(PDF) What Can Cloud Native Do for Csps?
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Migration Toward Safer, Secure Data Management
Cloud Database Trend Report Migration toward safer, secure data management BROUGHT TO YOU IN PARTNERSHIP WITH Table of Contents Highlights and Introduction 3 BY MELISSA HABIT Key Research Findings 4 BY MATT LEGER Leaders in Cloud Database 11 BY LINDSAY SMITH Ensuring SQL Server High Availability in the Cloud 16 BY DAVE BERMINGHAM Data Safety in Cloud-Based Databases 21 BY GRANT FRITCHEY 28 Diving Deeper Into Cloud Databases To sponsor a Trend Report: Call: (919) 678-0300 Email: [email protected] DZONE TREND REPORT: CLOUD DATABASES PAGE 2 Highlights and Introduction By Melissa Habit, Publications Manager at DZone Trends in cloud data storage continue to accelerate at a rapid pace. Now more than ever, organizations must evaluate their current and future data storage needs to find solutions that align with business goals. While cloud databases are relatively new to the scene, they show tremendous prospect in securing and managing data. In selecting our topic for this Trend Report, we found the amount of promise and advancement in the space to be unparalleled. This report highlights DZone’s original research on cloud databases and contributions from the community, as well as introduces new offerings within DZone Trend Reports. While you may know her as your friendly Java Zone copy editor, Lindsay Smith has stepped into the role of DZone’s Publications Content Manager. Among many new endeavors, she’s spearheading our new strategy for Executive Insights — a series we’ve titled, “Leaders in Tech,” which serves to complement our original research. The series focuses on the viewpoints of industry frontrunners, tech evangelists, and DZone members who share their insights into research findings and outlooks for the future. -

Department of Defense Enterprise Devsecops Initiative
Headquarters U.S. Air Force I n t e g r i t y - S e r v i c e - E x c e l l e n c e How did the Department of Defense move to Kubernetes and Istio? Mr. Nicolas Chaillan Chief Software Officer, U.S. Air Force Co-Lead, DoD Enterprise DevSecOps Initiative V2.5 – UNCLASSFIED Must Adapt to Challenges Must Rapidly Adapt To Challenges I n t e g r i t y - S e r v i c e - E x c e l l e n c e 2 Must Adapt to Challenges Work as a Team! Must Adapt To Challenges I n t e g r i t y - S e r v i c e - E x c e l l e n c e 3 Must Adapt to Challenges Work as a Team! A Large Team! Must Adapt To Challenges I n t e g r i t y - S e r v i c e - E x c e l l e n c e 4 Must Adapt to Challenges With Various TechnologiesWork as a Team! A Large Team! Must Adapt To Challenges I n t e g r i t y - S e r v i c e - E x c e l l e n c e 5 Must Adapt to Challenges With Various Technologies Work as a Team! A Large Team! Must AdaptBring To Challenges It With Us! I n t e g r i t y - S e r v i c e - E x c e l l e n c e 6 Must Adapt to Challenges With Various Technologies Work as a Team! Even To Space! A Large Team! Must AdaptBring To Challenges It With Us! I n t e g r i t y - S e r v i c e - E x c e l l e n c e 7 Must Adapt to Challenges With Various Technologies Work as a Team! To Space! A Large Team! MustWith Adapt a FewBring To Sensors! Challenges It With Us! I n t e g r i t y - S e r v i c e - E x c e l l e n c e 8 With Their Help! Must Adapt to Challenges With Various Technologies Work as a Team! To Space! A Large Team! MustWith Adapt a FewBring To Sensors! Challenges It With Us! I n t e g r i t y - S e r v i c e - E x c e l l e n c e 9 What is the DoD Enterprise DevSecOps Initiative? Joint Program with OUSD(A&S), DoD CIO, U.S. -

Monitoring Container Environment with Prometheus and Grafana
Matti Holopainen Monitoring Container Environment with Prometheus and Grafana Metropolia University of Applied Sciences Bachelor of Engineering Information and Communication Technology Bachelor’s Thesis 3.5.2021 Abstract Tekijä Matti Holopainen Otsikko Monitoring Container Environment with Prometheus and Grafana Sivumäärä Aika 50 sivua 3.5.2021 Tutkinto Insinööri (AMK) Tutkinto-ohjelma Tieto- ja viestintätekniikka Ammatillinen pääaine Ohjelmistotuotanto Ohjaajat Nina Simola, Projektipäällikkö Auvo Häkkinen, Yliopettaja Insinöörityön tavoitteena oli oppia pystyttämään monitorointijärjestelmä konttiympäristön re- surssien käytön seuraamista, monitorointia ja analysoimista varten. Tavoitteena oli helpot- taa monitorointijärjestelmän käyttöönottoa. Työ tehtiin käytettävien ohjelmistojen dokumen- taation ja käytännön tekemisellä opittujen asioiden pohjalta. Insinöörityön alussa käytiin läpi työssä käytettyjä teknologioita. Tämän jälkeen käytiin läpi monitorointi järjestelmän konfiguraatio ja käyttöönotto. Seuraavaksi tutustuttiin PromQL-ha- kukieleen, jonka jälkeen näytettiin kuinka pystyttää valvontamonitori ja hälytykset sähköpos- timuistutuksella. Työn lopussa käydään läpi kuinka monitorointijärjestelmässä saatua dataa analysoidaan ja mietitään miten monitorointijärjestelmää voisi parantaa. Keywords Monitorointi, Kontti, Prometheus, Grafana, Docker Abstract Author Matti Holopainen Title Monitoring Container Environment with Prometheus and Grafana Number of Pages Date 50 pages 3.5.2021 Degree Bachelor of Engineering Degree Programme Information -

Experimental Methods for the Evaluation of Big Data Systems Abdulqawi Saif
Experimental Methods for the Evaluation of Big Data Systems Abdulqawi Saif To cite this version: Abdulqawi Saif. Experimental Methods for the Evaluation of Big Data Systems. Computer Science [cs]. Université de Lorraine, 2020. English. NNT : 2020LORR0001. tel-02499941 HAL Id: tel-02499941 https://hal.univ-lorraine.fr/tel-02499941 Submitted on 5 Mar 2020 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. AVERTISSEMENT Ce document est le fruit d'un long travail approuvé par le jury de soutenance et mis à disposition de l'ensemble de la communauté universitaire élargie. Il est soumis à la propriété intellectuelle de l'auteur. Ceci implique une obligation de citation et de référencement lors de l’utilisation de ce document. D'autre part, toute contrefaçon, plagiat, reproduction illicite encourt une poursuite pénale. Contact : [email protected] LIENS Code de la Propriété Intellectuelle. articles L 122. 4 Code de la Propriété Intellectuelle. articles L 335.2- L 335.10 http://www.cfcopies.com/V2/leg/leg_droi.php http://www.culture.gouv.fr/culture/infos-pratiques/droits/protection.htm -

The Evolution to Cloud-Native Nfv: Early Adoption Brings Benefits with a Flexible Approach
THE EVOLUTION TO CLOUD-NATIVE NFV: EARLY ADOPTION BRINGS BENEFITS WITH A FLEXIBLE APPROACH NOVEMBER 2017 Caroline Chappell Ref: 2011421-463 analysysmason.com The evolution to cloud-native NFV: Early adoption brings benefits with a flexible approach | i Contents 1. Executive summary 1 2. What is cloud-native network virtualisation? 2 Drivers for the cloud-native network 2 The IT cloud community has pioneered cloud-native computing 3 Telco industry progress towards cloud-native NFV 4 Cloud native is an urgent goal, but most vendors are moving slowly towards it 5 3. Key principles of cloud-native computing in a telco context 6 CSPs should evaluate VNFs from three perspectives to ensure they are future-proofed for cloud-native computing 6 Designing VNFs for the cloud 7 Cloud-native deployment of VNFs 8 Cloud-native automation and management of VNFs 9 4. Cloud-native network use cases and migration strategy 11 When should cloud-native computing be applied? 11 Applying cloud-native computing: mitigating organisational and operational impacts 11 5. Huawei’s cloud-native core network solutions 12 6. Conclusion 13 About the author 15 About Analysys Mason 16 Research from Analysys Mason 17 Consulting from Analysys Mason 18 List of figures Figure 2.1: Drivers for applying cloud-native computing to the network ........................................................ 2 Figure 2.2: The evolution of cloud-native computing in the IT industry .......................................................... 3 Figure 2.3: How containers differ from virtual machines ................................................................................. 4 Figure 2.4: Progress towards cloud-native VNFs ............................................................................................. 6 Figure 3.1: Vertical and horizontal decomposition of VNFs ............................................................................ 8 Figure 3.2: Deployment options in different NFV data centres ....................................................................... -

Pentest-Report Prometheus 05.-06.2018 Cure53, Dr.-Ing
Dr.-Ing. Mario Heiderich, Cure53 Bielefelder Str. 14 D 10709 Berlin cure53.de · [email protected] Pentest-Report Prometheus 05.-06.2018 Cure53, Dr.-Ing. M. Heiderich, M. Wege, MSc. N. Krein, BSc. J. Hector, Dipl.-Ing. A. Inführ, J. Larsson Index Introduction Scope Test Methodology Part 1 (Manual Code Auditing) Part 2 (Code-Assisted Penetration Testing) Hardening Recommendations General Security Recommendations HTTP Security Headers Content Security Policy & Beyond Authentication / Authorization Non-Idempotent Request Protection Transport Security Clients/metrics endpoint API Endpoint Admin GUI Identified Vulnerabilities PRM-01-001 Web: Prometheus lifecycle killed with CSRF (Medium) PRM-01-003 Web: CORS header exposes API data to all origins (High) PRM-01-005 Server: Clients can cause Denial of Service via Gzip Bomb (Medium) Miscellaneous Issues PRM-01-002 Client: Clients leak Metrics data through unprotected endpoint (Low) PRM-01-004 Web: Parameters used insecurely in HTML templates (Low) Conclusions Cure53, Berlin · 06/11/18 1/18 Dr.-Ing. Mario Heiderich, Cure53 Bielefelder Str. 14 D 10709 Berlin cure53.de · [email protected] Introduction “An open-source monitoring system with a dimensional data model, flexible query language, efficient time series database and modern alerting approach.” From https://prometheus.io/ This report documents the findings of a security assessment targeting the Prometheus software compound and carried out by Cure53 in 2018. It should be noted that the project was sponsored by The Linux Foundation / Cloud Native Computing Foundation. In terms of the scope, the assignment entailed two main components as the Prometheus project was investigated through both a dedicated source code audit and comprehensive penetration testing. -

State of Cloud Native Development Q4-2019
THE LATEST TRENDS FROM OUR Q4 2019 SURVEY OF 17,000+ DEVELOPERS Supported by TO BE PUBLISHED AUGUST 2020 We help the world understand developers We survey 40,000+ developers annually – across web, mobile, IoT, cloud, Machine Learning, AR/VR, games and desktop – to help companies understand who developers are, what they buy and where they are going next. WHO DEVELOPERS ARE WHAT THEY BUY WHERE THEY ARE GOING Developer population sizing Why developers are adopting Emerging platforms – augmented & Developer segmentation competitor products – and how you virtual reality, machine learning can fix that Trusted by the leading tech brands and media TABLE OF CONTENTS Key findings 1. Introduction A. Defining cloud native computing B. Market size C. Usage of cloud native technologies across regions 2. Where are cloud native developers running their code? A. Infrastructure usage by cloud native developers and non-cloud native developers B. Cloud native developers and their infrastructure usage by verticals 3. Usage of cloud service vendors A. Usage of cloud service vendors by cloud native, non-cloud native, and other developers B. Private cloud usage by cloud native and non-cloud native developers 4. Awareness and use of Kubernetes A. Kubernetes and containers: usage and awareness among backend developers B. Overlap of Kubernetes and CaaS users C. Solutions used by developers not indicating they use Kubernetes 5. Serverless usage and awareness A. Usage and awareness of serverless solutions B. Usage of serverless solutions by role Methodology License terms KEY INSIGHTS FOR THE CLOUD NATIVE COMPUTING FOUNDATION THE STATE OF CLOUD NATIVE DEVELOPMENT Q4 2019 4 KEY FINDINGS • 6.5 million cloud native developers exist around the globe, 1.8 million more than in Q2 2019. -

Virtualization/Containerization of the PNNL High Energy Physics Computing Infrastructure
Virtualization/Containerization of the PNNL High Energy Physics Computing Infrastructure Kevin Fox, David Cowley, Malachi Schram, Evan Felix, James Czebotar, Smith Gary Grid Services Deployed DIRAC Belle2DB Distributed Data Management REST Service System UI Service Gatekeeper Services Payload Service Many development and testing Squid Cache services Postgresql Relational Database Condor CE's FTS3 DIRAC SiteDirector CVMFS Stratum HTCondor cluster Zero Squid Cache One Leadership Class Facility CE's Authorization DIRAC SiteDirector Gums HPC Cluster VOMS Server with multiple VO's SE's BestMan2 Gridftp Backed by Lustre Note to the Sysadmins New methodology for system administration. Cloud Native focuses around what the user cares about most, not what we Sysadmins are used to caring about. Users care about services. Users do not care about machines providing service. Pets vs Cattle analogy. We must unlearn what we have learned. Try and separate pets and cattle to different pools of resource. Our Infrastructure Journey Individual machines Automated provisioning Virtual machines OpenStack Cloud Repo Mirrors Containers Kubernetes Infrastructure Deployed Kubernetes + Docker Engine Prometheus OpenStack + KVM Grafana Ceph CheckMK GitLab ElasticSearch Lustre 389-DS LoadBalancing/HA Cobbler PerfSonar NFS Metric/Log gathering is very important for system problem analysis Current tool stack includes CheckMK Grafana/Prometheus Kibana/ElasticSearch/LogShippers Kubernetes Load Balancers Give users a load balancer to talk to. Back it with multiple instances of the software making up of the service whenever possible. When not possible, make it very quick to redeploy. Deployment Flow Separate Build and Deploy steps. Kubernetes/Docker example: #Build > docker build . -t pnnlhep/condor-compute:2017-09-01 … > docker push pnnlhep/condor-compute:2017-09-01 … #Deploy > helm install --name ce0-compute condor-compute \ –set version=2017-09-01 .. -
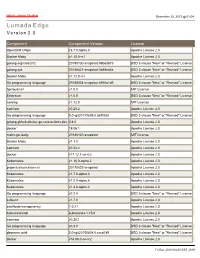
Lumada Edge Version
Hitachi - Inspire The Next December 20, 2019 @ 01:04 Lumada Edge V e r s i o n 3 . 0 Component Component Version License OpenShift Origin v3.7.0-alpha.0 Apache License 2.0 Docker Moby v1.10.0-rc1 Apache License 2.0 golang.org/x/oauth2 20190130-snapshot-99b60b75 BSD 3-clause "New" or "Revised" License golang sys 20180821-snapshot-3b58ed4a BSD 3-clause "New" or "Revised" License Docker Moby v1.12.0-rc1 Apache License 2.0 Go programming language 20180824-snapshot-4910a1d5 BSD 3-clause "New" or "Revised" License hpcloud-tail v1.0.0 MIT License Ethereum v1.5.0 BSD 3-clause "New" or "Revised" License zerolog v1.12.0 MIT License cadvisor v0.28.2 Apache License 2.0 Go programming language 0.0~git20170629.0.5ef0053 BSD 3-clause "New" or "Revised" License golang-github-docker-go-connections-dev 0.4.0 Apache License 2.0 docker 18.06.1 Apache License 2.0 mattn-go-isatty 20180120-snapshot MIT License Docker Moby v1.1.0 Apache License 2.0 cadvisor v0.23.4 Apache License 2.0 docker v17.12.1-ce-rc2 Apache License 2.0 Kubernetes v1.15.0-alpha.2 Apache License 2.0 projectcalico/calico-cni 20170522-snapshot Apache License 2.0 Kubernetes v1.7.0-alpha.3 Apache License 2.0 Kubernetes v1.2.0-alpha.6 Apache License 2.0 Kubernetes v1.4.0-alpha.2 Apache License 2.0 Go programming language v0.2.0 BSD 3-clause "New" or "Revised" License kubevirt v1.7.0 Apache License 2.0 certificate-transparency 1.0.21 Apache License 2.0 kubernetes/api kubernetes-1.15.0 Apache License 2.0 cadvisor v0.28.1 Apache License 2.0 Go programming language v0.3.0 BSD 3-clause "New" or "Revised" -

Why to Cloud Native Karthik Gaekwad @Iteration1 Principal Engineer, Oracle Cloud Innotech OKC Hello
Why to Cloud Native Karthik Gaekwad @iteration1 Principal Engineer, Oracle Cloud Innotech OKC Hello • I’m Karthik Gaekwad • NOT a DBA • https://cloudnative.oracle.com/ • Cloud Native evangelist at Oracle Cloud • Previous: developer on the Oracle Managed @iteration1 Kubernetes Team. Hello • Been in Industry 15 years. • In general, I like building stuff with friends. • A maintainer for Gauntlt- Open source security scanner. • Love Teaching and building community. • Run Devopsdays Austin, Container Days, Cloud Austin. • Chair All Day Devops Cloud Native track. • LinkedIn Learning Author for Learning Kubernetes (and more). Need an OCI Trial Account? http://bitly.com/ocicloud My questions for you.. Agenda • What is cloud native? • Where are we today in the cloud native world? • The Cloud Native ecosystem. • Cloud Native adoption. • Challenges. What is Cloud Native? What is Cloud Native? “A new computing paradigm that is optimized for modern distributed systems environments capable of scaling to tens of thousands of self healing multi-tenant nodes” -Cloud Native Computing Foundation Pillars of Cloud Native Continuous Containers Delivery Devops Microservices Pillars of Cloud Native: Devops “DevOps is the practice of operations and development engineers participating together in the entire service lifecycle, from design through the development process to production support.” -The Agile Admin blog https://theagileadmin.com/what-is-devops/ Pillars of Cloud Native: Devops • Generally based on principles of CALMS • Based on the ideas of Automation, -

Improving Resource Efficiency in Virtualized Datacenters by Marcelo Amaral
“Virtualization is a mechanism to abstract the operating system, hard are and system resources, hiding from the application the complexity of the underlying resources"“ Improving Resource Efficiency in Virtualized Datacenters By Marcelo Amaral Advisors: David Carrera Jordà Polo Le fils de l'homme (The Son of Man) René Magritte (1898-1967) 1964. Oil on canvas. 116 cm x 89 cm “We desire to see what#s hi en be"ind the visi$le.% A dissertation submitted in partial fulfilment of the requirements for the degree of: Doctor of Philosophy at Universitat Politècnica de Catalunya Barcelona (Spain) 2019 Technical University of Catalunya – BarcelonaTech (UPC) "Everything we see hides another thing, we always want to see what is hidden by what we see. There is an interest in that which is hidden and which the visible does not show us. This interest can take the form of a quite intense feeling, a sort of conflict, one might say, between the visible that is hidden and the visible that is present." — Rene Magritte, 1965 Marcelo Carneiro do Amaral: Improving Resource Efficiency in Virtualized Datacenters, Topology- Aware Resource Provision Techniques, © January 2019 Dedicated to my loving wife. Dedicated also in memory of my mother. 1948 – 2010 ABSTRACT Modern applications demand resources at an unprecedented level and, therefore, dat- acenters are required to scale efficiently when more resources are added to the infras- tructure, increasing their efficiency and flexibility to manage workloads. A technology that confers advantages towards resource-efficiency is virtualization. A virtualized data center offers higher management flexibility and at the same time increases resource uti- lization by allowing workload collocation and isolation. -

Why Use Containers and Cloud-Native Functions Anyway? 2
WHITE PAPER Communications Service Providers Cloud-Native Network Functions Why Use Containers and Cloud- Native Functions Anyway? Learn how to correctly implement cloud-native network functions for 5G Executive Overview The telecommunications industry is at an inflection point. Communications service providers (CoSPs) need to adopt new strategies to successfully monetize their networks as 5G deployments transition from nebulous plans to real-world projects. The traditional CoSP approach, with monolithic virtualized network functions (VNFs) that take years to deploy or upgrade cannot keep pace with the new 5G landscape. The nature of the 5G core network—dynamic, configurable and agile— requires a cloud-native approach that uses web-scale, containerized network functions (CNFs) that are resilient, decomposed into microservices and, as much as Authors possible, open source. Muthurajan Jayakumar (M Jay) As 5G use cases multiply, experts predict the number of services will quadruple Cloud-Native Solution Architect & those delivered during the last 40 years1. Without making a smooth and successful Platform Software Engineer, Network transition to a cloud-native 5G core network, CoSPs risk losing customers to other Product Group, Intel players, such as cloud service providers. Table of Contents Intel is working with the telecommunications industry to deliver software-defined networking (SDN) and automation powered by Intel® hardware and software. The Executive Overview . 1 Intel® Network Builders is an ecosystem of independent software vendors (ISVs), Introduction . 1 operating system vendors (OSVs), original equipment manufacturers (OEMs), telecom equipment manufacturers (TEMs), system integrators and CoSPs coming Why CoSPs should go cloud native . 2 together to ease and accelerate the adoption of 5G.