Conference Brochure
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
SFLC V Conservancy
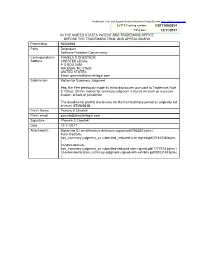
Trademark Trial and Appeal Board Electronic Filing System. http://estta.uspto.gov ESTTA Tracking number: ESTTA863914 Filing date: 12/11/2017 IN THE UNITED STATES PATENT AND TRADEMARK OFFICE BEFORE THE TRADEMARK TRIAL AND APPEAL BOARD Proceeding 92066968 Party Defendant Software Freedom Conservancy Correspondence PAMELA S CHESTECK Address CHESTEK LEGAL P O BOX 2492 RALEIGH, NC 27602 UNITED STATES Email: [email protected] Submission Motion for Summary Judgment Yes, the Filer previously made its initial disclosures pursuant to Trademark Rule 2.120(a); OR the motion for summary judgment is based on claim or issue pre- clusion, or lack of jurisdiction. The deadline for pretrial disclosures for the first testimony period as originally set or reset: 07/20/2018 Filer's Name Pamela S Chestek Filer's email [email protected] Signature /Pamela S Chestek/ Date 12/11/2017 Attachments Motion for SJ on affirmative defenses-signed.pdf(756280 bytes ) Kuhn-Declara- tion_summary-judgment_as-submitted_reduced-size-signed.pdf(2181238 bytes ) Sandler-declara- tion_summary-judgment_as-submitted-reduced-size-signed.pdf(1777273 bytes ) Chestek declaration_summary-judgment-signed-with-exhibits.pdf(2003142 bytes ) IN THE UNITED STATES PATENT AND TRADEMARK OFFICE BEFORE THE TRADEMARK TRIAL AND APPEAL BOARD In the Mater of Registraion No. 4212971 Mark: SOFTWARE FREEDOM CONSERVANCY Registraion date: September 25, 2012 Sotware Freedom Law Center Peiioner, v. Cancellaion No. 92066968 Sotware Freedom Conservancy Registrant. RESPONDENT’S MOTION FOR SUMMARY JUDGMENT ON ITS AFFIRMATIVE DEFENSES Introducion The Peiioner, Sotware Freedom Law Center (“SFLC”), is a provider of legal services. It had the idea to create an independent enity that would ofer inancial and administraive services for free and open source sotware projects. -

Augmenting Your IP Portfolio Is Virtually the Only Way to Compete in AR/VR
The GLOBAL REACH, LOCAL KNOWLEDGE www.patentlawyermagazine.com May / June 2021 Augmenting your IP portfolio is virtually the only way to compete in AR/VR TH AM U ER O I S C A Law firm RANKINGS Finnegan, Henderson, Farabow, Garrett & Dunner, LLP experts Christopher Howes, Zachery Olah, Forrest Jones, and Karthik Kumar, discuss the developments in the augmented and virtual reality sphere with advice for protecting innovation. Ismat Levin, Automated Inde niteness Synamedia patent analysis Page 60 Page 12 Page 24 Front cover_TPL54_v3.indd 1 22/06/2021 16:22 EDITOR’S WELCOME The May / June 2021 GLOBAL REACH, LOCAL KNOWLEDGE www.patentlawyermagazine.com Augmenting your IP portfolio is virtually the only way to compete in AR/VR Editor’s H AM UT ER O IC S A Law firm RANKINGS welcome Finnegan, Henderson, Farabow, Garrett & Dunner, LLP experts Christopher Howes, Zachery Olah, Forrest Jones, and Karthik Kumar, discuss the developments in the augmented and virtual reality sphere with advice for protecting innovation. IndeĀ niteness Automated Page 60 Ismat Levin, patent analysis Synamedia Page 24 ith the global circumstances of the past year limiting our Page 12 activities, it is no surprise that virtual realty has become a 22/06/2021 16:22 greater focus than ever. As consumers, we have technology d 1 W at our fingertips that was mere science fiction only a few decades ago. THE PATENT LAWYER So, what can we expect of the future of augmented and virtual reality, Issue 54 and how can that innovation be protected? Finnegan, Jederson, Farabow, Garrett & Dunner, LLP discuss in our cover story this issue. -

THE DEFENSIVE PATENT PLAYBOOK James M
THE DEFENSIVE PATENT PLAYBOOK James M. Rice† Billionaire entrepreneur Naveen Jain wrote that “[s]uccess doesn’t necessarily come from breakthrough innovation but from flawless execution. A great strategy alone won’t win a game or a battle; the win comes from basic blocking and tackling.”1 Companies with innovative ideas must execute patent strategies effectively to navigate the current patent landscape. But in order to develop a defensive strategy, practitioners must appreciate the development of the defensive patent playbook. Article 1, Section 8, Clause 8 of the U.S. Constitution grants Congress the power to “promote the Progress of Science and useful Arts, by securing for limited Times to Authors and Inventors the exclusive Right to their respective Writings and Discoveries.”2 Congress attempts to promote technological progress by granting patent rights to inventors. Under the utilitarian theory of patent law, patent rights create economic incentives for inventors by providing exclusivity in exchange for public disclosure of technology.3 The exclusive right to make, use, import, and sell a technology incentivizes innovation by enabling inventors to recoup the costs of development and secure profits in the market.4 Despite the conventional theory, in the 1980s and early 1990s, numerous technology companies viewed patents as unnecessary and chose not to file for patents.5 In 1990, Microsoft had seven utility patents.6 Cisco © 2015 James M. Rice. † J.D. Candidate, 2016, University of California, Berkeley, School of Law. 1. Naveen Jain, 10 Secrets of Becoming a Successful Entrepreneur, INC. (Aug. 13, 2012), http://www.inc.com/naveen-jain/10-secrets-of-becoming-a-successful- entrepreneur.html. -

Cip Forum 2016 Göteborg 25 - 27 Sept Convergence Cip Forum 2016 | Program
CIP FORUM 2016 GÖTEBORG 25 - 27 SEPT CONVERGENCE CIP FORUM 2016 | PROGRAM All text material in the CIP FORUM 2016 Program brochure, is provided under a Creative Commons Attribution 3.0 License. Quotes and images may be subjected to copyright held by third parties and are not included under this license. LAYOUT & PRODUCTION PRINTING Anna Holmberg University of Gothenburg Linn Holmström Natalie Lorin CIP FORUM 2016 | PROGRAM CONTENTS WELCOME TO CIP FORUM 2016 7 CIP FORUM – WE’RE BACK 8 COLLABORATION PARTNERS 10 CIP.... AND THEN THERE WERE THREE 11 STUDENT PARTICIPATION 12 SPEAKERS 13 PROGRAM OVERVIEW 23 SESSION OVERVIEW 24 CONFERENCE VENUES 33 PRACTICAL INFORMATION 34 NOTE PAGES 35 CALL CENTER INFORMATION AND TRANSPORTATION +46 76 - 618 26 14 CIP FORUM 2016 | PROGRAM CONVERGENCE We are in the midst of a convergent world where the storms of disruptive change are brewing. Industries, universities, and nations alike will need to take heed. Some actors will define the future and others will have the future define them. Which one will you be? CIP FORUM 2016 | PROGRAM CIP FORUM 2016 WELCOME TO GÖTEBORG for the seventh addition of CIP FORUM. For those first- time participants, we are happy to welcome you not only to our city and event, but to our CIP community of academics, executives, policy-makers, professionals, students, and alumni gathered around the common goal of transforming knowledge into wealth and welfare. For those past-participants, we hope to reward your patience since the last event with another impressive program whose theme of convergence promises to deliver a new set of opportunities and challenges on the winding road to economic growth and prosperity in the knowledge economy. -

Toyota Activities for OSS Compliance
Toyota Activities for OSS Compliance Masato Endo Assistant Manager Connected Vehicle Group Intellectual Property Div. Toyota Motor Corporation Nov. 16, 2017, Open Compliance Summit © 2017 Toyota Motor Corporation 1 1.1. Expansion of OSS in the Automotive Sector Automotive sector Toyota products In the automotive sector, the number of OSS projects is growing rapidly, and some are already available on the market. Nov. 16, 2017, Open Compliance Summit © 2017 Toyota Motor Corporation 2 1.2. What is Automotive Grade Linux (AGL) AGL is a Linux Foundation project to develop an operating system for infotainment platforms. Nov. 16, 2017, Open Compliance Summit © 2017 Toyota Motor Corporation 3 1.3. AGL Members Ten global OEMs have joined the project. Many automotive industry suppliers and IT companies also contribute to AGL. Nov. 16, 2017, Open Compliance Summit © 2017 Toyota Motor Corporation 4 1.4. Recent AGL Activities AGL All Member Meeting Automotive Linux Summit (Feb 8 to Feb 10) (May 31 to June2) AGL holds many events to foster community engagement. These events include not only discussions of technical issues, but also of legal issues. Nov. 16, 2017, Open Compliance Summit © 2017 Toyota Motor Corporation 5 1.5. Toyota and AGL (1/5) 2011 Toyota joined the Linux Foundation. 1st ALS: Automotive Linux Summit (Yokohama, Japan) Nov. 16, 2017, Open Compliance Summit © 2017 Toyota Motor Corporation 6 1.6. Toyota and AGL (2/5) 2011 2012 2013 2014 Automotive Linux Summit 2014 (Tokyo, Japan) AGL Steering Committee Meeting: • AGL projects started and funded. Nov. 16, 2017, Open Compliance Summit © 2017 Toyota Motor Corporation 7 1.7. -

CLE Materials
Software Freedom Law Center Fall Conference at Columbia Law School CLE materials October 30, 2015 License Compliance Dispute Resolution Software Freedom Law Center October 30, 2015 1) Software Freedom Law Center: Guide to GPL Compliance 2nd Edition 2) Free Software Foundation: Principles for Community-Oriented GPL Enforcement 3) Terry J. Ilardi: FOSS Compliance @ IBM 15 Years (and count- ing) Software Freedom Law Center Guide to GPL Compliance 2nd Edition Eben Moglen & Mishi Choudhary October 31, 2014 Contents TheWhat,WhyandHowofGNUGPL . 3 CopyrightandCopyleft . 4 Concepts and License Mechanics of Copyleft. 6 LicenseProvisionsAnalyzed. 10 GPLv2............................... 10 GPLv3............................... 18 GPLSpecialExceptionLicenses . 31 AGPL............................... 31 LGPL ............................... 34 Understanding Your Compliance Responsibilities . 41 WhoHasComplianceObligations? . 41 HowtoMeetComplianceObligations . 43 TheKeytoComplianceisGovernance . 45 PrinciplesofPreparedCompliance . 47 HandlingComplianceInquiries . 48 Appendix1: OfferofSourceCode . 52 References................................ 56 This document presents the legal analysis of the Software Freedom Law Center and the authors. This document does not express the views, intentions, policy, or legal analysis of any SFLC clients or client organizations. This document does not constitute legal advice or opinion regarding any specific factual situation or party. Specific legal advice should always be sought from qualified legal counsel on the application -

October 20, 2020 / Schedule *All Times Are Eastern Standard
The 2020 schedule is proudly sponsored and made possible by Google Open Source. October 20, 2020 / Schedule *All times are Eastern Standard. All Things Open is made possible by these sponsors Day Two of All Things Open 2020 will feature morning plenary keynotes as well as 45 minute sessions across 24 topic tracks. There is also a Featured Session block from PRESENTING 12:30 - 1:15 pm ET highlighting talks and topics we feel are widely applicable. SPONSORS 8:45AM - 9:00AM Welcome & Keynotes (Main Stage) Todd Lewis, All Things Open KEYNOTES (MAIN STAGE) 9:00AM - 9:15AM 10 Commandments of Navigating Code Reviews Angie Jones, Applitools 9:20AM - 9:35AM Security is Everyone’s Responsibility PLATINUM Marten Mickos, HackerOne SPONSORS 9:40AM - 10:00AM An Animated Guide to Vue 3 Reactivity and Internals Sarah Drasner, Netlify 10:05AM - 10:20AM Open Source Licenses at the Center Chris DiBona, Google 10:20AM - 10:30AM BREAK - NETWORKING/SPONSORS 10:30AM - 11:15AM Sessions (See Next Page) 11:15am - 11:30PM BREAK GOLD SPONSORS 11:30AM - 12:15PM Sessions (See Next Page) 12:15PM - 12:30PM BREAK 12:30PM - 1:15PM Featured Sessions (See Next Page) 1:15PM - 1:30PM BREAK 1:30PM - 2:15PM Sessions (See Next Page) 2:15PM - 2:30PM BREAK 2:30PM - 3:15PM Sessions (See Next Page) SILVER SPONSORS 3:15PM - 3:30PM BREAK 3:30PM - 4:15PM Sessions (See Next Page) 4:15PM - 4:30PM BREAK 4:30PM - 5:15PM Sessions (See Next Page) 5:15PM - 5:30PM Final comments and wrap-up (Main Stage) Todd Lewis, All Things Open BRONZE SPONSORS Commersetools hyper63 Confluent MySQL cprime Syncfusion Elastic TerminusDB Please note, minor changes to the schedule are possible prior to event date. -

News@UK the Newsletter of UKUUG, the UK’S Unix and Open Systems Users Group Published Electronically At
news@UK The Newsletter of UKUUG, the UK's Unix and Open Systems Users Group Published electronically at http://www.ukuug.org/newsletter/ Volume 17, Number 3 ISSN 0965-9412 September 2008 Contents News from the Secretariat 3 Chairman's report 3 LISA '08 announcement 4 OSCON 2008 5 Open Tech 2008 (1) 7 Open Tech 2008 (2) 8 Linux kernel resource allocation in virtualized environments 8 Fear and Loathing in the Routing System 10 Hardware review: Fujitsu Siemens Esprimo P2411 15 Book review: Java Pocket Guide 16 Book review: CakePHP Application Development 16 Book review: The Gift: How the Creative Spirit Transforms the World 17 Book review: Intellectual Property and Open Source 18 Contributors 19 Contacts 20 news@UK UKUUG Newsletter News from the Secretariat Jane Morrison On 30th June UKUUG, in conjunction with O'Reilly, organised a successful tutorial on Moodle. This event was the first of many we hope to bring you in the future with UKUUG working alongside O'Reilly. Josette Garcia has access to many authors who can also be of interest to our membership by providing tutorials etc. OpenTech 2008 (organised by Council member Sam Smith), was an exceptional success with some 600 people attending. Two accounts of the event appear in this Newsletter. The 2008 event was so successful that plans are going forward for a similar event in early July 2009. The Linux event this year has been delayed to November and you should find enclosed in this Newsletter the provisional programme and booking information. On 26th November we are organising the OpenBSD's PF tutorial by Peter N M Hansteen. -

Safe Cities, the Smart Way
MAR / APR 2020 SAFE CITIES, THE SMART WAY In Focus In Focus Security Feature Security Feature How To Navigate Tips For Small Business Intrusion And A Ransomware Ransomware Cybersecurity Access Control: Recovery Protection On Threats And How The Perfect Pair For Process Windows Systems To Fix the Fox Facility Security SST COVER.indd 1 5/3/20 4:06 PM At GSX2020, thousands of executives and decision makers will be actively assessing the latest security technologies and solutions. of them don’t attend other events.* Let’s discuss how we can support your business development goals. SECURE YOUR BOOTH SPACE TODAY GSX.org/exhibit Untitled-2Untitled-4 1 8/1/205/3/20 9:553:11 AMPM Untitled-4 1 5/3/20 3:12 PM 2 CONTENT SECURITY SOLUTIONS TODAY IN THIS ISSUE 6 Calendar Of Events 8 Editor’s Note 10 In The News Updates From Asia And Beyond 32 Cover Story Cover Story Safe Cities, The Safe Cities, The Smart Way 32 | Smart Way 37 Security Feature + How Can A Digital Twin Create A Seamless Workplace For Employees? + How Businesses Need To Show How AI Decides + Small Business Cybersecurity Threats And How To Fix The Fox + Working Smarter: The Intelligent Office + Increasing Business ROI With IoT In Facilities Management + Check Point Software Fast Tracks Network Security With New Security Gateways Security Feature + Commercial Applications For Cutting-Edge Small Business Cybersecurity Threats And How to Fix the Fox Intrusion And Alarm Tech 37 | + Tech Trends: Put Radar On Your Radar + Lidar Comes Of Age In Security + Intrusion And Access Control: The Perfect -

Redacted Saurabh Dutta System Design and Management Program, MIT May 10, 2017
Striking a balance between usability and cyber-security in loT Devices by Saurabh Dutta M.S. Architecture and Design, 2009 Mississippi State University Submitted to the System Design and Management Program in Partial Fulfillment of the Requirements for the Degree of Master of Science in Engineering and Management at the Massachusetts Institute of Technology June 2017 @ 2017 Saurabh Dutta. All rights reserved The author hereby grants to MIT permission to reproduce and to distribute publicly paper and electronic copies of this thesis document in whole or in part in any medium now known or hereafter created. Signature of Author: Signature redacted Saurabh Dutta System Design and Management Program, MIT May 10, 2017 Certified by: /Signature redacted Thesis Supervisor: Professor Stuart Madnick John Norris Maguire Professor of Information Technologies, MIT Sloan School of Management Professor of Engineering Systems, MIT School of Engineering Signature redacted Accepted by: 1' Joan S Rubin Executive Director, System Design & Management Program, MIT MASSCF1JETS INSTITUTE OF TEQHNOLOGY JUN 2 7017 LIBRARIES (This page left intentionally blank) 2 Striking a balance between usability and cyber-security in loT Devices By Saurabh Dutta Submitted to the System Design and Management Program on May 12, 2017 in Partial fulfillment of the requirements for the Degree of Master of Science in Engineering and Management. ABSTRACT Today more and more physical objects are being connected to internet. The Internet of Things, or loT, is dramatically changing the way of living and the way we interact with things and each other. Home doors can be opened remotely with a watch, cars' performance can be upgraded remotely, devices monitor health and send updates to physicians remotely. -

Out of the Blocks – Mitigating Patent Risk Over Distributed Ledgers
Summer 2020 94 Market focus | New tech www.IAM-media.com Out of the blocks – mitigating patent risk over distributed ledgers This rapidly developing technology is set to be hugely disruptive across a range of sectors. Companies should act fast to ensure they are aware of the IP risks By Mehdi Ansari, Jay Thornton, Raffaele DeMarco and Rudy Kleysteuber ew recent digital innovations have captured existence of such patent rights, which apply to various the business community’s imagination more components of distributed ledger technology, suggests Fthan blockchain and other distributed ledger that many of the companies building, acquiring or technologies. These technologies not only enable bitcoin, otherwise deploying distributed ledgers (or those that Ether and other cryptocurrencies or crypto-assets, some plan to do so in the future) may be at risk of patent innovators have devised diverse new commercial uses liability and litigation down the road. for them – from global supply-chain tracking, energy This article first describes and discusses the growing distribution and trading to secure digital identity volume of these patents and patent applications – along management and tamper-proof voting and elections. with the resulting risks and opportunities that arise for Some commentators predict that these systems will various players – and second proposes some potential become the new fabric of commercial exchange and will mitigation strategies to address such risks. generate hundreds of billions of dollars of economic value-add in the coming decades. While only time will tell whether distributed ledgers are a truly paradigm- shifting innovation, current figures suggest that companies are already spending several billion dollars a year to build or deploy such systems, with these amounts forecast to rise even further. -

Hacking the Patent System
Hacking the Patent System A Guide to Alternative Patent Licensing for Innovators By Marta Belcher and John Casey Juelsgaard Intellectual Property & Innovation Clinic Stanford Law School May 2014 Table of Contents Introduction to Alternative Patent Licensing…………………………………….1 The Patent System Is Broken…………………………………………………………1 Innovators Are Hacking the System to Use Patents for Good………………...1 Opting Out of the Patent System May Not Solve the Problem…………..……2 Defensive Patent Aggregators………………………………………………..………3 Unified Patents………………………………………………......……………………..4 Allied Security Trust (AST)………………………………………………………….…5 RPX……………………………………………………………………………………..…7 Patent Pledges………………………………………………………………………………9 Defensive Patent License (DPL)…………………………………..…………………9 Open Invention Network (OIN) ……………………………………...……………11 Twitter’s Innovator’s Patent Agreement (IPA).……………………………….…12 Google’s License on Transfer (LOT) Agreement…………………………….….14 Comparison Tables………………………………………………………………………16 This work is licensed under a Creative Commons Attribution 4.0 International License i Introduction to Alternative Patent Licensing The patent system is intended to incentivize innovation, but the current system often does the opposite. The traditional model of patent licensing—whereby a company pays a patent owner to license an invention that the company legitimately uses—has been hijacked by non-practicing entities (“patent trolls”) and other aggressive patent holders who assert overbroad patents that never should have been granted in the first place. Within this broken patent regime, companies are increasingly hacking the system—that is, finding alternatives to the traditional patent licensing model in order to both promote open innovation and protect the companies themselves. These patent system hacks can be organized into two broad categories: (1) defensive patent aggregators, which pool member companies’ resources to defensively purchase patents for the group and to fight patent trolls, and (2) patent pledges, whereby companies opt to openly and defensively license their patents to others.