Essays on Inventory Management, Capacity Management, and Resource-Sharing Systems Ph.D
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
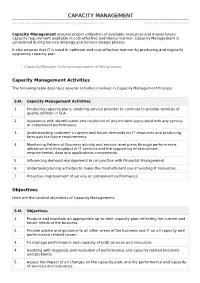
Capacity Management Ensures Proper Utilization of Available Resources and Makes Future Capacity Requirement Available in Cost-Effective and Timely Manner
CCAAPPAACCIITTYY MMAANNAAGGEEMMEENNTT http://www.tutorialspoint.com/itil/capacity_management.htm Copyright © tutorialspoint.com Capacity Management ensures proper utilization of available resources and makes future capacity requirement available in cost-effective and timely manner. Capacity Management is considered during Service Strategy and Service Design phases. It also ensures that IT is sized in optimum and cost-effective manner by producing and regularly upgrading capacity plan. Capacity Manager is the process owner of this process. Capacity Management Activities The following table describes several activities involved in Capacity Management Process: S.N. Capacity Management Activities 1. Producing capacity plans, enabling service provider to continue to provide services of quality defined in SLA. 2. Assistance with identification and resolution of any incident associated with any service or component performance. 3. Understanding customer’s current and future demands for IT resources and producing forecasts for future requirements 4. Monitoring Pattern of Business activity and service level plans through performance, utilization and throughput of IT services and the supporting infrastructure, environmental, data and applications components. 5. Influencing demand management in conjunction with Financial Management 6. Undertaking tuning activities to make the most efficient use of existing IT resources. 7. Proactive improvement of service or component performance Objectives Here are the several objectives of Capacity Management: S.N. Objectives 1. Produce and maintain an appropriate up-to-date capacity plan reflecting the current and future needs of the business. 2. Provide advice and guidance to all other areas of the business and IT on all capacity and performance related issues. 3. To manage performance and capacity of both services and resources. -

Design and Simulation of a Capacity Management Model Using a Digital Twin Approach Based on the Viable System Model: Case Study of an Automotive Plant
applied sciences Article Design and Simulation of a Capacity Management Model Using a Digital Twin Approach Based on the Viable System Model: Case Study of an Automotive Plant Sergio Gallego-García 1,* , Jan Reschke 2,* and Manuel García-García 1,* 1 Department of Construction and Fabrication Engineering, National Distance Education University (UNED), 28040 Madrid, Spain 2 Institute for Industrial Management (FIR), RWTH Aachen University, 52074 Aachen, Germany * Correspondence: [email protected] (S.G.-G.); Jan.Reschke@fir.rwth-aachen.de (J.R.); [email protected] (M.G.-G.); Tel.: +34-682-880-591 (M.G.-G.) Received: 21 October 2019; Accepted: 11 December 2019; Published: 17 December 2019 Abstract: Matching supply capacity and customer demand is challenging for companies. Practitioners often fail due to a lack of information or delays in the decision-making process. Moreover, researchers fail to holistically consider demand patterns and their dynamics over time. Thus, the aim of this study is to propose a holistic approach for manufacturing organizations to change or manage their capacity. The viable system model was applied in this study. The focus of the research is the clustering of manufacturing and assembly companies. The goal of the developed capacity management model is to be able to react to all potential demand scenarios by making decisions regarding labor and correct investments and in the right moment based on the needed information. To ensure this, demand data series are analyzed enabling autonomous decision-making. In conclusion, the proposed approach enables companies to have internal mechanisms to increase their adaptability and reactivity to customer demands. -

Capacity Planning Practices Guide
CDC UNIFIED PROCESS PRACTICES GUIDE CAPACITY PLANNING PRACTICES GUIDE Purpose The purpose of this document is to provide guidance on the practice of Capacity Planning and to describe the practice overview, requirements, best practices, activities, and key terms related to these requirements. In addition, templates relevant to this practice are provided at the end of this guide. Practice Overview Capacity is defined as the maximum amount or number that can be received or contained. For example, the amount of data that a computer hard disk can store is the disk’s capacity. The maximum possible data rate received over a communication channel under ideal conditions is its capacity. Capacity can also refer to non-technical things such as the maximum amount of work that an organization is capable of completing in a given period of time or the maximum number of people that can physically occupy a room. Discrepancies in capacity and demand results in inefficiencies associated with either under-utilized resources or unmet user demand. The goal of capacity planning is to minimize this discrepancy and to provide satisfactory service levels in a cost-efficient manner. The Information Technology Infrastructure Library (ITIL) defines capacity management as supporting the optimum, and cost effective, provisioning of services by helping organizations match their resources to the business demands. Capacity planning doesn’t always mean planning for periods of peak demand. Capacity requirements can vary greatly from times of peak demand to times of limited demand. As a result their may be drastic differences in the resources required to maintain normal operations during periods of peak demand. -

Implementing Capacity Management: a Journey Into the Unknown
SESSION 703 Friday, November 4, 9:00 AM - 10:00 AM Track: The Generalist Implementing Capacity Management: A Journey Into the Unknown Malcolm Gunn Capacity and Availability Lead,Soprasteria [email protected] Session Description What if we told you that there's a process waiting to be unleashed that can take ITSM from reactive to proactive? One that results in less down time and increased cost savings while making sure processing power and storage are ready and waiting when your business needs it? This hidden gem is called business capacity management, and this session will show you how to implement and grow this process to deliver real business benefits. (Experience Level: Fundamental) Speaker Background Malcolm Gunn is well versed in implementing and developing ITIL processes, having worked with internal supply chains and IT outsourcing companies. Working initially in the reactive areas, he realized that if a proactive process could be effectively implemented and aligned to critical business goals, ITSM could become the game changer it was always meant to be. Malcolm is a firm believer that capacity management is one of those key proactive building blocks. Session 703 Capacity Management A Journey Into The Unknown Malcolm Gunn Background •Retail Banking •Commercial Banking •Service Management •IT Outsourcing Why Capacity Management 6 We all Capacity Manage Capacity Management Vs Monitoring and Alerting “We have monitoring and alerting in place across the estate” “I’m not going to paying twice for the same thing” “We’re cloud based, capacity -

Introduction to Materials Management
Introduction to Materials Management SIXTH EDITION J. R. Tony Arnold, P.E., CFPIM, CIRM Fleming College, Emeritus Stephen N. Chapman, Ph.D., CFPIM North Carolina State University Lloyd M. Clive, P.E., CFPIM Fleming College Upper Saddle River, New Jersey Columbus, Ohio Editor in Chief: Vernon R. Anthony Acquisitions Editor: Eric Krassow Editorial Assistant: Nancy Kesterson Production Editor: Louise N. Sette Production Supervision: GGS Book Services Design Coordinator: Diane Ernsberger Cover Designer: Jeff Vanik Production Manager: Deidra M. Schwartz Director of Marketing: David Gesell Marketing Manager: Jimmy Stephens Marketing Assistant: Alicia Dysert This book was set by GGS Book Services. It was printed and bound by R. R. Donnelley & Sons Company. The cover was printed by Phoenix Color Corp. Copyright © 2008, 2004, 2001, 1998, 1996, 1991 by Pearson Education, Inc., Upper Saddle River, New Jersey 07458. Pearson Prentice Hall. All rights reserved. Printed in the United States of America. This publication is protected by Copyright and permission should be obtained from the publisher prior to any prohibited reproduction, storage in a retrieval system, or transmission in any form or by any means, electronic, mechanical, photocopying, recording, or likewise. For information regarding permission(s), write to: Rights and Permissions Department. Pearson Prentice Hall™ is a trademark of Pearson Education, Inc. Pearson® is a registered trademark of Pearson plc. Pearson Hall® is a registered trademark of Pearson Education, Inc. Pearson Education Ltd. Pearson Education Australia Pty. Limited Pearson Education Singapore Pte. Ltd. Pearson Education North Asia Ltd. Pearson Education Canada, Ltd. Pearson Educación de Mexico, S.A. de C.V. Pearson Education—Japan Pearson Education Malaysia Pte. -

Understanding How Organizations Operate Their IT Capacity-Management Processes Joseph Frederick Bauer
Eastern Michigan University DigitalCommons@EMU Master's Theses, and Doctoral Dissertations, and Master's Theses and Doctoral Dissertations Graduate Capstone Projects 11-16-2015 Understanding how organizations operate their IT capacity-management processes Joseph Frederick Bauer Follow this and additional works at: http://commons.emich.edu/theses Part of the Science and Technology Studies Commons Recommended Citation Bauer, Joseph Frederick, "Understanding how organizations operate their IT capacity-management processes" (2015). Master's Theses and Doctoral Dissertations. 660. http://commons.emich.edu/theses/660 This Open Access Dissertation is brought to you for free and open access by the Master's Theses, and Doctoral Dissertations, and Graduate Capstone Projects at DigitalCommons@EMU. It has been accepted for inclusion in Master's Theses and Doctoral Dissertations by an authorized administrator of DigitalCommons@EMU. For more information, please contact [email protected]. Understanding How Organizations Operate Their IT Capacity-Management Processes by Joseph Frederick Bauer Dissertation Submitted to the College of Technology Eastern Michigan University in partial fulfillment of the requirements for the degree of DOCTOR OF PHILOSOPHY Technology Concentration in Technology Management Dissertation Committee: Al Bellamy, PhD, Dissertation Chair Ali Eydgahi, Ph.D. Dorothy McAllen, Ph.D. Denise Tanguay, Ph.D. November 16, 2015 Ypsilanti, Michigan Running head: UNDERSTANDING HOW ORGANIZATIONS ii Acknowledgements The author would like to acknowledge the help and support he received from his family, friends, colleagues, and mentors. Completing this research was a large commitment and your continued support made it possible. Thank you. Special thanks to Dr. Carol Haddad for her support and feedback while working through this dissertation. -

Production Capacity Planning Under Different Procurement Strategies with Considering of Business Objectives
Production capacity planning under different procurement strategies with considering of business objectives Sidi Wu Department of Industrial & Management Systems Engineering Faculty of Science & Engineering, WASEDA University, Tokyo, Japan [email protected] Hisashi Onari Department of Industrial & Management Systems Engineering Faculty of Science & Engineering, WASEDA University, Tokyo, Japan Abstract This study concerns the production capacity planning on products and components which are on their fast-growing stage. Capacity planning Decision making model under spot contract and supply chain contract for players with different business objectives was designed to investigate the better procurement strategy by comparing with ROA and Market share. Keywords: Supply chain, Procurement strategy, Contract INTRODUCTION In this paper, we focus on the manufacturers who producing the mature stage products and supplying them to the product market. In order to finish products producing, it is necessary for them to do procurement of key components to finish products producing from the component market. Market share up strategy is usually considered by these manufacturers to get more profit to extend the surviving period in such mature market with heavy price competition. To expand market share, it means, manufacturers should do investment of production capacity continuously. Price increasing and short supply of components makes the manufacturers worry about low profit achievement and over investment. Especially, while the components are on their fast-growing stage, high price fluctuation and high supply uncertainty make components procurement risk more serious. For example, like the camera manufacturers in Japan, they are under such severe environments. Camera is a mature product in Japan, a CCD image sensor can be considered as the key component of a camera, the sell price of a camera decided by the price of a sensor. -

Cooperative and Noncooperative Games for Capacity Planning and Scheduling
INFORMS 2008 c 2008 INFORMS | isbn 978-1-877640-23-0 doi 10.1287/educ.1080.0041 Cooperative and Noncooperative Games for Capacity Planning and Scheduling Nicholas G. Hall Department of Management Sciences and 3D Laboratory, Fisher College of Business, The Ohio State University, Columbus, Ohio 43210, hall 33@fisher.osu.edu Zhixin Liu Department of Management Studies, School of Management, University of Michigan–Dearborn, Dearborn, Michigan 48126, [email protected] Abstract This tutorial provides an overview of cooperative and noncooperative games for capac- ity planning and scheduling decisions. For both cooperative and noncooperative games, we present some basic definitions and concepts, review the recent literature, and dis- cuss our own current research. The discussion of the literature of cooperative games includes sequencing games, models of outsourcing operations, and economic lot-sizing and schedule planning games. Our research considers a combined capacity plan- ning and scheduling problem where a supplier allocates capacity to distributors, who may then cooperate to share their capacity allocations and resubmit revised orders. The discussion of the literature of noncooperative games includes capacity allocation mechanisms based on order sizes and sales, incentives for truth telling, models of decentralized versus centralized decision making, and auction mechanisms for capac- ity allocation. Our research develops an auction mechanism to allocate capacity to various agents with jobs that can be scheduled profitably; depending upon the choice of market good in the auction, there may be some flexibility in converting the allo- cated capacity into a feasible schedule. We also provide a discussion of future research directions, where we identify several issues that can be studied using new cooperative and noncooperative games. -

Understanding How Organizations Operate Their IT Capacity-Management Processes Joseph Frederick Bauer
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Eastern Michigan University: Digital Commons@EMU Eastern Michigan University DigitalCommons@EMU Master's Theses, and Doctoral Dissertations, and Master's Theses and Doctoral Dissertations Graduate Capstone Projects 11-16-2015 Understanding how organizations operate their IT capacity-management processes Joseph Frederick Bauer Follow this and additional works at: http://commons.emich.edu/theses Part of the Science and Technology Studies Commons Recommended Citation Bauer, Joseph Frederick, "Understanding how organizations operate their IT capacity-management processes" (2015). Master's Theses and Doctoral Dissertations. 660. http://commons.emich.edu/theses/660 This Open Access Dissertation is brought to you for free and open access by the Master's Theses, and Doctoral Dissertations, and Graduate Capstone Projects at DigitalCommons@EMU. It has been accepted for inclusion in Master's Theses and Doctoral Dissertations by an authorized administrator of DigitalCommons@EMU. For more information, please contact [email protected]. Understanding How Organizations Operate Their IT Capacity-Management Processes by Joseph Frederick Bauer Dissertation Submitted to the College of Technology Eastern Michigan University in partial fulfillment of the requirements for the degree of DOCTOR OF PHILOSOPHY Technology Concentration in Technology Management Dissertation Committee: Al Bellamy, PhD, Dissertation Chair Ali Eydgahi, Ph.D. Dorothy McAllen, Ph.D. Denise Tanguay, Ph.D. November 16, 2015 Ypsilanti, Michigan Running head: UNDERSTANDING HOW ORGANIZATIONS ii Acknowledgements The author would like to acknowledge the help and support he received from his family, friends, colleagues, and mentors. Completing this research was a large commitment and your continued support made it possible. -

6 Steps to Successful Capacity Management
6 Steps to Successful Capacity Management Deliver consistently high-quality digital services while avoiding wasted spend Why capacity management matters—more than ever Today, business success depends That’s especially important in modern hybrid cloud environments, which are especially prone on digital excellence. To compete, Unused server capacity differentiate, and win, companies need to overprovisioning, sprawl, management complexity, and unnecessary operating expense. to deliver the high-quality services their 28% According to ESG, 81 percent of enterprises use customers’ demand and they must two or more public cloud environments, and maintain this reliability no matter how 51 percent use three or more. fast or how often things change. With IT infrastructure budget now spanning both With capacity management, you can make informed decisions about which apps, services, operational and capital, it’s also essential Unused storage capacity to get the most possible out of every and workloads make the most sense to move to the cloud, as well as about the right way 40% dollar spent. to make those moves. Visibility into what you have, what you’re using, and what you’re paying Capacity management provides the visibility and for makes it possible to manage cost and avoid insight to keep your IT resources closely aligned overspending. with business needs. According to Gartner, approximately 28 percent of server capacity In this ebook, we’ll explore the practice, value, currently goes unused, as well as 40 percent and steps for successfully managing your IT enterprises using two or more of storage. By taking a holistic approach to public cloud environments infrastructure – regardless of whether they are planning, management, and optimization for on premises or in the cloud. -

A Deeper Dive Into the Question of Investment Capacity
For Professional Investors and Advisers Only A deeper dive into the question of investment capacity Arthur Grigoryants As transparency in the broader investment industry relates directly to an implicit contract between the asset gradually increases, largely assisted by regulation such manager and its customers. There are a few other as MiFID II in Europe, investors today have ever greater definitions used within our industry, including those that visibility of the various costs involved in managing their try to estimate a maximum amount of wealth that could assets. Such improved investor awareness, amongst be created (i.e. trying to solve for a maximum product other things, now allows our clients to consider a of alpha and AUM) or the one that defines capacity as broader range of costs when discussing capacity with a maximum AUM at which the net excess return of an their investment managers. investment approach is reduced to zero. We will ignore those for the purposes of this article as the one we focus In our view, the investment capacity of any active on is the only client-centric one and therefore, in our strategy is an extremely important subject as it is directly minds, the only one that matters. linked to an investment manager’s ability to deliver a high quality service to its customers. It also often acts How is alpha affected by increasing AUM? as a very effective gauge for clients seeking to establish whether their investment service provider is primarily If we focus on alpha potential, then the first important driven by its own business interests (i.e. -

The Storage Capacity Design Dilemma an ITIL Approach
KT v01.14 EDUCATION The Storage Capacity Design Dilemma an ITIL approach LeRoy Budnik Knowledge Transfer KT v01.14 SNIA Legal Notice EDUCATION • The material contained in this tutorial is copyrighted by the SNIA and portions are subject to other copyrights1. • Member companies and individuals may use this material in presentations and literature under the following conditions: – Any slide or slides used must be reproduced without modification – The SNIA must be acknowledged as source of any material used in the body of any document containing material from these presentations. – This specific legal notice shall not be removed. • This presentation is a project of the SNIA Education Committee. The Storage Capacity Design Dilemma © 2007 Storage Networking Industry Association. All Rights Reserved. 1 © 1997-2007 Knowledge Transfer 2 KT v01.14 Abstract EDUCATION The Storage Capacity Design Dilemma As architects, we must continually discover capability limits, constraints, and patterns and match requirements, capabilities and cost to provide an effective design. When we add the business requirements, it becomes the core mantra of ILM. Yet translating these requirements into hardware and software is not easy. In the process, we must continuously choose between complex alternatives, some of which seem equally unacceptable, and hence the dilemma. In this session, we will introduce fundamentals of storage infrastructure design from the perspective of ILM requirements. We will introduce key formulas, the science of storage capacity planning and follow a case study to demonstrate application in host, fabric and array design, to meet the requirements. The dilemmas of design decisions clear up once you know the formulas.