Avira Antivir Server/ Professional (UNIX) 2 1About This Manual
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Amateur Computer Group of New Jersey NEWS Volume 39, Number 01 January 2014
Amateur Computer Group of New Jersey NEWS Volume 39, Number 01 January 2014 Main Meeting/Election Report ACGNJ Meetings Brenda Bell, ACGNJ For the very latest news on ACGNJ meetings, please On December 6, 2013, we held our Annual Business visit the ACGNJ Website (www.acgnj.org). Meeting, with 8 persons attending. Having reached a Board of Directors Meeting: December 31, 7:00 PM quorum, the meeting was called to order at 9:09 PM. MOVED to Friday, January 3, 7:00 PM. Mike Redlich presented a President's Report. (Due to the New Year's Holiday) Malthi Masurekar presented a Treasurer's Report. Board of Directors Meeting: Friday, Jan 3, 7:00 PM Several topics were raised for discussion, including Mike Redlich (president (at) acgnj.org) membership issues and outreach to other clubs. Main Meeting: Friday, January 3. 8:00 PM Election results. Without discussion, and with no Mike Redlich (president (at) acgnj.org) additional candidates being nominated for our two Lunics (Linux/UNIX): Monday, January 6, 8:00 PM still open Director positions, John Raff moved that Andreas Meyer (lunics (at) acgnj.org) the Secretary cast one vote for the pat slate. The Investing: Thursday, January 9, 8:00 PM motion was seconded and carried. Jim Cooper (jim (at) thecoopers.org). President: Michael Redlich NJ Gamers: Friday, January 10, 6:00 PM Vice-President: Wendy Bell Gregg McCarthy (greggmajestic (at) gmail.com) Secretary: Brenda Bell Treasurer: Malthi Masurekar Layman’s Forum: Monday, January 13, 8:00 PM Directors (Two year term, through end of 2015): Matt Skoda (som359 (at) gmail.com) Gregg McCarthy Java: Tuesday, January 14, 7:30 PM John Raff Mike Redlich (mike (at) redlich.net) Frank Warren Window Pains: Friday, January 17, 7:00 PM Directors (From last year, through end of 2014): !!!WARNING!!! This meeting will NOT be held in Bob Hawes our usual location. -

Contrôles De Conformité Nessus Audit Des Configurations Et Du Contenu Du Système 14 Janvier 2014 (Révision 74)
Contrôles de conformité Nessus Audit des configurations et du contenu du système 14 janvier 2014 (Révision 74) Table des matières Introduction ......................................................................................................................................... 4 Prérequis ...................................................................................................................................................... 4 Clients de Nessus et de SecurityCenter .................................................................................................... 4 Normes et conventions ............................................................................................................................... 4 Normes de conformité ................................................................................................................................. 5 Audits de configuration, fuites de données et conformité ....................................................................... 6 Qu'est-ce qu'un audit ? .............................................................................................................................. 6 Audit et scan des vulnérabilités .................................................................................................................. 6 Exemples d'éléments d'audit ...................................................................................................................... 6 Windows .................................................................................................................................................................... -

EMC® Cloud Tiering Appliance and Cloud Tiering Appliance/VE Version 12.0
EMC® Cloud Tiering Appliance and Cloud Tiering Appliance/VE Version 12.0 Getting Started Guide P/N 300-005-094 Rev 24 Copyright © 2016-2017 Dell Inc. or its subsidiaries All rights reserved. Published July 2017 Dell believes the information in this publication is accurate as of its publication date. The information is subject to change without notice. THE INFORMATION IN THIS PUBLICATION IS PROVIDED “AS-IS.“ DELL MAKES NO REPRESENTATIONS OR WARRANTIES OF ANY KIND WITH RESPECT TO THE INFORMATION IN THIS PUBLICATION, AND SPECIFICALLY DISCLAIMS IMPLIED WARRANTIES OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE. USE, COPYING, AND DISTRIBUTION OF ANY DELL SOFTWARE DESCRIBED IN THIS PUBLICATION REQUIRES AN APPLICABLE SOFTWARE LICENSE. Dell, EMC, and other trademarks are trademarks of Dell Inc. or its subsidiaries. Other trademarks may be the property of their respective owners. Published in the USA. Dell EMC Hopkinton, Massachusetts 01748-9103 1-508-435-1000 In North America 1-866-464-7381 http://www.DellEMC.com Error! No text of specified style in document.Error! No text of specified style in document. 1 Contents Contents Chapter 1 Introduction ........................................................................... 11 Overview of the Cloud Tiering Appliance ............................................................ 12 File tiering and migration .............................................................................. 12 Block archiving ............................................................................................ -

List of New Applications Added in ARL #2574
List of New Applications Added in ARL #2574 Application Name Publisher Virtual Office Desktop 5.5 8x8 Virtual Office Desktop 5.3 8x8 FlexiCapture Scanning Station 12.0 ABBYY FlexiCapture 12.0 ABBYY Video Studio 4.0 ACD Systems Add-ins Collection for Microsoft Outlook 19.1 Add-in Express Dynamic Media Classic 20.20 Adobe Photoshop Lightroom Classic CC (2019) Adobe Substance in Maya 2019 Adobe Airtame 4.1 Airtame FoneTrans Aiseesoft Studio Akkadian Console Akkadian Labs Structure Plugin for JIRA 1.5 ALM Works Alteryx Designer 2020.3 Alteryx Syncios Data Recovery 3.0 Anvsoft Any PDF to DWG Converter 2018 AnyDWG Software Video Converter Ultimate AnyMP4 Studio Maven 3.5 Apache Software Foundation Video Converter Studio 4.8 Apowersoft iPhone/iPad Recorder Apowersoft ApowerREC Apowersoft AFT SteamCalc 3.0 Applied Flow Technology AFT Fathom 11.0 Applied Flow Technology AFT Impulse 6.0 Demo Applied Flow Technology AFT Impulse Client 7.0 Applied Flow Technology AFT Arrow Client 7.0 Applied Flow Technology AFT Impulse Client 8.0 Applied Flow Technology AFT Arrow 8.0 Applied Flow Technology AFT Impulse 8.0 Applied Flow Technology AFT Impulse 7.0 Applied Flow Technology AFT Fathom Client 10.0 Applied Flow Technology AFT Chempak Viewer 3.0 Applied Flow Technology ActivePresenter 7.3 Atomi Systems VirtualDJ 8.4 Atomix Productions Registry Cleaner 8.5 Auslogics Software BoostSpeed 11.5 Auslogics Software Avaya IX Workplace 3.9 Avaya ProjectDox Components 8.4 Avolve Software MAGIC TH2plus AVT Audio Video Technologies Media Control 7.3 Axis Communications -
Free Disk Space in Mac Os X
Free disk space in mac os x To really free up disk space on your Mac's hard drive, you're going to need to Mac OS X tries to automatically remove temporary files, but a. Ever wonder how much free space is available on your Mac's hard disk or partitions? It's easy to check in OS X. Plus, if your Mac is running Mac. Optimized Storage in macOS Sierra and later can save space by storing your content You'll see an overview of your free space and the space used by different Move your pointer over the file name, then click the x button. Mac running out of disk space? Maybe you don't have room for installing a new app, backing up a device, copying some files, or much of. on your Mac? These 10 tips can help you free up space you didn't know you were even using! . Service files and app remnants can eat up terrible amounts of disk space. This is bad if . How To Completely Uninstall Software under Mac OS X [MacRx] iPhone X won't reveal your lock screen notifications to anyone else. Disk Inventory X, disk usage utility for Mac OS X. If you've ever wondered where all your disk space has gone, Disk Inventory X will help you to answer this. DaisyDisk is a disk analyzer tool for OS X that visualizes hard disk usage and allows to free up hard disk space. After the break we'll look at the most efficient ways to free up space on your Mac. -
Free Scan Download Software WS1040/WS1065 Scanner Firmware Updates and Downloads
free scan download software WS1040/WS1065 Scanner Firmware Updates and Downloads. Note: Before updating your firmware, please check the version of your unit. Turn your scanner on and press the 3 key while the Welcome screen is being displayed to view the currently installed firmware versions. If the “uP Appl Ver” number is the same as the available download version (currently U2.9), there is no need to update. If you have corrupted, missing or older uP Appl version, proceed with the CPU Firmware Updater download. If download links do not appear below, please make sure you are using the most current version of your browser. Some browsers may have difficulty showing the links. Company. Whistler has been an innovator in automotive electronics for almost 50 years. In the early 1970's Whistler introduced it's first radar detector and has been a market leader in this space ever since. Corporate Headquarters. 1716 SW Commerce Dr Ste. 8 Bentonville, AR 72712 Phone: 479.273.6012. Scanner for Windows. Scanner is a free system utility software that allows you to check how much your files are taking up space on your PC via a pie chart . Developed by Steffen Gerlach, this is a disk space analyzing and management tool that offers a visual representation of your storage. Similar to TreeSize, Scanner can display the diagnostics of your PC—although the focus of this program is solely on your disk space and nothing else. It uses a multi-level chart to show the different directories within your PC memory, which is very helpful. -

Operating Systems
Operating Systems Find information about different operating systems. Recommended Operating Systems: MacOS & Windows Computer Backup Computer Storage Management Computer Performance Change your macOS Login Password Change your Windows 10 Login Password Backing Up with Windows File History Change the Default Application Associated with a File Type How do I install device drivers? Help for New Mac Users Start your Windows Computer in Safe Mode macOS Startup Key Commands Use VirtualBox to Create a Windows Virtual Machine Create a Disk Image Backup with Macrium Reflect Recommended Operating Systems: MacOS & Windows IT highly recommends using either macOS or Windows 10 operating systems. Keeping your operating system up to date with the most current upgrades available will allow your system to run at optimal performance and security levels. macOS Apple provides free upgrades to newer operating systems when they become available. Big Sur Apple's newest version of macOS Compatible with these computers: https://support.apple.com/en-us/HT211238 Once you have installed the latest operating system available, keep it up-to-date by enabling automatic updates by following the instructions here. Windows Microsoft's newest operating systems must be purchased before being installed. Windows 10 Microsoft's newest windows operating system Windows 10 is compatible with most PCs Once you have installed the latest operating system available, keep it up-to-date by enabling automatic updates by following the instructions here. Windows 7 Microsoft no longer provides support for Windows 7. If you have any computers that are still running Windows 7, contact IT as soon as possible to be upgraded to Windows 10. -
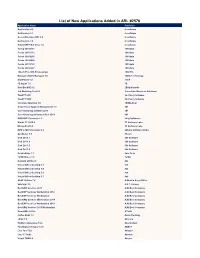
List of New Applications Added in ARL #2576
List of New Applications Added in ARL #2576 Application Name Publisher NetCmdlets 4.0 /n software NetCmdlets 3.1 /n software SecureBlackbox.NET 8.0 /n software NetCmdlets 3.0 /n software EldoS SFTP Net Drive 1.0 /n software Tenup 20190117 1010data Tendo 20151112 1010data Tendo 20160205 1010data Tendo 20190905 1010data Tendo 20170723 1010data Tendo 20161207 1010data 1042-S Pro 2016 Professional 1099 Pro Manager (10ZiG Manager) 3.0 10ZIG Technology DataParser 7.5 17a-4 1E Agent 7.2 1E SyncBackSE 8.2 2BrightSparks 2c8 Modeling Tool 4.2 2conciliate Business Solutions TaxACT 2017 2nd Story Software TaxACT 2018 2nd Story Software Complete Anatomy 5.0 3D4Medical Clean-Trace Hygiene Management 1.3 3M Core Grouping Software 2019 3M Core Grouping Software Client 2019 3M DWG DXF Converter 1.1 3nity Softwares Studio 3T 2020.9 3T Software Labs MongoChef 4.5 3T Software Labs MP4 to MP3 Converter 6.8 4Media Software Studio SendLater 3.4 4Team Disk Dril 3.7 508 Software Disk Dril 1.0 508 Software Disk Dril 3.5 508 Software Disk Dril 3.6 508 Software DoublePane 1.7 5am Code 7-PDF Maker 1.5 7-PDF Network Utility 2.2 8x8 Virtual Office Desktop 6.1 8x8 Virtual Office Desktop 6.4 8x8 Virtual Office Desktop 5.6 8x8 Virtual Office Desktop 6.7 8x8 ASAP Utilities 7.8 A Must in Every Office SafeSign 3.5 A.E.T. Europe BestSRQ Services 2015 A.M. Best Company BestESP Services Workstation 2012 A.M. Best Company BestESP Services Workstation A.M. -

Freeflow Scanner 665E System Administration Guide
FreeFlow Scanner 665E System Administration Guide 701P44149 Version 1.0/September 2005 Xerox Corporation Global Knowledge & Language Services 800 Phillips Road Building 845 Webster, New York 14580 ©Copyright 2005 by Xerox Corporation. All Rights Reserved. Printed in the U.S.A. Copyright protection claimed includes all forms and matters of copyrighted material and information now allowed by statutory or judicial law or hereinafter granted, including without limitation, material generated from the software programs that are displayed on the screen such as styles, templates, icons, screen displays, looks, etc. Xerox®, Xerox Canada Ltd®, Xerox Limited®, FreeFlow™, and all Xerox product names and product numbers mentioned in this publication are trademarks of XEROX CORPORATION. Copyright protection claimed includes all forms and matters of copyrightable material and information now allowed by statutory or judicial law or hereinafter granted, including without limitations, material generated from the software programs which are displayed on the screen such as styles, templates, icons, screen displays looks, etc. Other company brands and product names may be trademarks or registered trademarks of the respective companies and are also acknowledged. While every care has been taken in the preparation of this material, no liability will be accepted by Xerox Corporation arising out of any inaccuracies or omissions. Other company trademarks are acknowledged as follows: Adaptec®, the Adaptec logo, SCSlSelect®, and EZ-SCSI® are trademarks of Adaptec, Inc. Adobe PDFL - Adobe PDF Library Copyright© 1987-2002 Adobe Systems Incorporated. Adobe®, the Adobe logo, Acrobat®, the Acrobat logo, Acrobat Reader®, Distiller®, Adobe PDF JobReady™, and PostScript®, and the PostScript logo are either registered trademarks or trademarks of Adobe Systems Incorporated in the United States and/or other countries. -

Hiren's Bootcd Berbentuk Iso File Dan Harus Di Burning Ke CD Dan Bisa Anda Jalankan Melalui Met Ode Boot Atau Explore
Hiren's BootCD berbentuk iso file dan harus di burning ke CD dan bisa anda jalankan melalui met ode boot atau explore. salah satu software penting untuk merecovery data karena software ini juga memiliki mini windows yg di jalankan pada bootable. Selanjutnya lihat saja review yg saya ambil dari websitenya, www.hirensbootcd.or g. seperti di bawah ini. Antivirus Tools Avira AntiVir Personal (11-04-2011): Free anti-virus and anti-spyware on-demand scanner, detects and removes more than 50000 viruses and trojans (Windows Freewa re). ComboFix (11-04-2011): Designed to cleanup malware infections and restore settin gs modified by malware (Windows Freeware). Dr.Web CureIt! Antivirus (11-04-2011): A free standalone anti-virus and anti-spy ware on-demand scanner (Windows Freeware). GMER 1.0.15: Hidden services, hidden registry, hidden file scanner, Rootkit Dete ctor and Remover (Windows Freeware). Malwarebytes Anti-Malware 1.50.1 (11-04-2011): Anti-malware application that can thoroughly remove even the most advanced malware (Windows Freeware). Remove Fake Antivirus 1.76: A tool to remove virus/malware which disguises itsel f to be an antivirus and produces fake alert/warnings and urge you to purchase a useless copy of the fake antivirus (Windows Freeware). RootkitRevealer 1.7.1: Rootkit Revealer is an advanced patent-pending root kit d etection utility (Windows Freeware). Spybot Search & Destroy 1.6.2 (11-04-2011): Application to scan for spyware, adw are, hijackers and other malicious software (Windows Freeware). SpywareBlaster 4.4 (11-04-2011): Prevent the installation of spyware and other p otentially unwanted software (Windows Freeware). -
Apple Remote Desktop Administrator’S Guide Version 2.2
Apple Remote Desktop Administrator’s Guide Version 2.2 Apple Computer, Inc. © 2005 Apple Computer, Inc. All rights reserved. The owner or authorized user of a valid copy of Apple Remote Desktop software may reproduce this publication for the purpose of learning to use such software. No part of this publication may be reproduced or transmitted for commercial purposes, such as selling copies of this publication or for providing paid for support services. The Apple logo is a trademark of Apple Computer, Inc., registered in the U.S. and other countries. Use of the “keyboard” Apple logo (Option-Shift-K) for commercial purposes without the prior written consent of Apple may constitute trademark infringement and unfair competition in violation of federal and state laws. Apple, the Apple logo, AirPort, AppleScript, AppleTalk, AppleWorks, FireWire, iBook, iMac, Keychain, Mac, Macintosh, Mac OS, PowerBook, QuickTime, and Xserve are trademarks of Apple Computer, Inc., registered in the U.S. and other countries. eMac, Finder, iCal, Bonjour, and Safari are trademarks of Apple Computer, Inc. Adobe and Acrobat are trademarks of Adobe Systems Incorporated. Java and all Java-based trademarks and logos are trademarks or registered trademarks of Sun Microsystems, Inc. in the U.S. and other countries. UNIX is a registered trademark in the United States and other countries, licensed exclusively through X/Open Company, Ltd. 019-0359 3/4/05 3 Contents Preface 5 About This Book 5 What Is Apple Remote Desktop? 5 Using This Guide 7 Where to Find More Information -

Automated Malware Analysis Report for Foldersize
ID: 358426 Sample Name: FolderSize-2.6- x86.msi Cookbook: defaultwindowsofficecookbook.jbs Time: 15:49:20 Date: 25/02/2021 Version: 31.0.0 Emerald Table of Contents Table of Contents 2 Analysis Report FolderSize-2.6-x86.msi 5 Overview 5 General Information 5 Detection 5 Signatures 5 Classification 5 Analysis Advice 5 Startup 5 Malware Configuration 5 Yara Overview 5 Sigma Overview 6 Signature Overview 6 Compliance: 6 Mitre Att&ck Matrix 6 Behavior Graph 7 Screenshots 7 Thumbnails 7 Antivirus, Machine Learning and Genetic Malware Detection 8 Initial Sample 8 Dropped Files 8 Unpacked PE Files 8 Domains 8 URLs 8 Domains and IPs 9 Contacted Domains 9 URLs from Memory and Binaries 9 Contacted IPs 10 General Information 10 Simulations 11 Behavior and APIs 11 Joe Sandbox View / Context 11 IPs 11 Domains 11 ASN 11 JA3 Fingerprints 11 Dropped Files 11 Created / dropped Files 11 Static File Info 12 General 12 File Icon 12 Static OLE Info 12 General 12 OLE File "FolderSize-2.6-x86.msi" 12 Indicators 12 Summary 12 Streams 13 Stream Path: \x5SummaryInformation, File Type: data, Stream Size: 468 13 General 13 Stream Path: \x16786\x17522\x15358\x17394\x16935\x16181\x18284\x18344\x16812\x18482, File Type: MS Windows icon resource - 9 icons, 48x48, 16 colors, 4 bits/pixel, 32x32, 16 colors, 4 bits/pixel, Stream Size: 25214 13 General 13 Stream Path: \x17163\x16689\x18229\x15870\x18088, File Type: MS Windows icon resource - 1 icon, 16x16, 16 colors, Stream Size: 318 13 General 13 Stream Path: \x17163\x16689\x18229\x16318\x18483, File Type: MS Windows icon