Using Cloud Services and Object Storage Bacula Community Version
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

1) Installation 2) Configuration
rclone 1) Installation........................................................................................................................................1 2) Configuration...................................................................................................................................1 2.1) Server setup..............................................................................................................................1 2.2) Client setup...............................................................................................................................2 2.3) Server setup - part 2..................................................................................................................2 2.4) Client verification.....................................................................................................................3 2.5) rclone - part 1............................................................................................................................3 2.6) rclone - part 2............................................................................................................................4 3) Backup configuration.......................................................................................................................5 4) Usage................................................................................................................................................5 1) Installation https://rclone.org/install/ Script installation To install rclone on Linux/macOS/BSD -

Scaling a Game-Sharing Platform Introduction
Level Up and SIMMER.io Down Scaling a Game-sharing Platform Introduction Much like gaming, starting a business means a lot of trial and error. In the beginning, you’re just trying to get your bearings and figure out which enemy to fend off first. After a few hours (or a few years on the market), it’s time to level up. SIMMER.io, a community site that makes sharing Unity WebGL games easy for indie game developers, leveled up in a big way to make their business sustainable for the long haul. When the site was founded in September 2017, the development team focused on getting the platform built and out the door, not on what egress costs would look like down the road. As it grew into a home for 80,000+ developers and 30,000+ games, though, those costs started to encroach on their ability to sustain and grow the business. We spoke with the SIMMER.io development team about their experience setting up a multi-cloud solution—including their use of the Bandwidth Alliance between Cloudflare and Backblaze B2 Cloud Storage to reduce egress to $0—to prepare the site for continued growth. © 2021 Backblaze Inc. All rights reserved. 500 Ben Franklin Ct. San Mateo, CA 94401 USA How to Employ a Multi-cloud Approach for Scaling a Web Application In 2017, sharing games online with static hosting through a service like AWS S3 was possible but certainly not easy. As one SIMMER.io team member put it, “No developer in the world would want to go through that.” The team saw a clear market opportunity. -

Initial Definition of Protocols and Apis
Initial definition of protocols and APIs Project acronym: CS3MESH4EOSC Deliverable D3.1: Initial Definition of Protocols and APIs Contractual delivery date 30-09-2020 Actual delivery date 16-10-2020 Grant Agreement no. 863353 Work Package WP3 Nature of Deliverable R (Report) Dissemination Level PU (Public) Lead Partner CERN Document ID CS3MESH4EOSC-20-006 Hugo Gonzalez Labrador (CERN), Guido Aben (AARNET), David Antos (CESNET), Maciej Brzezniak (PSNC), Daniel Muller (WWU), Jakub Moscicki (CERN), Alessandro Petraro (CUBBIT), Antoon Prins Authors (SURFSARA), Marcin Sieprawski (AILLERON), Ron Trompert (SURFSARA) Disclaimer: The document reflects only the authors’ view and the European Commission is not responsible for any use that may be made of the information it contains. This project has received funding from the European Union’s Horizon 2020 research and innovation programme under grant agreement No 863353 Table of Contents 1 Introduction ............................................................................................................. 3 2 Core APIS .................................................................................................................. 3 2.1 Open Cloud Mesh (OCM) ...................................................................................................... 3 2.1.1 Introduction .......................................................................................................................................... 3 2.1.2 Advancing OCM .................................................................................................................................... -

A Backup-As-A-Service (Baas) Software Solution
Universidade de Brasília Institute of Exact Sciences Department of Computer Science A Backup-as-a-Service (BaaS) Software Solution Heitor M. de Faria Dissertation presented as partial requirement for conclusion on the Professional Master in Applied Computing Advisor Prof. Dra. Priscila Solis Brasília 2018 Universidade de Brasília Institute of Exact Sciences Department of Computer Science A Backup-as-a-Service (BaaS) Software Solution Heitor M. de Faria Dissertation resented as partial requirement for conclusion do Professional Master in Applied Computing Prof. Dra. Priscila Solis (Advisor) CIC/UnB Prof. Dr. Jacir Bordim Dr. Georges Amvame-Nzê Universidade de Brasília Universidade de Brasília Prof. Dr. Marcelo Ladeira Coordinator of the Post-graduation Program in Applied Computing Brasília, July 1st, 2018 Abstract Backup is a replica of any data that can be used to restore its original form. However, the total amount of digital data created worldwide more than doubles every two years and is expected reach 44 trillions of gigabytes in 2020, bringing constant new challenges to backup processes. Enterprise backup is one of the oldest and most performed tasks by in- frastructure and operations professionals. Still, most backup systems have been designed and optimized for outdated environments and use cases. That fact, generates frustration over currently backup challenges and leads to a greater willingness to modernize and to consider new technologies. Traditional backup and archive solutions are no longer able to meet users current needs. The ideal modern currently backup and recovery software product should not only provide features to attend a traditional data center, but also allow the integration and exploration of the growing Cloud, including “backup client as a service” and “backup storage as a service”. -

Improving Read Performance with BP-Dags for Storage-Efficient File Backup
Send Orders for Reprints to [email protected] 90 The Open Electrical & Electronic Engineering Journal, 2013, 7, 90-97 Open Access Improving Read Performance with BP-DAGs for Storage-Efficient File Backup Tianming Yang*, Jing Zhang and Ningbo Hao International College, Huanghuai University, Henan, 463000, China Abstract: The continued growth of data and high-continuity of application have raised a critical and mounting demand on storage-efficient and high-performance data protection. New technologies, especially the D2D (Disk-to-Disk) de- duplication storage are therefore getting wide attention both in academic and industry in the recent years. Existing de- duplication systems mainly rely on duplicate locality inside the backup workload to achieve high throughput but suffer from read performance degrading under conditions of poor duplicate locality. This paper presents the design and perform- ance evaluation of a D2D-based de-duplication file backup system, which employs caching techniques to improve write throughput while encoding files as graphs called BP-DAGs (Bi-pointer-based Directed Acyclic Graphs). BP-DAGs not only satisfy the 'unique' chunk storing policy of de-duplication, but also help improve file read performance in case of poor duplicate locality workloads. Evaluation results show that the system can achieve comparable read performance than non de-duplication backup systems such as Bacula under representative workloads, and the metadata storage overhead for BP-DAGs are reasonably low. Keywords: Data De-duplication, File Backup, Storage-Efficient, Read Performance. 1. INTRODUCTION schemes are emerging to provide more storage-efficient and high performance data protection for enterprises [9-13]. Data explosion [1] has been forcing backups to expand storage capacity, which makes modern enterprises face sig- In de-duplication, files or streams are divided into chunks nificant cost pressures and data management challenges. -

Bacula Community API Using Bacula Community Version
Bacula Community API Using Bacula Community Version This document is intended to provide insight into the considera- tions and processes required to design and implement a GUI Inter- face upon Bacula. Bacula Version 1.3, May 14, 2017 Systems Copyright (C) 2008-2017, Bacula Systems S.A. White All rights reserved. Paper Contents 1 Bacula Programming API2 1.1 General...................................2 1.2 Assumptions................................2 1.3 Implementing a GUI Interface......................3 1.3.1 Simple Console Interface....................4 1.3.2 Native Console Interface....................4 1.4 Bacula Commands............................5 1.4.1 Job Management........................6 1.4.2 Volume Management...................... 10 1.4.3 Restore GUI Using Bvfs API.................. 13 1.5 Object Detailed Information....................... 18 1.6 Resource List............................... 18 1.7 JSON Bacula Resource Description................... 20 1.8 Generate Bacula Configuration..................... 21 1.9 Enable Bacula Statistics Management................. 21 1.10 Autochanger Operations......................... 22 1.11 Bacula Catalog.............................. 22 1.11.1 Catalog Schema......................... 22 1.11.2 Common Queries........................ 28 1.12 .api version 2............................... 31 2 Revision History 32 1 / 33 Copyright © May 2017 Bacula Systems SA www.baculasystems.com/contactus................................... All trademarks are the property of their respective owners 1 Bacula Programming API 1.1 General This White Paper will outline the best practices to design custom GUI and Panel for Bacula Community version 9.0.0 or later. The current Bacula interface can be described as a human interface, doing so, interfacing a program with Bacula requires a bit of work. 1.2 Assumptions The following are the assumptions that we have made: • You have a basic understanding of Bacula, Volumes, recycling, and backup strategies. -

Faq Cloud Sync
FAQ CLOUD SYNC 1 What is Cloud Sync? NetApp® Data Fabric Cloud Sync is a simple replication and synchronization service. This software-as-a-service (SaaS) offering enables you to transfer and synchronize NAS data to and from cloud or on-premises object storage. The SMB/CIFS or NFS server can be the NetApp Cloud Volumes Service, a NetApp system, or a non-NetApp system. Cloud Sync supports these sources and targets: • CIFS • NFS • Amazon S3 • Amazon EFS • Azure Blob • IBM Cloud Object Storage • NetApp StorageGRID® Webscale appliance After your data is synchronized, it remains available for use in the target server and is updated during the next synchronization cycle. © 2019 NetApp, Inc. All Rights Reserved. | 1 2 Why should I use Cloud Sync? Cloud Sync enables you to perform data migration, data transformation, and data synchronization in a fast, efficient, and secure way. Key benefits of using Cloud Sync are: Fast. Cloud Sync transfers data in parallel processes. This speeds throughput to 1TB in four hours (in the default configuration), and up to 10x faster than in-house developed or traditional tools (such as rsync or Robocopy). Efficient. After the initial synchronization, only changes since the last synchronization are transferred. Data that hasn’t changed isn’t re-replicated, which makes updates faster. Cost-effective. Cloud Sync pricing is based on hourly usage, not on capacity. Compatible. Cloud Sync supports any NFS or CIFS servers, Amazon or private S3 buckets, Azure Blob, IBM Cloud Object Storage, Amazon EFS. Secure. Data is not transferred to our service domain; it remains in your protected environment. -

Bacula Regression Testing Bacula Community Version
Bacula Regression Testing Bacula Community Version This document is intended to provide insight into the considera- tions and processes required to implement regression testing with the Community Version of Bacula. Bacula Version 1.3, Saturday 15th December, 2018 Systems Copyright (C) 2008-2018, Bacula Systems White All rights reserved. Paper Contents 1 / ?? Copyright © December 2018 Bacula Systems www.baculasystems.com/contactus................................... All trademarks are the property of their respective owners 1 Bacula Regression Testing If you decided to install Bacula from source, and want to be as sure as possible that your self-compiled binaries behave as expected, the regression testing suite included with the source code is the best way to do so. You do not need to be a developer to run the regression scripts. If you installed Bacula from packages, going through the regression tests can be a reasonable way to ensure that everything behaves as expected and can be an important part of the pre-production testing routine. The tests are shell scripts that drive Bacula through bconsole and then typically compare the input and output with diff, so no particular infrastructure beyond what you needed to build Bacula and what is part of a typical Unix / Linux system is required. To get started, we recommend that you create a directory named bacula, under which you will put the current source code and the current set of regression scripts. The directory could have any name you like, though. Note, all the standard regression scripts run as non-root and can be run on the same machine as a production Bacula system. -

Analysis of Outsourcing Data to the Cloud Using Autonomous Key Generation
Scholars' Mine Masters Theses Student Theses and Dissertations Fall 2017 Analysis of outsourcing data to the cloud using autonomous key generation Mortada Abdulwahed Aman Follow this and additional works at: https://scholarsmine.mst.edu/masters_theses Part of the Computer Engineering Commons Department: Recommended Citation Aman, Mortada Abdulwahed, "Analysis of outsourcing data to the cloud using autonomous key generation" (2017). Masters Theses. 7713. https://scholarsmine.mst.edu/masters_theses/7713 This thesis is brought to you by Scholars' Mine, a service of the Missouri S&T Library and Learning Resources. This work is protected by U. S. Copyright Law. Unauthorized use including reproduction for redistribution requires the permission of the copyright holder. For more information, please contact [email protected]. ANALYSIS OF OUTSOURCING DATA TO THE CLOUD USING AUTONOMOUS KEY GENERATION by MORTADA ABDULWAHED AMAN A THESIS Presented to the Graduate Faculty of the MISSOURI UNIVERSITY OF SCIENCE AND TECHNOLOGY In Partial Fulfillment of the Requirements for the Degree MASTER OF SCIENCE in COMPUTER ENGINEERING 2017 Approved by Dr. Egemen K. Çetinkaya, Advisor Dr. Maciej J. Zawodniok Dr. Sanjay K. Madria Copyright 2017 MORTADA ABDULWAHED AMAN All Rights Reserved iii ABSTRACT Cloud computing, a technology that enables users to store and manage their data at a low cost and high availability, has been emerging for the past few decades because of the many services it provides. One of the many services cloud computing provides to its users is data storage. The majority of the users of this service are still concerned to outsource their data due to the integrity and confidentiality issues, as well as performance and cost issues, that come along with it. -
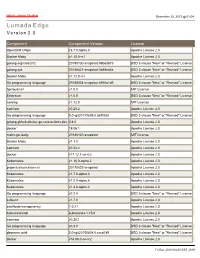
Lumada Edge Version
Hitachi - Inspire The Next December 20, 2019 @ 01:04 Lumada Edge V e r s i o n 3 . 0 Component Component Version License OpenShift Origin v3.7.0-alpha.0 Apache License 2.0 Docker Moby v1.10.0-rc1 Apache License 2.0 golang.org/x/oauth2 20190130-snapshot-99b60b75 BSD 3-clause "New" or "Revised" License golang sys 20180821-snapshot-3b58ed4a BSD 3-clause "New" or "Revised" License Docker Moby v1.12.0-rc1 Apache License 2.0 Go programming language 20180824-snapshot-4910a1d5 BSD 3-clause "New" or "Revised" License hpcloud-tail v1.0.0 MIT License Ethereum v1.5.0 BSD 3-clause "New" or "Revised" License zerolog v1.12.0 MIT License cadvisor v0.28.2 Apache License 2.0 Go programming language 0.0~git20170629.0.5ef0053 BSD 3-clause "New" or "Revised" License golang-github-docker-go-connections-dev 0.4.0 Apache License 2.0 docker 18.06.1 Apache License 2.0 mattn-go-isatty 20180120-snapshot MIT License Docker Moby v1.1.0 Apache License 2.0 cadvisor v0.23.4 Apache License 2.0 docker v17.12.1-ce-rc2 Apache License 2.0 Kubernetes v1.15.0-alpha.2 Apache License 2.0 projectcalico/calico-cni 20170522-snapshot Apache License 2.0 Kubernetes v1.7.0-alpha.3 Apache License 2.0 Kubernetes v1.2.0-alpha.6 Apache License 2.0 Kubernetes v1.4.0-alpha.2 Apache License 2.0 Go programming language v0.2.0 BSD 3-clause "New" or "Revised" License kubevirt v1.7.0 Apache License 2.0 certificate-transparency 1.0.21 Apache License 2.0 kubernetes/api kubernetes-1.15.0 Apache License 2.0 cadvisor v0.28.1 Apache License 2.0 Go programming language v0.3.0 BSD 3-clause "New" or "Revised" -

Bacula Console
Bacula Console << Back to man.ChinaUnix.net Next: The Bacula Console Restore Up: Bacula User's Guide Previous: Monitor Configuration Contents Index Subsections General Console Configuration Running the Console Program Stopping the Console Program Alphabetic List of Console Keywords Alphabetic List of Console Commands Special dot Commands Special At (@) Commands Running the Console Program from a Shell Script Adding Volumes to a Pool Bacula Console General The Bacula Console (sometimes called the User Agent) is a program that allows the user or the System Administrator, to interact with the Bacula Director daemon while the daemon is running. The current Bacula Console comes in two versions: a shell interface (TTY style), and a GNOME GUI interface. Both permit the administrator or authorized users to interact with Bacula. You can determine the status of a particular job, examine the contents of the Catalog as well as perform certain tape manipulations with the Console program. In addition, there is a wx-console built with wxWidgets that allows a graphic restore of files. As of version 1.34.1 it is in an early stage of development, but it already is quite useful. Since the Console program interacts with the Director through the network, your Console and Director programs do not necessarily need to run on the same machine. In fact, a certain minimal knowledge of the Console program is needed in order for Bacula to be able to write on more than one tape, because when Bacula requests a new tape, it waits until the user, via the Console program, indicates that the new tape is mounted. -

What Happens When the Science DMZ Meets the Commodity Internet?
What happens when the Science DMZ meets the Commodity Internet? Presenter: Joe Breen Work done: Brian Haymore, Sam Liston University of Utah Center for High Performance Computing Boil and Bubble, Toil and Trouble, What do you get with a Science DMZ, That's mixed up with unlimited storage Fast and free? Image credit: http://www.zastavki.com/eng/Holidays/Halloween/wallpaper-24660.htm Start with a researcher Offer him candy (unlimited storage) Tell her its free Mix in a "frictionless" Science DMZ environment with 40G and 10G Data Transfer Nodes Image: https://fasterdata.es.net/science-dmz/science-dmz-architecture/ Mix in a well built commodity cloud service that can consume lots of data quickly Throw in an open source parallel tool that knows how to efficiently utilize a cloud provider’s API Google Drive Amazon S3 Openstack Swift / Rackspace cloud files / Memset Memstore Dropbox Google Cloud Storage Amazon Cloud Drive The local filesystem http://rclone.org/ What do you get? 14+Gig spikes, 5-8Gb/s of sustained traffic One 10G commodity pipe fills completely, traffic rolls to next available close peering point, and fills it too R&E routes yanked temporarily by Cloud vendor NOC to allow service to other commodity users and to better understand nature of congestion A call from a cloud provider NOC early in the morning asking to stop. (at least for a bit) Almost 100TB of data moved in 2.5 days Very happy researchers who want more What's an HPC center to do? Start mixing more... Multiple vendors now offering Apps/unlimited storage targeted at EDUcation *individual* users.