Working with ZIP Files
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

ACS – the Archival Cytometry Standard
http://flowcyt.sf.net/acs/latest.pdf ACS – the Archival Cytometry Standard Archival Cytometry Standard ACS International Society for Advancement of Cytometry Candidate Recommendation DRAFT Document Status The Archival Cytometry Standard (ACS) has undergone several revisions since its initial development in June 2007. The current proposal is an ISAC Candidate Recommendation Draft. It is assumed, however not guaranteed, that significant features and design aspects will remain unchanged for the final version of the Recommendation. This specification has been formally tested to comply with the W3C XML schema version 1.0 specification but no position is taken with respect to whether a particular software implementing this specification performs according to medical or other valid regulations. The work may be used under the terms of the Creative Commons Attribution-ShareAlike 3.0 Unported license. You are free to share (copy, distribute and transmit), and adapt the work under the conditions specified at http://creativecommons.org/licenses/by-sa/3.0/legalcode. Disclaimer of Liability The International Society for Advancement of Cytometry (ISAC) disclaims liability for any injury, harm, or other damage of any nature whatsoever, to persons or property, whether direct, indirect, consequential or compensatory, directly or indirectly resulting from publication, use of, or reliance on this Specification, and users of this Specification, as a condition of use, forever release ISAC from such liability and waive all claims against ISAC that may in any manner arise out of such liability. ISAC further disclaims all warranties, whether express, implied or statutory, and makes no assurances as to the accuracy or completeness of any information published in the Specification. -

Pack, Encrypt, Authenticate Document Revision: 2021 05 02
PEA Pack, Encrypt, Authenticate Document revision: 2021 05 02 Author: Giorgio Tani Translation: Giorgio Tani This document refers to: PEA file format specification version 1 revision 3 (1.3); PEA file format specification version 2.0; PEA 1.01 executable implementation; Present documentation is released under GNU GFDL License. PEA executable implementation is released under GNU LGPL License; please note that all units provided by the Author are released under LGPL, while Wolfgang Ehrhardt’s crypto library units used in PEA are released under zlib/libpng License. PEA file format and PCOMPRESS specifications are hereby released under PUBLIC DOMAIN: the Author neither has, nor is aware of, any patents or pending patents relevant to this technology and do not intend to apply for any patents covering it. As far as the Author knows, PEA file format in all of it’s parts is free and unencumbered for all uses. Pea is on PeaZip project official site: https://peazip.github.io , https://peazip.org , and https://peazip.sourceforge.io For more information about the licenses: GNU GFDL License, see http://www.gnu.org/licenses/fdl.txt GNU LGPL License, see http://www.gnu.org/licenses/lgpl.txt 1 Content: Section 1: PEA file format ..3 Description ..3 PEA 1.3 file format details ..5 Differences between 1.3 and older revisions ..5 PEA 2.0 file format details ..7 PEA file format’s and implementation’s limitations ..8 PCOMPRESS compression scheme ..9 Algorithms used in PEA format ..9 PEA security model .10 Cryptanalysis of PEA format .12 Data recovery from -

Metadefender Core V4.12.2
MetaDefender Core v4.12.2 © 2018 OPSWAT, Inc. All rights reserved. OPSWAT®, MetadefenderTM and the OPSWAT logo are trademarks of OPSWAT, Inc. All other trademarks, trade names, service marks, service names, and images mentioned and/or used herein belong to their respective owners. Table of Contents About This Guide 13 Key Features of Metadefender Core 14 1. Quick Start with Metadefender Core 15 1.1. Installation 15 Operating system invariant initial steps 15 Basic setup 16 1.1.1. Configuration wizard 16 1.2. License Activation 21 1.3. Scan Files with Metadefender Core 21 2. Installing or Upgrading Metadefender Core 22 2.1. Recommended System Requirements 22 System Requirements For Server 22 Browser Requirements for the Metadefender Core Management Console 24 2.2. Installing Metadefender 25 Installation 25 Installation notes 25 2.2.1. Installing Metadefender Core using command line 26 2.2.2. Installing Metadefender Core using the Install Wizard 27 2.3. Upgrading MetaDefender Core 27 Upgrading from MetaDefender Core 3.x 27 Upgrading from MetaDefender Core 4.x 28 2.4. Metadefender Core Licensing 28 2.4.1. Activating Metadefender Licenses 28 2.4.2. Checking Your Metadefender Core License 35 2.5. Performance and Load Estimation 36 What to know before reading the results: Some factors that affect performance 36 How test results are calculated 37 Test Reports 37 Performance Report - Multi-Scanning On Linux 37 Performance Report - Multi-Scanning On Windows 41 2.6. Special installation options 46 Use RAMDISK for the tempdirectory 46 3. Configuring Metadefender Core 50 3.1. Management Console 50 3.2. -

Steganography and Vulnerabilities in Popular Archives Formats.| Nyxengine Nyx.Reversinglabs.Com
Hiding in the Familiar: Steganography and Vulnerabilities in Popular Archives Formats.| NyxEngine nyx.reversinglabs.com Contents Introduction to NyxEngine ............................................................................................................................ 3 Introduction to ZIP file format ...................................................................................................................... 4 Introduction to steganography in ZIP archives ............................................................................................. 5 Steganography and file malformation security impacts ............................................................................... 8 References and tools .................................................................................................................................... 9 2 Introduction to NyxEngine Steganography1 is the art and science of writing hidden messages in such a way that no one, apart from the sender and intended recipient, suspects the existence of the message, a form of security through obscurity. When it comes to digital steganography no stone should be left unturned in the search for viable hidden data. Although digital steganography is commonly used to hide data inside multimedia files, a similar approach can be used to hide data in archives as well. Steganography imposes the following data hiding rule: Data must be hidden in such a fashion that the user has no clue about the hidden message or file's existence. This can be achieved by -
![User Commands GZIP ( 1 ) Gzip, Gunzip, Gzcat – Compress Or Expand Files Gzip [ –Acdfhllnnrtvv19 ] [–S Suffix] [ Name ... ]](https://docslib.b-cdn.net/cover/1609/user-commands-gzip-1-gzip-gunzip-gzcat-compress-or-expand-files-gzip-acdfhllnnrtvv19-s-suffix-name-561609.webp)
User Commands GZIP ( 1 ) Gzip, Gunzip, Gzcat – Compress Or Expand Files Gzip [ –Acdfhllnnrtvv19 ] [–S Suffix] [ Name ... ]
User Commands GZIP ( 1 ) NAME gzip, gunzip, gzcat – compress or expand files SYNOPSIS gzip [–acdfhlLnNrtvV19 ] [– S suffix] [ name ... ] gunzip [–acfhlLnNrtvV ] [– S suffix] [ name ... ] gzcat [–fhLV ] [ name ... ] DESCRIPTION Gzip reduces the size of the named files using Lempel-Ziv coding (LZ77). Whenever possible, each file is replaced by one with the extension .gz, while keeping the same ownership modes, access and modification times. (The default extension is – gz for VMS, z for MSDOS, OS/2 FAT, Windows NT FAT and Atari.) If no files are specified, or if a file name is "-", the standard input is compressed to the standard output. Gzip will only attempt to compress regular files. In particular, it will ignore symbolic links. If the compressed file name is too long for its file system, gzip truncates it. Gzip attempts to truncate only the parts of the file name longer than 3 characters. (A part is delimited by dots.) If the name con- sists of small parts only, the longest parts are truncated. For example, if file names are limited to 14 characters, gzip.msdos.exe is compressed to gzi.msd.exe.gz. Names are not truncated on systems which do not have a limit on file name length. By default, gzip keeps the original file name and timestamp in the compressed file. These are used when decompressing the file with the – N option. This is useful when the compressed file name was truncated or when the time stamp was not preserved after a file transfer. Compressed files can be restored to their original form using gzip -d or gunzip or gzcat. -

An Analysis of XML Compression Efficiency
An Analysis of XML Compression Efficiency Christopher J. Augeri1 Barry E. Mullins1 Leemon C. Baird III Dursun A. Bulutoglu2 Rusty O. Baldwin1 1Department of Electrical and Computer Engineering Department of Computer Science 2Department of Mathematics and Statistics United States Air Force Academy (USAFA) Air Force Institute of Technology (AFIT) USAFA, Colorado Springs, CO Wright Patterson Air Force Base, Dayton, OH {chris.augeri, barry.mullins}@afit.edu [email protected] {dursun.bulutoglu, rusty.baldwin}@afit.edu ABSTRACT We expand previous XML compression studies [9, 26, 34, 47] by XML simplifies data exchange among heterogeneous computers, proposing the XML file corpus and a combined efficiency metric. but it is notoriously verbose and has spawned the development of The corpus was assembled using guidelines given by developers many XML-specific compressors and binary formats. We present of the Canterbury corpus [3], files often used to assess compressor an XML test corpus and a combined efficiency metric integrating performance. The efficiency metric combines execution speed compression ratio and execution speed. We use this corpus and and compression ratio, enabling simultaneous assessment of these linear regression to assess 14 general-purpose and XML-specific metrics, versus prioritizing one metric over the other. We analyze compressors relative to the proposed metric. We also identify key collected metrics using linear regression models (ANOVA) versus factors when selecting a compressor. Our results show XMill or a simple comparison of means, e.g., X is 20% better than Y. WBXML may be useful in some instances, but a general-purpose compressor is often the best choice. 2. XML OVERVIEW XML has gained much acceptance since first proposed in 1998 by Categories and Subject Descriptors the World-Wide Web Consortium (W3C). -

Desktop Security
JPL Informat'1" I Desktop Security Alan Stepakoff lClS - Desktop Services January 14,2004 JPL lnformatio-” ill*--- Interoperable Computing Environment UWindows 2000, XP +=5500 UMac OS 9, 1O.x += 1800 ULinux Red Hat 8, 9 +=150 orrnatio Desktop Configuration Standard Interoperable Environment MS Word Norton Anti-Virus (F-Prof) PowerPoint Meeting Maker Excel QuickTime player Netscape Real Player Acrobat Reader Timbuktu (VNC) Eudora Stuffit (TAR) SMS or Netoctopus Systems are configured to a standard set of Protective Measures + JPL specific security requirements in-line with NASA regulations + Separate Protective Measure for each OS JPL lnforr_ ” - i_*- User Privileges II Authorization 4 Windows users authorize to Active Directory + Macintosh and Linux users authorize to local system, considering Kerberos Privileges 4 Users are given System Administrative privileges 4 Users are not given System Administrative responsibility 4 Support Contractor has SA privileges and respsonsibility JPL System Management Requirements II Monthly and ad-hoc reporting II New systems delivered secure II Security patches maintained monthly Anti-Virus signature files maintained as needed II Emergency patches within 7 days Quarterlv Service Packs or point releases JPL Information-__1_c System Tools H Periodic ISS scans ITSecure - Custom maintenance utility for Windows II SMS - Windows patch deployment H Netoctopus - Macintosh patch deployment H Norton Anti-Virus Liveupdate Issues ISS scans - may take many scans to capture information w ITSecure needs to be deployed q ua rter I y w SMS + Domain dependant + Too costly to prepare packages w Netoctopus Costly to prepare packages System Management-Future Tools Periodic ISS scans Norton Anti-Virus Liveupdate 4 sus 4 Easy to support 4 Responsibility is transferred to users PatchLink - NASA-wide tool 4 Unobtrusive data gathering and patch delivery + User can control reboot 4 Large patch repository 4 Cross platform 4 Upload data to IT Security Database to close SPL tickets and update configuration information . -

Windows Tips for Genealogists (Based on Windows XP)
Windows Tips for Genealogists (based on Windows XP) Experienced genealogists consider their computer to be just another tool, albeit a very expensive and powerful tool, in their bulging box of tools for helping with their research. However, if one does not know how to use all the features of such a tool, it will be seriously underutilized. This class is intended to be a basic operator’s manual of the features in Windows I find most useful for genealogists. It begins with some very basic concepts in Windows and adds some great shortcuts and things to keep in mind while doing your research. 1. Desk Top “Folder” for most often used files and programs 2. Explore (File manager) – [not to be confused with Internet Explorer] Utility program to maintain and organize the files and programs on your computer (right click on START button.- Fisheye button in Vista) Views Choose details Customize the tool bar (View>Toolbars>Customize) 3. File organization System of hierarchical folders within folders Desktop is the top folder Documents and Settings Creating folders 4. File names Naming rules (do not use < > : “ / \ | ? * . ) max length=260 Renaming Renaming multiple files 5. File extensions 3 letter codes to designate the type of file or the format of the contents of the file Be careful not to delete or change them (unless you know what you are doing) 6. File type assignments Method for assigning file types to programs Displaying file extensions My Computer>Tools>Folder Options> View>Hide Extensions Tools>Folder Options>File Types>extension>Change… 7. Read-Only flag Setting that prevents changes to the file Automatically set for non-writeable media Explore>File-name>right-click>Properties>General>Attributes>Read-only 8. -

How to 'Zip and Unzip' Files
How to 'zip and unzip' files The Windows 10 operating system provides a very easy way to zip-up any file (or folder) you want by using a utility program called 7-zip (Seven Zip). The program is integrated in the context menu which you get when you right-click on anything selected. Here are the basic steps you need to take in order to: Zip a file and create an archive 1. Open a folder in your machine and select any file (by clicking on it once). I selected a single file called 'how-to send an email.docx' 2. Now right click the mouse to have the context menu appear 3. In the context menu you should be able to see some commands like the capture below 4. Since we want to zip up the file you need to select one of the bottom two options a. 'Add to archive' will actually open up a dialog of the 7-zip application and will give you the opportunity to customise the archive. b. 'Add to how-to send an email.zip' is actually the quickest way possible to create an archive. The software uses the name of the file and selects a default compression scheme (.zip) so that you can, with two clicks, create a zip archive containing the original file. 5. Now you can use the 'how-to send an email.zip' file and send it as a 'smaller' email attachment. Now consider that you have just received (via email) the 'how-to send an email.zip' file and you need to get (the correct phrase is extract) the file it contains. -
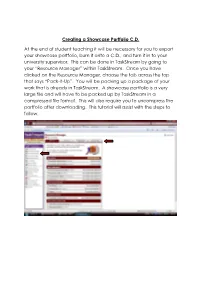
Creating a Showcase Portfolio CD
Creating a Showcase Portfolio C.D. At the end of student teaching it will be necessary for you to export your showcase portfolio, burn it onto a C.D., and turn it in to your university supervisor. This can be done in TaskStream by going to your “Resource Manager” within TaskStream. Once you have clicked on the Resource Manager, choose the tab across the top that says “Pack-It-Up”. You will be packing up a package of your work that is already in TaskStream. A showcase portfolio is a very large file and will have to be packed up by TaskStream in a compressed file format. This will also require you to uncompress the portfolio after downloading. This tutorial will assist with the steps to follow. The next step is to select the work you would like TaskStream to package. This is done by clicking on the tab for selecting work. You will then be asked what type of work you want to package. Your showcase portfolio is a presentation portfolio, so you will click there and click next step. The next step will be to choose the presentation portfolio you want packaged, check the box, and click next step. TaskStream will confirm your selection and then ask you to choose the type of file you need your work to be packaged into. If you are using a computer with a Windows operating system, you will choose a zip file. If you are using a computer with a Macintosh operating system, you will choose a sit file. You will also be asked how you would like TaskStream to notify you that they have completed the task of packing up your work. -

Frequently Asked Questions from Researchers and Downloaders
Frequently Asked Questions from Researchers and Downloaders Table of contents 1. What format are the images and packages?..................................................................... 2 1.1. What format is each package of images and documents?...........................................2 1.2. My system does not understand bzip2 or tar files - where can I get a tool to decompress them?........................................................................................................................................2 1.3. Is the package available as a zip file instead?.............................................................2 1.4. What file format are the images?................................................................................2 1.5. What file format are the report documents?................................................................2 1.6. Is there a DICOMDIR?...............................................................................................2 2. Can the images be viewed on line or accessed individually?...........................................3 2.1. Can the images be viewed on line?............................................................................ 3 2.2. Can the images be accessed or downloaded individually?..........................................3 2.3. Are the images available in alternative formats?........................................................ 3 3. How can I download the files?.........................................................................................3 -

Deduplicating Compressed Contents in Cloud Storage Environment
Deduplicating Compressed Contents in Cloud Storage Environment Zhichao Yan, Hong Jiang Yujuan Tan* Hao Luo University of Texas Arlington Chongqing University University of Nebraska Lincoln [email protected] [email protected] [email protected] [email protected] Corresponding Author Abstract Data compression and deduplication are two common approaches to increasing storage efficiency in the cloud environment. Both users and cloud service providers have economic incentives to compress their data before storing it in the cloud. However, our analysis indicates that compressed packages of different data and differ- ently compressed packages of the same data are usual- ly fundamentally different from one another even when they share a large amount of redundant data. Existing data deduplication systems cannot detect redundant data among them. We propose the X-Ray Dedup approach to extract from these packages the unique metadata, such as the “checksum” and “file length” information, and use it as the compressed file’s content signature to help detect and remove file level data redundancy. X-Ray Dedup is shown by our evaluations to be capable of breaking in the boundaries of compressed packages and significantly Figure 1: A user scenario on cloud storage environment reducing compressed packages’ size requirements, thus further optimizing storage space in the cloud. will generate different compressed data of the same con- tents that render fingerprint-based redundancy identifi- cation difficult. Third, very similar but different digital 1 Introduction contents (e.g., files or data streams), which would other- wise present excellent deduplication opportunities, will Due to the information explosion [1, 3], data reduc- become fundamentally distinct compressed packages af- tion technologies such as compression and deduplica- ter applying even the same compression algorithm.