Bluesocket Wireless Gateway Setup and Administration Guide V4.0
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Connectra Web Security Gateway
puresecurity PRODUCT DESCRIPTION Connectra Connectra™ is a complete Web Security Gateway that unifies SSL VPN access with comprehensive endpoint security Web Security Gateway and integrated intrusion prevention. Web connectivity with unmatched security PRODUCT FEATURES n Secure SSL VPN remote access YOUR CHALLENGE n Comprehensive endpoint security Access to information is critical to modern businesses, and, increasingly, n Integrated intrusion prevention employees and business partners need to access it anytime from virtually n Appliance or software platforms anywhere. Sharing timely information increases your business competitiveness, partnership effectiveness, and employee productivity. And sharing this informa- tion requires a solution that is universally available and easy to use—even for PRODUCT BENEFITS the lay user. n Delivers Web-based secure remote access for an extensive In addition to enabling ubiquitous access, the confidentiality and integrity of range of enterprise applications this information is even more important in today’s information-driven economy. Yet the explosion of spyware, like keystroke loggers and Trojan horses, threat- n Shields information from malicious ens the confidentiality and integrity of information shared with remote users. spyware and malware on remote endpoints Bottom line, you need to provide easy access to information from anywhere n Defends the integrity of internal while ensuring that your enterprise IT resources retain their security everywhere. infrastructure from worms and attacks n Provides standalone or full OUR SOLUTION SmartCenter™ central management ™ Connectra is a complete Web Security Gateway that provides SSL VPN n Protects against new threats access and comprehensive endpoint and integrated intrusion prevention through SmartDefense™ Services security in a single, unified solution. -

Check Point Firewall V1.0
Check Point Firewall Benchmark v1.0 Editor: John Traenkenschuh December 2007 Copyright 2001-2007, The Center for Internet Security (CIS) http://cisecurity.org [email protected] TERMS OF USE AGREEMENT Background. The Center for Internet Security ("CIS") provides benchmarks, scoring tools, software, data, information, suggestions, ideas, and other services and materials from the CIS website or elsewhere (―Products‖) as a public service to Internet users worldwide. Recommendations contained in the Products (―Recommendations‖) result from a consensus-building process that involves many security experts and are generally generic in nature. The Recommendations are intended to provide helpful information to organizations attempting to evaluate or improve the security of their networks, systems, and devices. Proper use of the Recommendations requires careful analysis and adaptation to specific user requirements. The Recommendations are not in any way intended to be a ―quick fix‖ for anyone‘s information security needs. No Representations, Warranties, or Covenants. CIS makes no representations, warranties, or covenants whatsoever as to (i) the positive or negative effect of the Products or the Recommendations on the operation or the security of any particular network, computer system, network device, software, hardware, or any component of any of the foregoing or (ii) the accuracy, reliability, timeliness, or completeness of the Products or the Recommendations. CIS is providing the Products and the Recommendations ―as is‖ and ―as available‖ without representations, warranties, or covenants of any kind. User Agreements. By using the Products and/or the Recommendations, I and/or my organization (―We‖) agree and acknowledge that: 1. No network, system, device, hardware, software, or component can be made fully secure; 2. -

030107 Schulungskatalog 07.Indd
Horizonte erweitern? Die neuen Trainings for Professionals 2007 07 2 Editorial Liebe Leserin, lieber Leser, ich freue mich, Ihnen eine überaus positive Neuigkeit mitteilen Noch Fragen zu unseren Schulungen? zu können: die Training Group COMPUTERLINKS wurde aufgrund Für mehr Details wenden Sie sich ihrer überragenden Leistung und allerbester Referenzen von in Deutschland bitte an: Microsoft in der Kategorie „Best Learning Solution“ zum Schulungszentrum München „Microsoft Partner 2006“ gekürt. T: +49 (0)89 9 30 99-168, F: +49 (0)89 9 30 99-499 [email protected] http://training.computerlinks.de Eine Auszeichnung, über die wir uns ganz besonders freuen, da Schulungszentrum Frankfurt sie unsere außergewöhnlichen Anstrengungen im Trainingsmarkt T: +49 (0)6103 98 45-50, F: +49 (0)6103 98 45-55 [email protected] belohnt. Sicher hat dabei auch eine Rolle gepielt, dass wir als http://training.computerlinks.de Microsoft Gold Partner mit unseren zertifizierten und fest- Schulungszentrum Berlin angestellten Trainern in den letzten drei Jahren mehr als 2.000 Teilnehmer auf die unter- in Kooperation mit SPC GmbH schiedlichsten Microsoft-Produkte und -Zertifizierungen vorbereitet haben. T: +49 (0)6103 98 45-50, F: +49 (0)6103 98 45-55 [email protected] http://training.computerlinks.de Natürlich haben wir bereits für das neue Betriebssystem Microsoft Vista eine Reihe von Kursen Schulungszentrum Düsseldorf (ab Seite 32) in unserem Schulungsangebot. Dazu bietet Microsoft zwei Ausbildungsgänge an: in Kooperation mit Unilog Integrata Training AG den Technology Specialist (TS) und den Enterprise Desktop Support Technician (EDST). Ebenso T: +49 (0)6103 98 45-50, F: +49 (0)6103 98 45-55 können Sie sich schon für Schulungen zum neuen Microsoft Exchange Server 2007 anmelden. -

Security Gateway Appliances R77 Security Target
Security Gateway Appliances R77 Security Target Version 1.4 November 18, 2013 Prepared by: Metatron Security Services Metatron Security Services Ltd. Security Gateway Appliances R77 Security Target Version 1.4 2 Prologue 11/18/2013 © 2013 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright and distributed under licensing restricting their use, copying, distribution, and decompilation. No part of this product or related documentation may be reproduced in any form or by any means without prior written authorization of Check Point. While every precaution has been taken in the preparation of this book, Check Point assumes no responsibility for errors or omissions. This publication and features described herein are subject to change without notice. RESTRICTED RIGHTS LEGEND: Use, duplication, or disclosure by the government is subject to restrictions as set forth in subparagraph (c)(1)(ii) of the Rights in Technical Data and Computer Software clause at DFARS 252.227-7013 and FAR 52.227-19. TRADEMARKS: Refer to the Copyright page (http://www.checkpoint.com/copyright.html) for a list of our trademarks. Refer to the Third Party copyright notices (http://www.checkpoint.com/3rd_party_copyright.html) for a list of relevant copyrights and third-party licenses. Copyright 2013, Check Point Software Technologies Ltd. All Rights Reserved. Security Gateway Appliances R77 Security Target Version 1.4 3 Prologue 11/18/2013 Document Version Control Log Version Date Author Description Version 0.1 July 13, Nir Initial draft. 2009 Naaman Version 0.5 December Nir Post-iVOR updates: removed FAU_SAA.4. Expanded 7, 2009 Naaman description of L2TP support. -

KATALOG SZKOLEN 2008 Siêgnij Po Profesjonaln¹ Wiedzê
KATALOG SZKOLEN 2008 siêgnij po profesjonaln¹ wiedzê BEZPIECZENSTWO SYSTEMY MICROSOFT SYSTEMY LINUX SIECI I TELEKOMUNIKACJA BAZY DANYCH PRZECHOWYWANIE DANYCH ZARZADZANIE PROJEKTAMI I PROCESAMI www.compendium.pl SZKOLENIA AUTORYZOWANE 3Com .................. 4 Assuria .................. 4 Check Point Software Technologies .................. 4 Computer Associates .................. 4 Extreme Networks .................. 5 F5 Networks .................. 5 Fortinet .................. 5 F-Secure .................. 5 IBM Internet Security Systems .................. 6 Microsens .................. 6 Microsoft .................. 6 Molex Premise Networks .................. 10 MySQL .................. 10 Nokia Enterprise Solutions .................. 10 Novell .................. 11 Proxim Corporation .................. 11 Red Hat .................. 12 RSA Security .................. 12 Sony .................. 12 Utimaco Software .................. 12 SZKOLENIA AUTORSKIE Bezpieczeństwo .................. 13 Bazy danych .................. 13 Przechowywanie danych .................. 13 Systemy Linux .................. 14 Systemy Microsoft .................. 14 Sieci i telekomunikacja .................. 15 Zarządzanie projektami i procesami .................. 15 Centrum Egzaminacyjne Pearson VUE .................. 16 Centrum Egzaminacyjne Prometric .................. 16 Centrum Kompetencyjne HP .................. 16 Linux Center For Excellence .................. 16 Novell Practicum Testing Center .................. 16 SZKOLENIA AUTORYZOWANE 3Com Authorized -

End-Point Security with Check Point Integrity
End-point security with Check Point Integrity Patrick Hanel 1 June 2006 ©2006 Check Point Software Technologies Ltd. Proprietary & Confidential Agenda Risks to Endpoints Business Requirements to Secure Endpoints – Policy management – Access rights – Network protection Integrity Endpoint Security Solution – IPS – Program Controls – Anti-X – Compliance Enforcement Deployment Options – Scalability – Manageability 1 June 2006 2 ©2006 Check Point Software Technologies Ltd. Proprietary & Confidential Many Endpoint Threats Keystroke Contractor logger with latest capturing worm or virus ID, PW Backdoor Unauthorized listening for access to HR inbound server connection Rogue Spyware wireless download user via P2P and IM 1 June 2006 3 ©2006 Check Point Software Technologies Ltd. Proprietary & Confidential Endpoint Security Value Keep the network up and running Avoid disruption of operations Block exposure of sensitive data TCO Stop theft of proprietary information Protect valuable reputation, brand Maintain executive confidence 1 June 2006 4 ©2006 Check Point Software Technologies Ltd. Proprietary & Confidential Business Requirements to Secure Endpoints Policy management – Reusable Policy Elements – Monitoring & Reporting Access rights – End User rights to networks and applications – Endpoint Compliance Validation Network Protection – Protect key elements of Infrastructure – Ensure Uptime and availability – Integrity with current networking components 1 June 2006 5 ©2006 Check Point Software Technologies Ltd. Proprietary & Confidential Solution: -

Check Point VSX Security Target
Check Point VSX Security Target Version 1.1 May 20, 2012 Prepared for: 5 Ha’Solelim St. Tel Aviv, Israel 67897 Prepared by: Metatron Security Services Ltd. 66 Yosef St., Modiin, Israel 71724 All marks, trademarks, and logos mentioned in this material are the property of their respective owners. ©2012 Check Point Software Technologies Ltd. All Rights Reserved. Classification: [Unrestricted]—For everyone Check Point VSX Security Target Version 1.1 2 Prologue 5/20/2012 Document Version Control Log Version Date Author Description 0.1 June 11, 2009 Nir Naaman Initial CCv3.1 version. 0.7 October 15, 2009 Nir Naaman Post-iVOR validator-requested updates. 0.95 November 9, 2011 Nir Naaman Updated TOE software version to VSX R67.10.20 in combination with Provider-1 R71 with R7x hotfix. Added supported VSX appliances. 1.0 February 15, 2012 Nir Naaman Updated list of supported Open Servers. Referenced updated evaluated configuration guidance. 1.1 May 20, 2012 Nir Naaman Referenced final evaluated configuration guidance. ©2012 Check Point Software Technologies Ltd. All Rights Reserved. 2 Classification: [Unrestricted]—For everyone Check Point VSX Security Target Version 1.1 3 Prologue 5/20/2012 Table of Contents 1. ST Introduction ........................................................................................................................... 9 1.1. ST Reference .................................................................................................................. 9 1.2. TOE Reference .............................................................................................................. -

ICS Dissolvable Agent for Safeguard Administration Guide Contents
ICS Dissolvable Agent for SafeGuard Alcatel-Lucent Release 2.2 ICS Release 4.0 Administration Guide PART NUMBER: 005-0030 REV A1 PUBLISHED: MARCH 2007 ALCATEL-LUCENT 26801 WEST AGOURA ROAD CALABASAS, CA 91301 USA (818) 880-3500 WWW.ALCATEL-LUCENT.COM Alcatel-Lucent Proprietary Copyright © 2007 Alcatel-Lucent. All rights reserved. This document may not be reproduced in whole or in part without the expressed written permission Alcatel-Lucent. Alcatel-Lucent ® and the Alcatel- Lucent logo are registered trademarks of Alcatel-Lucent. All other trademarks are the property of their respective owners. 2 ICS Dissolvable Agent for SafeGuard Administration Guide Contents Preface About this Guide . 6 Related Publications. 6 Chapter 1: Introduction Integrity Clientless Security Features . 10 Integrity Clientless Security Scanner. 10 Reports . 10 ICSInfo Utility. 10 Supported Features . 11 Unsupported Features . 11 Chapter 2: Prerequisites End Point Prerequisites . 14 Supported Operating Systems . .14 Supported Browsers . 14 Java Requirements . 14 Chapter 3: General Administration Tasks Planning for Security . 16 Security Scenario . 16 Vulnerabilities . 16 Risks . 17 End Point Users and Disruption Tolerance . 17 Sample Solution . 17 Understanding Security Lifecycles . .17 Supporting the End Point User. 19 Logging In . 19 Configuration Workflow . 20 General Administration Tasks. 20 Configuring ICS to Fail Open. 21 Configuring Updates . 21 ICS Dissolvable Agent for SafeGuard Administration Guide 3 Contents Chapter 4: Administering Security Scanner Policies Understanding Integrity Clientless Security Scanner. 24 Implementing Policies . 24 Understanding Enforcement Rules . 24 Enforcement Rule Types . 25 Firewall Application Rules . 26 Creating a Firewall Application Rule . 26 Anti-virus Application Rules . 27 Creating an Anti-virus Application Rule . 27 Anti-Spyware Scan Rules . -

Check Point Userauthority Guide
Check Point UserAuthority Guide Version NGX R62 700358 January 2006 © 2003-2006 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright and distributed under licensing restricting their use, copying, distribution, and decompilation. No part of this product or related documentation may be reproduced in any form or by any means without prior written authorization of Check Point. While every precaution has been taken in the preparation of this book, Check Point assumes no responsibility for errors or omissions. This publication and features described herein are subject to change without notice. RESTRICTED RIGHTS LEGEND: Use, duplication, or disclosure by the government is subject to restrictions as set forth in subparagraph (c)(1)(ii) of the Rights in Technical Data and Computer Software clause at DFARS 252.227-7013 and FAR 52.227-19. TRADEMARKS: ©2003-2006 Check Point Software Technologies Ltd. All rights reserved. Check Point, Application Intelligence, Check Point Express, the Check Point logo, AlertAdvisor, ClusterXL, ConnectControl, Connectra, Cooperative Enforcement, Cooperative Security Alliance, CoSa, DefenseNet, Eventia, Eventia Analyzer, Eventia Reporter, FireWall-1, FireWall -1 GX, FireWall-1 SecureServer, FloodGate-1, Hacker ID, IMsecure, INSPECT, INSPECT XL, Integrity, InterSpect, IQ Engine, NGX, Open Security Extension, OPSEC, OSFirewall, Policy Lifecycle Management, Provider-1, Safe@Office, SecureClient, SecureKnowledge, SecuRemote, SecurePlatform, SecureServer, -

Integrity Secureclient Mobile
Integrity SecureClient Mobile For additional technical information about Check Point products, consult Check Point’s SecureKnowledge at: https://secureknowledge.checkpoint.com View the latest version of this document in the User Center at: http://www.checkpoint.com/support/technical/documents/ August 2006 © 2003-2005 Check Point Software Technologies Ltd. NONINFRINGEMENT. IN NO EVENT SHALL THE OPEN GROUP BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, All rights reserved. This product and related documentation are protected by copyright TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE and distributed under licensing restricting their use, copying, distribution, and SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE. decompilation. No part of this product or related documentation may be reproduced in The following statements refer to those portions of the software copyrighted by The any form or by any means without prior written authorization of Check Point. While every OpenSSL Project. This product includes software developed by the OpenSSL Project for precaution has been taken in the preparation of this book, Check Point assumes no use in the OpenSSL Toolkit (http://www.openssl.org/). responsibility for errors or omissions. This publication and features described herein are THIS SOFTWARE IS PROVIDED BY THE OpenSSL PROJECT ``AS IS'' AND ANY * subject to change without notice. EXPRESSED OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR RESTRICTED RIGHTS LEGEND: PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE OpenSSL PROJECT OR ITS Use, duplication, or disclosure by the government is subject to restrictions as set forth in CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, subparagraph (c)(1)(ii) of the Rights in Technical Data and Computer Software clause at EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, DFARS 252.227-7013 and FAR 52.227-19. -

1. Operating Systems: 1
1 Krishna: 9849010760 Hi all, If u want any Software Cd’s or DVD’s call : +91 98490 10760 Or Mail : [email protected] 1. Operating Systems: 1. Windows 98 SE Boot CD ……… …………………………………….……….…….…100/- 2. Windows 95 Boot CD.……………………………………………….……………………100/- 3. Windows ME Boot CD ………………………………………………………….……..…100/- 4. Windows NT Server4.0 Boot CD ………………………………………….…….….……100/- 5. Windows NT Workstation Boot CD …………………………………..………………….100/- 6. Windows 2000 Prof Boot CD …………………………………………….…….….…….100/- 7. Windows 2000 Server Boot CD …………………….……………………..……..………100/- 8. Windows 2000 Adv Server Boot CD …………………………………………………….100/- 9. Windows XP Prof. Boot CD …………………………………………………….……..…100/- 10. Windows XP Prof. With Service Pack 1 (SP1) Boot CD…....……………………………100/- 11. Windows XP Prof. With Service Pack 2 (SP2) Boot CD…………………………..……..100/- 12. Windows 2003 Server Ent. Full Version Boot CD ……………………………………….100/- 13. Dos6.22 , WinNT Server, Win ME, Win97, Win98Se, Win NT Workstation……………100/- 14. Red hat Linux 7.2 Boot ……………………..……….………3 CD’s……………………150/- 15. Red hat Linux 8.0 Boot ……………..……………….……… 4 CD’s…………..…….….250/- 16. Red hat Linux 9.0 Boot ………………….….……….………7 CD’s……………………400/- 17. Fedora Core 1 (RH Linux 10.0) …………………………….. 5 CD’s………………..…..300/- 18. FEDORA CORE 3…………………………………………... 4 CD’s……………………250/- 19. Red Hat Linux Advanced Server 2.1AS …………………… 4 CD’s………………..…..250/- 20. Red Hat Enterprise Linux 3.0……………….……..…………4 CD’s……….……….…..300/- 21. SUSE Linux 8.0 Boot ……………………………… ……… 3 CD’s……..……………..200/- 22. Suse Linux 9.1 Prof …………………………….……………5 CD’s….………………..300/- 23. Sco-Unix 5.05. Boot ……………………………………………….……………………..100/- 24. Sco-Unix 7.1.1 Boot ……………………………………..…. 4 CD’s…….…….………..300/- 25. Novel Netware 6.0 ……………………………….…………. 3 CD’s……………..……..250/- 26. -
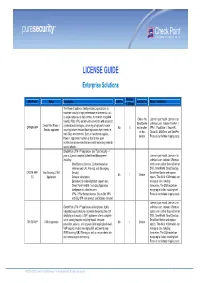
LICENSE GUIDE Enterprise Solutions
LICENSE GUIDE Enterprise Solutions Number SKU Prefix Name Description Additive Installed on Notes / Limitations of Strings The Power-1 appliance family enables organizations to maximize security in high-performance environments such as large campuses or data centers. It combines integrated One on the License is per model. License is for firewall, IPSec VPN, and intrusion prevention with advanced SmartCenter unlimited users.Includes FireWall-1, Check Point Power-1 acceleration technologies, delivering a high-performance CPPWR-APP No 2 and another VPN-1, FloodGate-1, SecureXL, Security appliance security platform that can block application layer threats in on the ClusterXL, MultiCore, and SplatPro. multi-Gbps environments. Even as new threats appear, device) Prices do not include shipping costs. Power-1 appliances maintain or-due to their open architecture-increase performance while protecting networks against attacks. Check Point UTM-1™ appliances plus Total Security – 1 year or 3 years complete Unified threat Management License is per model. License is for including: unlimited users. Includes 5 Remote - SmartDefense Services, Content Inspection access users (either SecureClient or (Antivirus and URL Filtering), and Messaging SNX), SmartPortal, SmartDirectory, CPUTM-APP- Total Security UTM-1 Security. SmartView Monitor and express No 1 Device TS Appliances - Software subscription, reports. The 450 & 1050 models can - Entitlement to reduced product support rates. manage 3 sites including - Check Point FireWall-1 including Application themselves. The 2050 model can Intelligence for unlimited users mange up to 5 sites including itself. - VPN – IPSec Remote Access, Site-to-Site VPN, Prices do not include shipping costs. and SSL VPN (see product specification) included License is per model.