Embedded Android
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Android (Operating System) 1 Android (Operating System)
Android (operating system) 1 Android (operating system) Android Home screen displayed by Samsung Nexus S with Google running Android 2.3 "Gingerbread" Company / developer Google Inc., Open Handset Alliance [1] Programmed in C (core), C++ (some third-party libraries), Java (UI) Working state Current [2] Source model Free and open source software (3.0 is currently in closed development) Initial release 21 October 2008 Latest stable release Tablets: [3] 3.0.1 (Honeycomb) Phones: [3] 2.3.3 (Gingerbread) / 24 February 2011 [4] Supported platforms ARM, MIPS, Power, x86 Kernel type Monolithic, modified Linux kernel Default user interface Graphical [5] License Apache 2.0, Linux kernel patches are under GPL v2 Official website [www.android.com www.android.com] Android is a software stack for mobile devices that includes an operating system, middleware and key applications.[6] [7] Google Inc. purchased the initial developer of the software, Android Inc., in 2005.[8] Android's mobile operating system is based on a modified version of the Linux kernel. Google and other members of the Open Handset Alliance collaborated on Android's development and release.[9] [10] The Android Open Source Project (AOSP) is tasked with the maintenance and further development of Android.[11] The Android operating system is the world's best-selling Smartphone platform.[12] [13] Android has a large community of developers writing applications ("apps") that extend the functionality of the devices. There are currently over 150,000 apps available for Android.[14] [15] Android Market is the online app store run by Google, though apps can also be downloaded from third-party sites. -

Android Operating System
Software Engineering ISSN: 2229-4007 & ISSN: 2229-4015, Volume 3, Issue 1, 2012, pp.-10-13. Available online at http://www.bioinfo.in/contents.php?id=76 ANDROID OPERATING SYSTEM NIMODIA C. AND DESHMUKH H.R. Babasaheb Naik College of Engineering, Pusad, MS, India. *Corresponding Author: Email- [email protected], [email protected] Received: February 21, 2012; Accepted: March 15, 2012 Abstract- Android is a software stack for mobile devices that includes an operating system, middleware and key applications. Android, an open source mobile device platform based on the Linux operating system. It has application Framework,enhanced graphics, integrated web browser, relational database, media support, LibWebCore web browser, wide variety of connectivity and much more applications. Android relies on Linux version 2.6 for core system services such as security, memory management, process management, network stack, and driver model. Architecture of Android consist of Applications. Linux kernel, libraries, application framework, Android Runtime. All applications are written using the Java programming language. Android mobile phone platform is going to be more secure than Apple’s iPhone or any other device in the long run. Keywords- 3G, Dalvik Virtual Machine, EGPRS, LiMo, Open Handset Alliance, SQLite, WCDMA/HSUPA Citation: Nimodia C. and Deshmukh H.R. (2012) Android Operating System. Software Engineering, ISSN: 2229-4007 & ISSN: 2229-4015, Volume 3, Issue 1, pp.-10-13. Copyright: Copyright©2012 Nimodia C. and Deshmukh H.R. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited. -

Android (Operating System) 1 Android (Operating System)
Android (operating system) 1 Android (operating system) Android Android 4.4 home screen Company / developer Google Open Handset Alliance Android Open Source Project (AOSP) Programmed in C (core), C++, Java (UI) OS family Unix-like Working state Current Source model Open source with proprietary components Initial release September 23, 2008 Latest stable release 4.4.2 KitKat / December 9, 2013 Marketing target Smartphones Tablet computers Available language(s) Multi-lingual (46 languages) Package manager Google Play, APK Supported platforms 32-bit ARM, MIPS, x86 Kernel type Monolithic (modified Linux kernel) [1] [2] [3] Userland Bionic libc, shell from NetBSD, native core utilities with a few from NetBSD Default user interface Graphical (Multi-touch) License Apache License 2.0 Linux kernel patches under GNU GPL v2 [4] Official website www.android.com Android is an operating system based on the Linux kernel, and designed primarily for touchscreen mobile devices such as smartphones and tablet computers. Initially developed by Android, Inc., which Google backed financially Android (operating system) 2 and later bought in 2005, Android was unveiled in 2007 along with the founding of the Open Handset Alliance: a consortium of hardware, software, and telecommunication companies devoted to advancing open standards for mobile devices. The first publicly available smartphone running Android, the HTC Dream, was released on October 22, 2008. The user interface of Android is based on direct manipulation, using touch inputs that loosely correspond to real-world actions, like swiping, tapping, pinching and reverse pinching to manipulate on-screen objects. Internal hardware such as accelerometers, gyroscopes and proximity sensors are used by some applications to respond to additional user actions, for example adjusting the screen from portrait to landscape depending on how the device is oriented. -

History and Evolution of the Android OS
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Springer - Publisher Connector CHAPTER 1 History and Evolution of the Android OS I’m going to destroy Android, because it’s a stolen product. I’m willing to go thermonuclear war on this. —Steve Jobs, Apple Inc. Android, Inc. started with a clear mission by its creators. According to Andy Rubin, one of Android’s founders, Android Inc. was to develop “smarter mobile devices that are more aware of its owner’s location and preferences.” Rubin further stated, “If people are smart, that information starts getting aggregated into consumer products.” The year was 2003 and the location was Palo Alto, California. This was the year Android was born. While Android, Inc. started operations secretly, today the entire world knows about Android. It is no secret that Android is an operating system (OS) for modern day smartphones, tablets, and soon-to-be laptops, but what exactly does that mean? What did Android used to look like? How has it gotten where it is today? All of these questions and more will be answered in this brief chapter. Origins Android first appeared on the technology radar in 2005 when Google, the multibillion- dollar technology company, purchased Android, Inc. At the time, not much was known about Android and what Google intended on doing with it. Information was sparse until 2007, when Google announced the world’s first truly open platform for mobile devices. The First Distribution of Android On November 5, 2007, a press release from the Open Handset Alliance set the stage for the future of the Android platform. -

Devices, the Weak Link in Achieving an Open Internet
Smartphones, tablets, voice assistants... DEVICES, THE WEAK LINK IN ACHIEVING AN OPEN INTERNET Report on their limitations and proposals for corrective measures French République February 2018 Devices, the weak link in achieving an open internet Content 1 Introduction ..................................................................................................................................... 5 2 End-user devices’ possible or probable evolution .......................................................................... 7 2.1 Different development models for the main internet access devices .................................... 7 2.1.1 Increasingly mobile internet access in France, and in Europe, controlled by two main players 7 2.1.2 In China, mobile internet access from the onset, with a larger selection of smartphones .................................................................................................................................. 12 2.2 Features that could prove decisive in users’ choice of an internet access device ................ 14 2.2.1 Artificial intelligence, an additional level of intelligence in devices .............................. 14 2.2.2 Voice assistance, a feature designed to simplify commands ........................................ 15 2.2.3 Mobile payment: an indispensable feature for smartphones? ..................................... 15 2.2.4 Virtual reality and augmented reality, mere goodies or future must-haves for devices? 17 2.2.5 Advent of thin client devices: giving the cloud a bigger role? -

Android Programming Introduction
Android Programming Introduction Riya Jacob K Dept of BCA 2020 - 21 Modules 5 Modules 1 Module: Introduction & installation of Android(12 T+3L) 2 Module : Understanding Android Resources(12 T + 3L) 3 Module : UI development in Android (12 T + 3L) 4 Module : Android Menus (12 T+ 3L) 5Module : Data storing &file saving concept (12 T + 3 L) Module 1 History of Android Android software stack Developing end user application using android SDK Android java packages, Setting up the development environment, Installing android development tools (ADT) Fundamental components Android virtual devices, Running on real device Structure of android application Application life cycle. Introduction Android is an open source and Linux- based Operating System for mobile devices such as smartphones and tablet computers. Android was developed by the Open Handset Alliance, led by Google, and other companies. Android offers a unified approach to application development for mobile devices which means developers need only develop for Android, and their applications should be able to run on different devices powered by Android. Intro. The first beta version of the Android Software Development Kit (SDK) was released by Google in 2007 where as the first commercial version, Android 1.0, was released in September 2008. On June 27, 2012, at the Google I/O conference, Google announced the next Android version, 4.1 Jelly Bean. Jelly Bean is an incremental update, with the primary aim of improving the user interface, both in terms of functionality and performance. The source code for Android is available under free and open source software licenses. Google publishes most of the code under the Apache License version 2.0 and the rest, Linux kernel changes, under the GNU General Public License version 2. -

Content Distribution for Mobile Internet: a Cloud-Based Approach Zhenhua Li Guihai Chen Tsinghua University Shanghai Jiao Tong University Beijing Shanghai China China
Zhenhua Li · Yafei Dai Guihai Chen · Yunhao Liu Content Distribution for Mobile Internet: A Cloud-based Approach Zhenhua Li Guihai Chen Tsinghua University Shanghai Jiao Tong University Beijing Shanghai China China Yafei Dai Yunhao Liu Peking University Tsinghua University Beijing Beijing China China ISBN 978-981-10-1462-8 ISBN 978-981-10-1463-5 (eBook) DOI 10.1007/978-981-10-1463-5 Library of Congress Control Number: 2016943326 © Springer Science+Business Media Singapore 2016 This work is subject to copyright. All rights are reserved by the Publisher, whether the whole or part of the material is concerned, specifically the rights of translation, reprinting, reuse of illustrations, recitation, broadcasting, reproduction on microfilms or in any other physical way, and transmission or information storage and retrieval, electronic adaptation, computer software, or by similar or dissimilar methodology now known or hereafter developed. The use of general descriptive names, registered names, trademarks, service marks, etc. in this publication does not imply, even in the absence of a specific statement, that such names are exempt from the relevant protective laws and regulations and therefore free for general use. The publisher, the authors and the editors are safe to assume that the advice and information in this book are believed to be true and accurate at the date of publication. Neither the publisher nor the authors or the editors give a warranty, express or implied, with respect to the material contained herein or for any errors or omissions that may have been made. Printed on acid-free paper This Springer imprint is published by Springer Nature The registered company is Springer Science+Business Media Singapore Pte Ltd. -

Android Y Open Handset Alliance Santiago Diaz Peña
Android y Open Handset Alliance Santiago Diaz Peña Trabajo Práctico TAI2 2010 Ing. Juan de Urraza Ingeniería Informática Universidad Católica “Nuestra Señora de la Asunción” Asunción, Paraguay 1 Introducción En el 2005, Google adquirió Android, una pequeña compañía que recién comenzaba. Los fundadores de Android fueron a trabajar a Google. En ese entonces, era poco lo que se conocía sobre Android, solo que desarrollaban software para teléfonos móviles. Esto genero rumores de que Google estaba planeando entrar en el mercado de la telefonía móvil. En Google, un equipo desarrolló una plataforma para dispositivos móviles basado en el kernel de Linux los cuales fueron promocionados a los fabricantes y prestadores de servicios móviles a partir de la premisa de aportar una sistema flexible y fácilmente actualizable. La Open Handset Alliance fue creada a finales de 2007, liderado por Google con 34 miembros más, incluyendo fabricantes de dispositivos móviles, desarrolladores de aplicación, algunos prestadores de servicios de telefonía móvil y fabricantes de semi-conductores. Android, el software insignia de la alianza, es creado a partir de una licencia de open source y compite contra otras plataformas móviles propietario de Apple, Microsoft, Nokia, Palm, Symbian. El primer teléfono móvil corriendo Android comercialmente disponible es el T-Mobile G1, también conocido como el HTC Dream. Fue aprobado por la FCC en agosto del 2008, estuvo finalmente disponible a finales de octubre. Android nació a partir de la necesidad de crear un plataforma abierta y libre, que pueda ser actualizada, mejorada, modificada para cualquier tipo de teléfono móvil especifico con sus problemas de heterogeneidad por la comunidad de software libre, completa, es decir que tenga todas las funcionalidades que tiene cualquier otra plataforma propietario. -

Android (Operating System) 1 Android (Operating System)
android text PDF generated using the open source mwlib toolkit. See http://code.pediapress.com/ for more information. PDF generated at: Sun, 11 Sep 2011 07:56:19 UTC Android (operating system) 1 Android (operating system) Android Home screen displayed by Samsung Nexus S with Google, running Android 2.3 "Gingerbread" Company / developer Google Inc, Open Handset Alliance [1] Programmed in C (core), Java (UI), C++ Working state Current [2] [3] Source model Mixed (free and open source software and proprietary software) Initial release 21 October 2008 [4] [4] Latest stable release Tablets: 3.2 (Honeycomb) Phones: 2.3.6 (Gingerbread) / 2 September 2011 Package manager APK [5] [6] Supported platforms ARM, MIPS, x86 Kernel type Linux kernel (monolithic) Android (operating system) 2 Default user interface Graphical [7] License Apache License 2.0 before 3.0, closed source for 3.0, 3.1 and 3.2: Linux kernel patches under GNU GPL v2 [8] Official website android.com Android is an operating system for mobile devices such as smartphones and tablet computers. It is developed by the Open Handset Alliance led by Google.[9] [10] Google purchased the initial developer of the software, Android Inc., in 2005.[11] The unveiling of the Android distribution on 5 November 2007 was announced with the founding of the Open Handset Alliance, a consortium of 84 hardware, software, and telecommunication companies devoted to advancing open standards for mobile devices.[12] [13] [14] [15] Google released most of the Android code under the Apache License, a free software license.[16] The Android Open Source Project (AOSP) is tasked with the maintenance and further development of Android.[17] Android consists of a kernel based on the Linux kernel, with middleware, libraries and APIs written in C and application software running on an application framework which includes Java-compatible libraries based on Apache Harmony. -

Android – the First Truly Open and Complete Platform for Mobile Devices
#50 Android – the first truly open and complete platform for mobile devices Android is a new open-source platform for mobile «Android is the first truly open and comprehensive plat- phones. With its solid Linux foundation, a very busi- form for mobile devices. It includes an operating system, ness-friendly open-source license and an easy-to-use user-interface and applications – all of the software to Java programming model, it provides a perfect basis run a mobile phone, but without the proprietary obst- for mobile applications – and beyond. As part of the acles that have hindered mobile innovation. We have Open Handset Alliance that guides Android‘s evolution, developed Android in cooperation with the Open Hand- Noser Engineering AG contributed functionality to the set Alliance, which consists of more than 30 technology core platform. and mobile leaders including Motorola, Qualcomm, HTC and T-Mobile. Through deep partnerships with carriers, device manufacturers, developers, and others, we hope to enable an open ecosystem for the mobile world by creating a standard, open mobile software platform. We think the result will ultimately be a better and faster pace for innovation that will give mobile customers unforeseen applications and capabilities.» Andy Rubin Director of Mobile Platforms at Google, official Google Blog entry 11/5/2007 NOSER ENGINEERING AG WINTERTHUR I LUZERN I BERN I MÜNCHEN RUDOLF-DIESEL-STRASSE 3 GALGENFELDWEG 18 WWW.NOSER.COM CH-8404 WINTERTHUR CH-3006 BERN [email protected] TEL +41 52 234 56 11 TEL +41 31 917 45 11 PLATZ 4 BERNABEISTR. 1 CH-6039 ROOT D4 C/O STEUERKANZLEI SCHNEIDER GERALD TEL +41 41 455 66 11 DE-80639 MÜNCHEN TEL +41 52 234 56 11 The Project As part of the Open Handset Alliance and on behalf of Google, Noser Engineering AG contributed the larger part of the so-called «Android core libraries». -

Android – the First Truly Open and Complete Platform for Mobile Devices
Android – the first truly open and complete platform for mobile devices KNOW-HOW # 50 Android is a new open-source platform for mobile phones. With its solid Linux foundation, a very business-friendly open-source license and an easy-to-use Java programming model, it provides a perfect basis for mobile applications – and beyond. As part of the Open Handset Alliance that guides Android‘s evolution, Noser Engineering AG contributed functionality to the core platform. «Android is the first truly open and comprehensive platform for mobile devices. It includes an operating system, user-interface and applications – all of the software to run a mobile phone, but without the proprietary obstacles that have hindered mobile innovation. We have developed Android in cooperation with the Open Handset Alliance, which consists of more than 30 technology and mobile leaders including Motorola, Qualcomm, HTC and T-Mobile. Through deep partnerships with carriers, device manufacturers, developers, and others, we hope to enable an open ecosystem for the mobile world by creating a standard, open mobile software platform. We think the result will ultimately be a better and faster pace for innovation that will give mobile customers unforeseen applications and capabilities.» Andy Rubin, Director of Mobile Platforms at Google, official Google Blog entry 11/5/2007 we know how The project As part of the Open Handset Alliance and on behalf of Google, Noser Engineering AG contributed the larger part of the so-called «Android core libraries». These are basically a set of libraries that provide most of the functionality typically found in desktop implementations of the Java programming language, but adapted to and optimized for a mobile device. -
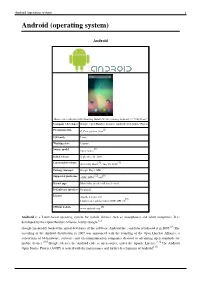
Android (Operating System) 1 Android (Operating System)
Android (operating system) 1 Android (operating system) Android Home screen displayed by Samsung Galaxy Nexus, running Android 4.1 "Jelly Bean" Company / developer Google, Open Handset Alliance, Android Open Source Project [1] Programmed in C, C++, python, Java OS family Linux Working state Current [2] Source model Open source Initial release September 20, 2008 [3] [4] Latest stable release 4.1.1 Jelly Bean / July 10, 2012 Package manager Google Play / APK [5] [6] Supported platforms ARM, MIPS, x86 Kernel type Monolithic (modified Linux kernel) Default user interface Graphical License Apache License 2.0 [7] Linux kernel patches under GNU GPL v2 [8] Official website www.android.com Android is a Linux-based operating system for mobile devices such as smartphones and tablet computers. It is developed by the Open Handset Alliance, led by Google.[2] Google financially backed the initial developer of the software, Android Inc., and later purchased it in 2005.[9] The unveiling of the Android distribution in 2007 was announced with the founding of the Open Handset Alliance, a consortium of 86 hardware, software, and telecommunication companies devoted to advancing open standards for mobile devices.[10] Google releases the Android code as open-source, under the Apache License.[11] The Android Open Source Project (AOSP) is tasked with the maintenance and further development of Android.[12] Android (operating system) 2 Android has a large community of developers writing applications ("apps") that extend the functionality of the devices. Developers write primarily in a customized version of Java.[13] Apps can be downloaded from third-party sites or through online stores such as Google Play (formerly Android Market), the app store run by Google.