The Best-Ever Freeware List 1 Best Free Web Browser [1]
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Easy Slackware
1 Создание легкой системы на базе Slackware I - Введение Slackware пользуется заслуженной популярностью как классический linux дистрибутив, и поговорка "кто знает Red Hat тот знает только Red Hat, кто знает Slackware тот знает linux" несмотря на явный снобизм поклонников "бога Патре га" все же имеет под собой основания. Одним из преимуществ Slackware является возможность простого создания на ее основе практически любой системы, в том числе быстрой и легкой десктопной, о чем далее и пойдет речь. Есть дис трибутивы, клоны Slackware, созданные именно с этой целью, типа Аbsolute, но все же лучше создавать систему под себя, с максимальным учетом именно своих потребностей, и Slackware пожалуй как никакой другой дистрибутив подходит именно для этой цели. Легкость и быстрота системы определяется выбором WM (DM) , набором программ и оптимизацией программ и системы в целом. Первое исключает KDE, Gnome, даже новые версии XFCЕ, остается разве что LXDE, но набор программ в нем совершенно не устраивает. Оптимизация наиболее часто используемых про грамм и нескольких базовых системных пакетов осуществляется их сборкой из сорцов компилятором, оптимизированным именно под Ваш комп, причем каж дая программа конфигурируется исходя из Ваших потребностей к ее возможно стям. Оптимизация системы в целом осуществляется ее настройкой согласно спе цифическим требованиям к десктопу. Такой подход был выбран по банальной причине, возиться с gentoo нет ни какого желания, комп все таки создан для того чтобы им пользоваться, а не для компиляции программ, в тоже время у каждого есть минимальный набор из не большого количества наиболее часто используемых программ, на которые стоит потратить некоторое, не такое уж большое, время, чтобы довести их до ума. Кро ме того, такой подход позволяет иметь самые свежие версии наиболее часто ис пользуемых программ. -

Further Reading and What's Next
APPENDIX Further Reading and What’s Next I hope you have gotten an idea of how, as a penetration tester, you could test a web application and find its security flaws by hunting bugs. In this concluding chapter, we will see how we can extend our knowledge of what we have learned so far. In the previous chapter, we saw how SQL injection has been done; however, we have not seen the automated part of SQL injection, which can be done by other tools alongside Burp Suite. We will use sqlmap, a very useful tool, for this purpose. Tools that Can Be Used Alongside Burp Suite We have seen earlier that the best alternative to Burp Suite is OWASP ZAP. Where Burp Community edition has some limitations, ZAP can help you overcome them. Moreover, ZAP is an open source free tool; it is community-based, so you don’t have to pay for it for using any kind of advanced technique. We have also seen how ZAP works. Here, we will therefore concentrate on sqlmap only, another very useful tool we need for bug hunting. The sqlmap is command line based. It comes with Kali Linux by default. You can just open your terminal and start scanning by using sqlmap. However, as always, be careful about using it against any live © Sanjib Sinha 2019 197 S. Sinha, Bug Bounty Hunting for Web Security, https://doi.org/10.1007/978-1-4842-5391-5 APPENDIX FuRtHeR Reading and What’s Next system; don’t use it without permission. If your client’s web application has vulnerabilities, you can use sqlmap to detect the database, table names, columns, and even read the contents inside. -

Creating Permanent Test Collections of Web Pages for Information Extraction Research*
Creating Permanent Test Collections of Web Pages for Information Extraction Research* Bernhard Pollak and Wolfgang Gatterbauer Database and Artificial Intelligence Group Vienna University of Technology, Austria {pollak, gatter}@dbai.tuwien.ac.at Abstract. In the research area of automatic web information extraction, there is a need for permanent and annotated web page collections enabling objective performance evaluation of different algorithms. Currently, researchers are suffering from the absence of such representative and contemporary test collections, especially on web tables. At the same time, creating your own sharable web page collections is not trivial nowadays because of the dynamic and diverse nature of modern web technologies employed to create often short- lived online content. In this paper, we cover the problem of creating static representations of web pages in order to build sharable ground truth test sets. We explain the principal difficulties of the problem, discuss possible approaches and introduce our solution: WebPageDump, a Firefox extension capable of saving web pages exactly as they are rendered online. Finally, we benchmark our system with current alternatives using an innovative automatic method based on image snapshots. Keywords: saving web pages, web information extraction, test data, Firefox, web table ground truth, performance evaluation 1 Introduction In the visions of a future Semantic Web, agents will crawl the web for information related to a given task. With the current web lacking semantic annotation, researchers are working on automatic information extraction systems that allow transforming heterogonous and semi-structured information into structured databases that can be later queried for data analysis. For testing purposes researchers need representative and annotated ground truth test data sets in order to benchmark different extraction algorithms against each other. -

Digicult.Info Issue 6
.Info Issue 6 A Newsletter on Digital Culture ISSN 1609-3941 December 2003 INTRODUCTION his is a rich issue of DigiCULT.Info covering topics in such Tareas as digitisation, asset management and publication, virtual reality, documentation, digital preservation, and the development of the knowledge society. n October the Italian Presidency of the European Union pro- Imoted, in cooperation with the European Commission and the ERPANET (http://www.erpanet.org) and MINERVA Continued next page (UofGlasgow),© HATII Ross, Seamus 2003 Technology explained and applied ... Challenges, strategic issues, new initiatives ... 6 3D-ArchGIS:Archiving Cultural Heritage 16 New Open-source Software for Content in a 3D Multimedia Space and Repository Management 10 Zope at Duke University: Open Source Content 19 The IRCAM Digital Sound Archive in Context Management in a Higher Education Context 55 Towards a Knowledge Society 16 PLEADE – EAD for the Web 31 Metadata Debate:Two Perspectives on Dublin Core News from DigiCULT´s Regional Correspondents ... 34 Cistercians in Yorkshire: Creating a Virtual Heritage Learning Package 37 Bulgaria 45 SMIL Explained 38 Czech Republic 47 Finding Names with the Autonom Parser 40 France 49 The Object of Learning:Virtual and Physical 41 Greece Cultural Heritage Interactions 42 Italy News, events ... 44 Poland 44 Serbia and Montenegro 23 Delivering The Times Digital Archive 30 NZ Electronic Text Centre 37 Cultural Heritage Events Action in the Preservation of Memory ... 52 New Project Highlights the Growing Use of DOIs 24 PANDORA,Australia’s -

Monitoring of Online Offenders by Researchers
SGOC STUDYING GROUP ON ORGANISED CRIME https://sgocnet.org Sifting through the Net: Monitoring of Online Offenders by Researchers Research note Sifting through the Net: Monitoring of Online Offenders by Researchers David Décary-Hétu and Judith Aldridge* Abstract: Criminologists have traditionally used official records, interviews, surveys, and observation to gather data on offenders. Over the past two decades, more and more illegal activities have been conducted on or facilitated by the Internet. This shift towards the virtual is important for criminologists as traces of offenders’ activities can be accessed and monitored, given the right tools and techniques. This paper will discuss three techniques that can be used by criminologists looking to gather data on offenders who operate online: 1) mirroring, which takes a static image of an online resource like websites or forums; 2) monitoring, which involves an on- going observation of static and dynamic resources like websites and forums but also online marketplaces and chat rooms and; 3) leaks, which involve downloading of data placed online by offenders or left by them unwittingly. This paper will focus on how these tools can be developed by social scientists, drawing in part on our experience developing a tool to monitor online drug “cryptomarkets” like Silk Road and its successors. Special attention will be given to the challenges that researchers may face when developing their own custom tool, as well as the ethical considerations that arise from the automatic collection of data online. Keywords: Cybercrime – Internet research methods – Crawler – Cryptomarkets avid e cary- e tu is Assistant Professor at the School of Criminology, University of Montreal, and Researcher at the International Centre of Comparative Criminology (ICCC). -
Open Source Software Notice
Open Source Software Notice This document describes open source software contained in LG Smart TV SDK. Introduction This chapter describes open source software contained in LG Smart TV SDK. Terms and Conditions of the Applicable Open Source Licenses Please be informed that the open source software is subject to the terms and conditions of the applicable open source licenses, which are described in this chapter. | 1 Contents Introduction............................................................................................................................................................................................. 4 Open Source Software Contained in LG Smart TV SDK ........................................................... 4 Revision History ........................................................................................................................ 5 Terms and Conditions of the Applicable Open Source Licenses..................................................................................... 6 GNU Lesser General Public License ......................................................................................... 6 GNU Lesser General Public License ....................................................................................... 11 Mozilla Public License 1.1 (MPL 1.1) ....................................................................................... 13 Common Public License Version v 1.0 .................................................................................... 18 Eclipse Public License Version -
Download Calendar Program Windows 10 5 Best Free Open Source Calendar Software for Windows
download calendar program windows 10 5 Best Free Open Source Calendar Software for Windows. Here is a list of best free open source calendar software for Windows. These are free desktop calendar software which come with open source license. You can freely download and study source code of these calendar software and even manipulate the source code. These calendar software let you view the calendar in monthly, daily, weekly, or yearly view. You can also add and schedule important events on particular dates in a month. All of these software provide appointment editor tool to add and manage multiple appointments with date and time, reminder settings, priority, etc. You also get a feature to add and manage various contacts in a few of these software. Additionally, you can create a to-do list in these software to keep up with your daily tasks. You can also add essential notes and memos on particular dates. In one of these software, you can also import iCalendar files to add calendar events. Also, for students, there is a nice software with features including time table and booklet creator. Other than that, you get various useful features in these software which include task categories creator, email alert generator, setup calendar appearance, reminder tone, etc. In general, these are featured open source calendar software which are useful in keeping up with the dates and managing important tasks. My favorite Free Open Source Calendar Software for Windows: BORG Calendar is a good desktop calendar software which comes with a lot of handy tools including appointment editor, tasks creator, memos creator, checklists maker, etc. -

Juridische Aandachtspunten Bij Het Gebruik Van Open Source Software
Juridische aandachtspunten bij het gebruik van Open Source Software [email protected] 1 Inhoud Achtergrond en open source definitie Voorbeelden open source software en licenties Welke licentie is van toepassing? Enkele bepalingen uitgelicht Praktijktips 2 Technische achtergrond 3 Conceptuele achtergrond 4 Open source definitie 1. De licentie mag niemand verbieden de software gratis weg te geven óf te verkopen. 2. De broncode moet met de software meegeleverd worden of vrij beschikbaar zijn. 3. Wederverspreiding van afgeleide werken en aangepaste versies van de software moet toegestaan zijn. 4. Licenties mogen vereisen dat aanpassingen alleen als patch verspreid worden. 5. De licentie mag niet discrimineren tegen gebruikers(groepen). 6. De licentie mag niet discrimineren tegen gebruiksomgeving van de software. 7. De rechten verbonden aan het programma moeten opgaan voor iedereen aan wie het programma gedistribueerd wordt. 8. De rechten verbonden aan het programma moeten niet afhangen van softwaredistributies waarvan de software een onderdeel is. 9. De licentie mag niet verlangen dat andere software die samen met de software verspreid wordt onder dezelfde licentie valt. 10. Geen van de bepalingen van de licentie mag slaan op een bepaalde technologie of interface-stijl. 5 Voorbeelden Apache License, 2.0 BSD licenses GNU General Public License (GPL) GNU Library or "Lesser" General Public License (LGPL) MIT license Mozilla Public License 1.1 (MPL) Common Development and Distribution License Common Public License 1.0 Eclipse Public License -
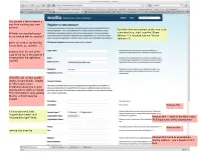
Eg, Right Now the "Street Address 2 Is Required, but Not "
You are just a few moments a way from creating your new browser. For fields that are required, make sure to be All fields are required except consistent (e.g., right now the "Street those marked with an asterisk * Address 2 is required, but not "Street Address 1") [note: no need to say that this is your basic account info....”] [remove all of the rest of the copy at the top of the page as it is repeated in the right-hand column] UPDATE: will call this “profile” Under account details, simplify to: “We require some information about you or your organization in order to register. This information is only used by Mozilla and will never be shared. Remove this If select personal, hide "organization name" and "organization type" fields Remove this -- add it to the field name: “Full legal name of the organization” Remove this remove star from fax Change field name to organization mailing address - use a header in that form Simplify this copy to something like: “The information in this section will show up in the browser directory [note is there a way not to have this publicly available?]. Simplify this copy to something like: Headline: Thank you for registering! Youʼre almost ready to create a customized browser! Youʼll receive an email shortly confirming that your account is approved. Please follow the instructions in order to finalize your registration. If for some reason you donʼt receive an email after 24 hours, please contact us at [email protected] (check your SPAM filter first!). Alternatively, click the button below to re-send your activation information now. -

IFIP AICT 404, Pp
Identifying Success Factors for the Mozilla Project Robert Viseur1,2 1 University of Mons (FPMs), Rue de Houdain, 9, B-7000 Mons, Belgium [email protected] 2 CETIC, Rue des Frères Wright, 29/3, B-6041 Charleroi, Belgium [email protected] Abstract. The publication of the Netscape source code under free software li- cense and the launch of the Mozilla project constitute a pioneering initiative in the field of free and open source software. However, five years after the publi- cation came years of decline. The market shares rose again after 2004 with the lighter Firefox browser. We propose a case study covering the period from 1998 to 2012. We identify the factors that explain the evolution of the Mozilla project. Our study deepens different success factors identified in the literature. It is based on authors' experience as well as the abundant literature dedicated to the Netscape company and the Mozilla project. It particularly highlights the im- portance of the source code complexity, its modularity, the responsibility as- signment and the existence of an organisational sponsorship. 1 Introduction After the launch of the GNU project in 1984 and the emergence of Linux in 1991, the Mozilla project was probably one of the most important events in the field of free and open source software at the end of the nineteenth century (Viseur, 2011). It was a pioneering initiative in the release of proprietary software, while commercial involvement in the development of free and open source software has accelerated over the last ten years (Fitzgerald, 2006). Netscape was the initiator. -

Vdirsyncer Documentation Release 0.18.1.Dev82+Gdb6da70
vdirsyncer Documentation Release 0.18.1.dev82+gdb6da70 Markus Unterwaditzer Sep 22, 2021 Users 1 When do I need Vdirsyncer?3 2 Installation 5 3 Tutorial 9 4 SSL and certificate validation 15 5 Storing passwords 17 6 Syncing with read-only storages 19 7 Full configuration manual 21 8 Other tutorials 31 9 Known Problems 39 10 Contributing to this project 41 11 The Vdir Storage Format 45 12 Packaging guidelines 47 13 Support and Contact 49 14 Changelog 51 15 Credits and License 65 16 Donations 67 Bibliography 69 Index 71 i ii vdirsyncer Documentation, Release 0.18.1.dev82+gdb6da70 • Documentation • Source code Vdirsyncer is a command-line tool for synchronizing calendars and addressbooks between a variety of servers and the local filesystem. The most popular usecase is to synchronize a server with a local folder and use a set of other programs to change the local events and contacts. Vdirsyncer can then synchronize those changes back to the server. However, vdirsyncer is not limited to synchronizing between clients and servers. It can also be used to synchronize calendars and/or addressbooks between two servers directly. It aims to be for calendars and contacts what OfflineIMAP is for emails. Users 1 vdirsyncer Documentation, Release 0.18.1.dev82+gdb6da70 2 Users CHAPTER 1 When do I need Vdirsyncer? 1.1 Why not Dropbox + todo.txt? Projects like todo.txt criticize the complexity of modern productivity apps, and that rightfully. So they set out to create a new, super-simple, human-readable format, such that vim suffices for viewing the raw data. -

CIT381 COURSE TITLE: File Processing and Management
NATIONAL OPEN UNIVERSITY OF NIGERIA SCHOOL OF SCIENCE AND TECHNOLOGY COURSE CODE: CIT381 COURSE TITLE: File Processing and Management CIT381 COURSE GUIDE COURSE GUIDE CIT381 FILE PROCESSING AND MANAGEMENT Course Team Ismaila O. Mudasiru (Developer/Writer) - OAU NATIONAL OPEN UNIVERSITY OF NIGERIA ii CIT381 COURSE GUIDE National Open University of Nigeria Headquarters 14/16 Ahmadu Bello Way Victoria Island Lagos Abuja Office No. 5 Dar es Salaam Street Off Aminu Kano Crescent Wuse II, Abuja Nigeria e-mail: [email protected] URL: www.nou.edu.ng Published By: National Open University of Nigeria First Printed 2011 ISBN: 978-058-525-7 All Rights Reserved CONTENTS PAGE iii CIT381 COURSE GUIDE Introduction …………………..…………………………………… 1 What You Will Learn in this Course………………………………. 1 Course Aims ………………………………………………………. 2 Course Objectives …………………………………………………. 2 Working through this Course………………………….…………… 3 The Course Materials………………………………………………. 3 Study Units…………………………………………………………. 3 Presentation Schedule……………….……………………………… 4 Assessment…………………………………………………………. 5 Tutor-Marked Assignment…………………………………………. 5 Final Examination and Grading……………………………………. 6 Course Marking Scheme…………………………………………… 6 Facilitators/Tutors and Tutorials…………………………………… 6 Summary…………………………………………………………… 7 iv CIT381 FILE PROCESSING AND MANAGEMENT Introduction File Processing and Management is a second semester course. It is a 2- credit course that is available to students offering Bachelor of Science, B. Sc., Computer Science, Information Systems and Allied degrees. Computers can store information on several different types of physical media. Magnetic tape, magnetic disk and optical disk are the most common media. Each of these media has its own characteristics and physical organisation. For convenience use of the computer system, the operating system provides a uniform logical view of information storage. The operating system abstracts from the physical properties of its storage devices to define a logical storage unit, the file.