Mcafee Foundstone Fsl Update 2019-Jan-17
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Enchant 1300
ENCHANT 1300 Quick Start Guide For more information, please visit harmankardon.com / 1. WHAT’S IN THE BOX Soundbar Remote Control VOL Power Cables* HDMI Cable AUX cable Optical Cable (4ft, 1200mm) (4ft, 1200mm) (4ft, 1200mm) (4ft, 1200mm) Wall-Mount Brackets Product Information & Wall-mounted guide * Power cable quantities vary by region / 2. PLACE YOUR SOUNDBAR 2a. Place the soundbar on the table TV 2B. Wall mount the soundbar Use tape to stick the wall-mounted paper guide on the wall, push a pen tip through the center to mark the wall-mounted bracket location and remove the paper. 1 TV WALLMOUNTED PAPER GUIDE Using the appropriate anchors, screw the wall mount brackets on the pen mark; Fix the screws at the back of soundbar; then hook the soundbar on the wall. 3 2 x3 4 TV / 3. CONNECT YOUR SOUNDBAR 3a. Connect to your TV Option 1 (Best): HDMI TV HDMI OUT HDMI (ARC) (TV ARC) Option 2: OPTICAL TV OPTICAL OUT OPTICAL IN 3b. Connect to other devices HDMI 1 HDMI 2 HDMI 3 HDMI OUT / 4. POWER YOUR SYSTEM 1 2 3 After the power cord is plugged in, the soundbar will take about 30 seconds to start up and then will enter standby mode, ready to use. / 5. CONNECT TO WI-FI 1 2 3 HK ENCHANT 1300 Once the soundbar connects to the internet for the first time, it may detect a software update to improve performance. This update may take a few minutes to complete. / 6. CONTROL YOUR SOUNDBAR 6a. Top Panel Volume Volume Power Down Up Source Display 6b. -

Desktop Migration and Administration Guide
Red Hat Enterprise Linux 7 Desktop Migration and Administration Guide GNOME 3 desktop migration planning, deployment, configuration, and administration in RHEL 7 Last Updated: 2021-05-05 Red Hat Enterprise Linux 7 Desktop Migration and Administration Guide GNOME 3 desktop migration planning, deployment, configuration, and administration in RHEL 7 Marie Doleželová Red Hat Customer Content Services [email protected] Petr Kovář Red Hat Customer Content Services [email protected] Jana Heves Red Hat Customer Content Services Legal Notice Copyright © 2018 Red Hat, Inc. This document is licensed by Red Hat under the Creative Commons Attribution-ShareAlike 3.0 Unported License. If you distribute this document, or a modified version of it, you must provide attribution to Red Hat, Inc. and provide a link to the original. If the document is modified, all Red Hat trademarks must be removed. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, the Red Hat logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other countries. -

Rawkit Documentation Release 0.6.0
rawkit Documentation Release 0.6.0 Cameron Paul, Sam Whited Sep 20, 2018 Contents 1 Requirements 3 2 Installing rawkit 5 3 Getting Help 7 4 Tutorials 9 5 Architecture and Design 13 6 API Reference 15 7 Indices and tables 73 Python Module Index 75 i ii rawkit Documentation, Release 0.6.0 Note: rawkit is still alpha quality software. Until it hits 1.0, it may undergo substantial changes, including breaking API changes. rawkit is a ctypes-based set of LibRaw bindings for Python inspired by Wand. It is licensed under the MIT License. from rawkit.raw import Raw from rawkit.options import WhiteBalance with Raw(filename='some/raw/image.CR2') as raw: raw.options.white_balance= WhiteBalance(camera=False, auto=True) raw.save(filename='some/destination/image.ppm') Contents 1 rawkit Documentation, Release 0.6.0 2 Contents CHAPTER 1 Requirements • Python – CPython 2.7+ – CPython 3.4+ – PyPy 2.5+ – PyPy3 2.4+ • LibRaw – LibRaw 0.16.x (API version 10) – LibRaw 0.17.x (API version 11) 3 rawkit Documentation, Release 0.6.0 4 Chapter 1. Requirements CHAPTER 2 Installing rawkit First, you’ll need to install LibRaw: • libraw on Arch • LibRaw on Fedora 21+ • libraw10 on Ubuntu Utopic+ • libraw-bin on Debian Jessie+ Now you can fetch rawkit from PyPi: $ pip install rawkit 5 rawkit Documentation, Release 0.6.0 6 Chapter 2. Installing rawkit CHAPTER 3 Getting Help Need help? Join the #photoshell channel on Freenode. As always, don’t ask to ask (just ask) and if no one is around: be patient, if you part before we can answer there’s not much we can do. -

1. D-Bus a D-Bus FAQ Szerint D-Bus Egy Interprocessz-Kommunikációs Protokoll, És Annak Referenciamegvalósítása
Az Udev / D-Bus rendszer - a modern asztali Linuxok alapja A D-Bus rendszer minden modern Linux disztribúcióban jelen van, sőt mára már a Linux, és más UNIX jellegű, sőt nem UNIX rendszerek (különösen a desktopon futó változatok) egyik legalapvetőbb technológiája, és az ismerete a rendszergazdák számára lehetővé tesz néhány rendkívül hasznos trükköt, az alkalmazásfejlesztőknek pedig egyszerűen KÖTELEZŐ ismerniük. Miért ilyen fontos a D-Bus? Mit csinál? D-Bus alapú technológiát teszik lehetővé többek között azt, hogy közönséges felhasználóként a kedvenc asztali környezetünkbe bejelentkezve olyan feladatokat hajtsunk végre, amiket a kernel csak a root felasználónak engedne meg. Felmountolunk egy USB meghajtót? NetworkManagerrel konfiguráljuk a WiFi-t, a 3G internetet vagy bármilyen más hálózati csatolót, és kapcsolódunk egy hálózathoz? Figyelmeztetést kapunk a rendszertől, hogy új szoftverfrissítések érkeztek, majd telepítjük ezeket? Hibernáljuk, felfüggesztjük a gépet? A legtöbb esetben ma már D-Bus alapú technológiát használunk ilyen esetben. A D-Bus lehetővé teszi, hogy egymástól függetlenül, jellemzően más UID alatt indított szoftverösszetevők szabványos és biztonságos módon igénybe vegyék egymás szolgáltatásait. Ha valaha lesz a Linuxhoz professzionális desktop tűzfal vagy vírusirtó megoldás, a dolgok jelenlegi állasa szerint annak is D- Bus technológiát kell használnia. A D-Bus technológia legfontosabb ihletője a KDE DCOP rendszere volt, és mára a D-Bus leváltotta a DCOP-ot, csakúgy, mint a Gnome Bonobo technológiáját. 1. D-Bus A D-Bus FAQ szerint D-Bus egy interprocessz-kommunikációs protokoll, és annak referenciamegvalósítása. Ezen referenciamegvalósítás egyik összetevője, a libdbus könyvtár a D- Bus szabványnak megfelelő kommunikáció megvalósítását segíti. Egy másik összetevő, a dbus- daemon a D-Bus üzenetek routolásáért, szórásáért felelős. -

Security: Patches, BIOS and EC Write Protection, Reproducible Builds (Diffoscope) and Coreboot
Published on Tux Machines (http://www.tuxmachines.org) Home > content > Security: Patches, BIOS and EC Write Protection, Reproducible Builds (DiffoScope) and Coreboot Security: Patches, BIOS and EC Write Protection, Reproducible Builds (DiffoScope) and Coreboot By Roy Schestowitz Created 25/07/2020 - 1:48am Submitted by Roy Schestowitz on Saturday 25th of July 2020 01:48:23 AM Filed under Security [1] Security updates for Friday [2] Security updates have been issued by Debian (qemu), Fedora (java-11-openjdk, mod_authnz_pam, podofo, and python27), openSUSE (cni-plugins, tomcat, and xmlgraphics- batik), Oracle (dbus and thunderbird), SUSE (freerdp, kernel, libraw, perl-YAML-LibYAML, and samba), and Ubuntu (libvncserver and openjdk-lts). Librem 14 Features BIOS and EC Write Protection [3] We have been focused on BIOS security at Purism since the beginning, starting with our initiative to replace the proprietary BIOS on our first generation laptops with the open source coreboot project. This was a great first step as it not only meant customers could avoid proprietary code in line with Purism?s social purpose, it also meant the BIOS on Purism laptops could be audited for security bugs and possible backdoors to help avoid problems like the privilege escalation bug in Lenovo?s AMI firmware. Our next goal in BIOS security was to eliminate, replace or otherwise bypass the proprietary Intel Management Engine (ME) in our firmware. We have made massive progress on this front and our Librem laptops, Librem Mini, and Librem Server all ship with an ME that?s been disabled and neutralized. After that we shifted focus to protecting the BIOS against tampering. -

CIS Ubuntu Linux 18.04 LTS Benchmark
CIS Ubuntu Linux 18.04 LTS Benchmark v1.0.0 - 08-13-2018 Terms of Use Please see the below link for our current terms of use: https://www.cisecurity.org/cis-securesuite/cis-securesuite-membership-terms-of-use/ 1 | P a g e Table of Contents Terms of Use ........................................................................................................................................................... 1 Overview ............................................................................................................................................................... 12 Intended Audience ........................................................................................................................................ 12 Consensus Guidance ..................................................................................................................................... 13 Typographical Conventions ...................................................................................................................... 14 Scoring Information ..................................................................................................................................... 14 Profile Definitions ......................................................................................................................................... 15 Acknowledgements ...................................................................................................................................... 17 Recommendations ............................................................................................................................................ -

A Brief History of GNOME
A Brief History of GNOME Jonathan Blandford <[email protected]> July 29, 2017 MANCHESTER, UK 2 A Brief History of GNOME 2 Setting the Stage 1984 - 1997 A Brief History of GNOME 3 Setting the stage ● 1984 — X Windows created at MIT ● ● 1985 — GNU Manifesto Early graphics system for ● 1991 — GNU General Public License v2.0 Unix systems ● 1991 — Initial Linux release ● Created by MIT ● 1991 — Era of big projects ● Focused on mechanism, ● 1993 — Distributions appear not policy ● 1995 — Windows 95 released ● Holy Moly! X11 is almost ● 1995 — The GIMP released 35 years old ● 1996 — KDE Announced A Brief History of GNOME 4 twm circa 1995 ● Network Transparency ● Window Managers ● Netscape Navigator ● Toolkits (aw, motif) ● Simple apps ● Virtual Desktops / Workspaces A Brief History of GNOME 5 Setting the stage ● 1984 — X Windows created at MIT ● 1985 — GNU Manifesto ● Founded by Richard Stallman ● ● 1991 — GNU General Public License v2.0 Our fundamental Freedoms: ○ Freedom to run ● 1991 — Initial Linux release ○ Freedom to study ● 1991 — Era of big projects ○ Freedom to redistribute ○ Freedom to modify and ● 1993 — Distributions appear improve ● 1995 — Windows 95 released ● Also, a set of compilers, ● 1995 — The GIMP released userspace tools, editors, etc. ● 1996 — KDE Announced This was an overtly political movement and act A Brief History of GNOME 6 Setting the stage ● 1984 — X Windows created at MIT “The licenses for most software are ● 1985 — GNU Manifesto designed to take away your freedom to ● 1991 — GNU General Public License share and change it. By contrast, the v2.0 GNU General Public License is intended to guarantee your freedom to share and ● 1991 — Initial Linux release change free software--to make sure the ● 1991 — Era of big projects software is free for all its users. -

PIC Licensing Information User Manual
Oracle® Communications Performance Intelligence Center Licensing Information User Manual Release 10.1 E56971 Revision 3 April 2015 Oracle Communications Performance Intelligence Center Licensing Information User Manual, Release 10.1 Copyright © 2003, 2015 Oracle and/or its affiliates. All rights reserved. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, the following notices are applicable: U.S. GOVERNMENT END USERS: Oracle programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, delivered to U.S. Government end users are "commercial computer software" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, use, duplication, disclosure, modification, and adaptation of the programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, shall be subject to license terms and license restrictions applicable to the programs. -

The Showfoto Handbook the Showfoto Handbook
The Showfoto Handbook The Showfoto Handbook 2 Contents 1 Introduction 13 1.1 Background . 13 1.1.1 About Showfoto . 13 1.1.2 Reporting Bugs . 13 1.1.3 Support . 13 1.1.4 Getting Involved . 13 1.2 Supported Image Formats . 14 1.2.1 Introduction . 14 1.2.2 Still Image Compression . 14 1.2.3 JPEG . 14 1.2.4 TIFF . 15 1.2.5 PNG . 15 1.2.6 PGF . 15 1.2.7 RAW . 15 2 The Showfoto sidebar 17 2.1 The Showfoto Right Sidebar . 17 2.1.1 Introduction to the Right Sidebar . 17 2.1.2 Properties . 17 2.1.3 Metadata . 18 2.1.3.1 EXIF Tags . 19 2.1.3.1.1 What is EXIF . 19 2.1.3.1.2 How to Use EXIF Viewer . 19 2.1.3.2 Makernote Tags . 20 2.1.3.2.1 What is Makernote . 20 2.1.3.2.2 How to Use Makernote Viewer . 20 2.1.3.3 IPTC Tags . 20 2.1.3.3.1 What is IPTC . 20 2.1.3.3.2 How to Use IPTC Viewer . 21 2.1.3.4 XMP Tags . 21 2.1.3.4.1 What is XMP . 21 2.1.3.4.2 How to Use XMP Viewer . 21 2.1.4 Colors . 21 The Showfoto Handbook 2.1.4.1 Histogram Viewer . 21 2.1.4.2 How To Use an Histogram . 23 2.1.5 Maps . 25 2.1.6 Captions . 26 2.1.6.1 Introduction . -

SUSE Linux Enterprise Server 15 SP2 Security and Hardening Guide Security and Hardening Guide SUSE Linux Enterprise Server 15 SP2
SUSE Linux Enterprise Server 15 SP2 Security and Hardening Guide Security and Hardening Guide SUSE Linux Enterprise Server 15 SP2 Introduces basic concepts of system security, covering both local and network security aspects. Shows how to use the product inherent security software like AppArmor, SELinux, or the auditing system that reliably collects information about any security-relevant events. Supports the administrator with security-related choices and decisions in installing and setting up a secure SUSE Linux Enterprise Server and additional processes to further secure and harden that installation. Publication Date: September 24, 2021 SUSE LLC 1800 South Novell Place Provo, UT 84606 USA https://documentation.suse.com Copyright © 2006– 2021 SUSE LLC and contributors. All rights reserved. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or (at your option) version 1.3; with the Invariant Section being this copyright notice and license. A copy of the license version 1.2 is included in the section entitled “GNU Free Documentation License”. For SUSE trademarks, see https://www.suse.com/company/legal/ . All other third-party trademarks are the property of their respective owners. Trademark symbols (®, ™ etc.) denote trademarks of SUSE and its aliates. Asterisks (*) denote third-party trademarks. All information found in this book has been compiled with utmost attention to detail. However, this does not guarantee complete accuracy. Neither SUSE LLC, its -

Fedora 25 Networking Guide
Fedora 25 Networking Guide Configuration and Administration of Networking for Fedora 25 Stephen Wadeley Networking Guide Draft Fedora 25 Networking Guide Configuration and Administration of Networking for Fedora 25 Edition 1 Author Stephen Wadeley [email protected] Copyright © 2016 Red Hat, Inc. and others. The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at http://creativecommons.org/licenses/by-sa/3.0/. The original authors of this document, and Red Hat, designate the Fedora Project as the "Attribution Party" for purposes of CC-BY-SA. In accordance with CC-BY-SA, if you distribute this document or an adaptation of it, you must provide the URL for the original version. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, JBoss, MetaMatrix, Fedora, the Infinity Logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. For guidelines on the permitted uses of the Fedora trademarks, refer to https://fedoraproject.org/wiki/ Legal:Trademark_guidelines. Linux® is the registered trademark of Linus Torvalds in the United States and other countries. Java® is a registered trademark of Oracle and/or its affiliates. XFS® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. -
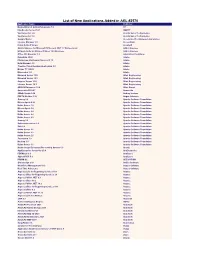
List of New Applications Added in ARL #2570
List of New Applications Added in ARL #2570 Application Name Publisher Nomad Branch Admin Extensions 7.0 1E FineReader Server 14.1 ABBYY VoxConverter 2.0 Acarda Sales Technologies VoxConverter 3.0 Acarda Sales Technologies Sample Master Accelerated Technology Laboratories License Manager 3.5 AccessData Prizm ActiveX Viewer AccuSoft Add-in Express for Microsoft Office and .NET 7.7 Professional Add-in Express Ultimate Suite for Microsoft Excel 18.5 Business Add-in Express Office 365 Reporter 3.5 AdminDroid Solutions RoboHelp 2020 Adobe Photoshop Lightroom Classic CC 10 Adobe Help Manager 4.0 Adobe Creative Cloud Desktop Application 5.3 Adobe Bridge CC (2021) Adobe Dimension 3.4 Adobe Monarch Server 15.0 Altair Engineering Monarch Server 15.3 Altair Engineering Angoss Server 10.4 Altair Engineering License Server 14.1 Altair Engineering ARGUS Enterprise 12.0 Altus Group Anaconda 2020.07 Anaconda SMath Studio 0.98 Andrey Ivashov PDFTK Builder 3.10 Angus Johnson Groovy 2.6 Apache Software Foundation Mesos Agent 0.28 Apache Software Foundation Kafka Server 1.0 Apache Software Foundation Mesos Agent 1.8 Apache Software Foundation Kafka Server 2.4 Apache Software Foundation Kafka Server 2.6 Apache Software Foundation Kafka Server 2.3 Apache Software Foundation Groovy 2.5 Apache Software Foundation Subversion server 1.9 Apache Software Foundation Solr 2.0 Apache Software Foundation Kafka Server 2.1 Apache Software Foundation Kafka Server 2.2 Apache Software Foundation Kafka Server 2.5 Apache Software Foundation Cassandra 3.9 Apache Software Foundation