“Network Monitoring and Management 2.0”
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
SQL Server 2017 on Linux Quick Start Guide | 4
SQL Server 2017 on Linux Quick Start Guide Contents Who should read this guide? ........................................................................................................................ 4 Getting started with SQL Server on Linux ..................................................................................................... 5 Why SQL Server with Linux? ..................................................................................................................... 5 Supported platforms ................................................................................................................................. 5 Architectural changes ............................................................................................................................... 6 Comparing SQL on Windows vs. Linux ...................................................................................................... 6 SQL Server installation on Linux ................................................................................................................ 8 Installing SQL Server packages .................................................................................................................. 8 Configuration capabilities ....................................................................................................................... 11 Licensing .................................................................................................................................................. 12 Administering and -

Latest Pgwatch2 Docker Image with Built-In Influxdb Metrics Storage DB
pgwatch2 Sep 30, 2021 Contents: 1 Introduction 1 1.1 Quick start with Docker.........................................1 1.2 Typical “pull” architecture........................................2 1.3 Typical “push” architecture.......................................2 2 Project background 5 2.1 Project feedback.............................................5 3 List of main features 7 4 Advanced features 9 4.1 Patroni support..............................................9 4.2 Log parsing................................................ 10 4.3 PgBouncer support............................................ 10 4.4 Pgpool-II support............................................. 11 4.5 Prometheus scraping........................................... 12 4.6 AWS / Azure / GCE support....................................... 12 5 Components 13 5.1 The metrics gathering daemon...................................... 13 5.2 Configuration store............................................ 13 5.3 Metrics storage DB............................................ 14 5.4 The Web UI............................................... 14 5.5 Metrics representation.......................................... 14 5.6 Component diagram........................................... 15 5.7 Component reuse............................................. 15 6 Installation options 17 6.1 Config DB based operation....................................... 17 6.2 File based operation........................................... 17 6.3 Ad-hoc mode............................................... 17 6.4 Prometheus -

Centralized Logging Implementation Guide Centralized Logging Implementation Guide
Centralized Logging Implementation Guide Centralized Logging Implementation Guide Centralized Logging: Implementation Guide Copyright © Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks and trade dress may not be used in connection with any product or service that is not Amazon's, in any manner that is likely to cause confusion among customers, or in any manner that disparages or discredits Amazon. All other trademarks not owned by Amazon are the property of their respective owners, who may or may not be affiliated with, connected to, or sponsored by Amazon. Centralized Logging Implementation Guide Table of Contents Welcome ........................................................................................................................................... 1 Cost .................................................................................................................................................. 2 Cost estimate example ............................................................................................................... 2 Architecture overview ......................................................................................................................... 4 Log ingestion ............................................................................................................................. 4 Log indexing .............................................................................................................................. 6 Visualization ............................................................................................................................. -

Grafana and Mysql Benefits and Challenges 2 About Me
Grafana and MySQL Benefits and Challenges 2 About me Philip Wernersbach Software Engineer Ingram Content Group https://github.com/philip-wernersbach https://www.linkedin.com/in/pwernersbach 3 • I work in Ingram Content Group’s Automated Print On Demand division • We have an automated process in which publishers (independent or corporate) request books via a website, and we automatically print, bind, and ship those books to them • This process involves lots of hardware devices and software components 4 The Problem 5 The Problem “How do we aggregate and track metrics from our hardware and software sources, and display those data points in a graph format to the end user?” à Grafana! 6 Which data store should we use with Grafana? ▸ Out of the box, Grafana supports Elasticsearch, Graphite, InfluxDB, KairosDB, OpenTSDB 7 Which data store should we use with Grafana? ▸ We compared the options and tried InfluxDB ▸ There were several sticking points with InfluxDB, both technical and organizational, that caused us to rule it out 8 Which data store should we use with Grafana? ▸ We already have a MySQL cluster deployed, System Administrators and Operations know how to manage it ▸ Decided to go with MySQL as a data store for Grafana 9 The Solution: Ingram Content’s Grafana-MySQL Integration 10 ▸ Written in Nim ▸ Emulates an InfluxDB server ▸ Connects to an existing The Integration MySQL server ▸ Protocol compatible with InfluxDB 0.9.3 ▸ Acts as a proxy that converts the InfluxDB protocol to the MySQL protocol and vice- versa 11 Grafana The Integration -

Monitoring Container Environment with Prometheus and Grafana
Matti Holopainen Monitoring Container Environment with Prometheus and Grafana Metropolia University of Applied Sciences Bachelor of Engineering Information and Communication Technology Bachelor’s Thesis 3.5.2021 Abstract Tekijä Matti Holopainen Otsikko Monitoring Container Environment with Prometheus and Grafana Sivumäärä Aika 50 sivua 3.5.2021 Tutkinto Insinööri (AMK) Tutkinto-ohjelma Tieto- ja viestintätekniikka Ammatillinen pääaine Ohjelmistotuotanto Ohjaajat Nina Simola, Projektipäällikkö Auvo Häkkinen, Yliopettaja Insinöörityön tavoitteena oli oppia pystyttämään monitorointijärjestelmä konttiympäristön re- surssien käytön seuraamista, monitorointia ja analysoimista varten. Tavoitteena oli helpot- taa monitorointijärjestelmän käyttöönottoa. Työ tehtiin käytettävien ohjelmistojen dokumen- taation ja käytännön tekemisellä opittujen asioiden pohjalta. Insinöörityön alussa käytiin läpi työssä käytettyjä teknologioita. Tämän jälkeen käytiin läpi monitorointi järjestelmän konfiguraatio ja käyttöönotto. Seuraavaksi tutustuttiin PromQL-ha- kukieleen, jonka jälkeen näytettiin kuinka pystyttää valvontamonitori ja hälytykset sähköpos- timuistutuksella. Työn lopussa käydään läpi kuinka monitorointijärjestelmässä saatua dataa analysoidaan ja mietitään miten monitorointijärjestelmää voisi parantaa. Keywords Monitorointi, Kontti, Prometheus, Grafana, Docker Abstract Author Matti Holopainen Title Monitoring Container Environment with Prometheus and Grafana Number of Pages Date 50 pages 3.5.2021 Degree Bachelor of Engineering Degree Programme Information -

Eventindex Monitoring
BigData tools for the monitoring of the ATLAS EventIndex Evgeny Alexandrov1, Andrei Kazymov1, Fedor Prokoshin2, on behalf of the ATLAS collaboration 1Joint Institute for Nuclear Research, Dubna, Russia. 2Centro Científico Tecnológico de Valparaíso-CCTVal, Universidad Técnica Federico Santa María. GRID Conference at JINR 12 September 2018 Introduction • The EventIndex is the complete catalogue of all ATLAS events, keeping the references to all files that contain a given event in any processing stage. • The ATLAS EventIndex collects event information from data both at CERN and Grid sites. • It uses the Hadoop system to store the results, and web services to access them. • Its successful operation depends on a number of different components. • Each component has completely different sets of parameters and states and requires a special approach. Monitoring Components Prodsys EIOracle ??? Event Picking Tests XML ORACLE? Old Monitoring System based on Kibana Disadvantages of Kibana Slow dashboard retrieving time: - for two days period: 15 seconds; - for 7 days period: 1 minute 30 seconds; - for a longer periods: it may take tens of minutes and eventually get stuck. Not very comfortable way of editing the dashboard’s page Grafana Grafana is one of the most popular packages for visualizing monitoring data. Uses modern technologies: - back-end is written using Go programming language; - front-end is written on typescript and uses angular approach. The following datasources are officially supported: Graphite InfluxDB MySQL Elasticsearch OpenTSDB Postgres CloudWatch Prometheus Microsoft SQL Server (MSSQL) InfluxDB InfluxDB is InfluxData's open source time series database designed to handle high write and query loads. Uses modern technologies: - it is written on GO; - It has the possibility of working in cluster mode; - availability of libraries for a large number of programming languages (Python, JavaScript, PHP, Haskell and others); - SQL-like query language, with which you can perform various operations with time series (merging, splitting). -

Experimental Methods for the Evaluation of Big Data Systems Abdulqawi Saif
Experimental Methods for the Evaluation of Big Data Systems Abdulqawi Saif To cite this version: Abdulqawi Saif. Experimental Methods for the Evaluation of Big Data Systems. Computer Science [cs]. Université de Lorraine, 2020. English. NNT : 2020LORR0001. tel-02499941 HAL Id: tel-02499941 https://hal.univ-lorraine.fr/tel-02499941 Submitted on 5 Mar 2020 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. AVERTISSEMENT Ce document est le fruit d'un long travail approuvé par le jury de soutenance et mis à disposition de l'ensemble de la communauté universitaire élargie. Il est soumis à la propriété intellectuelle de l'auteur. Ceci implique une obligation de citation et de référencement lors de l’utilisation de ce document. D'autre part, toute contrefaçon, plagiat, reproduction illicite encourt une poursuite pénale. Contact : [email protected] LIENS Code de la Propriété Intellectuelle. articles L 122. 4 Code de la Propriété Intellectuelle. articles L 335.2- L 335.10 http://www.cfcopies.com/V2/leg/leg_droi.php http://www.culture.gouv.fr/culture/infos-pratiques/droits/protection.htm -

Pentest-Report Prometheus 05.-06.2018 Cure53, Dr.-Ing
Dr.-Ing. Mario Heiderich, Cure53 Bielefelder Str. 14 D 10709 Berlin cure53.de · [email protected] Pentest-Report Prometheus 05.-06.2018 Cure53, Dr.-Ing. M. Heiderich, M. Wege, MSc. N. Krein, BSc. J. Hector, Dipl.-Ing. A. Inführ, J. Larsson Index Introduction Scope Test Methodology Part 1 (Manual Code Auditing) Part 2 (Code-Assisted Penetration Testing) Hardening Recommendations General Security Recommendations HTTP Security Headers Content Security Policy & Beyond Authentication / Authorization Non-Idempotent Request Protection Transport Security Clients/metrics endpoint API Endpoint Admin GUI Identified Vulnerabilities PRM-01-001 Web: Prometheus lifecycle killed with CSRF (Medium) PRM-01-003 Web: CORS header exposes API data to all origins (High) PRM-01-005 Server: Clients can cause Denial of Service via Gzip Bomb (Medium) Miscellaneous Issues PRM-01-002 Client: Clients leak Metrics data through unprotected endpoint (Low) PRM-01-004 Web: Parameters used insecurely in HTML templates (Low) Conclusions Cure53, Berlin · 06/11/18 1/18 Dr.-Ing. Mario Heiderich, Cure53 Bielefelder Str. 14 D 10709 Berlin cure53.de · [email protected] Introduction “An open-source monitoring system with a dimensional data model, flexible query language, efficient time series database and modern alerting approach.” From https://prometheus.io/ This report documents the findings of a security assessment targeting the Prometheus software compound and carried out by Cure53 in 2018. It should be noted that the project was sponsored by The Linux Foundation / Cloud Native Computing Foundation. In terms of the scope, the assignment entailed two main components as the Prometheus project was investigated through both a dedicated source code audit and comprehensive penetration testing. -

Virtualization/Containerization of the PNNL High Energy Physics Computing Infrastructure
Virtualization/Containerization of the PNNL High Energy Physics Computing Infrastructure Kevin Fox, David Cowley, Malachi Schram, Evan Felix, James Czebotar, Smith Gary Grid Services Deployed DIRAC Belle2DB Distributed Data Management REST Service System UI Service Gatekeeper Services Payload Service Many development and testing Squid Cache services Postgresql Relational Database Condor CE's FTS3 DIRAC SiteDirector CVMFS Stratum HTCondor cluster Zero Squid Cache One Leadership Class Facility CE's Authorization DIRAC SiteDirector Gums HPC Cluster VOMS Server with multiple VO's SE's BestMan2 Gridftp Backed by Lustre Note to the Sysadmins New methodology for system administration. Cloud Native focuses around what the user cares about most, not what we Sysadmins are used to caring about. Users care about services. Users do not care about machines providing service. Pets vs Cattle analogy. We must unlearn what we have learned. Try and separate pets and cattle to different pools of resource. Our Infrastructure Journey Individual machines Automated provisioning Virtual machines OpenStack Cloud Repo Mirrors Containers Kubernetes Infrastructure Deployed Kubernetes + Docker Engine Prometheus OpenStack + KVM Grafana Ceph CheckMK GitLab ElasticSearch Lustre 389-DS LoadBalancing/HA Cobbler PerfSonar NFS Metric/Log gathering is very important for system problem analysis Current tool stack includes CheckMK Grafana/Prometheus Kibana/ElasticSearch/LogShippers Kubernetes Load Balancers Give users a load balancer to talk to. Back it with multiple instances of the software making up of the service whenever possible. When not possible, make it very quick to redeploy. Deployment Flow Separate Build and Deploy steps. Kubernetes/Docker example: #Build > docker build . -t pnnlhep/condor-compute:2017-09-01 … > docker push pnnlhep/condor-compute:2017-09-01 … #Deploy > helm install --name ce0-compute condor-compute \ –set version=2017-09-01 .. -
Lumada Edge Version
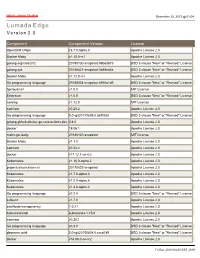
Hitachi - Inspire The Next December 20, 2019 @ 01:04 Lumada Edge V e r s i o n 3 . 0 Component Component Version License OpenShift Origin v3.7.0-alpha.0 Apache License 2.0 Docker Moby v1.10.0-rc1 Apache License 2.0 golang.org/x/oauth2 20190130-snapshot-99b60b75 BSD 3-clause "New" or "Revised" License golang sys 20180821-snapshot-3b58ed4a BSD 3-clause "New" or "Revised" License Docker Moby v1.12.0-rc1 Apache License 2.0 Go programming language 20180824-snapshot-4910a1d5 BSD 3-clause "New" or "Revised" License hpcloud-tail v1.0.0 MIT License Ethereum v1.5.0 BSD 3-clause "New" or "Revised" License zerolog v1.12.0 MIT License cadvisor v0.28.2 Apache License 2.0 Go programming language 0.0~git20170629.0.5ef0053 BSD 3-clause "New" or "Revised" License golang-github-docker-go-connections-dev 0.4.0 Apache License 2.0 docker 18.06.1 Apache License 2.0 mattn-go-isatty 20180120-snapshot MIT License Docker Moby v1.1.0 Apache License 2.0 cadvisor v0.23.4 Apache License 2.0 docker v17.12.1-ce-rc2 Apache License 2.0 Kubernetes v1.15.0-alpha.2 Apache License 2.0 projectcalico/calico-cni 20170522-snapshot Apache License 2.0 Kubernetes v1.7.0-alpha.3 Apache License 2.0 Kubernetes v1.2.0-alpha.6 Apache License 2.0 Kubernetes v1.4.0-alpha.2 Apache License 2.0 Go programming language v0.2.0 BSD 3-clause "New" or "Revised" License kubevirt v1.7.0 Apache License 2.0 certificate-transparency 1.0.21 Apache License 2.0 kubernetes/api kubernetes-1.15.0 Apache License 2.0 cadvisor v0.28.1 Apache License 2.0 Go programming language v0.3.0 BSD 3-clause "New" or "Revised" -

Monitoring with Influxdb and Grafana
Monitoring with InfluxDB and Grafana Andrew Lahiff STFC RAL ! HEPiX 2015 Fall Workshop, BNL Introduction Monitoring at RAL • Like many (most?) sites, we use Ganglia • have ~89000 individual metrics • What’s wrong with Ganglia? Problems with ganglia • Plots look very dated Problems with ganglia • Difficult & time-consuming to make custom plots • currently use long, complex, messy Perl scripts • e.g. HTCondor monitoring > 2000 lines Problems with ganglia • Difficult & time-consuming to make custom plots • Ganglia UI for making customised plots is restricted & doesn’t give good results Problems with ganglia • Ganglia server has demanding host requirements • e.g. we store all rrds in a RAM disk • have problems if trying to use a VM • Doesn’t handle dynamic resources well • Occasional problems with gmond using too much memory, affecting other processes on machines • Not really suitable for Ceph monitoring A possible alternative • InfluxDB + Grafana • InfluxDB is a time-series database • Grafana is a metrics dashboard • originally a fork of Kibana • can make plots of data from InfluxDB, Graphite, others… • Very easy to make (nice) plots • Easy to install InfluxDB • Time series database written in Go • No external dependencies • SQL-like query language • Distributed • can be run as a single node • can be run as a cluster for redundancy & performance (not suitable for production use yet) • Data can be written in using REST, or an API (e.g. Python) • or from collectd or graphite InfluxDB • Data organised by time series, grouped together into databases • Time series have zero to many points • Each point consists of: • time - the timestamp • a measurement (e.g. -

(PDF) What Can Cloud Native Do for Csps?
What Can Cloud Native Do for CSPs? Cloud Native Can Improve…. Development Cloud native is a way of approaching the development and deployment of applications in such a way that takes account of the characteristics and nature of the cloud—resulting in processes and workflows that fully take advantage of the platform. Operations Cloud native is an approach to building and running software applications that exploits the advantages of the cloud computing delivery model. Cloud-native is about how applications are created and deployed, not where. Infrastructure Cloud native platforms available “as a service” in the cloud can accommodate hybrid and multi-cloud environments. What are Cloud Native Core Concepts? Continuous Integration DevSecOps Microservices Containers and Deployment Not My Problem Release Once Every Tightly Coupled Directly Ported to a VM Separate tools, varied 6 Months Components Monolithic application incentives, opaque process More bugs in production Slow deployment cycles unable to leverage modern waiting on integrated tests cloud tools teams Shared Responsibility Release Early Loosely Coupled Packaged for Containers Common incentives, tools, and Often Components Focus on business process and culture Higher quality of code Automated deploy without software by leveraging waiting on individual the platform ecosystem components What are the Benefits of Cloud Native? Business Optimization Microservices architecture enables flexibility, agility, and reuse across various platforms. CAPEX and OPEX Reduction Service-based architecture allows integration with the public Cloud to handle overload capacity, offer new services with less development, and take advantage of other 3rd party services such as analytics, machine learning, and artificial intelligence. Service Agility Common services can be shared by all network functions deployed on the Cloud-Native Environment (CNE).