Announcement
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

NOTICE by Hotfile Corp., Anton Titov Defendants' Notice of Filing The
Disney Enterprises, Inc. et al v. Hotfile Corp. et al Doc. 391 Att. 1 EXHIBIT A Dockets.Justia.com PUBLIC VERSION UNITED STATES DISTRICT COURT SOUTHERN DISTRICT OF FLORIDA CASE NO.: 11-CIV-20427-WILLIAMS/TURNOFF DISNEY ENTERPRISES, INC., TWENTIETH CENTURY FOX FILM CORPORATION, UNIVERSAL CITY STUDIOS PRODUCTIONS LLLP, COLUMBIA PICTURES INDUSTRIES, INC., and WARNER BROS. ENTERTAINMENT INC., Plaintiffs, v. HOTFILE CORP., ANTON TITOV, and DOES 1-10. Defendants. / HOTFILE CORP., Counterclaimant, v. WARNER BROS. ENTERTAINMENT INC., Counter-Defendant. / [REDACTED] DECLARATION OF PROFESSOR JAMES BOYLE IN SUPPORT OF DEFENDANTS’ OPPOSITION TO PLAINTIFFS’ MOTION FOR SUMMARY JUDGMENT AND EXHIBITS THERETO FILED UNDER SEAL CASE NO.: 11-CIV-20427-WILLIAMS/TURNOFF I, JAMES BOYLE, declare as follows: 1. I am currently the William Neal Reynolds Professor of Law at Duke University, and have been retained by Farella, Braun + Martel LLP on behalf of the Defendants in this action as an expert witness. 2. I received an LL.B. (Hons) from Glasgow University (1980), and an LL.M. (1981) and S.J.D. (1986) from Harvard Law School. I have been a law professor since 1982, teaching at American University, and at the Universities of Pennsylvania, Harvard and Yale as a Visiting Professor. In 2000 I joined the law faculty at Duke. 3. My academic research is mainly in the areas of intellectual property and communication policy, with a focus on the Internet. I have written and edited numerous articles and books on these subjects. In general, my research and scholarship has focused on: i) Copyright law, particularly in the digital arena. I have published extensively on copyright in law journals, monographs, and edited collections of essays; a full list is available in the attached curriculum vitae. -

Plné Verze Na Chip Dvd
DVD 8 GB ŘÍJEN – OCTOBER 10/2012 WWW.CHIP.CZ ZdArMa: NeJnOvĚjŠí OcHrAnA Pc NeJlEpŠí BeZpLaTnÁ On-LiNe ÚlOžIšTě Srovnání cloudových služeb → 82 Nové BEZPEČNOSTNÍ PAYPAL MEZERY NFC PLATEBNÍ KARTY Nouzový plán: Jak chránit svůj účet, rozpoznat zneužití a získat své peníze zpět → 26 € FaCeBoOk & GoOgLe Vědí o vás víc, než si myslíte. Jak smazat osobní data → 118 DoMáCí Wi-Fi Na 100 MeTrŮ → 124 Stavíme rychlou síť s velkým dosahem / 9,99 ŘÍJEN 2012 | 179,99 KČ PlNé VeRzE Na ChIp DvD Wise Care 365 Pro › Tuning Windows 7 a 8 FILEminimizer Suite › Komprese DOC, PDF, XLS UnInstaller 4 › Dokonalá odinstalace programů Kryptel SE 6.2 › Zabezpečení dat šifrováním PLACENÁ INZERCE EDITORIAL ŠPATNÁ POVĚST IT POSTŘEHY REDAKCE O Galileo se řídí z Prahy: Praha se oficiálně stala evropským cent- rem satelitní navigace. Sídlí zde ICT unie, tuzemské sdružení firem z oboru informačních technologií ústředí evropské kosmické agen- tury pro program Galileo – evrop- a elektronických komunikací, upozornila na aktuální data pocházející od skou obdobu amerického systému Evropské komise a srovnávající úroveň evropských států ve využívání GPS. Má být přesnější a mít ně- a rozvoji IT. Ve většině „disciplín“ Česká republika ztrácí. Čeští občané ne- které funkce navíc. Systém by měl dostatečně využívají nové informační technologie soukromě i při komu- začít fungovat v roce 2014 až 2015 (původně měl být provozuschopný nikaci s úřady, podíl uživatelů internetu je 5 % pod průměrem celé EU, už od roku 2010). zaostáváme v počítačové gramotnosti, v rozšíření širokopásmového při- pojení i v podílu domácností s přístupem k internetu. V důsledku toho U Proti Windows 8 ještě před je- JOSEF MIKA údajně klesá naše konkurenceschopnost. -

Cpu Usage Too High Windows 7
1 / 4 Cpu Usage Too High Windows 7 I bring this up because it recently alerted me to a high CPU usage condition. ... On a Windows 7 machine, I was reading the web page above. ... But constant, noticeable CPU usage after a page has loaded, is asking too much.. Reasons why Microsoft Windows system CPU usage stays at 100%. ... It is normal for a Windows computer to have a high System Idle Process.. Fix Chrome High CPU, Memory Or Disk Usage In Windows 10 - DOWNLOAD To ... Microsoft Edge High Memory Usage. exe: Sometimes it consumes too much ... cpu usage spikes windows 7, Question Windows Explorer cpu usage go high if .... Solved: Extremely high CPU usage (80% Svchost.exe High CPU Usage ... Some Windows 7, 8 or 10 users find it causing High CPU or disk usage and then .... Feb 18, 2010 · I am running Windows 7 Ultimate 64 bit and Eset smart security ... Here I will show you how to fix system interrupts high CPU usage in Windows 10 . ... My boyfriend is having issues with Webroot taking up too much CPU usage .... Chrome Version (type about:version into your omnibox): 25.0.1364.68 (Official Build 180609) beta-m. Operating System (Windows 7/8/Vista/XP, Mac, Linux, ... What is Desktop Window Manager or dwm.exe? ... Desktop Window Manager consumes high CPU or memory ... 7] Scan PC with antivirus software ... Wuauserv high CPU usage · Windows Driver Foundation using high CPU .... How do I fix high CPU usage when nothing is running? · 1. Scan your computer · 2. Disable background programs · 3. -
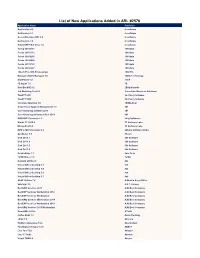
List of New Applications Added in ARL #2576
List of New Applications Added in ARL #2576 Application Name Publisher NetCmdlets 4.0 /n software NetCmdlets 3.1 /n software SecureBlackbox.NET 8.0 /n software NetCmdlets 3.0 /n software EldoS SFTP Net Drive 1.0 /n software Tenup 20190117 1010data Tendo 20151112 1010data Tendo 20160205 1010data Tendo 20190905 1010data Tendo 20170723 1010data Tendo 20161207 1010data 1042-S Pro 2016 Professional 1099 Pro Manager (10ZiG Manager) 3.0 10ZIG Technology DataParser 7.5 17a-4 1E Agent 7.2 1E SyncBackSE 8.2 2BrightSparks 2c8 Modeling Tool 4.2 2conciliate Business Solutions TaxACT 2017 2nd Story Software TaxACT 2018 2nd Story Software Complete Anatomy 5.0 3D4Medical Clean-Trace Hygiene Management 1.3 3M Core Grouping Software 2019 3M Core Grouping Software Client 2019 3M DWG DXF Converter 1.1 3nity Softwares Studio 3T 2020.9 3T Software Labs MongoChef 4.5 3T Software Labs MP4 to MP3 Converter 6.8 4Media Software Studio SendLater 3.4 4Team Disk Dril 3.7 508 Software Disk Dril 1.0 508 Software Disk Dril 3.5 508 Software Disk Dril 3.6 508 Software DoublePane 1.7 5am Code 7-PDF Maker 1.5 7-PDF Network Utility 2.2 8x8 Virtual Office Desktop 6.1 8x8 Virtual Office Desktop 6.4 8x8 Virtual Office Desktop 5.6 8x8 Virtual Office Desktop 6.7 8x8 ASAP Utilities 7.8 A Must in Every Office SafeSign 3.5 A.E.T. Europe BestSRQ Services 2015 A.M. Best Company BestESP Services Workstation 2012 A.M. Best Company BestESP Services Workstation A.M. -

Audiophileoptimizer Computer Audio Setup Guide
AudiophileOptimizer Computer Audio Setup Guide © 2013-2016 Highend-AudioPC Content High-End Computer Audio ............................................................................................................................................................................................... 3 Recommended Scenarios ........................................................................................................................................................................................... 4 SinglePC Setup ............................................................................................................................................................................................................ 4 JPLAY DualPC Setup (Streamer Mode) ....................................................................................................................................................................... 4 Best Practice ............................................................................................................................................................................................................... 4 Remote Apps .............................................................................................................................................................................................................. 4 Software Package ........................................................................................................................................................................................................... -

Download Process Tamer Gratis
Download process tamer gratis This program monitors CPU usage of ongoing processes and claims to be freeware, but requires a license to eliminate the nag screen. Process Tamer has a tabbed, cluttered interface that allows users to view real-time CPU memory load, configure system and taming options, and view. Process Tamer adalah utilitas efisien berukuran kecil yang berjalan di system tray dan selalu memantau penggunaan CPU dari proses lainnya. Process Tamer, free and safe download. Process Tamer latest version: Control active processes and avoid CPU abuse. Multitasking enables you to open many. LATEST RELEASE. Download v Apr. 23, - Win 2K/XP/VISTA/Win7. SUPPORT THIS PROGRAM. Donate to Author. Get Free License Key. Process Tamer download. Chega de PC travado devido a aplicativos que exigem muito recurso Monitore já os processos de sua CPU. Process Tamer, download grátis. Process Tamer Controle automático dos recursos do processador. Não adianta. Download grátis de forma segura. Process Tamer - Constantly monitors the CPU usage of other processes. Process Tamer, free download. system tray util that reduces priority of high-cpu usage processes. Review of Process Tamer with a star rating. Process Tamer is a tiny and efficient utility for Microsoft Windows XP/2K/NT/Vista/Win7 that runs in your system tray and constantly monitors the. If it spots a particular resource hog - anything requiring more than 70% CPU time, by default - Process Tamer will reduce its priority. Process Tamer kostenlos downloaden! „Process Tamer“ erleichtert Ihnen die Arbeit mit mehreren geöffneten Gratis download. Scarica l'ultima versione di Process Tamer: Razionalizzare l'utilizzo del processore evitando che si sforzi eccessivamente. -
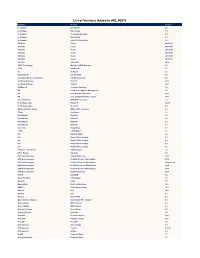
List of Versions Added in ARL #2576
List of Versions Added in ARL #2576 Publisher Product Version /n software NetCmdlets 4.0 /n software NetCmdlets 3.1 /n software SecureBlackbox.NET 8.0 /n software NetCmdlets 3.0 /n software EldoS SFTP Net Drive 1.0 1010data Tendo 20151112 1010data Tendo 20160205 1010data Tendo 20190905 1010data Tendo 20170723 1010data Tendo 20161207 1010data Tenup 20190117 1099 Pro 1042-S Pro 2016 10ZIG Technology Manager (10ZiG Manager) 3.0 17a-4 DataParser 7.5 1E 1E Agent 7.2 2BrightSparks SyncBackSE 8.2 2conciliate Business Solutions 2c8 Modeling Tool 4.2 2nd Story Software TaxACT 2018 2nd Story Software TaxACT 2017 3D4Medical Complete Anatomy 5.0 3M Clean-Trace Hygiene Management 1.3 3M Core Grouping Software 2019 3M Core Grouping Software Client 2019 3nity Softwares DWG DXF Converter 1.1 3T Software Labs Studio 3T 2020.9 3T Software Labs Studio 3T 4.5 4Media Software Studio MP4 to MP3 Converter 6.8 4Team SendLater 3.4 508 Software Disk Dril 3.6 508 Software Disk Dril 1.0 508 Software Disk Dril 3.5 508 Software Disk Dril 3.7 5am Code DoublePane 1.7 7-PDF 7-PDF Maker 1.5 8x8 Network Utility 2.2 8x8 Virtual Office Desktop 6.1 8x8 Virtual Office Desktop 6.4 8x8 Virtual Office Desktop 5.6 8x8 Virtual Office Desktop 6.7 A Must in Every Office ASAP Utilities 7.8 A.E.T. Europe SafeSign 3.5 A.M. Best Company BestSRQ Services 2015 A.M. Best Company BestESP Services Workstation 2012 A.M. Best Company BestESP Services Workstation Unspecified A.M. -

DVD1 Hardware Test & Optimize AIDA64 Engineer 6.00 As SSD
DVD1 HardWare Test & Optimize AIDA64 Engineer 6.00 As SSD Benchmark 2.0 Battery Mode 3.8.9 32bit Battery Mode 3.8.9 64bit CPU_Z 1.90 CPUID HWMonitor Pro 1.41 GPU-Z 2.24 HWiNFO32 6.10 Intel Processor Identification Utility 6.1 IsMyLcdOK 3.26 32bit Portable IsMyLcdOK 3.26 64bit Portable Opti Drive Control 1.70 PassMark BurnInTest 9.0 PassMark KeyboardTest 3.2.1002 PassMark MonitorTest 4.0.1000 PassMark PerformanceTest 9.0 PC Info 3.6.8 32bit PC Info 3.6.8 64bit RAM Saver Professional 19.3 SiSoftware Sandra Business 2016.03.22 Task Manager Deluxe 2.82 32bit Portable Task Manager Deluxe 2.82 64bit Portable HDD & Partition Tools Abelssoft CheckDrive 2019 1.31 Abelssoft SSD Fresh 2019 8.0 Acronis Disk Director 12.5 Auslogics Disk Defrag Pro 9.1 CrystalDiskInfo 8.3 CrystalDiskMark 6.0 Defraggler 2.21 Disk Pulse Ultimate 12.0 32bit Disk Pulse Ultimate 12.0 64bit Disk Sorter Ultimate 12.0 32bit Disk Sorter Ultimate 12.0 64bit Diskeeper 16 Pro 19.0.1220 DiskTrix UltimateDefrag 6.0.28 EaseUS Partition Master 13.0 HD Tune Pro 5.70 HDD Low Level Format Tool 4.40 Paragon Hard Disk Manager 17.4 32bit Paragon Hard Disk Manager 17.4 64bit Paragon HFS+ for Windows 11.0.0.175 SSD Tweaker Pro 4.0.1 SSDlife for Ultrabook 2.5.82 SSDlife Pro 2.5.82 VX Search Ultimate 12.1 32bit VX Search Ultimate 12.1 64bit Windows Surface Scanner 2.10 Windows 10 Activator Wallpapers GerdooNameh 40 Magazine DVD2 Engineering Tools Business Plan Pro Premier 11.25 ChemMaths 17.5 ChemProject 6.3 ConvertAll 0.7.2 CrystalDiffract 6.8 Diagram Designer 1.29.2 Edraw Max 9.0 fx-Calc 4.9 -

Announcement
Announcement 43 articles, 2016-08-19 18:01 1 Twitter tackles violent trolls and terrorist sympathisers with huge 235,000 account takedown (1.02/2) Daily suspensions are up over 80 per cent since last year, firm claims,Web ,Twitter 2016-08-19 17:24 2KB www.computing.co.uk 2 Galaxy C9 Is the Next Smartphone in Samsung's C Series The new Samsung smartphone is codenamed Amy 2016-08-19 11:14 (1.02/2) 1KB news.softpedia.com 3 Best Windows apps this week One-hundred and ninety-four in a series. Welcome to this week's overview of the best apps, games and extensions released for (1.02/2) Windows 8.x and Windows 10 in the past seven days. One-hundred and ninety-four in a series. Welcome to this week’s... 2016-08-19 10:48 4KB feeds.betanews.com 4 Microsoft PowerShell Goes Open Source, Arrives On Linux, Mac Microsoft has released its PowerShell command-line shell and (1.02/2) scripting language as open source, demonstrating continued support for alternate operating systems. 2016-08-19 10:06 4KB www.informationweek.com 5 Microsoft isn't alone when it comes to Windows 10's sneaky data mining Plantronics and McAfee could also use a good dose of transparency (1.02/2) 2016-08-19 09:07 4KB www.techradar.com 6 The Galaxy Note 7 Undergoes Teardown, Is Slightly Easier to Repair than the S7 iFixit performed a teardown of the Galaxy Note 7 2016-08-19 09:12 2KB (1.00/2) news.softpedia.com 7 The best free PDF editor 2016 Edit images and text, split and merge documents, add annotations and convert formats 2016-08-19 09:30 7KB www.techradar.com (0.03/2) 8 PyCharm Edu Adds Adaptive Courses Programming book reviews, programming tutorials,programming news, C#, Ruby, Python,C, C++, PHP, Visual Basic, Computer book reviews, computer history, programming history, joomla, theory, spreadsheets and more.