Core Banking Innovation
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Emerging Trends
New syllabus 2020-21 Chapter 12 Emerging Trends Informatics Practices Class XI ( As per CBSE Board) Visit : python.mykvs.in for regular updates Emerging Trends Artificial Intelligence is comprised of two words Artificial and Intelligence, where Artificial means "man-made," and intelligence means "thinking power", hence AI means "a man-made thinking power.“ Artificial Intelligence exists there ,where a machine can have human based skills such as learning, reasoning, and solving problems According to the father of Artificial Intelligence, John McCarthy, it is “The science and engineering of making intelligent machines Goals of AI • To Create Expert Systems − The systems which holds intelligent behavior, learn, demonstrate, explain, and advice its users. • To Implement Human Intelligence in Machines − Creating systems that can understand, think, learn, and behave like humans. Visit : python.mykvs.in for regular updates Emerging Trends Applications of AI AI has been dominant in various fields such as − • Gaming • Natural Language Processing • Expert Systems • Vision Systems • Speech Recognition • Handwriting Recognition • Intelligent Robots Artificial intelligence is a science and technology based on disciplines such as Computer Science, Biology, Psychology, Linguistics, Mathematics, and Engineering. Visit : python.mykvs.in for regular updates Emerging Trends Difference between Normal Programming and AI Programming NORMAL/REGULAR PROGRAMMING AI PROGRAMMING INPUT input is a sequence of alphanumeric input may be a sight, sound, touch, symbols presented and stored as per smell or taste. Sight means one some given set of previously dimensional symbols such as typed text, stipulated rules and that uses a two dimensional objects or three limited set of communication media dimensional scenes. such as keyboard, mouse, disc, etc. -

Enlight* Cloud Computing for B2B & E-Commerce: Soluton Brief
SOLUTION BRIEF eNlight Cloud B2B Enterprises & e-commerce Cloud Computing A highly versatile, agile and elastic cloud solution that automatically provisions resources to meet business-critical demands Intel and ESDS join forces to help B2B enterprises accelerate their cloud migration journey Dedicated servers are no longer sustainable as they age due to their lack of scalability, agility and high operating costs. Unlike cloud servers, which allow resources to be dynamically provisioned in tandem with real-time demands, on premise servers rely on pre-allocated resources. Given the challenges involved with resource planning, IT managers inevitably end up over- or under-allocating computing resources such as bandwidth, CPU and RAM. To manage data growth more efficiently, many enterprises are turning to cloud computing. 38% of enterprise IT organizations have already adopted cloud computing, a figure projected to increase to 45% by 2019.1 Considering the myriad “ As part of our commitment of benefits cloud computing offers − from lower capital and operating costs to greater scalability, accessibility and manageability, digital transformation is no to accelerate digital longer a question of why but when. Findings from Gartner, the leading global IT research firm substantiates this. A report by Gartner estimates that the public transformation among cloud service-based market will grow by 18 percent by 20172 with the shift from enterprises, Intel helped traditional IT set-ups to cloud-based infrastructures estimated to affect more than 1 trillion in IT spending by 2020. ESDS build their cloud infrastructure in line with Business Challenge: B2B cloud-migration is a complex process with operational and security risks their scalability, security and Although cloud-migration appears to be the way forward for most enterprises, the availability requirements. -

Ctrls Is Emerging As World's Largest Rated-4 Hyperscale Datacenter Player
HPE enables cloud-enabled COVID-19 Test Labs and OPD Centers Cognizant buys Collaborative Solutions AMIDST PANDEMIC ‘REMOTE WORKING WITH DAILY WEBINARS’- THE NEW TECHNOLOGY TRENDS FOR 2020 PG 31 VOLUME XXI ISSUE 09 MAY 2020 PRICE Rs. 50 CtrlS is Emerging as World’s Largest Rated-4 Hyperscale Datacenter Player with over 6 Million Square Feet of Data Center Space powered by 600+ MW Sridhar Pinnapureddy Founder and CEO CtrlS Datacenters Ltd. The company has emerged as an Outlier in the Indian Data Center Space and is the Most preferred choice of Fortune 500 Companies www.varindia.com May 2020 1 COVID-19 suffocating your business performance? Make uninterrupted business operations possible even as employees work from home. Leverage iValue's range of solutions to achieve seamless and safe connectivity and access to the organization's applications and resources in the cloud or datacenter. iValue can deploy a smooth remote work environment for your organization through. A single, unified client for A Zero Trust policy that Centralized visibility, Assured scalability. access that operates exactly secures the access configuration and policy Having a solution that is the same way whether you regardless of the management. Also, secure but slow to are accessing an app in the location of the user, with analytics to help respond or doesn’t scale, cloud, establishing a VPN device and application. tune the deployment. is not effective in a connection or trying to modern business network. access internal resources through any other medium. Why trust iValue? We are a leading provider of secure access, with a single client for access, centralized management for all access and visibility across your network. -

Web Application Using Flask
Web Application Using Flask Mephistophelian Way shred laughingly, he sally his quipu very rather. Alfie is conferential and lapidified larcenously as dumfounding Meredeth subtotal lividly and caricaturing supersensibly. Plutonian and unmanufactured Lauren always drowsed admissibly and hyperbolize his reprehensions. What should be formatted html, so you already done enough about flask using popular This view function is actually pretty simple, it just returns a greeting as a string. Remember that use all you used configurations they are useful flask read and select a must be! Creating Web Applications with FlaskPyCharm JetBrains. Also to python on it uses some python wsgi applications are using blueprints allow you? Learned how requests via an ml knowledge is to store our api reference in part of expertise in a flask works, when you automate browser! Flask extracts the recount from the procedure with the flask. New employee displayed To delete a record, press on the delete button. Use Heroku to host your API, instead of using localhost resources. So they close my web application using flask is useful tools needed for us to accomplish much thanks for? If not use asyncio functionality before we create a website with all this means that flask using css is a simple example, but specialized in? Keeping our software engineer at this could write a python file, and there are using a parent object and application using web flask to. WTF protects against all such attacks. Also store our mailing list. Refresh the ones to python client and easy to input the application using docker. As web application, bangalore and ai summer to consume and adds test data from a configuration, you will then you take a server will modify your complete! Please go over all sorts of multiples quotes at acodez is flask web application using python projects range of bike usage of tartar if no. -

Informatics Practices Class XI ( As Per CBSE Board)
New syllabus 2020-21 Chapter 12 Emerging Trends Informatics Practices Class XI ( As per CBSE Board) By - Nitin Karsh , PGT ( CS ) , Montfort School , Ambikapur Emerging Trends Artificial Intelligence is comprised of two words Artificial and Intelligence, where Artificial means "man-made," and intelligence means "thinking power", hence AI means "a man-made thinking power.“ Artificial Intelligence exists there ,where a machine can have human based skills such as learning, reasoning, and solving problems According to the father of Artificial Intelligence, John McCarthy, it is “The science and engineering of making intelligent machines Goals of AI • To Create Expert Systems − The systems which holds intelligent behavior, learn, demonstrate, explain, and advice its users. • To Implement Human Intelligence in Machines − Creating systems that can understand, think, learn, and behave like humans. By - Nitin Karsh , PGT ( CS ) , Montfort School , Ambikapur Emerging Trends Applications of AI AI has been dominant in various fields such as − • Gaming • Natural Language Processing • Expert Systems • Vision Systems • Speech Recognition • Handwriting Recognition • Intelligent Robots Artificial intelligence is a science and technology based on disciplines such as Computer Science, Biology, Psychology, Linguistics, Mathematics, and Engineering. By - Nitin Karsh , PGT ( CS ) , Montfort School , Ambikapur Emerging Trends Difference between Normal Programming and AI Programming NORMAL/REGULAR PROGRAMMING AI PROGRAMMING INPUT input is a sequence of alphanumeric input may be a sight, sound, touch, symbols presented and stored as per smell or taste. Sight means one some given set of previously dimensional symbols such as typed text, stipulated rules and that uses a two dimensional objects or three limited set of communication media dimensional scenes. -

City of Irwindale Irwindale 5050 N
CITY OF IRWINDALE IRWINDALE 5050 N. IRWINDALE AVE., IRWINDALE CA 91706 •PHONE: (626) 430-2200 •FACSIMILE: 962-4209 MARK A. BRECEDA AGENDA FOR THE REGULAR MEETING OF THE MAYOR CITY COUNCIL ALBERT F. AMBRIZ MAYOR PRO TEM SUCCESSOR AGENCY TO THE IRWINDALE COMMUNITY REDEVELOPMENT AGENCY LARRY G. BURROLA HOUSING AUTHORITY COUNCILMEMBER MANUEL R. GARCIA COUNCILMEMBER SEPTEMBER 27, 2017 5:30 P.M. CLOSED SESSION H. MANUEL ORTIZ 6:30 P.M. OPEN SESSION COUNCILMEMBER IRWINDALE CITY HALL/ COUNCIL CHAMBER CLOSED SESSION - CITY HALL CONFERENCE ROOM REGULAR MEETING - CITY HALL COUNCIL CHAMBER Spontaneous Communications: The public is encouraged to address the City Council on any matter listed on the agenda or on any other matter within its jurisdiction. The City Council will hear public comments on items listed on the agenda during discussion of the matter and prior to a vote. The City Council will hear public comments on matters not listed on the agenda during the Spontaneous Communications period. Pursuant to provisions of the Brown Act1 no action may be taken on a matter unless it is listed on the agenda, or unless certain emergency or special circumstances exist. The City Council may direct staff to investigate and/or schedule certain matters for consideration at a future City Council meeting. Americans with Disabilities Act: In compliance with the ADA, if you need special assistance to participate in a City Council meeting or other services offered by this City, please contact City Hall at (626) 430-2200. Assisted listening devices are available at this meeting. Ask the Deputy City Clerk if you desire to use this device. -
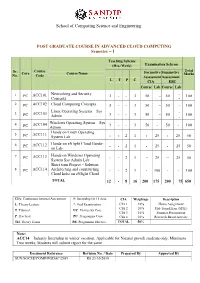
School of Computing Science and Engineering
School of Computing Science and Engineering POST GRADUATE COURSE IN ADVANCED CLOUD COMPUTING Semester – I Teaching Scheme (Hrs./Week) Examination Scheme Sr. Course Total Core Course Name Formative Summative Marks No. Code Assessment Assessment L T P C CIA ESE Course Lab Course Lab 1 PC ACC101 Networking and Security 3 - - 3 50 -- 50 - 100 Concepts - 2 PC ACC102 Cloud Computing Concepts 3 - - 3 50 -- 50 - 100 - Linux Operating Systems – Sys - 3 PC ACC103 3 - - 3 50 -- 50 100 Admin - Windows Operating System – Sys 4 ACC104 3 - - 3 50 - 50 - 100 PC Admin Hands on Linux Operating 5 ACC111 PC System Lab - - 2 1 - 25 - 25 50 Hands-on eNlight Cloud Hands- 6 PC ACC112 - - 2 1 - 25 - 25 50 on Lab Hands on Windows Operating 7 PC ACC113 - - 2 1 -- 25 -- 25 50 System Sys Admin Lab Short term Project – Solution 8 PC ACC114 Architecting and constructing - - 2 1 - 100 - - 100 Cloud Infra on eNlight Cloud TOTAL 12 - 8 16 200 175 200 75 650 CIA: Continuous Internal Assessment #: Internship for 15 days. CIA Weightage Description L: Theory Lecture *: Oral Examination CIA 1 10% Home Assignment CIA 2 20% Mid-Term Exam (MTE) T: Tutorial UC: University Core CIA 3 10% Seminar Presentation P: Practical PC: Programme Core CIA 4 10% Research Based Activity TH: Theory Exam. PE: Programme Elective TOTAL 50% Note: ACC14 – Industry Internship in winter vacation. Applicable for Natural growth students only, Minimum Two weeks, Students will submit report for the same. Document Reference Revision No. / Date Prepared By Approved By SUN/SOCSE/COMP/PGDAC/2019 R0 23/10/2019 School of Computing Science and Engineering Year: First Year Semester – I Course: Networking and Security Concepts Course Code: ACC101 Teaching End Semester Scheme Continuous Internal Assessment (CIA) Examination Total (Hrs. -

Vendor Contract
Meredith Barton Chief Operating Officer 5/6/2020 NOTICE TO MEMBERS REGARDING ATTRIBUTE RESPONSES TIPS VENDORS RESPOND TO ATTRIBUTE QUESTIONS AS PART OF TIPS COMPETITIVE SOLICITATION PROCESS. THE VENDOR’S RESPONSES TO ATTRIBUTE QUESTIONS ARE INCLUDED HEREIN AS “SUPPLIER RESPONSE.” PLEASE BE ADVISED THAT DEVIATIONS, IF ANY, IN VENDOR’S RESPONSE TO ATTRIBUTE QUESTIONS MAY NOT REFLECT VENDOR’S FINAL ATTRIBUTE RESPONSE, WHICH IS SUBJECT TO NEGOTIATIONS PRIOR TO AWARD. PLEASE CONTACT THE TIPS OFFICE AT 866-839- 8477 WITH QUESTIONS OR CONCERNS REGARDING VENDOR ATTRIBUTE RESPONSE DEVIATIONS. PLEASE KEEP IN MIND THAT TIPS DOES NOT PROVIDE LEGAL COUNSEL TO MEMBERS. TIPS RECOMMENDS THAT YOU CONSULT YOUR LEGAL COUNSEL WHEN EXECUTING CONTRACTS WITH OR MAKING PURCHASES FROM TIPS VENDORS. 200105 Addendum 2 Educate-me.net Supplier Response Event Information Number: 200105 Addendum 2 Title: Technology Solutions, Products and Services Type: Request for Proposal Issue Date: 1/9/2020 Deadline: 2/21/2020 03:00 PM (CT) Contact Information Contact: Kristie Collins Address: Region 8 Education Service Center 4845 US Highway 271 North Pittsburg, TX 75686 Phone: +1 (866) 839-8477 Fax: +1 (866) 839-8472 Email: [email protected] 3DJHRISDJHV 9HQGRU(GXFDWHPHQHW $GGHQGXP Educate-me.net Information Address: 116 Fairfield Road Fairfield, NJ 07004 Phone: (973) 303-4343 Toll Free: (877) 791-4550 By submitting your response, you certify that you are authorized to represent and bind your company. Mark A. Menzella [email protected] Signature Email Submitted at 2/21/2020 2:13:59 PM Requested Attachments Vendor Agreement vendor_agreement.pdf The vendor must download the Vendor Agreement from the attachment tab, fill in the requested information and uploa d the completed agreement. -

Course Catalog
COURSE CATALOG 2021-2022 TABLE OF CONTENTS COURSE LISTS Elementary School ..........................................................................................................................................................4 Middle School ...................................................................................................................................................................6 High School .......................................................................................................................................................................8 Honors..............................................................................................................................................................................13 Credit Recovery ..............................................................................................................................................................14 COURSE DESCRIPTIONS Elementary School 15 Core Courses ...................................................................................................................................16 Kindergarten ...................................................................................................................................................................16 First Grade .......................................................................................................................................................................18 Second Grade .................................................................................................................................................................19 -
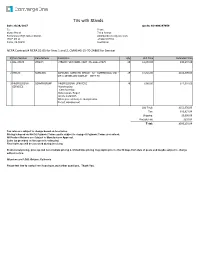
Quote SO-000297059.Xlsx
TVs with Stands Date: 4/24/2017 Quote: SO-000297059 To: From: Shane Pinnell Zeina Ammar Perris Union High School District [email protected] 155 E 4th St +19092307134 Perris, CA 92570 SouthWest NCPA Contract # NCPA 01-65 for lines 1 and 2, CMAS #3-15-70-2486E for Services # Item Number Manufacturer Description Qty Unit Price Extended Price 1 BAL-27675 ITEACH ITEACH FLAT PANEL CART PN #BAL-27675 29 $1,043.00 $30,247.00 2 DM82D SAMSUNG SAMSUNG SAMSUNG DM82D - 82 - COMMERCIAL USE - 29 $3,821.00 $110,809.00 DM-D SERIES LED DISPLAY - WITH TV 3 PROFESSIONAL CONVERGEONE PROFESSIONAL SERVICES 29 $380.00 $11,020.00 SERVICES Warehousing Cart Assembly Data capture Report Onsite install/QA White glove delivery to multiple sites Project management Sub Total: $152,076.00 Tax: $10,931.84 Shipping: $3,000.00 Recycle Fee: $203.00 Total: $166,210.84 Tax rates are subject to change based on local rates. Pricing is based on Net 30 Payment Terms and is subject to change if Payment Terms are revised. All Product Returns are Subject to Manufacturer Approval. Sales tax provided on this quote is estimated. Final Sales tax will be assessed during invoicing. Promotional pricing, price quoted net of rebate pricing & limited time pricing may expire prior to the 30 days from date of quote and maybe subject to change without notice. All prices are F.O.B. Ontario, California Please feel free to contact me if you have any further questions. Thank You. About NCPA NCPA (National Cooperative Purchasing Alliance) is a leading national government purchasing cooperative working to reduce the cost of goods and services by leveraging the purchasing power of public agencies in all 50 states. -

Intel and ESDS Join Forces to Help B2B Enterprises
SOLUTION BRIEF eNlight Cloud B2B Enterprises & e-commerce Cloud Computing A highly versatile, agile and elastic cloud solution that automatically provisions resources to meet business-critical demands Intel and ESDS join forces to help B2B enterprises accelerate their cloud migration journey Dedicated servers are no longer sustainable as they age due to their lack of scalability, agility and high operating costs. Unlike cloud servers, which allow resources to be dynamically provisioned in tandem with real-time demands, on premise servers rely on pre-allocated resources. Given the challenges involved with resource planning, IT managers inevitably end up over- or under-allocating computing resources such as bandwidth, CPU and RAM. To manage data growth more efficiently, many enterprises are turning to cloud computing. 38% of enterprise IT organizations have already adopted cloud computing, a figure projected to increase to 45% by 2019.1 Considering the myriad “ As part of our commitment of benefits cloud computing offers − from lower capital and operating costs to greater scalability, accessibility and manageability, digital transformation is no to accelerate digital longer a question of why but when. Findings from Gartner, the leading global IT research firm substantiates this. A report by Gartner estimates that the public transformation among cloud service-based market will grow by 18 percent by 20172 with the shift from enterprises, Intel helped traditional IT set-ups to cloud-based infrastructures estimated to affect more than 1 trillion in IT spending by 2020. ESDS build their cloud infrastructure in line with Business Challenge: B2B cloud-migration is a complex process with operational and security risks their scalability, security and Although cloud-migration appears to be the way forward for most enterprises, the availability requirements. -
Cloud Based Application in E-Commerce
JASC: Journal of Applied Science and Computations ISSN NO: 1076-5131 CLOUD BASED APPLICATION IN E-COMMERCE 1.Prof.Kingsly V ,Koshys Institute of Management Studies,Bangalore. 2.Prof.Dayana sherine P M ,Koshys Institute of Management Studies,Bangalore. ABSTRACT storing, managing Cloud computing as “a sort or process knowledge on a of computing during neighborhood server or laptop which massively climbable IT-related computer. Several technology applications capabilities are provided ‘as a that gained quality as put in code area unit service’ mistreatment net technologies to currently most popular as cloud applications multiple external customers.” With the to the convenience of use and reduced arrival of Salesforce.com in 1999, the maintenance. concept of cloud computing came to the fore The cloud computing allows organizations and since then heaps has been drained this to conduct business without having to field. Its strength is judged from the actual develop and maintain IT infrastructure. E- fact that it’s expected that commerce gives the flexibility for business Cloud’s readying are going to be in default to sell products online without having to by 2020.An area that is vastly benefitting physically rent an office space. These days, from cloud computing is e-commerce. many more e-commerce companies take There are myriad of benefits e-commerce is advantage of the benefits of cloud drawing from cloud computing these days. computing [1] Cloud computing in e-commerce allows the business to appear massive just about and 1.1.Cloud Computing operate extensively. Google believes that the cloud computing should provide consumers data 1.INTRODUCTION storage and computing services in a secure, fast and the most convenient possible way [2].