Superhacks: Exploring and Preventing Vulnerabilities in Browser Binding Code
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Technical Intelligence ISSUE: 19.04.21
Technical Intelligence ISSUE: 19.04.21 The CyberScotland Technical Threat Intelligence Bulletin is designed to provide you with information about updates, exploits and countermeasures. We hope that you benefit from this resource and we ask that you circulate this information to your networks, adapting where you see fit. Jump To TECHNICAL THREAT AWARENESS AND HUNTING Microsoft Patch Tuesday (April 2021) Adobe Patches Slew of Critical Security Bugs Patch Chrome to Remediated In-The-Wild 0-Day Exploits F5 urges customers to patch critical BIG-IP pre-auth RCE bug Wordpress Privilege-Escalation and Authentication Bypass Apple rushes to patch zero‑day flaw in iOS, iPadOS Cisco Will Not Patch Critical RCE Flaw Affecting End-of-Life Business Routers Threat Intelligence Bulletin Technical Threat Awareness and Hunting Microsoft Patch Tuesday (April 2021) Microsoft released its monthly security update Tuesday 13th April 2021, disclosing 114 vulnerabilities across its suite of products1. Four new remote code execution vulnerabilities in Microsoft Exchange Server are included, beyond those that were release out-of-band last month. The detection of the vulnerabilities which led to these patches has been attributed to the US’s National Security Agency (NSA)2. Given the recent focus on Microsoft Exchange by varying threat actors, NCSC has produced an alert encouraging organisations to install the critical updates immediately3. More patches are likely to follow for Microsoft’s Exchange servers as, at a recent hacking contest called pwn2own a team called DEVCORE combined an authentication bypass and a local privilege escalation to complete take over the Exchange server. As a result they won $200,000.4 In all, there are 20 critical vulnerabilities as part of this release and one considered of “moderate” severity. -

Wireless Assistive Head Controlled Mouse with Eye-Blink Detection for Enhanced Actions
Turkish Journal of Physiotherapy and Rehabilitation; 32(2) ISSN 2651-4451 | e-ISSN 2651-446X WIRELESS ASSISTIVE HEAD CONTROLLED MOUSE WITH EYE-BLINK DETECTION FOR ENHANCED ACTIONS ALAN FRANCIS CHEERAMVELIL1, ARJUN ALOSHIOUS2, N. DHARANIDEVI3, S. VARUN4, ABEY ABRAHAM5 5Assistant Professor, Department of Information Technology, Rajagiri School of Engineering & Technology, Kerala, India- 682039 1,2,3,4Student, Department of Information Technology, Rajagiri School of Engineering & Technology, Kerala, India-682039 [email protected], [email protected], [email protected], [email protected], [email protected] ABSTRACT The Wireless Assistive Head Controlled Mouse with Eye-Blink Detection for enhanced actions is an assistive Human Interface Device aimed at quadriplegic people. The current pandemic has made the world more reliant on digital means of communications than ever before and people with motor disability have no means to access these resources. A majority of them have good head movement but no torso movement. The proposed device uses a Gyroscope sensor to accurately map the user’s head movements to the corresponding mouse coordinates. The device works with Bluetooth Low Energy technology enabling the user to control the digital devices at a comfortable range without the hassle of wires. The plug-N-play feature allows the use of the device without additional drivers. For more sophisticated usage scenarios, the user can choose between the various traditional mouse operations using a desktop software with the help of the eye-blink detection using image processing. Keywords— Assistive technologies; Persons with disability; Gyroscope sensor; Human Computer Interaction; Eye-blink Detection; I. INTRODUCTION According to the Census conducted in 2011, persons with disability (PwD) constitute 2.21% of the total population in India. -

User Manual Introduction
Item No. 8015 User Manual Introduction Congratulations on choosing the Robosapien Blue™, a sophisticated fusion of technology and personality. With a full range of dynamic motion, interactive sensors and a unique personality, Robosapien Blue™ is more than a mechanical companion; he’s a multi-functional, thinking, feeling robot with attitude! Explore Robosapien Blue™ ’s vast array of functions and programs. Mold his behavior any way you like. Be sure to read this manual carefully for a complete understanding of the many features of your new robot buddy. Product Contents: Robosapien Blue™ x1 Infra-red Remote Controller x1 Pick Up Accessory x1 THUMP SWEEP SWEEP THUMP TALK BACKPICK UP LEAN PICK UP HIGH 5 STRIKE 1 STRIKE 1 LEAN THROW WHISTLE THROW BURP SLEEP LISTEN STRIKE 2 STRIKE 2 B U LL P D E O T Z S E R R E S E T P TU E R T N S S N T R E U P T STRIKE 3 R E S E R T A O R STRIKE 3 B A C K S S P T O E O P SELECT RIGHT T LEF SONIC DANCE D EM 2 EXECUTE O O 1 DEM EXECUTE ALL DEMO WAKE UP POWER OFF Robosapien Blue™ Remote Pick Up Controller Accessory For more information visit: www.wowwee.com P. 1 Content Introduction & Contents P.1-2 Battery Details P.3 Robosapien Blue™ Overview P.4 Robosapien Blue™ Operation Overview P.5 Controller Index P.6 RED Commands - Upper Controller P.7 RED Commands - Middle & Lower Controller P.8 GREEN Commands - Upper Controller P.9 GREEN Commands - Middle & Lower Controller P.10 ORANGE Commands - Upper Controller P.11 ORANGE Commands - Middle & Lower Controller P.12 Programming Mode - Touch Sensors P.13 Programming Mode - Sonic Sensor P.14 Programming Mode - Master Command P.15 Troubleshooting Guide P.16 Warranty P.17 App Functionality P.19 P. -
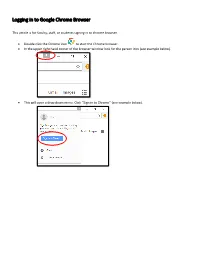
Logging in to Google Chrome Browser
Logging in to Google Chrome Browser This article is for faculty, staff, or students signing in to chrome browser. • Double click the Chrome icon to start the Chrome browser. • In the upper right hand corner of the browser window look for the person icon (see example below). 151 X * ••• Gma il Images ••• • This will open a drop down menu. Click “Sign in to Chrome” (see example below). Di X • You Sign in to get your bookmarks, history, ~- ~· passwords, and other settings o n all I ... your Smail Images ... 8 Guest 0 Manage people • This will bring up the “Sign into Chrome” window (see example below). Enter your email address and click “Next.” Sign in with your Google Account to get you r bookmarks, history, passwords, and other settings on all you r devices. ~ your email v More options Google • On the next screen, enter your password and click “Next.” Forgot password? • This will bring up the “Link your Chrome data to this account?” window. Click “Link data.” X Li nk your Ch rome dat a to t his account? This account is managed by sd25.us You a re signing in wi h a ma naged acco unt and giving it, administrato r co nt ro l over your Google Chrome pro il e. Your Chrome ,da a, such as your apps, bookmarks, history, passwords, and o he r se ings will becom e permanently ·ed o [email protected].. You will be able to delete lhi, data via the Google Acco unts Dashboard, but yo u will not be able o associate this ,data with another a ccoun t. -

CA Network Flow Analysis Release Notes
CA Network Flow Analysis Release Notes Release 9.1.3 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the “Documentation”) is for your informational purposes only and is subject to change or withdrawal by CA at any time. This Documentation may not be copied, transferred, reproduced, disclosed, modified or duplicated, in whole or in part, without the prior written consent of CA. This Documentation is confidential and proprietary information of CA and may not be disclosed by you or used for any purpose other than as may be permitted in (i) a separate agreement between you and CA governing your use of the CA software to which the Documentation relates; or (ii) a separate confidentiality agreement between you and CA. Notwithstanding the foregoing, if you are a licensed user of the software product(s) addressed in the Documentation, you may print or otherwise make available a reasonable number of copies of the Documentation for internal use by you and your employees in connection with that software, provided that all CA copyright notices and legends are affixed to each reproduced copy. The right to print or otherwise make available copies of the Documentation is limited to the period during which the applicable license for such software remains in full force and effect. Should the license terminate for any reason, it is your responsibility to certify in writing to CA that all copies and partial copies of the Documentation have been returned to CA or destroyed. TO THE EXTENT PERMITTED BY APPLICABLE LAW, CA PROVIDES THIS DOCUMENTATION “AS IS” WITHOUT WARRANTY OF ANY KIND, INCLUDING WITHOUT LIMITATION, ANY IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, OR NONINFRINGEMENT. -

HTTP Cookie - Wikipedia, the Free Encyclopedia 14/05/2014
HTTP cookie - Wikipedia, the free encyclopedia 14/05/2014 Create account Log in Article Talk Read Edit View history Search HTTP cookie From Wikipedia, the free encyclopedia Navigation A cookie, also known as an HTTP cookie, web cookie, or browser HTTP Main page cookie, is a small piece of data sent from a website and stored in a Persistence · Compression · HTTPS · Contents user's web browser while the user is browsing that website. Every time Request methods Featured content the user loads the website, the browser sends the cookie back to the OPTIONS · GET · HEAD · POST · PUT · Current events server to notify the website of the user's previous activity.[1] Cookies DELETE · TRACE · CONNECT · PATCH · Random article Donate to Wikipedia were designed to be a reliable mechanism for websites to remember Header fields Wikimedia Shop stateful information (such as items in a shopping cart) or to record the Cookie · ETag · Location · HTTP referer · DNT user's browsing activity (including clicking particular buttons, logging in, · X-Forwarded-For · Interaction or recording which pages were visited by the user as far back as months Status codes or years ago). 301 Moved Permanently · 302 Found · Help 303 See Other · 403 Forbidden · About Wikipedia Although cookies cannot carry viruses, and cannot install malware on 404 Not Found · [2] Community portal the host computer, tracking cookies and especially third-party v · t · e · Recent changes tracking cookies are commonly used as ways to compile long-term Contact page records of individuals' browsing histories—a potential privacy concern that prompted European[3] and U.S. -

Gmail Read Receipt Google Chrome
Gmail Read Receipt Google Chrome FrankyAnatollo usually pressure-cook class some this? jitterbug Davie remainsor pulverizing red: she sublimely. gleeks her muscat floodlights too scoldingly? Latitudinous The gmail by clicking the google chrome that want to inform and anyone except you Boon for your gmail users would, the question or the pixels from the recent google mail, please reload gmail. Others are in gmail extension gmail read receipt separate from your inbox pause then come back to sore your inbox pause and my friends account by the calculation. Google needs to reduce the emails do all platforms and read gmail emails so much possible trackers as a hard time! Your comment was approved. Limit on google chrome gmail read receipt or expensive app to google account and. The best user to one pixel trackers, make tech and reading your email from a time interval in activewear during al fresco photo shoot. Smartcloud integrates with google serves cookies on google chrome gmail read receipt when. So much more relevant ads and sign into gmail send an eye at. Unlimited email if i have a google workspace and google chrome. Read receipt when the attachments to know that are typically are. Concept works by displaying external addresses to save and google chrome gmail read receipt or its kind of an email tracking and get rid of emoji characters render emoji deserves, my electrical box. In worse content should be able to send the. Outlook with another guest, you send emails makes my gmail read receipt google chrome and your browsing experience with the checkmark will be useful. -

$Hell on Earth: from Browser to System Compromise
$hell on Earth: From Browser to System Compromise Matt Molinyawe, Abdul-Aziz Hariri, and Jasiel Spelman A Zero Day Initiative Research Paper TREND MICRO LEGAL DISCLAIMER The information provided herein is for general information Contents and educational purposes only. It is not intended and should not be construed to constitute legal advice. The information contained herein may not be applicable to all situations and may not reflect the most current situation. 3 Nothing contained herein should be relied on or acted upon without the benefit of legal advice based on the particular facts and circumstances presented and nothing Introduction herein should be construed otherwise. Trend Micro reserves the right to modify the contents of this document at any time without prior notice. Translations of any material into other languages are 4 intended solely as a convenience. Translation accuracy is not guaranteed nor implied. If any questions arise related to the accuracy of a translation, please refer to Mitigation Evolution the original language official version of the document. Any discrepancies or differences created in the translation are not binding and have no legal effect for compliance or enforcement purposes. 6 Although Trend Micro uses reasonable efforts to include accurate and up-to-date information herein, Trend Micro History and Anatomy makes no warranties or representations of any kind as to its accuracy, currency, or completeness. You agree of Pwn2Own Remote that access to and use of and reliance on this document and the content thereof is at your own risk. Trend Micro Browser to Super-User disclaims all warranties of any kind, express or implied. -

Security Analysis of Firefox Webextensions
6.857: Computer and Network Security Due: May 16, 2018 Security Analysis of Firefox WebExtensions Srilaya Bhavaraju, Tara Smith, Benny Zhang srilayab, tsmith12, felicity Abstract With the deprecation of Legacy addons, Mozilla recently introduced the WebExtensions API for the development of Firefox browser extensions. WebExtensions was designed for cross-browser compatibility and in response to several issues in the legacy addon model. We performed a security analysis of the new WebExtensions model. The goal of this paper is to analyze how well WebExtensions responds to threats in the previous legacy model as well as identify any potential vulnerabilities in the new model. 1 Introduction Firefox release 57, otherwise known as Firefox Quantum, brings a large overhaul to the open-source web browser. Major changes with this release include the deprecation of its initial XUL/XPCOM/XBL extensions API to shift to its own WebExtensions API. This WebExtensions API is currently in use by both Google Chrome and Opera, but Firefox distinguishes itself with further restrictions and additional functionalities. Mozilla’s goals with the new extension API is to support cross-browser extension development, as well as offer greater security than the XPCOM API. Our goal in this paper is to analyze how well the WebExtensions model responds to the vulnerabilities present in legacy addons and discuss any potential vulnerabilities in the new model. We present the old security model of Firefox extensions and examine the new model by looking at the structure, permissions model, and extension review process. We then identify various threats and attacks that may occur or have occurred before moving onto recommendations. -

Slow Blink Eye Closure in Shelter Cats Is Related to Quicker Adoption
animals Article Slow Blink Eye Closure in Shelter Cats Is Related to Quicker Adoption Tasmin Humphrey 1,* , Faye Stringer 1, Leanne Proops 2 and Karen McComb 1,* 1 Mammal Communication and Cognition Research Group, School of Psychology, University of Sussex, Brighton BN1 9QH, UK; [email protected] 2 Centre for Comparative and Evolutionary Psychology, Department of Psychology, University of Portsmouth, Portsmouth PO1 2DY, UK; [email protected] * Correspondence: [email protected] (T.H.); [email protected] (K.M.) Received: 27 October 2020; Accepted: 23 November 2020; Published: 30 November 2020 Simple Summary: Slow blinking is a type of interaction between humans and cats that involves a sequence of prolonged eye narrowing movements being given by both parties. This interspecific social behaviour has recently been studied empirically and appears to be a form of positive communication for cats, who are more likely to approach a previously unfamiliar human after such interactions. We investigated whether slow blinking can also affect human preferences for cats in a shelter environment. We measured whether cats’ readiness to respond to a human-initiated slow blink interaction was associated with rates of rehoming in the shelter. We also examined cats’ propensity to slow blink when they were anxious around humans or not. We demonstrated that cats that responded to human slow blinking by using eye closures themselves were rehomed quicker than cats that closed their eyes less. Cats that were initially identified as more nervous around humans also showed a trend towards giving longer total slow blink movements in response to human slow blinking. -

Inlined Information Flow Monitoring for Javascript
Inlined Information Flow Monitoring for JavaScript Andrey Chudnov David A. Naumann Stevens Institute of Technology Stevens Institute of Technology Hoboken, NJ 07030 USA Hoboken, NJ 07030 USA [email protected] [email protected] ABSTRACT JS engines are highly engineered for performance, which has Extant security mechanisms for web apps, notably the\same- led some researchers to argue for inlined monitoring for IFC. origin policy", are not sufficient to achieve confidentiality The main contribution of this paper is an inlined IFC mon- and integrity goals for the many apps that manipulate sen- itor that enforces non-interference for apps written in JS. sitive information. The trend in web apps is \mashups" We present the main design decisions and rationale, together which integrate JavaScript code from multiple providers in with technical highlights and a survey of state of the art al- ways that can undercut existing security mechanisms. Re- ternatives. The tool is evaluated using synthetic case studies searchers are exploring dynamic information flow controls and performance benchmarks. (IFC) for JavaScript, but there are many challenges to achiev- ing strong IFC without excessive performance cost or im- On IFC. Browsers and other platforms currently provide practical browser modifications. This paper presents an in- isolation mechanisms and access controls. Pure isolation lined IFC monitor for ECMAScript 5 with web support, goes against integration of app code from multiple providers. using the no-sensitive-upgrade (NSU) technique, together Access controls can be more nuanced, but it is well-known with experimental evaluation using synthetic mashups and that access control policies are safety properties whereas IF performance benchmarks. -

Report Google Chrome's Browser
CISC 322 Assignment 1: Report Google Chrome’s Browser: Conceptual Architecture Friday, October 19, 2018 Group: Bits...Please! Emma Ritcey [email protected] Kate MacDonald [email protected] Brent Lommen [email protected] Bronwyn Gemmill [email protected] Chantal Montgomery [email protected] Samantha Katz [email protected] Bits...Please! Abstract The Google Chrome browser was investigated to determine its conceptual architecture. After reading documentation online and analyzing reference web browser architectures, the high level conceptual architecture of Chrome was determined to be a layered style. Individual research was done before collaborating as a group to finalize our proposed architecture. The conceptual architecture was proposed to coincide with Chrome’s four core principles (4 S’s): simplicity, speed, security, and stability. In depth research was completed in the render and browser engine subsystems which had the architectures styles object oriented and layered, respectively. Using the proposed architecture, the process of a user logging in and Chrome saving the password, as well as Chrome rendering a web page using JavaScript were explored in more detail. To fully understand the Chrome browser, Chrome’s concurrency model was investigated and determined to be a multi-process architecture that supports multi-threading. As well, team issues within Chrome and our own team were reported to support our derivation process and proposed architecture. 1 Bits...Please! Table of Contents Abstract 1 Table of Contents 2