Thesis Al Fannah
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Uila Supported Apps
Uila Supported Applications and Protocols updated Oct 2020 Application/Protocol Name Full Description 01net.com 01net website, a French high-tech news site. 050 plus is a Japanese embedded smartphone application dedicated to 050 plus audio-conferencing. 0zz0.com 0zz0 is an online solution to store, send and share files 10050.net China Railcom group web portal. This protocol plug-in classifies the http traffic to the host 10086.cn. It also 10086.cn classifies the ssl traffic to the Common Name 10086.cn. 104.com Web site dedicated to job research. 1111.com.tw Website dedicated to job research in Taiwan. 114la.com Chinese web portal operated by YLMF Computer Technology Co. Chinese cloud storing system of the 115 website. It is operated by YLMF 115.com Computer Technology Co. 118114.cn Chinese booking and reservation portal. 11st.co.kr Korean shopping website 11st. It is operated by SK Planet Co. 1337x.org Bittorrent tracker search engine 139mail 139mail is a chinese webmail powered by China Mobile. 15min.lt Lithuanian news portal Chinese web portal 163. It is operated by NetEase, a company which 163.com pioneered the development of Internet in China. 17173.com Website distributing Chinese games. 17u.com Chinese online travel booking website. 20 minutes is a free, daily newspaper available in France, Spain and 20minutes Switzerland. This plugin classifies websites. 24h.com.vn Vietnamese news portal 24ora.com Aruban news portal 24sata.hr Croatian news portal 24SevenOffice 24SevenOffice is a web-based Enterprise resource planning (ERP) systems. 24ur.com Slovenian news portal 2ch.net Japanese adult videos web site 2Shared 2shared is an online space for sharing and storage. -

The Web Never Forgets: Persistent Tracking Mechanisms in the Wild
The Web Never Forgets: Persistent Tracking Mechanisms in the Wild Gunes Acar1, Christian Eubank2, Steven Englehardt2, Marc Juarez1 Arvind Narayanan2, Claudia Diaz1 1KU Leuven, ESAT/COSIC and iMinds, Leuven, Belgium {name.surname}@esat.kuleuven.be 2Princeton University {cge,ste,arvindn}@cs.princeton.edu ABSTRACT 1. INTRODUCTION We present the first large-scale studies of three advanced web tracking mechanisms — canvas fingerprinting, evercookies A 1999 New York Times article called cookies compre and use of “cookie syncing” in conjunction with evercookies. hensive privacy invaders and described them as “surveillance Canvas fingerprinting, a recently developed form of browser files that many marketers implant in the personal computers fingerprinting, has not previously been reported in the wild; of people.” Ten years later, the stealth and sophistication of our results show that over 5% of the top 100,000 websites tracking techniques had advanced to the point that Edward employ it. We then present the first automated study of Felten wrote “If You’re Going to Track Me, Please Use Cook evercookies and respawning and the discovery of a new ev ies” [18]. Indeed, online tracking has often been described ercookie vector, IndexedDB. Turning to cookie syncing, we as an “arms race” [47], and in this work we study the latest present novel techniques for detection and analysing ID flows advances in that race. and we quantify the amplification of privacy-intrusive track The tracking mechanisms we study are advanced in that ing practices due to cookie syncing. they are hard to control, hard to detect and resilient Our evaluation of the defensive techniques used by to blocking or removing. -

Do Not Track a Nokia Browser Look
Do Not Track Nokia Browser Position - Vikram Malaiya Copyright: Nokia Corporation, 2011 Our understanding of Do Not Track (DNT) • DNT is a technology to enables users to opt out of third-party web tracking • No agreed upon definition of DNT. There are currently 3 major technology proposals for responding to third-party privacy concern. 1. Stanford University and Mozilla’s DNT HTTP Header technique. 2. Blacklist based technique such as Microsoft’s ‘Tracking Protection’ which is part of IE9 3. Network Advertising Initiative’s model of a per company opt-out cookie. Opt-out cookie approach is being promoted by Google. DNT as HTTP Header The Browser adds ‘DNT’/ ‘X-Do-Not-Track’ to its http header. The header is sent out to the server with every web request. This header acts as a signal to the server suggesting that the user wishes to opt out of tracking. Adoption: Firefox 4, IE9 DNT as HTTP Header • Pros: – Scope: Server could apply restrictions to all third party entities and tracking mechanisms – Persistent: No reconfiguration needed once set – Simple: Easy to implement on the browser side • Cons: – Only work as long as the server honors users preferences – No way to enforce national regulations/legislations to servers located beyond country boundaries Block(Black) List / Tracking Protection This is a consumer opt-in mechanism which blocks web connections from known tracking domains that are compiled on a list. First party Third party Adoption: ‘Tracking Protection’ in Internet Explorer 9 cy.analytix.com The downloadable Tracking allow Protection Lists enable IE9 xy.ads.com consumers to control what deny third-party site content can deny track them when they’re ads.tracker.com Tracking Protection online. -

Settlement Terms, As Approved by Venus’S Counsel and Class Counsel, Subject to Approval by The
Case3:15-cv-03578-EDL Document15 Filed09/29/15 Page1 of 29 1 LEXINGTON LAW GROUP Mark N. Todzo, State Bar No. 168389 2 Abigail Blodgett, State Bar No. 278813 503 Divisadero Street 3 San Francisco, CA 94117 Telephone: (415) 913-7800 4 Facsimile: (415) 759-4112 [email protected] 5 [email protected] 6 HALUNEN LAW Melissa W. Wolchansky (pro hac vice pending) 7 Charles D. Moore (pro hac vice pending) 80 South Eighth Street, Suite 1650 8 Minneapolis, MN 55402 Telephone: (612) 605-4098 9 Facsimile: (612) 605-4099 [email protected] 10 [email protected] 11 Attorneys for Plaintiffs and the Putative Classes 12 UNITED STATES DISTRICT COURT 13 NORTHERN DISTRICT OF CALIFORNIA 14 SAN FRANCISCO DIVISION 15 16 REBEKAH BAHARESTAN and JENA Case No. 3:15-cv-03578-EDL MCINTYRE, on behalf of themselves and all 17 others similarly situated, MEMORANDUM OF POINTS AND AUTHORITIES IN SUPPORT OF 18 Plaintiffs, MOTION FOR PRELIMINARY APPROVAL OF CLASS ACTION 19 v. SETTLEMENT AGREEMENT 20 Date: November 3, 2015 VENUS LABORATORIES, INC., dba EARTH Time: 10:00 a.m. 21 FRIENDLY PRODUCTS, INC., Location: Courtroom E Judge: Hon. Elizabeth D. Laporte 22 Defendant. 23 24 25 26 27 28 Case No. 3:15-cv-03578-EDL MEMORANDUM OF POINTS AND AUTHORITIES IN SUPPORT OF JOINT MOTION FOR PRELIMINARY APPROVAL OF CLASS ACTION SETTLEMENT AGREEMENT Case3:15-cv-03578-EDL Document15 Filed09/29/15 Page2 of 29 TABLE OF CONTENTS 1 Page 2 NOTICE OF MOTION AND MOTION ....................................................................................... vi 3 MEMORANDUM OF POINTS AND AUTHORITIES .................................................................1 4 INTRODUCTION ...........................................................................................................................1 5 STATEMENT OF FACTS ..............................................................................................................2 6 I. -

Anonymous Rate Limiting with Direct Anonymous Attestation
Anonymous rate limiting with Direct Anonymous Attestation Alex Catarineu Philipp Claßen Cliqz GmbH, Munich Konark Modi Josep M. Pujol 25.09.18 Crypto and Privacy Village 2018 Data is essential to build services 25.09.18 Crypto and Privacy Village 2018 Problems with Data Collection IP UA Timestamp Message Payload Cookie Type 195.202.XX.XX FF.. 2018-07-09 QueryLog [face, facebook.com] Cookie=966347bfd 14:01 1e550 195.202.XX.XX Chrome.. 2018-07-09 Page https://analytics.twitter.com/user/konark Cookie=966347bfd 14:06 modi 1e55040434abe… 195.202.XX.XX Chrome.. 2018-07-09 QueryLog [face, facebook.com] Cookie=966347bfd 14:10 1e55040434abe… 195.202.XX.XX Chrome.. 2018-07-09 Page https://booking.com/hotels/barcelona Cookie=966347bfd 16:15 1e55040434abe… 195.202.XX.XX Chrome.. 2018-07-09 QueryLog [face, facebook.com] Cookie=966347bfd 14:10 1e55040434abe… 195.202.XX.XX FF.. 2018-07-09 Page https://shop.flixbus.de/user/resetting/res Cookie=966347bfd 18:40 et/hi7KTb1Pxa4lXqKMcwLXC0XzN- 1e55040434abe… 47Tt0Q 25.09.18 Crypto and Privacy Village 2018 Anonymous data collection Timestamp Message Type Payload 2018-07-09 14 Querylog [face, facebook.com] 2018-07-09 14 Querylog [boo, booking.com] 2018-07-09 14 Page https://booking.com/hotels/barcelona 2018-07-09 14 Telemetry [‘engagement’: 0 page loads last week, 5023 page loads last month] More details: https://gist.github.com/solso/423a1104a9e3c1e3b8d7c9ca14e885e5 http://josepmpujol.net/public/papers/big_green_tracker.pdf 25.09.18 Crypto and Privacy Village 2018 Motivation: Preventing attacks on anonymous data collection Timestamp Message Type Payload 2018-07-09 14 querylog [book, booking.com] 2018-07-09 14 querylog [fac, facebook.com] … …. -
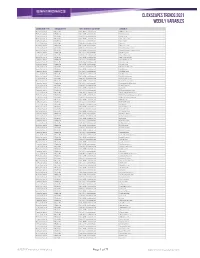
Clickscapes Trends 2021 Weekly Variables
ClickScapes Trends 2021 Weekly VariableS Connection Type Variable Type Tier 1 Interest Category Variable Home Internet Website Arts & Entertainment 1075koolfm.com Home Internet Website Arts & Entertainment 8tracks.com Home Internet Website Arts & Entertainment 9gag.com Home Internet Website Arts & Entertainment abs-cbn.com Home Internet Website Arts & Entertainment aetv.com Home Internet Website Arts & Entertainment ago.ca Home Internet Website Arts & Entertainment allmusic.com Home Internet Website Arts & Entertainment amazonvideo.com Home Internet Website Arts & Entertainment amphitheatrecogeco.com Home Internet Website Arts & Entertainment ancestry.ca Home Internet Website Arts & Entertainment ancestry.com Home Internet Website Arts & Entertainment applemusic.com Home Internet Website Arts & Entertainment archambault.ca Home Internet Website Arts & Entertainment archive.org Home Internet Website Arts & Entertainment artnet.com Home Internet Website Arts & Entertainment atomtickets.com Home Internet Website Arts & Entertainment audible.ca Home Internet Website Arts & Entertainment audible.com Home Internet Website Arts & Entertainment audiobooks.com Home Internet Website Arts & Entertainment audioboom.com Home Internet Website Arts & Entertainment bandcamp.com Home Internet Website Arts & Entertainment bandsintown.com Home Internet Website Arts & Entertainment barnesandnoble.com Home Internet Website Arts & Entertainment bellmedia.ca Home Internet Website Arts & Entertainment bgr.com Home Internet Website Arts & Entertainment bibliocommons.com -

MEIEA 2014 Color.Indd
Journal of the Music & Entertainment Industry Educators Association Volume 14, Number 1 (2014) Bruce Ronkin, Editor Northeastern University Published with Support from Songs As Branding Platforms? A Historical Analysis of People, Places, and Products in Pop Music Lyrics Storm Gloor University of Colorado Denver Abstract Artists have become decidedly more accustomed to partnering with product marketers. Typically, though, the relationships have involved tour sponsorships, endorsements, or the use of the artist’s music in commer- cials. There are plenty of examples of using popular music in advertising. However, how often has there been advertising in popular music? Artists are in a sense “brands.” Many of them appear to promote or acquaint au- diences with their lifestyles through the music they create. Popular songs can serve not only as a mechanism for the subtle marketing of commer- cial consumer products, but also as a platform for marketing artists. Three types of branding devices are typically employed by songwriters: the men- tion of specific product brands, geographical places including cities and states, and well-known people (e.g., celebrities, cultural icons, and politi- cians). The aim of this study is to identify just how often these three types of lyrical references have occurred in popular songs through the years. How frequently have popular songs employed lyrics that may be serving the purpose of branding or advertising consumer products or the artists themselves, and are there observable trends regarding the practice over -

List of Brands
Global Consumer 2019 List of Brands Table of Contents 1. Digital music 2 2. Video-on-Demand 4 3. Video game stores 7 4. Digital video games shops 11 5. Video game streaming services 13 6. Book stores 15 7. eBook shops 19 8. Daily newspapers 22 9. Online newspapers 26 10. Magazines & weekly newspapers 30 11. Online magazines 34 12. Smartphones 38 13. Mobile carriers 39 14. Internet providers 42 15. Cable & satellite TV provider 46 16. Refrigerators 49 17. Washing machines 51 18. TVs 53 19. Speakers 55 20. Headphones 57 21. Laptops 59 22. Tablets 61 23. Desktop PC 63 24. Smart home 65 25. Smart speaker 67 26. Wearables 68 27. Fitness and health apps 70 28. Messenger services 73 29. Social networks 75 30. eCommerce 77 31. Search Engines 81 32. Online hotels & accommodation 82 33. Online flight portals 85 34. Airlines 88 35. Online package holiday portals 91 36. Online car rental provider 94 37. Online car sharing 96 38. Online ride sharing 98 39. Grocery stores 100 40. Banks 104 41. Online payment 108 42. Mobile payment 111 43. Liability insurance 114 44. Online dating services 117 45. Online event ticket provider 119 46. Food & restaurant delivery 122 47. Grocery delivery 125 48. Car Makes 129 Statista GmbH Johannes-Brahms-Platz 1 20355 Hamburg Tel. +49 40 2848 41 0 Fax +49 40 2848 41 999 [email protected] www.statista.com Steuernummer: 48/760/00518 Amtsgericht Köln: HRB 87129 Geschäftsführung: Dr. Friedrich Schwandt, Tim Kröger Commerzbank AG IBAN: DE60 2004 0000 0631 5915 00 BIC: COBADEFFXXX Umsatzsteuer-ID: DE 258551386 1. -

QI Wireless Compatible Device List Apple Asus Blackberry CASIO
QI Wireless Compatible Device List Apple • iPhone 8 • iPhone 8 Plus • iPhone X • iPhone Xs • iPhone Xs Max • iPhone Xr Asus • Asus PadFone S BlackBerry • BlackBerry Passport • BlackBerry PRIV • BlackBerry Z30 CASIO • CASIO G'z One Commando Caterpillar • Cat S50 • Cat S50C DeWalt • Dewalt MD501 • Dewalt MIL810G Energy Sistem • Energy Phone Pro Qi Fujitsu • Fujitsu Arrows F-09D • Fujitsu Arrows Kiss F-03D • Fujitsu Arrows Kiss F-03E • Fujitsu Arrows X F-10D Google • Google Nexus 4 • Google Nexus 5 • Google Nexus 6 • Google Pixel 3 • Google Pixel 3 XL HP • HP Elite X3 HTC • HTC Droid DNA • HTC Windows Phone 8X Huawei • Huawei Mate20 Pro • Huawei Mate RS Porsche Design • Huawei P30 Pro Kyocera • Kyocera Brigadier • Kyocera DuraForce • Kyocera Hydro Elite • Kyocera Torque G02 • Kyocera Torque KC-S701 • Kyocera Urbano L01 • Kyocera Urbano L03 LG • LG G2 • LG G3 • LG G6 ¹ • LG G6 Plus ¹ • LG G7 • LG G7 ThinQ • LG Lucid 2 • LG Lucid 3 • LG Optimus F5 • LG Optimus G Pro • LG Optimus It L-05E • LG Spectrum 2 • LG Vu 2 • LG Vu 3 • LG V30 • LG V30 Plus • LG V40 ThinQ M.T.T. • M.T.T. Master 4G Meizu • Meizu Zero Microsoft • Microsoft Lumia 950 • Microsoft Lumia 950 Dual Sim • Microsoft Lumia 950 XL • Microsoft Lumia 950 XL Dual Sim Mlais • Mlais MX69W Motorola • Motorola Droid Maxx • Motorola Droid Mini • Motorola Droid Turbo • Motorola Droid Turbo 2 • Motorola Moto Maxx • Motorola Moto X Force mPhone • mPhone 8 NEC • NEC Medias PP N-01D • NEC Medias X N-04E Noa • Noa F10 Pro Nokia • Nokia Lumia 1520 • Nokia Lumia 735 • Nokia Lumia 830 • Nokia Lumia -
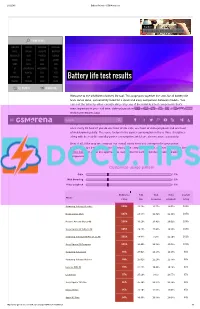
Battery Life Test Results HUAWEI TOSHIBA INTEX PLUM
2/12/2015 Battery life tests GSMArena.com Starborn SAMSUNG GALAXY S6 EDGE+ REVIEW PHONE FINDER SAMSUNG LENOVO VODAFONE VERYKOOL APPLE XIAOMI GIGABYTE MAXWEST MICROSOFT ACER PANTECH CELKON NOKIA ASUS XOLO GIONEE SONY OPPO LAVA VIVO LG BLACKBERRY MICROMAX NIU HTC ALCATEL BLU YEZZ MOTOROLA ZTE SPICE PARLA Battery life test results HUAWEI TOSHIBA INTEX PLUM ALL BRANDS RUMOR MILL Welcome to the GSMArena battery life tool. This page puts together the stats for all battery life tests we've done, conveniently listed for a quick and easy comparison between models. You can sort the table by either overall rating or by any of the individual test components that's most important to you call time, video playback or web browsing.TIP US 828K 100K You can find all about our84K 137K RSS LOG IN SIGN UP testing procedures here. SearchOur overall rating gives you an idea of how much battery backup you can get on a single charge. An overall rating of 40h means that you'll need to fully charge the device in question once every 40 hours if you do one hour of 3G calls, one hour of video playback and one hour of web browsing daily. The score factors in the power consumption in these three disciplines along with the reallife standby power consumption, which we also measure separately. Best of all, if the way we compute our overall rating does not correspond to your usage pattern, you are free to adjust the different usage components to get a closer match. Use the sliders below to adjust the approximate usage time for each of the three battery draining components. -

Whotracks. Me: Shedding Light on the Opaque World of Online Tracking
WhoTracks.Me: Shedding light on the opaque world of online tracking Arjaldo Karaj Sam Macbeth Rémi Berson [email protected] [email protected] [email protected] Josep M. Pujol [email protected] Cliqz GmbH Arabellastraße 23 Munich, Germany ABSTRACT print users and their devices [25], and the extent to Online tracking has become of increasing concern in recent which these methods are being used across the web [5], years, however our understanding of its extent to date has and quantifying the value exchanges taking place in on- been limited to snapshots from web crawls. Previous at- line advertising [7, 27]. There is a lack of transparency tempts to measure the tracking ecosystem, have been done around which third-party services are present on pages, using instrumented measurement platforms, which are not and what happens to the data they collect is a common able to accurately capture how people interact with the web. concern. By monitoring this ecosystem we can drive In this work we present a method for the measurement of awareness of the practices of these services, helping to tracking in the web through a browser extension, as well as inform users whether they are being tracked, and for a method for the aggregation and collection of this informa- what purpose. More transparency and consumer aware- tion which protects the privacy of participants. We deployed ness of these practices can help drive both consumer this extension to more than 5 million users, enabling mea- and regulatory pressure to change, and help researchers surement across multiple countries, ISPs and browser con- to better quantify the privacy and security implications figurations, to give an accurate picture of real-world track- caused by these services. -

Vmlogin Virtual Multi-Login Browser Instruction Ver
VMLogin virtual multi-login browser Instruction Ver 1.0 Skype: [email protected] Telegram1: Vmlogin Telegram2: vmlogin_us System Requirements Hardware requirements RAM: 4GB recommended; 1GB available disk space Effective GPU Supported operating systems Although VMLogin supports x86 (32-bit) systems, we recommend using VMLogin on x64 (64-bit) systems. OS supported by VMLogin Windows 10 Windows Server 2016 Windows 7 Windows 8 Software install Users can download the latest software installation package from the official website: vmlogin.us. The version used in this manual is 1.0.3.8. We can start the software installation package program, and the interface for selecting the installation language will be displayed: User can select the software language he likes, and can also change the language in the settings after installation. Currently supports Simplified Chinese and English. After the user select the language, enter the interface for selecting the installation directory: Here is generally installed by default, press the "Next" button, if the user customizes the installation directory, please pay attention to the directory permissions, the current user can edit. Generally, you need to create a desktop shortcut for convenient, we click the "Next" button to continue by default here. At this point we can click the "Install" button to install. We need to wait for the installation progress to complete. At this step, the software installation is complete. Software function 1. Start Software When we start the software, we will see the login interface. New users need to create a new account to log in. 2. Create Account To register as a new user, you need to use email as your account, set a password, and register.