Planning for Security Copyright Copyright © 2007 Microsoft Corporation
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Passwordless Authentication: How Giving up Your Password Might Make You More Secure
thalesgroup.com Passwordless Authentication: How Giving Up Your Password Might Make You More Secure White Paper Why Passwords Are Bad Passwords are one of the oldest security tools in the world of software and the internet. But in today’s environment, passwords cannot provide enough protection for businesses for several reasons. Password Fatigue Leads to Bad Hygiene Policy-driven password strengths and rotation leads to password fatigue, thereby contributing to poor password management. Verizon’s Data Breach Investigation Report1 indicates that over 70 percent of employees reuse passwords for work and personal accounts. A malicious actor could therefore abuse an employee’s credentials to access other applications and sensitive customer information. % out “123456” 81 ~40 4 of 5 “password” of breaches involve Average person People reuse same still among most use of weak or has roughly 40 passwords across popular password stolen credentials online accounts dierent accounts choices in 2018 People also tend to pick easy-to-hack passwords because of the trouble they have with remembering passwords. An analysis of over five million leaked passwords showed that 10 percent of people used one of the 25 worst passwords2. Seven percent of enterprise users had extremely weak passwords. Passwords Hurt User Experience Research by Carnegie Mellon University indicates that a properly written password policy can provide an organization with increased security. However, there is less accord over what should be in this policy to make it effective. To illustrate this fact, users commonly react to a policy rule that requires them to include numbers by picking the same number or by using the number in the same location in their passwords3. -

Run-Commands-Windows-10.Pdf
Run Commands Windows 10 by Bettertechtips.com Command Action Command Action documents Open Documents Folder devicepairingwizard Device Pairing Wizard videos Open Videos Folder msdt Diagnostics Troubleshooting Wizard downloads Open Downloads Folder tabcal Digitizer Calibration Tool favorites Open Favorites Folder dxdiag DirectX Diagnostic Tool recent Open Recent Folder cleanmgr Disk Cleanup pictures Open Pictures Folder dfrgui Optimie Drive devicepairingwizard Add a new Device diskmgmt.msc Disk Management winver About Windows dialog dpiscaling Display Setting hdwwiz Add Hardware Wizard dccw Display Color Calibration netplwiz User Accounts verifier Driver Verifier Manager azman.msc Authorization Manager utilman Ease of Access Center sdclt Backup and Restore rekeywiz Encryption File System Wizard fsquirt fsquirt eventvwr.msc Event Viewer calc Calculator fxscover Fax Cover Page Editor certmgr.msc Certificates sigverif File Signature Verification systempropertiesperformance Performance Options joy.cpl Game Controllers printui Printer User Interface iexpress IExpress Wizard charmap Character Map iexplore Internet Explorer cttune ClearType text Tuner inetcpl.cpl Internet Properties colorcpl Color Management iscsicpl iSCSI Initiator Configuration Tool cmd Command Prompt lpksetup Language Pack Installer comexp.msc Component Services gpedit.msc Local Group Policy Editor compmgmt.msc Computer Management secpol.msc Local Security Policy: displayswitch Connect to a Projector lusrmgr.msc Local Users and Groups control Control Panel magnify Magnifier -

Modern Password Security for System Designers What to Consider When Building a Password-Based Authentication System
Modern password security for system designers What to consider when building a password-based authentication system By Ian Maddox and Kyle Moschetto, Google Cloud Solutions Architects This whitepaper describes and models modern password guidance and recommendations for the designers and engineers who create secure online applications. A related whitepaper, Password security for users, offers guidance for end users. This whitepaper covers the wide range of options to consider when building a password-based authentication system. It also establishes a set of user-focused recommendations for password policies and storage, including the balance of password strength and usability. The technology world has been trying to improve on the password since the early days of computing. Shared-knowledge authentication is problematic because information can fall into the wrong hands or be forgotten. The problem is magnified by systems that don't support real-world secure use cases and by the frequent decision of users to take shortcuts. According to a 2019 Yubico/Ponemon study, 69 percent of respondents admit to sharing passwords with their colleagues to access accounts. More than half of respondents (51 percent) reuse an average of five passwords across their business and personal accounts. Furthermore, two-factor authentication is not widely used, even though it adds protection beyond a username and password. Of the respondents, 67 percent don’t use any form of two-factor authentication in their personal life, and 55 percent don’t use it at work. Password systems often allow, or even encourage, users to use insecure passwords. Systems that allow only single-factor credentials and that implement ineffective security policies add to the problem. -

The Tangled Web of Password Reuse
The Tangled Web of Password Reuse Anupam Das∗, Joseph Bonneauy, Matthew Caesar∗, Nikita Borisov∗ and XiaoFeng Wangz ∗University of Illinois at Urbana-Champaign fdas17, caesar, [email protected] yPrinceton University [email protected] zIndiana University at Bloomington [email protected] Abstract—Today’s Internet services rely heavily on text-based password meters to help users understand the strength of their passwords for user authentication. The pervasiveness of these passwords. Studies have shown that password composition services coupled with the difficulty of remembering large numbers policies along with password meters (or verbal notifications) of secure passwords tempts users to reuse passwords at multiple do help users to choose stronger passwords [35], [44], [46]. sites. In this paper, we investigate for the first time how an However, they also increase user fatigue. attacker can leverage a known password from one site to more easily guess that user’s password at other sites. We study several Unfortunately, the number of passwords a user must re- hundred thousand leaked passwords from eleven web sites and member continues to increase, with typical Internet user es- conduct a user survey on password reuse; we estimate that 43- timated to have 25 distinct online accounts [10], [11], [32]. 51% of users reuse the same password across multiple sites. Because of this, users often reuse passwords across accounts We further identify a few simple tricks users often employ to on different online services. Password reuse introduces a secu- transform a basic password between sites which can be used by an attacker to make password guessing vastly easier. We develop the rity vulnerability as an attacker who is able to compromise one first cross-site password-guessing algorithm, which is able to guess service can compromise other services protected by the same 30% of transformed passwords within 100 attempts compared to password, reducing overall security to that of the weakest site. -

Nfront Password Filter Documentation 2
nFront Password Filter Multiple Policy Edition for Domain Controllers Single Policy Edition for Domain Controllers Single Policy Edition for Member Servers Multiple Policy Edition for Member Servers Desktop Edition Version 7.1.0 © 2000 – 2021 nFront Security. Documentation All Rights Reserved. nFront Security, the nFront Security logo and nFront Password Filter are trademarks of Altus Network Solutions, Inc. All other trademarks or registered trademarks are the property of their Copyright © 2021 nFront Security. All Rights Reserved. Contents 1.0 nFront Password Filter Overview ........................................................................... 2 1.1 Versions ................................................................................................................. 2 1.2 Compatibility and System Requirements ................................................................ 3 1.3 What’s New ............................................................................................................ 4 1.3 Notes to Evaluators ................................................................................................ 5 1.4 Overview of Features ............................................................................................. 7 1.4.1 The logic behind multiple policies (MPE version only) ................................................... 8 1.4.2 The Message Box for Rejected Passwords ...................................................................... 8 1.5 Information about your Evaluation Copy. ............................................................... -
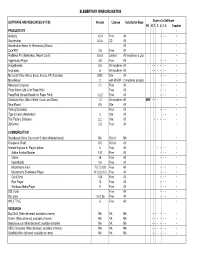
Elementary Windows Matrix
ELEMENTARY WINDOWS MATRIX SOFTWARE AND RESOURCES 8/17/05 Version License Installation Base Access to Software PK K 1 2 3 4 5 Teacher PRODUCTIVITY • Audacity 1.2.4 Free All • • • • Boardmaker 5.3.6 CD All • Boardmaker Addon for Elementary Schools All • Cute PDF 2.6 Free All • FileMaker Pro (Networked, Report Cards) 5.0v3 Limited AV machines & Lab • Hyperstudio Player 4.5 Free All • • • • ImageBlender 2.5 All machines All • • • • • • • • Inspiration 8 All machines All • • • • • • • Microsoft Office (Word, Excel, Access, PP, Publisher) 2000 Site All • • • • MovieMaker 2 with WinXP 2 machines on carts • Netscape Composer 7.1 Free All • • • • Photo Album add-in for PowerPoint Free All • • • • PowerTalk (Screen Reader for Power Point) 1.2.2 Free All • • • • Scholastic Keys (Max's Write, Count, and Show) 1.2 All machines All MW • • • • SmartBoard 9.5 Site All • Talking Calculator Free All • • • • Type to Learn (Networked) 3 Site All • • • Tool Factory Database 2.2 Site All • • • • • • ZipCentral 2.6 Free All • COMMUNICATION Blackboard Online Classroom Builder (Web-delivered) NA District NA • Groupwise Client 6.5 District All • Internet Explorer w. Plugins below: 6 Free All • • • • • Adobe Acrobat Reader 7.07 Free All • • • • Chime v6 Free All • • • • HyperStudio 4.5 Free All Macromedia Flash 7 (7.0.19.0) Free All • • • • Macromedia Shockwave Player 10 (0.0.21.0) Free All • • • • QuickTime 7.04 Free All • • • • Real Player 10 Free All • • • • Windows Media Player 9 Free All • • • • SOL Fonts Free All • • • • Sun Java 1.5.0_06 Free All • • • • -

Document Preparation in Classical Languages
4.2. Operating System Support: Windows tional language is not the same as anging the language of the user interface. If you want all your menus and so forth in German, that is an additional step. Additional Keyboard Resources Tom Gewee has created keyboards for many languages in addition to those provided by OS X. ey can be found at http://homepage. mac.com/thgewecke/tckbs.html. He also has a general “Multilin- gual Mac” page at http://homepage.mac.com/thgewecke/mlingos9. html and a blog at http://m10lmac.blogspot.com/, both of whi are excellent sources of information about using the Mac OS when writ- ing in languages other than English. ird-party Utilities You can use third-party utilities su as the well known PopChar to e out and enter aracters; see http://www.macility.com/ products/popcharx/), where a demo version is available. e Unicode Cheer utility from earthlingso does a few things that Character Palee doesn’t, su as convert Unicode values to HTML entities or help with normalization issues. In some ways it is more convenient than the Character Palee. See http://earthlingsoft. net/UnicodeChecker/index.html. See also the discussion of GreekKeys in §7.3, page 131. Warning for Mac Users! Be careful not to log out while using a keyboard that does not allow you to enter your password in order to get ba in — for example, logging out when a Hebrew or Greek keyboard is in effect if your password requires Latin aracters. SAMPLE4.2 Operating System Support: Windows -key Methods Windows, by contrast, provides two system-wide methods for access- ing non-English aracters, both of them clumsy. -

Copyrighted Material
18_579274 bindex.qxd 2/22/05 7:41 PM Page 312 Index A C accounts call waiting, dial-up account setup, 196 computer administrator, 157 cascade windows, 35 create, 156–157 CD Writing Wizard, 143 delete, 166–167 CDs Internet connection, manual setup, 194–197 backups to, 289 limited user, 157 burn music to, 124–125 name changes, 160–161 copy files to, 140–143 name restrictions, 161 music, Media Player and, 112–115, 120–123 passwords, 162–163 program installation, 18 picture change, 164–165 rip with Media Player, 120–121 sharing and, 155 view files, 135 switch between, 158–159 Character Map, special symbols, 62–63 User Accounts window, 154–155 check boxes, dialog boxes, 26 Welcome screen, 4 circles (Paint), 91 Activate Windows screen, 12–13 click mouse, 8–9 activate Windows XP, 12–13 close button, 23 Add or Remove Programs close windows, 33 installation and, 19 color uninstall programs, 40–41 background, 253 address bar (Internet Explorer), 206 custom, 256–257 Address Book (Outlook Express), 226–227 color box (Paint) addresses, Web, 204, 208–209 color selection, 99 airbrush freehand drawing (Paint), 96 eraser, 101 All Programs menu, 22 introduction, 86 Appearances and Themes, Display Properties and, 250–251 replace color, 101 attachments to e-mail (Outlook Express), 230-231, 240–241 color fills (Paint), 97 audio, play in Media Player, 110 combo boxes automatic updates, 280–281 dialog boxes, 26 item selection, 29 command buttons, dialog boxes, 27 B compressed folders, extract files, 150–151 Background, 252–253 computer administrator account, 157 Backup or Restore Wizard, 286–289 configuration, startup and, 4 Backup program, 286–287 connections, Internet. -

Security Controls and Best Practices for Financial Institutions Content I
Security Controls and Best Practices for Financial Institutions Content I. Overview. 3 II. The Threat Landscape and Compliance . 4 III. Combating Compromised Credentials . 5 A. Password Security . 5 B. Enhanced MFA (EMFA). 6 C. Hardware Tokens (Business/Commercial Banking Only) . 6 IV. Combating Local Malicious Software and Phishing . 7 A. Trusteer’s Browser Security . 7 B. VeriSign Extended Validation Certificates . 7 C. RSA Fraud Shutdown . 7 D. Separation of Duty, Positive Pay, & Limits (Business/Commercial Banking Only). 7 E. Limits . 7 V. Alerting (Business Banking and Business Financial Services only) . 8 VI. Training & Best Practices . 8 VII. Action Plan . 10 VIII. Glossary . 11 Guidance Materials . 14 Additional Resources . 14 Overview The intent of this document is to inform Financial Institutions about the online fraud threats they currently face. For each threat we discuss, we will provide some basic guidance about an available control that could mitigate the threat. This guidance represents a starting point for improving security. Digital Insight strongly recommends that you review your current security plans and policies, make any updates necessary, and communicate improvements to your customers or members. The Threat Landscape and Compliance In order to commit online fraud, a fraudster simply needs to authenticate as the victim, using that victim’s online credentials. For environments that rely on Single Factor Authentication (something the user knows), the fraudster can coax this information from a real user through compelling On June 28, 2011, the phishing campaigns, key logging, or Man-in-the-Middle proxy attacks. FFIEC issued a Supplement to the Authentication in an Internet Banking For environments that have deployed Two Factor Authentication (something the user Environment guidance. -
| Independent Consultant Logo
| INDEPENDENT CONSULTANT LOGO PRIMARY LOGO PRIMARY TWO-TONE HEXAGON LOGO The Scentsy Independent Consultant logo can be used by Consultants on their personal printed materials and websites to promote their business. The space between the elements within the logo should not be modified. The logo should always appear upright, with clearance on either side and clearance on the top and bottom equal to the height of the lower case “S” character as it’s used in the sized logo (see example). SPECIAL NOTE: If you need a two colour option for this logo, use Pantone 522 to replace the 80% screen. Pantone 519 Pantone 519 — 80% C 60 M 100 Y 0 K 40 C 45 M 57 Y 23 K 6 #5c305e #8f7290 7/22/15 SCENTSY CONSULTANT STYLE GUIDE 1 | FONT - INDEPENDENT CONSULTANT LOGO TYPE The logo displays the company name in the Scentsy Spirit font, and the accompanying type in Knockout-HTF34-Junior Sumo. No other fonts should be used to alter Scentsy Spirit the look of the Scentsy Independent Consultant logo. 1234567890!@#$%^&*()_=+ ABCDEFGHIJKLMNOPQRSTUVWXYZ abcdefghijklmnopqrstuvwxyz Knockout-HTF34-JuniorSumo 1234567890!@#$%^&*()_=+ ABCDEFGHIJKLMNOPQRSTUVWXYZ abcdefghijklmnopqrstuvwxyz 7/22/15 SCENTSY CONSULTANT STYLE GUIDE 2 | INDEPENDENT CONSULTANT LOGO SECONDARY LOGO OPTIONS ONE-COLOUR HEXAGON LOGO ONE-COLOUR LOGO + STAR TRIO The following secondary logos may be used on specific Scentsy Family Store materials and by Scentsy Consultants to promote their personal business. The space between the elements within the secondary logos should not be modified. The logos should always appear upright, with clearance on either side and clearance on the top and bottom equal to the height of the lower case “S” character as it’s used in the sized logo. -

A Records, 244–245, 279 -A Switch in Nbtstat, 190 in Netstat, 186 AAS Deployment Package, 710 .Aas Extension, 712 Abstract
22_InsideWin_Index 13/3/03 9:50 AM Page 1269 Index A A records, 244–245, 279 ACEs (Access Control Entries) -a switch access masks in, 568–570 in Nbtstat, 190 command-line tools for, 572–576 in Netstat, 186 for cumulative permissions, 577 AAS deployment package, 710 for deny permissions, 578 .aas extension, 712 inheritance in, 579–580, 725–728 Abstract classes, 299–300 object ownership in, 572 Accelerated Graphics Port (AGP) adapters, 164 viewing and modifying, 570–571 Access Control Entries. See ACEs (Access ACKs in DHCP, 101–102 Control Entries) ACL Editor, 570, 723 Access control lists (ACLs) Advanced view in Active Directory security, 732–734 for inheritance, 578, 581 objects in, 339 for ownership, 572 in security descriptors, 559 for special permissions, 723–724 Access Control Settings window, 728 Edit view, 725–726 Access masks for permissions inheritance, 578 in ACEs, 568–570 blocking, 579 in DSOs, 733 settings for, 581 Access requests in Kerberos, 621 viewings, 582 Access rights. See also Permissions ACLs (access control lists) in Active Directory security in Active Directory security, 732–734 delegation, 729–732 objects in, 339 types of, 724–725 in security descriptors, 559 for group policies, 682 ACPI (Advanced Configuration and Power Access tokens Interface) contents of, 560–561 compatibility of, 23–28, 148–149 local, 559 kernel version for, 135 SIDs in, 559, 561, 581 for PnP,17, 147–149 ACCM (Asynchronous-Control- ACPIEnable option, 149 Character-Map), 1124 Activation Account domain upgrades, 496–498 in IA64, 130 BDC, 494–496 in installation, 49–50 PDC, 490–493 unattended setup scripts for, 95 Account lockout policies Active Directory, 238 in domain design, 429 bulk imports and exports in, 353–356 in password security, 593–594 DNS deployment in, 242–243 Account logons, auditing, 647 DNS integration in, 238–239 Account management, auditing, 511, 648 dynamic updates, 244–245 Accounts in domain migration. -

Draft NIST SP 800-118, Guide to Enterprise Password Management
RETIRED DRAFT April 1, 2016 The attached DRAFT document (provided here for historical purposes): Draft NIST Special Publication (SP) 800-118, Guide to Enterprise Password Management (posted for public comment on April 21, 2009) has been RETIRED. Information on other NIST cybersecurity publications and programs can be found at: http://csrc.nist.gov/. The following information was originally posted with the attached DRAFT document: Apr. 21, 2009 SP 800-118 DRAFT Guide to Enterprise Password Management NIST announces that Draft Special Publication (SP) 800-118, Guide to Enterprise Password Management, has been released for public comment. SP 800-118 is intended to help organizations understand and mitigate common threats against their character-based passwords. The guide focuses on topics such as defining password policy requirements and selecting centralized and local password management solutions. NIST requests comments on draft SP 800-118 by May 29, 2009. Please submit comments to 800-118comments @nist.gov with "Comments SP 800-118" in the subject line. Special Publication 800-118 (Draft) Guide to Enterprise Password Management (Draft) Recommendations of the National Institute of Standards and Technology Karen Scarfone Murugiah Souppaya NIST Special Publication 800-118 Guide to Enterprise Password (Draft) Management (Draft) Recommendations of the National Institute of Standards and Technology Karen Scarfone Murugiah Souppaya C O M P U T E R S E C U R I T Y Computer Security Division Information Technology Laboratory National Institute of Standards and Technology Gaithersburg, MD 20899-8930 April 2009 U.S. Department of Commerce Gary Locke, Secretary National Institute of Standards and Technology Dr.