Nucypher Documentation Release 5.3.1
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Implementation of Smart Contracts for Blockchain Based Iot Applications
Implementation of smart contracts for blockchain based IoT applications Georgios Papadodimas, Georgios Palaiokrasas, Antoniοs Litke, Theodora Varvarigou Electrical and Computer Engineering Department National Technical University of Athens Athens, Greece [email protected], [email protected], [email protected], [email protected] Abstract—An increasing number of people, organizations [11], funding mechanisms [12] and many more. A milestone and corporations are expressing their interest in the for the course of blockchain technology was the development decentralization technology of the blockchain. The creation of of Ethereum project, offering new solutions by enabling smart the blockchain marks the time when we start building contracts’ implementation and execution. The Ethereum distributed peer-to-peer networks consisting of non-trusting blockchain is a Turing complete platform for executing smart members that interact with each other without a trusted contracts [13], [14], and not just a ledger serving financial intermediary but in a verifiable manner. In this paper, we transactions. It is a suite of tools and protocols for the creation propose a decentralized application (DApp) based on and operation of Decentralized Applications (DApps), blockchain technology for sharing Internet of Things (IoT) “applications that run exactly as programmed without any sensors’ data, and demonstrate various challenges addressed possibility of downtime, censorship, fraud or third-party during the development process. This application combines blockchain technology with IoT and operates through smart interference”. It also supports a contract-oriented, high-level, contracts that are executed on the Ethereum blockchain. More Turing-complete programming language [15], allowing specifically the application is a platform for sharing (buying and anyone to write smart contracts and create DApps. -

Versus Decentralized Prediction Markets for Financial Assets
Wolfgang Pacher Centralized- versus Decentralized Prediction Markets for Financial Assets Are blockchain-based prediction market applications simply the better solution to forecasting financial assets? MASTER THESIS submitted in fulfilment of the requirements for the degree of Master of Science Programme: Master's programme Applied Business Administration Branch of study: General Management Alpen-Adria-Universität Klagenfurt Evaluator Assoc.Prof.Mag.Dr. Alexander Brauneis Alpen-Adria-Universität Klagenfurt Institut für Finanzmanagement Klagenfurt, May 2019 Affidavit I hereby declare in lieu of an oath that - the submitted academic paper is entirely my own work and that no auxiliary materials have been used other than those indicated, - I have fully disclosed all assistance received from third parties during the process of writing the thesis, including any significant advice from supervisors, - any contents taken from the works of third parties or my own works that have been included either literally or in spirit have been appropriately marked and the respective source of the information has been clearly identified with precise bibliographical references (e.g. in footnotes), - to date, I have not submitted this paper to an examining authority either in Austria or abroad and that - when passing on copies of the academic thesis (e.g. in bound, printed or digital form), I will ensure that each copy is fully consistent with the submitted digital version. I understand that the digital version of the academic thesis submitted will be used for the purpose of conducting a plagiarism assessment. I am aware that a declaration contrary to the facts will have legal consequences. Wolfgang Pacher m.p. -

Metamask Pre-Assignment
MMS 562F: Tech Driven Transformation MetaMask Pre-Assignment Campbell R. Harvey Duke University and NBER February 2021 Setup • Metamask is a cryptocurrency wallet that is used to interface with the Ethereum-based Apps • We will be setting up this Wallet on your mobile device (iOS or Android only) – If you are unable to use a mobile device, the end of this deck has a web browser tutorial (Page 19) – If you already have MetaMask on your browser, the end of this deck has a tutorial to link your Web Account to the Mobile App (Page 25) Campbell R. Harvey 2021 2 Setup • Download the Metamask app from the App Store or Google Play Store • Click Get Started • Click Create a new wallet • Create a new account by typing in a password of your choosing and pressing “Create” • Go through the prompts to secure your wallet • Store Secret Backup Phrase in a secure location, ideally paper or a password manager – not on your phone or computer. • Type in secret backup phrase Campbell R. Harvey 2021 3 1 Using MetaMask 1. Network • This determines which Ethereum Network you are using. Click on this to see all network options in a 2 dropdown. For this class we will only discuss or use the Main Ethereum Network and the Ropsten Test Network. 3 Campbell R. Harvey 2021 4 1 Using MetaMask 1. Network • The Ethereum Mainnet is where live ether (ETH) with real value exists and is 2 used for payment and applications. I will refer to this as the “main network” or the “mainnet” 3 Campbell R. -

Bibliography of Erik Wilde
dretbiblio dretbiblio Erik Wilde's Bibliography References [1] AFIPS Fall Joint Computer Conference, San Francisco, California, December 1968. [2] Seventeenth IEEE Conference on Computer Communication Networks, Washington, D.C., 1978. [3] ACM SIGACT-SIGMOD Symposium on Principles of Database Systems, Los Angeles, Cal- ifornia, March 1982. ACM Press. [4] First Conference on Computer-Supported Cooperative Work, 1986. [5] 1987 ACM Conference on Hypertext, Chapel Hill, North Carolina, November 1987. ACM Press. [6] 18th IEEE International Symposium on Fault-Tolerant Computing, Tokyo, Japan, 1988. IEEE Computer Society Press. [7] Conference on Computer-Supported Cooperative Work, Portland, Oregon, 1988. ACM Press. [8] Conference on Office Information Systems, Palo Alto, California, March 1988. [9] 1989 ACM Conference on Hypertext, Pittsburgh, Pennsylvania, November 1989. ACM Press. [10] UNIX | The Legend Evolves. Summer 1990 UKUUG Conference, Buntingford, UK, 1990. UKUUG. [11] Fourth ACM Symposium on User Interface Software and Technology, Hilton Head, South Carolina, November 1991. [12] GLOBECOM'91 Conference, Phoenix, Arizona, 1991. IEEE Computer Society Press. [13] IEEE INFOCOM '91 Conference on Computer Communications, Bal Harbour, Florida, 1991. IEEE Computer Society Press. [14] IEEE International Conference on Communications, Denver, Colorado, June 1991. [15] International Workshop on CSCW, Berlin, Germany, April 1991. [16] Third ACM Conference on Hypertext, San Antonio, Texas, December 1991. ACM Press. [17] 11th Symposium on Reliable Distributed Systems, Houston, Texas, 1992. IEEE Computer Society Press. [18] 3rd Joint European Networking Conference, Innsbruck, Austria, May 1992. [19] Fourth ACM Conference on Hypertext, Milano, Italy, November 1992. ACM Press. [20] GLOBECOM'92 Conference, Orlando, Florida, December 1992. IEEE Computer Society Press. http://github.com/dret/biblio (August 29, 2018) 1 dretbiblio [21] IEEE INFOCOM '92 Conference on Computer Communications, Florence, Italy, 1992. -

Decentralized Reputation Model and Trust Framework Blockchain and Smart Contracts
IT 18 062 Examensarbete 30 hp December 2018 Decentralized Reputation Model and Trust Framework Blockchain and Smart contracts Sujata Tamang Institutionen för informationsteknologi Department of Information Technology Abstract Decentralized Reputation Model and Trust Framework: Blockchain and Smart contracts Sujata Tamang Teknisk- naturvetenskaplig fakultet UTH-enheten Blockchain technology is being researched in diverse domains for its ability to provide distributed, decentralized and time-stamped Besöksadress: transactions. It is attributed to by its fault-tolerant and zero- Ångströmlaboratoriet Lägerhyddsvägen 1 downtime characteristics with methods to ensure records of immutable Hus 4, Plan 0 data such that its modification is computationally infeasible. Trust frameworks and reputation models of an online interaction system are Postadress: responsible for providing enough information (e.g., in the form of Box 536 751 21 Uppsala trust score) to infer the trustworthiness of interacting entities. The risk of failure or probability of success when interacting with an Telefon: entity relies on the information provided by the reputation system. 018 – 471 30 03 Thus, it is crucial to have an accurate, reliable and immutable trust Telefax: score assigned by the reputation system. The centralized nature of 018 – 471 30 00 current trust systems, however, leaves the valuable information as such prone to both external and internal attacks. This master's thesis Hemsida: project, therefore, studies the use of blockchain technology as an http://www.teknat.uu.se/student infrastructure for an online interaction system that can guarantee a reliable and immutable trust score. It proposes a system of smart contracts that specify the logic for interactions and models trust among pseudonymous identities of the system. -

Bookings of Westin Diplomat Bookings
RESTful Web Applications with Spring 3.0 Arjen Poutsma Senior Software Engineer SpringSource Speaker’s qualifications • Fifteen years of experience in Enterprise Software Development • Six years of Web service experience • Development lead of Spring Web Services • Working on Spring 3.0 • Contributor to various Open Source frameworks: (XFire, Axis2, NEO, ...) SpringSource Confidential. Do not distribute without express permission Overview • RESTful URLs • URI templates • Content negotiation • HTTP method conversion • ETag support SpringSource Confidential. Do not distribute without express permission RESTful URLs Resources • URLs are unique identifiers for Resources • Typically nouns • Customer • Orders • Shopping cart URLs [scheme:][//authority][path][?query][#fragment] http://www.springsource.com https://mybank.com http://www.google.com/search?q=arjen %20poutsma http://java.sun.com/j2se/1.4.2/docs/api/java/lang/ String.html#indexOf(int) SpringSource Confidential. Do not distribute without express permission Paths • Represents hierarchy • Represents value for consumers • Collections on higher levels SpringSource Confidential. Do not distribute without express permission Example Path Description /hotels List of all hotels /hotels/westindiplomat Details of Westin Diplomat /hotels/westindiplomat/ List of bookings of Westin Diplomat bookings /hotels/westindiplomat/ Individual booking bookings/42584 No Hierarchy? Path Description maps/24.9195,17.821 Commas maps/24.9195;17.821 Semicolons Query Variables • Input for algorithms • Get ignored by proxies -

Makoto Yano Chris Dai Kenichi Masuda Yoshio Kishimoto Editors
Economics, Law, and Institutions in Asia Pacific Makoto Yano Chris Dai Kenichi Masuda Yoshio Kishimoto Editors Blockchain and Crypto Currency Building a High Quality Marketplace for Crypto Data Economics, Law, and Institutions in Asia Pacific Series Editor Makoto Yano, Research Institute of Economy, Trade and Industry (RIETI), Tokyo, Japan The Asia Pacific region is expected to steadily enhance its economic and political presence in the world during the twenty-first century. At the same time, many serious economic and political issues remain unresolved in the region. To further academic enquiry and enhance readers’ understanding about this vibrant region, the present series, Economics, Law, and Institutions in Asia Pacific, aims to present cutting-edge research on the Asia Pacific region and its relationship with the rest of the world. For countries in this region to achieve robust economic growth, it is of foremost importance that they improve the quality of their markets, as history shows that healthy economic growth cannot be achieved without high-quality markets. High-quality markets can be established and maintained only under a well-designed set of rules and laws, without which competition will not flourish. Based on these principles, this series places a special focus on economic, business, legal, and institutional issues geared towards the healthy development of Asia Pacific markets. The series considers book proposals for scientific research, either theoretical or empirical, that is related to the theme of improving market quality and has policy implications for the Asia Pacific region. The types of books that will be considered for publication include research monographs as well as relevant proceedings. -
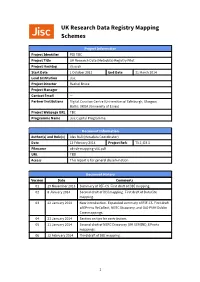
UK Research Data Registry Mapping Schemes
UK Research Data Registry Mapping Schemes Project Information Project Identifier PID TBC Project Title UK Research Data (Metadata) Registry Pilot Project Hashtag #jiscrdr Start Date 1 October 2013 End Date 31 March 2014 Lead Institution Jisc Project Director Rachel Bruce Project Manager — Contact Email — Partner Institutions Digital Curation Centre (Universities of Edinburgh, Glasgow, Bath); UKDA (University of Essex) Project Webpage URL TBC Programme Name Jisc Capital Programme Document Information Author(s) and Role(s) Alex Ball (Metadata Coordinator) Date 12 February 2014 Project Refs T3.1; D3.1 Filename uk-rdr-mapping-v06.pdf URL TBD Access This report is for general dissemination Document History Version Date Comments 01 29 November 2013 Summary of RIF-CS. First draft of DDI mapping. 02 8 January 2014 Second draft of DDI mapping. First draft of DataCite mapping. 03 22 January 2014 New introduction. Expanded summary of RIF-CS. First draft of EPrints ReCollect, NERC Discovery, and OAI-PMH Dublin Core mappings. 04 23 January 2014 Section on tips for contributors. 05 31 January 2014 Second draft of NERC Discovery (UK GEMINI), EPrints mappings. 06 12 February 2014 Third draft of DDI mapping. 1 Contents 1 Introduction 3 1.1 Typographical conventions . 3 2 RIF-CS 4 2.1 Elements . 4 2.2 Controlled vocabularies . 8 3 Internally managed RIF-CS elements 20 4 Mapping from DDI to RIF-CS 21 4.1 Related Objects . 22 5 Mapping from UK GEMINI 2 to RIF-CS 24 5.1 Related Objects . 26 6 Mapping from DataCite to RIF-CS 27 6.1 Related Objects . -

Gemini and NTS Exit Reform API Usage Guidelines
Gemini and NTS Exit Reform API Usage Guidelines ~ 1 ~ Table of Contents 1. Introduction ............................................................................................................................................6 1.1. API Technology Overview ....................................................................................................................6 2. API Client Development Guidelines .....................................................................................................8 2.1. HTTPS and SSL ...................................................................................................................................9 2.2. Authentication and Authorization ...................................................................................................... 10 2.3. Maintaining the Session .................................................................................................................... 10 2.4. Authentication / Loss of Session / Authorization Failures ................................................................. 10 2.5. Request a Compressed Response to your API Client ...................................................................... 11 3. API Configuration Details ................................................................................................................... 14 3.1. API Technology Overview ................................................................................................................. 14 3.2. Network Requirements ..................................................................................................................... -
$5.75 $727,91Mm $664,28Mm $7.50 +31.16% +
ETC INSIGHTS JULY 2020 07 MARKET JULY 01 JULY 31 $5.75 $7.50 +31.16% PRICE PRICE $727,91MM $876,75MM +148,835MM VOLUME (1D) VOLUME (1D) $664,28MM $857,30MM +193,020MM MARKET CAP MARKET CAP TECHNOLOGY UPDATES Core Geth seeing more adoption Core-geth is seeing the largest growing node adoption. Ethereum Classic no longer has LTS support for OpenEthereum or Multi-geth. Therefore, Ethereum Classic nodes must transition to Core-geth or Besu. 2nd most popular client, likely to reach most popular as Ethereum Classic no longer has LTS support for OpenEth & Multi-geth DEVELOPMENT Signatory and affiliated tools are nearing more maturity Growing collaboration with MetaMask regarding OpenRPC SigTools nearly Alpha Learn More ROADMAP CHANGES Tooling team is gathering requirements for a wallet project which may impact roadmap NEW TOOLS & FEATURES Signatory Core Learn More COMMUNITY ACCELERATOR NEWS & COHORT MEMBER UPDATES ETC Labs Announces Cohort III, Blockchain for Impact Startups Learn More EVENTS Blockchain course Angel Investing Learn More Learn More Ask Me Anything (AMA) Learn More SFBW’s Unitize 2020 Virtual Conference Watch the Presentation MOIP Episode feat. ETC Labs CEO Terry Culver Watch the Episode UNIVERSITIES INTEGRATIONS PARTNERSHIPS NEWS & EXISTING PARTNER UPDATES SWARM Alpha Event Learn More Launch Connect with Bloq, a developer suite platform for ETC and multi-chain support Learn More ETC Labs partners with World Wildlife Foundation Learn More WORKS IN PROGRESS ETC to build a stablecoin with top stablecoin project Diversifying support with more decentralized storage projects Leading AML project to support Accelerator startups and ETC SPOTLIGHT COHORT III Png.me Prescypto Open Relay Learn More Learn More Learn More IN THE NEWS RECENT MEDIA COVERAGE Ethereum Classic Labs Presents its Third Cohort and its Startups Learn More ETC Labs Launches Cohort III To Support Blockchain-Powered Impact Startups Learn More Ethereum Classic (ETC) Going Hot about How to Run a Swarm Node Learn More MoIP Interview with Terry Culver CEO ETC Labs Learn More ETC INSIGHTS JULY 2020. -

HTTPAPI S. Dalal Internet-Draft Intended Status: Standards Track E
HTTPAPI S. Dalal Internet-Draft Intended status: Standards Track E. Wilde Expires: January 11, 2022 July 10, 2021 The Deprecation HTTP Header Field draft-ietf-httpapi-deprecation-header-02 Abstract The HTTP Deprecation Response Header Field can be used to signal to consumers of a URI-identified resource that the resource has been deprecated. Additionally, the deprecation link relation can be used to link to a resource that provides additional context for the deprecation, and possibly ways in which clients can find a replacement for the deprecated resource. Status of This Memo This Internet-Draft is submitted in full conformance with the provisions of BCP 78 and BCP 79. Internet-Drafts are working documents of the Internet Engineering Task Force (IETF). Note that other groups may also distribute working documents as Internet-Drafts. The list of current Internet- Drafts is at https://datatracker.ietf.org/drafts/current/. Internet-Drafts are draft documents valid for a maximum of six months and may be updated, replaced, or obsoleted by other documents at any time. It is inappropriate to use Internet-Drafts as reference material or to cite them other than as "work in progress." This Internet-Draft will expire on January 11, 2022. Copyright Notice Copyright (c) 2021 IETF Trust and the persons identified as the document authors. All rights reserved. This document is subject to BCP 78 and the IETF Trust’s Legal Provisions Relating to IETF Documents (https://trustee.ietf.org/license-info) in effect on the date of publication of this document. Please review these documents carefully, as they describe your rights and restrictions with respect to this document. -

Next Steps in the Evolution of Decentralized Oracle Networks
Chainlink 2.0: Next Steps in the Evolution of Decentralized Oracle Networks Lorenz Breidenbach1 Christian Cachin2 Benedict Chan1 Alex Coventry1 Steve Ellis1 Ari Juels3 Farinaz Koushanfar4 Andrew Miller5 Brendan Magauran1 Daniel Moroz6 Sergey Nazarov1 Alexandru Topliceanu1 Florian Tram`er7 Fan Zhang8 15 April 2021 v1.0 1Chainlink Labs 2The author is a faculty member at University of Bern. He co-authored this work in his separate capacity as an advisor to Chainlink Labs. 3The author is a faculty member at Cornell Tech. He co-authored this work in his separate capacity as Chief Scientist at Chainlink Labs. 4The author is a faculty member at University of California, San Diego. She co-authored this work in her separate capacity as an advisor to Chainlink Labs. 5The author is a faculty member at University of Illinois Urbana-Champaign. He co-authored this work in his separate capacity as an advisor on Chainlink. 6The author is a PhD candidate at Harvard University. He co-authored this work while on leave from Harvard, in his capacity as a researcher at Chainlink Labs. 7The author is a PhD candidate at Stanford University. He co-authored this work in his separate capacity as an advisor to Chainlink Labs. 8The author will be joining the faculty of Duke University in fall 2021. He co-authored this work in his current capacity as a researcher at Chainlink Labs. 1 Abstract In this whitepaper, we articulate a vision for the evolution of Chainlink be- yond its initial conception in the original Chainlink whitepaper. We foresee an increasingly expansive role for oracle networks, one in which they comple- ment and enhance existing and new blockchains by providing fast, reliable, and confidentiality-preserving universal connectivity and off-chain computation for smart contracts.