr/tel-01730182 Submitted on 13 Mar 2018 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Numéro d’Ordre : D.U. 2816 EDSPIC : 799 Université Clermont Auvergne École Doctorale Sciences Pour l’Ingénieur de Clermont-Ferrand THÈSE Présentée par Jinhua ZHAO pour obtenir le grade de Docteur d’Université Spécialité : Informatique Le Problème de l’Arbre Enraciné Borné Maximum : Algorithmes et Polyèdres Soutenue publiquement le 19 juin 2017 devant le jury M. ou Mme Mohamed DIDI-BIHA Rapporteur et examinateur Sourour ELLOUMI Rapporteuse et examinatrice Ali Ridha MAHJOUB Rapporteur et examinateur Fatiha BENDALI Examinatrice Hervé KERIVIN Directeur de Thèse Philippe MAHEY Directeur de Thèse iii Acknowledgments First and foremost I would like to thank my PhD advisors, Professors Philippe Mahey and Hervé Kerivin. Without Professor Philippe Mahey, I would never have had the chance to come to ISIMA or LIMOS here in France in the first place, and I am really grateful and honored to be accepted as a PhD student of his. -

An Efficient Reachability Indexing Scheme for Large Directed Graphs
1 Path-Tree: An Efficient Reachability Indexing Scheme for Large Directed Graphs RUOMING JIN, Kent State University NING RUAN, Kent State University YANG XIANG, The Ohio State University HAIXUN WANG, Microsoft Research Asia Reachability query is one of the fundamental queries in graph database. The main idea behind answering reachability queries is to assign vertices with certain labels such that the reachability between any two vertices can be determined by the labeling information. Though several approaches have been proposed for building these reachability labels, it remains open issues on how to handle increasingly large number of vertices in real world graphs, and how to find the best tradeoff among the labeling size, the query answering time, and the construction time. In this paper, we introduce a novel graph structure, referred to as path- tree, to help labeling very large graphs. The path-tree cover is a spanning subgraph of G in a tree shape. We show path-tree can be generalized to chain-tree which theoretically can has smaller labeling cost. On top of path-tree and chain-tree index, we also introduce a new compression scheme which groups vertices with similar labels together to further reduce the labeling size. In addition, we also propose an efficient incremental update algorithm for dynamic index maintenance. Finally, we demonstrate both analytically and empirically the effectiveness and efficiency of our new approaches. Categories and Subject Descriptors: H.2.8 [Database management]: Database Applications—graph index- ing and querying General Terms: Performance Additional Key Words and Phrases: Graph indexing, reachability queries, transitive closure, path-tree cover, maximal directed spanning tree ACM Reference Format: Jin, R., Ruan, N., Xiang, Y., and Wang, H. -

"Some Contributions to Parameterized Complexity"
Laboratoire d'Informatique, de Robotique et de Micro´electronique de Montpellier Universite´ de Montpellier Speciality: Computer Science Habilitation `aDiriger des Recherches (HDR) Ignasi Sau Valls Some Contributions to Parameterized Complexity Quelques Contributions en Complexit´eParam´etr´ee Version of June 21, 2018 { Defended on June 25, 2018 Committee: Reviewers: Michael R. Fellows - University of Bergen (Norway) Fedor V. Fomin - University of Bergen (Norway) Rolf Niedermeier - Technische Universit¨at Berlin (Germany) Examinators: Jean-Claude Bermond - CNRS, U. de Nice-Sophia Antipolis (France) Marc Noy - Univ. Polit`ecnica de Catalunya (Catalonia) Dimitrios M. Thilikos - CNRS, Universit´ede Montpellier (France) Gilles Trombettoni - Universit´ede Montpellier (France) Contents 0 R´esum´eet projet de recherche7 1 Introduction 13 1.1 Contextualization................................. 13 1.2 Scientific collaborations ............................. 15 1.3 Organization of the manuscript......................... 17 2 Curriculum vitae 19 2.1 Education and positions............................. 19 2.2 Full list of publications.............................. 20 2.3 Supervised students ............................... 32 2.4 Awards, grants, scholarships, and projects................... 33 2.5 Teaching activity................................. 34 2.6 Committees and administrative duties..................... 35 2.7 Research visits .................................. 36 2.8 Research talks................................... 38 2.9 Journal and conference -

Parameterized Complexity of Finding a Spanning Tree with Minimum Reload Cost Diameter∗†
Parameterized Complexity of Finding a Spanning Tree with Minimum Reload Cost Diameter∗† Julien Baste1, Didem Gözüpek2, Christophe Paul3, Ignasi Sau4, Mordechai Shalom5, and Dimitrios M. Thilikos6 1 Université de Montpellier, LIRMM, Montpellier, France [email protected] 2 Department of Computer Engineering, Gebze Technical University, Kocaeli, Turkey [email protected] 3 AlGCo project team, CNRS, LIRMM, France [email protected] 4 Departamento de Matemática, Universidade Federal do Ceará, Fortaleza, Brazil and AlGCo project team, CNRS, LIRMM, France [email protected] 5 TelHai College, Upper Galilee, Israel and Department of Industrial Engineering, Bogaziçiˇ University, Istanbul, Turkey [email protected] 6 Department of Mathematics, National and Kapodistrian University of Athens, Greece and AlGCo project team, CNRS, LIRMM, France [email protected] Abstract We study the minimum diameter spanning tree problem under the reload cost model (Diameter- Tree for short) introduced by Wirth and Steffan (2001). In this problem, given an undirected edge-colored graph G, reload costs on a path arise at a node where the path uses consecutive edges of different colors. The objective is to find a spanning tree of G of minimum diameter with respect to the reload costs. We initiate a systematic study of the parameterized complexity of the Diameter-Tree problem by considering the following parameters: the cost of a solution, and the treewidth and the maximum degree ∆ of the input graph. We prove that Diameter- Tree is para-NP-hard for any combination of two of these three parameters, and that it is FPT parameterized by the three of them. We also prove that the problem can be solved in polynomial time on cactus graphs. -

The Surprizing Complexity of Generalized Reachability Games Nathanaël Fijalkow, Florian Horn
The surprizing complexity of generalized reachability games Nathanaël Fijalkow, Florian Horn To cite this version: Nathanaël Fijalkow, Florian Horn. The surprizing complexity of generalized reachability games. 2010. hal-00525762v2 HAL Id: hal-00525762 https://hal.archives-ouvertes.fr/hal-00525762v2 Preprint submitted on 2 Feb 2012 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. The surprising complexity of generalized reachability games Nathanaël Fijalkow1,2 and Florian Horn1 1 LIAFA CNRS & Université Denis Diderot - Paris 7, France {nath,florian.horn}@liafa.jussieu.fr 2 ÉNS Cachan École Normale Supérieure de Cachan, France Abstract. Games on graphs provide a natural and powerful model for reactive systems. In this paper, we consider generalized reachability objectives, defined as conjunctions of reachability objectives. We first prove that deciding the winner in such games is PSPACE-complete, although it is fixed-parameter tractable with the number of reachability objectives as parameter. Moreover, we consider the memory requirements for both players and give matching upper and lower bounds on the size of winning strategies. In order to allow more efficient algorithms, we consider subclasses of generalized reachability games. We show that bounding the size of the reachability sets gives two natural subclasses where deciding the winner can be done efficiently. -
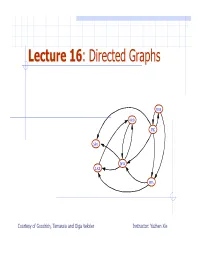
Lecture 16: Directed Graphs
Lecture 16: Directed Graphs BOS ORD JFK SFO DFW LAX MIA Courtesy of Goodrich, Tamassia and Olga Veksler Instructor: Yuzhen Xie Outline Directed Graphs Properties Algorithms for Directed Graphs DFS and BFS Strong Connectivity Transitive Closure DAG and Toppgological Ordering 2 Digraphs A digraph is a ggpraph whose E edges are all directed D Short for “directed graph” C Applications B one-way streets A flights task scheduling 3 Digraph Properties E D A graph G=(V,E) such that Each edge goes in one direction: C Ed(dge (A,B) goes from A to B, Edge (B,A) goes from B to A, B If G is simple, m < n*(n-1). A If we keep in-edges and out-edges in separate adjacency lists, we can perform listing of in-edges and out-edges in time proportional to their size OutgoingEdges(A): (A,C), (A,D), (A,B) IngoingEdges(A): (E,A),(B,A) We say that vertex w is reachable from vertex v if there is a directed path from v to w EiseahablefomAE is reachable from A E is not reachable from D 4 Algorithm DFS(G, v) Directed DFS Input digraph G and a start vertex v of G Output traverses vertices in G reachable from v We can specialize the setLabel(v, VISITED) traversal algorithms (DFS and for all e ∈ G.outgoingEdges(v) BFS) to digraphs by traversing edges only along w ← opposite(v,e) their direction if getLabel(w) = UNEXPLORED DFS(G, w) In the directed DFS algorithm, we have 3 four types of edges E discovery edges 4 bkdback edges D forward edges cross edges A directed DFS starting at a C 2 vertex s visits all the vertices reachable from s B 5