Remotely Controlling a Mechanical Laboratory Via the Internet
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

BOROUGH of MANHATTAN COMMUNITY COLLEGE City University of New York Department of Computer Information Systems Office S150/Phone: 212-220-1476
BOROUGH OF MANHATTAN COMMUNITY COLLEGE City University of New York Department of Computer Information Systems Office S150/Phone: 212-220-1476 Web Programming II Class hours: 2 CIS 485 Lab hours: 2 Spring 2012 Credits: 3 Course Description: This course will introduce students to server-side web programming. Emphasis is placed on database connectivity in order to solve intermediate level application problems. Students will be tasked with web projects that facilitate understanding of tier design and programming concepts. The overall goal of this course is to create a shopping cart application with a login and database component. Prerequisites/Co-requisite: Basic Skills: ENG 088, ESL 062, ACR 094, MAT 012/051; CIS 385 Web Programming I Learning Outcomes and Assessment After completing this course, students will be able to: Outcome: Demonstrate the use of a database with server-side scripting Assessment: Lab exercises and exam questions Outcome: Demonstrate the use a Cookie and Session manager with server-side scripting Assessment: Final project, lab exercises and exam questions Outcome: Develop a database-driven website Assessment: Lab exercises Outcome: Design and develop a shopping-cart application with a login and database component Assessment: Final Project General Education Outcomes and Assessment Quantitative Skills – Students will use quantitative skills and concepts and methods of mathematics to solve problems Assessment: Use formulas and concepts of mathematics to solve problems in programming assignments Information and Technology -

Steps for Downloading And/Or Installing Java SE 7, the JMF, Apache Tomcat & Eclipse
Steps for Downloading and/or Installing Java SE 7, the JMF, Apache Tomcat & Eclipse Java SE 7 The download instructions below refer to the latest version of the Java Standard Edition (Java SE), which (at the time of writing) is Java SE 7 Update 5. The Java SE Development Kit (JDK) includes the Java Runtime Environment (JRE) and command-line development tools. It is actually the JDK that you are downloading, but we shall be referring only to the Java SE. 1. Go to http://www.oracle.com/technetwork/java/javase/downloads/index.html. 2. Click on the Download button underneath JDK, which is to the right of the text heading showing the latest version of Java. 3. In the table heading halfway down the page, click on the radio button to accept the licence agreement. 4. Click on the filename that appears alongside Windows x86. (This should have the format jdk- 7u<Update version>-windows-i586.exe, where <Update version> is replaced with a number that is either 5 or one slightly higher. 5. Click on the Save button and navigate to a suitable location for the download file (probably the top level of your drive C) and then click the next Save button. (File takes up 87.95MB or more.) 6. After downloading to a suitable location, click on the Open Folder button. 7. Double-click on the executable file that has either been downloaded or been copied from the CD. 8. Click on the Run button. 9. Click on the Next> button (when it becomes available). 10. -

Media Rate Allocation
MEDIA RATE ALLOCATION A PROJECT REPORT Submitted by P.BALASUBRAMANIAN (32205205004) R.VIGNESWARAN (32205205302) in the partial fulfillment for the award of the degree of BACHELOR OF TECHNOLOGY In INFORMATION TECHNOLOGY DHANALAKSHMI SRINIVASAN COLLEGE OF ENGINEERING AND TECHNOLOGY: Mamallapuram ANNA UNIVERSITY: CHENNAI 600025 APRIL 2009 1 ANNA UNIVERSITY: CHENNAI 600 025 BONAFIDE CERTIFICATE Certified that this project report “MEDIA RATE ALLOCATION” is the bonafide work of “P.BALASUBRAMANIAN (32205205004), R.VIGNESWARAN (32205205302)” who carried out the project work under my supervision. SIGNATURE SIGNATURE Ms.D.Jansi Rani Ms.T.Yogeswari HEAD OF THE DEPARTMENT SUPERVISOR Department of Information Technology Department of Information Technology Dhanalakshmi Srinivasan Dhanalakshmi Srinivasan College of Engineering and Technology, College of Engineering and Technology, Mamallapuram. Mamallapuram. Submitted for the project viva voce examination held on ____________ INTERNAL EXAMINER EXTERNAL EXAMINER 2 ACKNOWLEDGEMENT We are glad to take this opportunity to cordially acknowledge a number of people who provide me with great support in these six months. First, we would like to thank Mr.A.Srinivasan, our Chairman who allowed me to do the project in the college campus. We are also thankful to Dr.R.Ponraj M.Tech Ph.D., our Principal, for his constant support in selecting the project. We wish to express my sincere gratitude to our respected Vice Principal, Mr.Pon.Arivanandham M.E, PhD., for his continued encouragement and support. We are grateful to Lecturer Ms.D.Jansi Rani M.Tech., our Head of the Department, who expressed her interest in my work and supplied me with some of her recent works. We would like to thank Lecturer Ms.T.Yogeswari B.E., for following my project with interest and for giving me constant support. -
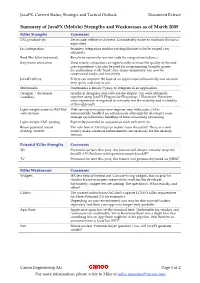
Javafx Strengths and Weaknesses
JavaFX: Current Status; Strategic and Tactical Outlook Document Extract Summary of JavaFX (Mobile) Strengths and Weaknesses as of March 2009 Killer Strengths Comments DSL productivity Terse code; reflective of intent. Considerably easier to maintain than Java equivalent. Java integration Seamless integration enables existing libraries to be leveraged very efficiently. Bind (the killer keyword) Results in extremely succinct code (in comparison to Java.) Key-frame animation Used wisely, animation can significantly increase the quality of the end- user experience. Can also be used for programming (simple) games. In combination with “bind”, key-frame animations can now be constructed easily and intuitively. Java2D effects Effects can improve the look of an application substantially and are now very quick and easy to use. Multimedia Multimedia is finally (!) easy to integrate in an application. Designer / developer Graphical designers and software developers can work efficiently workflow together using JavaFX Plugins for Photoshop / Illustrator. However, more experience is required to seriously test the viability and scalability of this approach. Light-weight access to RESTful Web-service invocation now requires very little code. Call is web services automatically handled asynchronously although the developer must manage asynchronous handling of time-consuming processing. Light-weight XML parsing Especially powerful in conjunction with web-services. Reuse potential across The rule here is: Develop for mobile from the outset! Then, in a new desktop/mobile project, make whatever enhancements are necessary for the desktop version. Potential Killer Strengths Comments 3D Promised for later this year, this feature will almost certainly wrap the Java3D API. But how will it perform under JavaME? TV Promised for later this year, this feature will presumably build on JSR927 Killer Weaknesses Comments Widgets JFX text field of limited use. -

JCP at Javapolis 2007
Javapolis News ❙ 14 December 2007 ❙ Nr 5 ❙ Published by Minoc Business Press 54 www.nonillion.com Parleys Want to become a NONILLIONAIRE ? mail us at : [email protected] Building Rich Internet Applications with Flex and JavaFX “There’s a well thought out com- an online environment using Adobe AIR. “Even when you ponent model for Flex”, he said. are offl ine, you still can update data. When the connec- “And there’s a thriving market tion comes back on, the system synchronizes automati- for components out there, both cally.” Open Source and commercial. So there are literally hundreds JavaPolis founder Stephan Janssen was next to explain of components available to how he decided to have Parleys.com rewritten using Flex. use in Flex.” And no, Flex isn’t Parleys.com offers a massive amount of Java talks – from there for fun and games only. JavaPolis, JavaOne and other Java events from all over “There are already a great the world – combining video images with the actual pres- number of business applica- entation slides of the speakers. Janssen programmed the tions running today, all built application for fun at fi rst, but with over 10 TB of streamed with Flex.” Eckel backed up video in just under a year, it’s clear Parleys.com sort of his statement with an ex- started to lead its own life. “The decision to write a new ample of an interface for an version was made six months ago”, he said. “It was still intranet sales application. too early to use JavaFX. And Silverlight? No thanks.” “Some people think Flex Flex allowed him to leverage the Java code of the earlier isn’t the right choice to version of Parleys.com and to resolve the Web 2.0 and make for business applica- AJAX issues he had en- countered while programming tions, because the render- the fi rst version. -

DLCGI Advanced Uses
DLCGI Advanced Uses Using DLCGI to achieve single sign-on with The Diver Solution In situations where authentication to DiveLine needs to be integrated with an existing authentication scheme, we provide "DLCGI", the DiveLine-Common Gateway Interface interfacing module. The "Common Gateway Interface" is a standard for interfacing external scripts and programs with a web server. How DLCGI works When dlcgi.exe is executed by the webserver, in the context of a user that the web server has already authenticated, it obtains a limited-lifetime one-time password from DiveLine. This password can be passed, via web page redirects, custom web page scripting, etc., to DivePort, NetDiver, or even ProDiver to allow the user to login. The typical strategy for using DLCGI is: 1. Configure DiveLine to accept DLCGI requests from your webserver. 2. Install dlcgi.exe in a scripts directory (e.g. /cgi-bin/) on your CGI-compliant webserver (e.g. IIS, Apache). You configure the name of your DiveLine server and other parameters using dlcgi.cfg in the same directory as the executable. 3. Restrict access to this script so that the webserver will only execute it when the user has already authenticated (e.g. Domain account). Typical uses • DivePort: Users go to the DivePort site, and are redirected to another URL for authentication. That URL, which runs dlcgi.exe, redirects the user back to the DivePort URL with a one-use authentication token. • ProDiver: When ProDiver connects to DiveLine, if configured with a DLCGI URL, it will access the URL in "raw" mode (see below) to obtain a parse-able result file containing a one-use DiveLine authentication token. -

Using the ELECTRIC VLSI Design System Version 9.07
Using the ELECTRIC VLSI Design System Version 9.07 Steven M. Rubin Author's affiliation: Static Free Software ISBN 0−9727514−3−2 Published by R.L. Ranch Press, 2016. Copyright (c) 2016 Static Free Software Permission is granted to make and distribute verbatim copies of this book provided the copyright notice and this permission notice are preserved on all copies. Permission is granted to copy and distribute modified versions of this book under the conditions for verbatim copying, provided also that they are labeled prominently as modified versions, that the authors' names and title from this version are unchanged (though subtitles and additional authors' names may be added), and that the entire resulting derived work is distributed under the terms of a permission notice identical to this one. Permission is granted to copy and distribute translations of this book into another language, under the above conditions for modified versions. Electric is distributed by Static Free Software (staticfreesoft.com), a division of RuLabinsky Enterprises, Incorporated. Table of Contents Chapter 1: Introduction.....................................................................................................................................1 1−1: Welcome.........................................................................................................................................1 1−2: About Electric.................................................................................................................................2 1−3: Running -

Design of a Distributed Architecture for Enriching Media Experience in Home Theaters
Design of a distributed architecture for enriching media experience in home theaters Citation for published version (APA): Hu, J. (2006). Design of a distributed architecture for enriching media experience in home theaters. Technische Universiteit Eindhoven. https://doi.org/10.6100/IR611954 DOI: 10.6100/IR611954 Document status and date: Published: 01/01/2006 Document Version: Publisher’s PDF, also known as Version of Record (includes final page, issue and volume numbers) Please check the document version of this publication: • A submitted manuscript is the version of the article upon submission and before peer-review. There can be important differences between the submitted version and the official published version of record. People interested in the research are advised to contact the author for the final version of the publication, or visit the DOI to the publisher's website. • The final author version and the galley proof are versions of the publication after peer review. • The final published version features the final layout of the paper including the volume, issue and page numbers. Link to publication General rights Copyright and moral rights for the publications made accessible in the public portal are retained by the authors and/or other copyright owners and it is a condition of accessing publications that users recognise and abide by the legal requirements associated with these rights. • Users may download and print one copy of any publication from the public portal for the purpose of private study or research. • You may not further distribute the material or use it for any profit-making activity or commercial gain • You may freely distribute the URL identifying the publication in the public portal. -

Puneet Lakhina
PUNEET LAKHINA 1. PERSONAL INFORMATION • Address: 182 Kailash Hills,Near East of Kailash, New Delhi – 10065, India • E-Mail: [email protected] • Phone: 00919818069803 2. AREAS OF INTEREST Distributed Systems, Peer to Peer Systems, Software Engineering, Information Retrieval, Computer Networks, Databases. 3. EDUCATION • Bachelor of Technology in Information Technology, Vellore Institute of Technology University, November 2006 CGPA: 9.23 Scale: 10 Rank: 5th (Class Strength: 65) 4. ACADEMIC INTERNSHIPS/FELLOWSHIPS • Position: Project Trainee (January 2006 – May 2006) Institution: Kanwal Rekhi School of Information Technology, Indian Institute Of Technology Bombay Mentor: Dr. Deepak. B. Phatak • Position: Summer Intern (June 2005-August 2005) Institution: Kanwal Rekhi School of Information Technology, Indian Institute Of Technology Bombay Mentor: Dr. Deepak B. Phatak 5. PROFESSIONAL WORK EXPERIENCE • Position: Associate System Engineer (June 2006 – Present) Institution: IBM India Private Limited. 6. PROJECTS • Virtualization: Executed at: IBM India Pvt. Ltd Team Size: 25 Abstract: Virtualization is a SOA based platform, that allows integration of multiple type of bearers (USSD, Web, SMS, IVR, Kiosk etc.) with service platform (network elements) providing scalable, flexible and easily configurable solutions. Virtualization is a key part of the Prepaid transformation that allows IT system to manage the increasing subscriber base (from current 45 million to projected 157 million by 2013) and can be applied for any telecom scenario. My role in the project was to manage the transport layer based on IBM Websphere MQ™ for service request processing. This involved development of a Listener Framework for allowing a business logic plugging without regard to the nature of the transport layer. I was also the lead for load testing and optimization group, whereby the performance target of 43 service requests processing per second was achieved. -

Leukemia Medical Application with Security Features
Journal of Software Leukemia Medical Application with Security Features Radhi Rafiee Afandi1, Waidah Ismail1*, Azlan Husin2, Rosline Hassan3 1 Faculty Science and Technology, Universiti Sains Islam Malaysia, Negeri Sembilan, Malaysia. 2 Department of Internal Medicine, School of Medicine, Universiti Sains Malaysia, Kota Bahru, Malaysia. 3 Department of Hematology, School of Medicine, Universiti Sains Malaysia, Kota Bahru, Malaysia. * Corresponding author. Tel.: +6 06 7988056; email: [email protected]. Manuscript submitted January 27, 2015; accepted April 28, 2015 doi: 10.17706/jsw.10.5.577-598 Abstract: Information on the Leukemia patients is very crucial by keep track medical history and to know the current status of the patient’s. This paper explains on development of Hematology Information System (HIS) in Hospital Universiti Sains Malaysia (HUSM). HIS is the web application, which is the enhancement of the standalone application system that used previously. The previous system lack of the implementation of security framework and triple ‘A’ elements which are authentication, authorization and accounting. Therefore, the objective of this project is to ensure the security features are implemented and the information safely kept in the server. We are using agile methodology to develop the HIS which the involvement from the user at the beginning until end of the project. The user involvement at the beginning user requirement until implemented. As stated above, HIS is web application that used JSP technology. It can only be access within the HUSM only by using the local Internet Protocol (IP). HIS ease medical doctor and nurse to manage the Leukemia patients. For the security purpose HIS provided password to login, three different user access levels and activity log that recorded from each user that entered the system Key words: Hematology information system, security feature, agile methodology. -

Interfacing Apache HTTP Server 2.4 with External Applications
Interfacing Apache HTTP Server 2.4 with External Applications Jeff Trawick Interfacing Apache HTTP Server 2.4 with External Applications Jeff Trawick November 6, 2012 Who am I? Interfacing Apache HTTP Server 2.4 with External Applications Met Unix (in the form of Xenix) in 1985 Jeff Trawick Joined IBM in 1990 to work on network software for mainframes Moved to a different organization in 2000 to work on Apache httpd Later spent about 4 years at Sun/Oracle Got tired of being tired of being an employee of too-huge corporation so formed my own too-small company Currently working part-time, coding on other projects, and taking classes Overview Interfacing Apache HTTP Server 2.4 with External Applications Jeff Trawick Huge problem space, so simplify Perspective: \General purpose" web servers, not minimal application containers which implement HTTP \Applications:" Code that runs dynamically on the server during request processing to process input and generate output Possible web server interactions Interfacing Apache HTTP Server 2.4 with External Applications Jeff Trawick Native code plugin modules (uhh, assuming server is native code) Non-native code + language interpreter inside server (Lua, Perl, etc.) Arbitrary processes on the other side of a standard wire protocol like HTTP (proxy), CGI, FastCGI, etc. (Java and \all of the above") or private protocol Some hybrid such as mod fcgid mod fcgid as example hybrid Interfacing Apache HTTP Server 2.4 with External Applications Jeff Trawick Supports applications which implement a standard wire protocol, no restriction on implementation mechanism Has extensive support for managing the application[+interpreter] processes so that the management of the application processes is well-integrated with the web server Contrast with mod proxy fcgi (pure FastCGI, no process management) or mod php (no processes/threads other than those of web server). -

Getting Started Guide with Wiz550web Getting Started Guide with Wiz550web
2015/02/09 17:48 1/21 Getting Started Guide with WIZ550web Getting Started Guide with WIZ550web WIZ550web is an embedded Web server module based on WIZnet’s W5500 hardwired TCP/IP chip, Users can control & monitor the 16-configurable digital I/O and 4-ADC inputs on module via web pages. WIZ550web provides the firmware & web page examples for user’s customization. This page describes the following topics: ● Product Preview ● Hello world ❍ Product contents ❍ SD card initialization ❍ Data flash initialization ❍ Serial debug message ● WIZ550web Basic operations and CGI ● Basic Demo Webpage ● Examples for WIZ550web customization Users can download the following source codes from the 'WIZ550web GitHub Repository' ● Firmware source code (The projects for Eclipse IDE) ❍ Application / Boot ● Demo webpage WIZ550web GitHub Repository https://github.com/Wiznet/WIZ550web WIZ550web GitHub Page http://wiznet.github.io/WIZ550web Develop Environment - http://wizwiki.net/wiki/ Last update: 2015/02/09 products:wiz550web:wiz550webgsg_en http://wizwiki.net/wiki/doku.php?id=products:wiz550web:wiz550webgsg_en 13:05 ● Eclipse IDE for C/C++ Developers, Kepler Service Release 2 ● ARM GCC 4.8.3 (2014q1) Product Preview Hello World Product Contents Ordering Part No: WIZ550web ● WIZ550web module x 1 Ordering Part No: WIZ550web-EVB ● WIZ550web module x 1 ● WIZ550web baseboard x 1 http://wizwiki.net/wiki/ Printed on 2015/02/09 17:48 2015/02/09 17:48 3/21 Getting Started Guide with WIZ550web ● LAN cable x 1 ● Serial cable x 1 ● 12V Power adapter x 1 SD card is option for both WIZ550web and WIZ550web-EVB Refer to recommended lists of SD card. Vendor Capacity(Bytes) Type Class 2G SD n/a Sandisk 4G SDHC 4 8G SDHC 4 Samsung 4G SDHC 6 Transcend 4G SDHC 4,10 SD card Initialization WIZ550web uses Micro SD card as a storage for web content and SD card is not included as default.