Percolation and Random Graphs
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Interpolation for Partly Hidden Diffusion Processes*
Interpolation for partly hidden di®usion processes* Changsun Choi, Dougu Nam** Division of Applied Mathematics, KAIST, Daejeon 305-701, Republic of Korea Abstract Let Xt be n-dimensional di®usion process and S(t) be a smooth set-valued func- tion. Suppose X is invisible when X S(t), but we can see the process exactly t t 2 otherwise. Let X S(t ) and we observe the process from the beginning till the t0 2 0 signal reappears out of the obstacle after t0. With this information, we evaluate the estimators for the functionals of Xt on a time interval containing t0 where the signal is hidden. We solve related 3 PDE's in general cases. We give a generalized last exit decomposition for n-dimensional Brownian motion to evaluate its estima- tors. An alternative Monte Carlo method is also proposed for Brownian motion. We illustrate several examples and compare the solutions between those by the closed form result, ¯nite di®erence method, and Monte Carlo simulations. Key words: interpolation, di®usion process, excursions, backward boundary value problem, last exit decomposition, Monte Carlo method 1 Introduction Usually, the interpolation problem for Markov process indicates that of eval- uating the probability distribution of the process between the discretely ob- served times. One of the origin of the problem is SchrÄodinger's Gedankenex- periment where we are interested in the probability distribution of a di®usive particle in a given force ¯eld when the initial and ¯nal time density functions are given. We can obtain the desired density function at each time in a given time interval by solving the forward and backward Kolmogorov equations. -

Optimal Subgraph Structures in Scale-Free Configuration
Submitted to the Annals of Applied Probability OPTIMAL SUBGRAPH STRUCTURES IN SCALE-FREE CONFIGURATION MODELS , By Remco van der Hofstad∗ §, Johan S. H. van , , Leeuwaarden∗ ¶ and Clara Stegehuis∗ k Eindhoven University of Technology§, Tilburg University¶ and Twente Universityk Subgraphs reveal information about the geometry and function- alities of complex networks. For scale-free networks with unbounded degree fluctuations, we obtain the asymptotics of the number of times a small connected graph occurs as a subgraph or as an induced sub- graph. We obtain these results by analyzing the configuration model with degree exponent τ (2, 3) and introducing a novel class of op- ∈ timization problems. For any given subgraph, the unique optimizer describes the degrees of the vertices that together span the subgraph. We find that subgraphs typically occur between vertices with specific degree ranges. In this way, we can count and characterize all sub- graphs. We refrain from double counting in the case of multi-edges, essentially counting the subgraphs in the erased configuration model. 1. Introduction Scale-free networks often have degree distributions that follow power laws with exponent τ (2, 3) [1, 11, 22, 34]. Many net- ∈ works have been reported to satisfy these conditions, including metabolic networks, the internet and social networks. Scale-free networks come with the presence of hubs, i.e., vertices of extremely high degrees. Another property of real-world scale-free networks is that the clustering coefficient (the probability that two uniformly chosen neighbors of a vertex are neighbors themselves) decreases with the vertex degree [4, 10, 24, 32, 34], again following a power law. -

Detecting Statistically Significant Communities
1 Detecting Statistically Significant Communities Zengyou He, Hao Liang, Zheng Chen, Can Zhao, Yan Liu Abstract—Community detection is a key data analysis problem across different fields. During the past decades, numerous algorithms have been proposed to address this issue. However, most work on community detection does not address the issue of statistical significance. Although some research efforts have been made towards mining statistically significant communities, deriving an analytical solution of p-value for one community under the configuration model is still a challenging mission that remains unsolved. The configuration model is a widely used random graph model in community detection, in which the degree of each node is preserved in the generated random networks. To partially fulfill this void, we present a tight upper bound on the p-value of a single community under the configuration model, which can be used for quantifying the statistical significance of each community analytically. Meanwhile, we present a local search method to detect statistically significant communities in an iterative manner. Experimental results demonstrate that our method is comparable with the competing methods on detecting statistically significant communities. Index Terms—Community Detection, Random Graphs, Configuration Model, Statistical Significance. F 1 INTRODUCTION ETWORKS are widely used for modeling the structure function that is able to always achieve the best performance N of complex systems in many fields, such as biology, in all possible scenarios. engineering, and social science. Within the networks, some However, most of these objective functions (metrics) do vertices with similar properties will form communities that not address the issue of statistical significance of commu- have more internal connections and less external links. -

Modern Discrete Probability I
Preliminaries Some fundamental models A few more useful facts about... Modern Discrete Probability I - Introduction Stochastic processes on graphs: models and questions Sebastien´ Roch UW–Madison Mathematics September 6, 2017 Sebastien´ Roch, UW–Madison Modern Discrete Probability – Models and Questions Preliminaries Review of graph theory Some fundamental models Review of Markov chain theory A few more useful facts about... 1 Preliminaries Review of graph theory Review of Markov chain theory 2 Some fundamental models Random walks on graphs Percolation Some random graph models Markov random fields Interacting particles on finite graphs 3 A few more useful facts about... ...graphs ...Markov chains ...other things Sebastien´ Roch, UW–Madison Modern Discrete Probability – Models and Questions Preliminaries Review of graph theory Some fundamental models Review of Markov chain theory A few more useful facts about... Graphs Definition (Undirected graph) An undirected graph (or graph for short) is a pair G = (V ; E) where V is the set of vertices (or nodes, sites) and E ⊆ ffu; vg : u; v 2 V g; is the set of edges (or bonds). The V is either finite or countably infinite. Edges of the form fug are called loops. We do not allow E to be a multiset. We occasionally write V (G) and E(G) for the vertices and edges of G. Sebastien´ Roch, UW–Madison Modern Discrete Probability – Models and Questions Preliminaries Review of graph theory Some fundamental models Review of Markov chain theory A few more useful facts about... An example: the Petersen graph Sebastien´ Roch, UW–Madison Modern Discrete Probability – Models and Questions Preliminaries Review of graph theory Some fundamental models Review of Markov chain theory A few more useful facts about.. -

Probabilistic and Geometric Methods in Last Passage Percolation
Probabilistic and geometric methods in last passage percolation by Milind Hegde A dissertation submitted in partial satisfaction of the requirements for the degree of Doctor of Philosophy in Mathematics in the Graduate Division of the University of California, Berkeley Committee in charge: Professor Alan Hammond, Co‐chair Professor Shirshendu Ganguly, Co‐chair Professor Fraydoun Rezakhanlou Professor Alistair Sinclair Spring 2021 Probabilistic and geometric methods in last passage percolation Copyright 2021 by Milind Hegde 1 Abstract Probabilistic and geometric methods in last passage percolation by Milind Hegde Doctor of Philosophy in Mathematics University of California, Berkeley Professor Alan Hammond, Co‐chair Professor Shirshendu Ganguly, Co‐chair Last passage percolation (LPP) refers to a broad class of models thought to lie within the Kardar‐ Parisi‐Zhang universality class of one‐dimensional stochastic growth models. In LPP models, there is a planar random noise environment through which directed paths travel; paths are as‐ signed a weight based on their journey through the environment, usually by, in some sense, integrating the noise over the path. For given points y and x, the weight from y to x is defined by maximizing the weight over all paths from y to x. A path which achieves the maximum weight is called a geodesic. A few last passage percolation models are exactly solvable, i.e., possess what is called integrable structure. This gives rise to valuable information, such as explicit probabilistic resampling prop‐ erties, distributional convergence information, or one point tail bounds of the weight profile as the starting point y is fixed and the ending point x varies. -

Patterns in Random Walks and Brownian Motion
Patterns in Random Walks and Brownian Motion Jim Pitman and Wenpin Tang Abstract We ask if it is possible to find some particular continuous paths of unit length in linear Brownian motion. Beginning with a discrete version of the problem, we derive the asymptotics of the expected waiting time for several interesting patterns. These suggest corresponding results on the existence/non-existence of continuous paths embedded in Brownian motion. With further effort we are able to prove some of these existence and non-existence results by various stochastic analysis arguments. A list of open problems is presented. AMS 2010 Mathematics Subject Classification: 60C05, 60G17, 60J65. 1 Introduction and Main Results We are interested in the question of embedding some continuous-time stochastic processes .Zu;0Ä u Ä 1/ into a Brownian path .BtI t 0/, without time-change or scaling, just by a random translation of origin in spacetime. More precisely, we ask the following: Question 1 Given some distribution of a process Z with continuous paths, does there exist a random time T such that .BTCu BT I 0 Ä u Ä 1/ has the same distribution as .Zu;0Ä u Ä 1/? The question of whether external randomization is allowed to construct such a random time T, is of no importance here. In fact, we can simply ignore Brownian J. Pitman ()•W.Tang Department of Statistics, University of California, 367 Evans Hall, Berkeley, CA 94720-3860, USA e-mail: [email protected]; [email protected] © Springer International Publishing Switzerland 2015 49 C. Donati-Martin et al. -
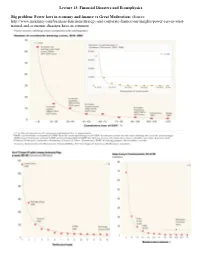
Lecture 13: Financial Disasters and Econophysics
Lecture 13: Financial Disasters and Econophysics Big problem: Power laws in economy and finance vs Great Moderation: (Source: http://www.mckinsey.com/business-functions/strategy-and-corporate-finance/our-insights/power-curves-what- natural-and-economic-disasters-have-in-common Analysis of big data, discontinuous change especially of financial sector, where efficient market theory missed the boat has drawn attention of specialists from physics and mathematics. Wall Street“quant”models may have helped the market implode; and collapse spawned econophysics work on finance instability. NATURE PHYSICS March 2013 Volume 9, No 3 pp119-197 : “The 2008 financial crisis has highlighted major limitations in the modelling of financial and economic systems. However, an emerging field of research at the frontiers of both physics and economics aims to provide a more fundamental understanding of economic networks, as well as practical insights for policymakers. In this Nature Physics Focus, physicists and economists consider the state-of-the-art in the application of network science to finance.” The financial crisis has made us aware that financial markets are very complex networks that, in many cases, we do not really understand and that can easily go out of control. This idea, which would have been shocking only 5 years ago, results from a number of precise reasons. What does physics bring to social science problems? 1- Heterogeneous agents – strange since physics draws strength from electron is electron is electron but STATISTICAL MECHANICS --- minority game, finance artificial agents, 2- Facility with huge data sets – data-mining for regularities in time series with open eyes. 3- Network analysis 4- Percolation/other models of “phase transition”, which directs attention at boundary conditions AN INTRODUCTION TO ECONOPHYSICS Correlations and Complexity in Finance ROSARIO N. -

Constructing a Sequence of Random Walks Strongly Converging to Brownian Motion Philippe Marchal
Constructing a sequence of random walks strongly converging to Brownian motion Philippe Marchal To cite this version: Philippe Marchal. Constructing a sequence of random walks strongly converging to Brownian motion. Discrete Random Walks, DRW’03, 2003, Paris, France. pp.181-190. hal-01183930 HAL Id: hal-01183930 https://hal.inria.fr/hal-01183930 Submitted on 12 Aug 2015 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Discrete Mathematics and Theoretical Computer Science AC, 2003, 181–190 Constructing a sequence of random walks strongly converging to Brownian motion Philippe Marchal CNRS and Ecole´ normale superieur´ e, 45 rue d’Ulm, 75005 Paris, France [email protected] We give an algorithm which constructs recursively a sequence of simple random walks on converging almost surely to a Brownian motion. One obtains by the same method conditional versions of the simple random walk converging to the excursion, the bridge, the meander or the normalized pseudobridge. Keywords: strong convergence, simple random walk, Brownian motion 1 Introduction It is one of the most basic facts in probability theory that random walks, after proper rescaling, converge to Brownian motion. However, Donsker’s classical theorem [Don51] only states a convergence in law. -

© in This Web Service Cambridge University Press Cambridge University Press 978-0-521-14577-0
Cambridge University Press 978-0-521-14577-0 - Probability and Mathematical Genetics Edited by N. H. Bingham and C. M. Goldie Index More information Index ABC, approximate Bayesian almost complete, 141 computation almost complete Abecasis, G. R., 220 metrizabilityalmost-complete Abel Memorial Fund, 380 metrizability, see metrizability Abou-Rahme, N., 430 α-stable, see subordinator AB-percolation, see percolation Alsmeyer, G., 114 Abramovitch, F., 86 alternating renewal process, see renewal accumulate essentially, 140, 161, 163, theory 164 alternating word, see word Addario-Berry, L., 120, 121 AMSE, average mean-square error additive combinatorics, 138, 162–164 analytic set, 147 additive function, 139 ancestor gene, see gene adjacency relation, 383 ancestral history, 92, 96, 211, 256, 360 Adler, I., 303 ancestral inference, 110 admixture, 222, 224 Anderson, C. W., 303, 305–306 adsorption, 465–468, 477–478, 481, see Anderson, R. D., 137 also cooperative sequential Andjel, E., 391 adsorption model (CSA) Andrews, G. E., 372 advection-diffusion, 398–400, 408–410 anomalous spreading, 125–131 a.e., almost everywhere Antoniak, C. E., 324, 330 Affymetrix gene chip, 326 Applied Probability Trust, 33 age-dependent branching process, see appointments system, 354 branching process approximate Bayesian computation Aldous, D. J., 246, 250–251, 258, 328, (ABC), 214 448 approximate continuity, 142 algorithm, 116, 219, 221, 226–228, 422, Archimedes of Syracuse see also computational complexity, weakly Archimedean property, coupling, Kendall–Møller 144–145 algorithm, Markov chain Monte area-interaction process, see point Carlo (MCMC), phasing algorithm process perfect simulation algorithm, 69–71 arithmeticity, 172 allele, 92–103, 218, 222, 239–260, 360, arithmetic progression, 138, 157, 366, see also minor allele frequency 162–163 (MAF) Arjas, E., 350 allelic partition distribution, 243, 248, Aronson, D. -

Processes on Complex Networks. Percolation
Chapter 5 Processes on complex networks. Percolation 77 Up till now we discussed the structure of the complex networks. The actual reason to study this structure is to understand how this structure influences the behavior of random processes on networks. I will talk about two such processes. The first one is the percolation process. The second one is the spread of epidemics. There are a lot of open problems in this area, the main of which can be innocently formulated as: How the network topology influences the dynamics of random processes on this network. We are still quite far from a definite answer to this question. 5.1 Percolation 5.1.1 Introduction to percolation Percolation is one of the simplest processes that exhibit the critical phenomena or phase transition. This means that there is a parameter in the system, whose small change yields a large change in the system behavior. To define the percolation process, consider a graph, that has a large connected component. In the classical settings, percolation was actually studied on infinite graphs, whose vertices constitute the set Zd, and edges connect each vertex with nearest neighbors, but we consider general random graphs. We have parameter ϕ, which is the probability that any edge present in the underlying graph is open or closed (an event with probability 1 − ϕ) independently of the other edges. Actually, if we talk about edges being open or closed, this means that we discuss bond percolation. It is also possible to talk about the vertices being open or closed, and this is called site percolation. -

Percolation Thresholds for Robust Network Connectivity
Percolation Thresholds for Robust Network Connectivity Arman Mohseni-Kabir1, Mihir Pant2, Don Towsley3, Saikat Guha4, Ananthram Swami5 1. Physics Department, University of Massachusetts Amherst, [email protected] 2. Massachusetts Institute of Technology 3. College of Information and Computer Sciences, University of Massachusetts Amherst 4. College of Optical Sciences, University of Arizona 5. Army Research Laboratory Abstract Communication networks, power grids, and transportation networks are all examples of networks whose performance depends on reliable connectivity of their underlying network components even in the presence of usual network dynamics due to mobility, node or edge failures, and varying traffic loads. Percolation theory quantifies the threshold value of a local control parameter such as a node occupation (resp., deletion) probability or an edge activation (resp., removal) probability above (resp., below) which there exists a giant connected component (GCC), a connected component comprising of a number of occupied nodes and active edges whose size is proportional to the size of the network itself. Any pair of occupied nodes in the GCC is connected via at least one path comprised of active edges and occupied nodes. The mere existence of the GCC itself does not guarantee that the long-range connectivity would be robust, e.g., to random link or node failures due to network dynamics. In this paper, we explore new percolation thresholds that guarantee not only spanning network connectivity, but also robustness. We define and analyze four measures of robust network connectivity, explore their interrelationships, and numerically evaluate the respective robust percolation thresholds arXiv:2006.14496v1 [physics.soc-ph] 25 Jun 2020 for the 2D square lattice. -

The Branching Process in a Brownian Excursion
The Branching Process in a Brownian Excursion By J. Neveu Laboratoire de Probabilites Universite P. et M. Curie Tour 56 - 3eme Etage 75252 Paris Cedex 05 Jim Pitman* Department of Statistics University of California Berkeley, California 94720 United States *Research of this author supported in part by NSF Grant DMS88-01808. To appear in Seminaire de Probabilites XXIII, 1989. Technical Report No. 188 February 1989 Department of Statistics University of California Berkeley, California THE BRANCHING PROCESS IN A BROWNIAN EXCURSION by J. NEVEU and J. W. PirMAN t Laboratoire de Probabilit6s Department of Statistics Universit6 Pierre et Marie Curie University of California 4, Place Jussieu - Tour 56 Berkeley, California 94720 75252 Paris Cedex 05, France United States §1. Introduction. This paper offers an alternative view of results in the preceding paper [NP] concerning the tree embedded in a Brownian excursion. Let BM denote Brownian motion on the line, BMX a BM started at x. Fix h >0, and let X = (X ,,0t <C) be governed by Itk's law for excursions of BM from zero conditioned to hit h. Here X may be presented as the portion of the path of a BMo after the last zero before the first hit of h, run till it returns to zero. See for instance [I1, [R1]. Figure 1. Definition of X in terms of a BMo. h Xt 0 A Ad' \A] V " - t - 4 For x > 0, let Nh be the number of excursions (or upcrossings) of X from x to x + h. Theorem 1.1 The process (Nh,x 0O) is a continuous parameter birth and death process, starting from No = 1, with stationary transition intensities from n to n ± 1 of n Ih.