Open-Falcon a Distributed and High-Performance Monitoring System
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Monitoring Container Environment with Prometheus and Grafana
Matti Holopainen Monitoring Container Environment with Prometheus and Grafana Metropolia University of Applied Sciences Bachelor of Engineering Information and Communication Technology Bachelor’s Thesis 3.5.2021 Abstract Tekijä Matti Holopainen Otsikko Monitoring Container Environment with Prometheus and Grafana Sivumäärä Aika 50 sivua 3.5.2021 Tutkinto Insinööri (AMK) Tutkinto-ohjelma Tieto- ja viestintätekniikka Ammatillinen pääaine Ohjelmistotuotanto Ohjaajat Nina Simola, Projektipäällikkö Auvo Häkkinen, Yliopettaja Insinöörityön tavoitteena oli oppia pystyttämään monitorointijärjestelmä konttiympäristön re- surssien käytön seuraamista, monitorointia ja analysoimista varten. Tavoitteena oli helpot- taa monitorointijärjestelmän käyttöönottoa. Työ tehtiin käytettävien ohjelmistojen dokumen- taation ja käytännön tekemisellä opittujen asioiden pohjalta. Insinöörityön alussa käytiin läpi työssä käytettyjä teknologioita. Tämän jälkeen käytiin läpi monitorointi järjestelmän konfiguraatio ja käyttöönotto. Seuraavaksi tutustuttiin PromQL-ha- kukieleen, jonka jälkeen näytettiin kuinka pystyttää valvontamonitori ja hälytykset sähköpos- timuistutuksella. Työn lopussa käydään läpi kuinka monitorointijärjestelmässä saatua dataa analysoidaan ja mietitään miten monitorointijärjestelmää voisi parantaa. Keywords Monitorointi, Kontti, Prometheus, Grafana, Docker Abstract Author Matti Holopainen Title Monitoring Container Environment with Prometheus and Grafana Number of Pages Date 50 pages 3.5.2021 Degree Bachelor of Engineering Degree Programme Information -

Zabbix 4.2 Data Processing and More Sponsors Gold Sponsors Co-Organizer
Zabbix 4.2 data processing and more Sponsors Gold sponsors Co-organizer 2 What is Zabbix? Zabbix is a universal Open Source enterprise level monitoring solution 3 4 We have found a good balance between giving away free software and having a sustainable growth 5 Free Software Services Services that save your time and money Free Software Services Services that save your time and money Customers in 75+ countries 8 Some of our users 9 Zabbix Real-time Alerting & Data collection problem Visualization Remediation detection 10 Where we are currently? 3.0 LTS 3.2 3.4 4.0 LTS 11 Zabbix 4.0 LTS 12 Data preprocessing { “host": { "name": "Linux #2356", "vms": [{ “name”: “vm034”, “network": { "read": “0xfa673”, "write": “0x45b30” } }, { “name”: “vm076”, “network": { "read": “0x76ab”, “write": “0xff3a” } }] } } 13 Data preprocessing "write": “0x45b30” } }, { “name”: “vm076”, “network": { "read": “0x76ab”, 0x76ab “write": “0xff3a” } }] JSON Path: .host.vms[1].network.read } } 14 Data preprocessing 0x76ab JSON Path: .host.vms[1].network.read 15 Data preprocessing 0x76ab 76ab Regexp: 0x(.*) 16 Data preprocessing 0x76ab 76ab 330379 Hex to Decimal 17 Data preprocessing 0x76ab 76ab 330379 338308096 KB -> bytes 18 Data preprocessing 19 Efficiency Zabbix server mysql[status] 20 Efficiency Master item 21 Efficiency Dependent items 22 Efficiency mysql[questions] mysql[status] Zabbix server mysql[reads] 23 Efficiency mysql[questions] mysql[status] Zabbix server mysql[reads] Performance, less user parameters, all logic in templates 24 Limitations 4.0 LTS 4.2 Not flexible -
5. Zabbix Appliance 5
2021/07/12 12:09 1/8 5. Zabbix appliance 5. Zabbix appliance As an alternative to setting up manually or reusing existing server for Zabbix, users may download Zabbix appliance. To get started, boot the appliance and point your browser at the IP it has received over DHCP. Booting Zabbix appliance Zabbix appliance versions are based upon the following OpenSUSE versions: Zabbix appliance version OpenSUSE version 2.2.0 12.3 It is available in the following formats: vmdk (VMware/Virtualbox) OVF (Open Virtualisation Format) KVM CD ISO HDD/flash image Preload ISO Xen guest Microsoft VHD Preload USB Zabbix Documentation 2.2 - https://www.zabbix.com/documentation/2.2/ Last update: 2018/09/04 11:39 manual:appliance https://www.zabbix.com/documentation/2.2/manual/appliance It has Zabbix server configured and running on MySQL, as well as frontend available. The appliance has been built using SUSE Studio. 1 Changes to SUSE configuration There are some changed applied to the base OpenSUSE configuration. 1.1 MySQL configuration changes Binary log is disabled; InnoDB is configured to store data for each table in a separate file. 1.2 Using a static IP address By default the appliance uses DHCP to obtain IP address. To specify a static IP address: Log in as root user; Open file /etc/sysconfig/network/ifcfg-eth0 in your favourite editor; Set BOOTPROTO variable to static; Set IPADDR, NETMASK and any other parameters as required for your network; Create file /etc/sysconfig/network/routes. For the default route, use default 192.168.1.1 - - (replacing with your gateway address). -

5 Installation from Containers Docker
2021/09/23 12:33 1/9 5 Installation from containers 5 Installation from containers Docker Zabbix provides Docker images for each Zabbix component as portable and self-sufficient containers to speed up deployment and update procedure. Zabbix components come with MySQL and PostgreSQL database support, Apache2 and Nginx web server support. These images are separated into different images. Docker base images Zabbix components are provided on Ubuntu, Alpine Linux and CentOS base images: Image Version alpine 3.9 ubuntu bionic centos latest All images are configured to rebuild latest images if base images are updated. Zabbix appliance images are based on Alpine Linux version 3.4, all other images are based on Alpine Linux 3.9. Docker file sources Everyone can follow Docker file changes using the Zabbix official repository on github.com. You can fork the project or make your own images based on official Docker files. Structure All Zabbix components are available in the following Docker repositories: Zabbix appliance with MySQL database support and Nginx web-server - zabbix/zabbix-appliance Zabbix agent - zabbix/zabbix-agent Zabbix server Zabbix server with MySQL database support - zabbix/zabbix-server-mysql Zabbix server with PostgreSQL database support - zabbix/zabbix-server-pgsql Zabbix web-interface Zabbix web-interface based on Apache2 web server with MySQL database support - zabbix/zabbix-web-apache-mysql Zabbix web-interface based on Apache2 web server with PostgreSQL database support - zabbix/zabbix-web-apache-pgsql Zabbix web-interface based on -

Experimental Methods for the Evaluation of Big Data Systems Abdulqawi Saif
Experimental Methods for the Evaluation of Big Data Systems Abdulqawi Saif To cite this version: Abdulqawi Saif. Experimental Methods for the Evaluation of Big Data Systems. Computer Science [cs]. Université de Lorraine, 2020. English. NNT : 2020LORR0001. tel-02499941 HAL Id: tel-02499941 https://hal.univ-lorraine.fr/tel-02499941 Submitted on 5 Mar 2020 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. AVERTISSEMENT Ce document est le fruit d'un long travail approuvé par le jury de soutenance et mis à disposition de l'ensemble de la communauté universitaire élargie. Il est soumis à la propriété intellectuelle de l'auteur. Ceci implique une obligation de citation et de référencement lors de l’utilisation de ce document. D'autre part, toute contrefaçon, plagiat, reproduction illicite encourt une poursuite pénale. Contact : [email protected] LIENS Code de la Propriété Intellectuelle. articles L 122. 4 Code de la Propriété Intellectuelle. articles L 335.2- L 335.10 http://www.cfcopies.com/V2/leg/leg_droi.php http://www.culture.gouv.fr/culture/infos-pratiques/droits/protection.htm -

Pentest-Report Prometheus 05.-06.2018 Cure53, Dr.-Ing
Dr.-Ing. Mario Heiderich, Cure53 Bielefelder Str. 14 D 10709 Berlin cure53.de · [email protected] Pentest-Report Prometheus 05.-06.2018 Cure53, Dr.-Ing. M. Heiderich, M. Wege, MSc. N. Krein, BSc. J. Hector, Dipl.-Ing. A. Inführ, J. Larsson Index Introduction Scope Test Methodology Part 1 (Manual Code Auditing) Part 2 (Code-Assisted Penetration Testing) Hardening Recommendations General Security Recommendations HTTP Security Headers Content Security Policy & Beyond Authentication / Authorization Non-Idempotent Request Protection Transport Security Clients/metrics endpoint API Endpoint Admin GUI Identified Vulnerabilities PRM-01-001 Web: Prometheus lifecycle killed with CSRF (Medium) PRM-01-003 Web: CORS header exposes API data to all origins (High) PRM-01-005 Server: Clients can cause Denial of Service via Gzip Bomb (Medium) Miscellaneous Issues PRM-01-002 Client: Clients leak Metrics data through unprotected endpoint (Low) PRM-01-004 Web: Parameters used insecurely in HTML templates (Low) Conclusions Cure53, Berlin · 06/11/18 1/18 Dr.-Ing. Mario Heiderich, Cure53 Bielefelder Str. 14 D 10709 Berlin cure53.de · [email protected] Introduction “An open-source monitoring system with a dimensional data model, flexible query language, efficient time series database and modern alerting approach.” From https://prometheus.io/ This report documents the findings of a security assessment targeting the Prometheus software compound and carried out by Cure53 in 2018. It should be noted that the project was sponsored by The Linux Foundation / Cloud Native Computing Foundation. In terms of the scope, the assignment entailed two main components as the Prometheus project was investigated through both a dedicated source code audit and comprehensive penetration testing. -

Mysql Performance Monitoring with Zabbix an Alternative
MySQL Performance Monitoring with Zabbix An alternative to the MySQL Enterprise Monitor? by Oli Sennhauser [email protected] http://www.fromdual.com www.fromdual.com 1 How many of you ... ● ¼ monitor their database servers? ● ¼ monitor their (MySQL) databases? ● ¼ monitor performance metrics? ● ¼ all the others: Why not? www.fromdual.com 2 Linux monitoring ● Question: What is your favourite Linux monitoring application? ● 1187 votes, April 2010 ● Manipulated? ● Lit: Linux Journal, [1] www.fromdual.com 3 What to monitor? ● Devices / Software ● Server, Router, Switches, I/O systems etc. ● Operating System, Networks, Applications, etc. ● Incidents ● DB down, Replication stopped, Server not reachable, etc. ● Critical Events ● Disk more than n% full or less than m Gbyte free, Replication more than n seconds lagging, Data node down, 100% CPU utilization, etc. → Alert, immediate intervention, fire fighting www.fromdual.com 4 What to monitor? ● Trends (includes time!) → Graphs ● How long does it take until ¼ ● ¼ my disk is full? ● ¼ my Index Memory is filled up? ● When does it happen? ● Peak? Backup? ● How often does it happen? Does it happen periodically? ● Once a day? Always at Sunday night? ● How does it correlate to other informations? ● I/O problems during our backup window? ● Reading the patterns! → this can help us to find the root cause of problems¼ www.fromdual.com 5 How to monitor? ● Basic solutions: ● top, vmstat, iostat, mytop, innotop, SHOW GLOBAL STATUS, SHOW INNODB STATUS ● CLI!, no graphs, no log term information, but good for adhoc analysis! ● Graphical solutions ● Nagios, Cactii, Zabbix, ¼ ● Typically NOT specialised in DB monitoring... www.fromdual.com 6 Focus ● Database + Server ● Trends Not the other stuff.. -

Virtualization/Containerization of the PNNL High Energy Physics Computing Infrastructure
Virtualization/Containerization of the PNNL High Energy Physics Computing Infrastructure Kevin Fox, David Cowley, Malachi Schram, Evan Felix, James Czebotar, Smith Gary Grid Services Deployed DIRAC Belle2DB Distributed Data Management REST Service System UI Service Gatekeeper Services Payload Service Many development and testing Squid Cache services Postgresql Relational Database Condor CE's FTS3 DIRAC SiteDirector CVMFS Stratum HTCondor cluster Zero Squid Cache One Leadership Class Facility CE's Authorization DIRAC SiteDirector Gums HPC Cluster VOMS Server with multiple VO's SE's BestMan2 Gridftp Backed by Lustre Note to the Sysadmins New methodology for system administration. Cloud Native focuses around what the user cares about most, not what we Sysadmins are used to caring about. Users care about services. Users do not care about machines providing service. Pets vs Cattle analogy. We must unlearn what we have learned. Try and separate pets and cattle to different pools of resource. Our Infrastructure Journey Individual machines Automated provisioning Virtual machines OpenStack Cloud Repo Mirrors Containers Kubernetes Infrastructure Deployed Kubernetes + Docker Engine Prometheus OpenStack + KVM Grafana Ceph CheckMK GitLab ElasticSearch Lustre 389-DS LoadBalancing/HA Cobbler PerfSonar NFS Metric/Log gathering is very important for system problem analysis Current tool stack includes CheckMK Grafana/Prometheus Kibana/ElasticSearch/LogShippers Kubernetes Load Balancers Give users a load balancer to talk to. Back it with multiple instances of the software making up of the service whenever possible. When not possible, make it very quick to redeploy. Deployment Flow Separate Build and Deploy steps. Kubernetes/Docker example: #Build > docker build . -t pnnlhep/condor-compute:2017-09-01 … > docker push pnnlhep/condor-compute:2017-09-01 … #Deploy > helm install --name ce0-compute condor-compute \ –set version=2017-09-01 .. -
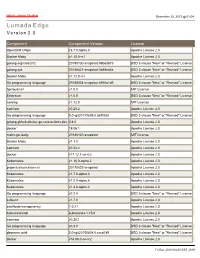
Lumada Edge Version
Hitachi - Inspire The Next December 20, 2019 @ 01:04 Lumada Edge V e r s i o n 3 . 0 Component Component Version License OpenShift Origin v3.7.0-alpha.0 Apache License 2.0 Docker Moby v1.10.0-rc1 Apache License 2.0 golang.org/x/oauth2 20190130-snapshot-99b60b75 BSD 3-clause "New" or "Revised" License golang sys 20180821-snapshot-3b58ed4a BSD 3-clause "New" or "Revised" License Docker Moby v1.12.0-rc1 Apache License 2.0 Go programming language 20180824-snapshot-4910a1d5 BSD 3-clause "New" or "Revised" License hpcloud-tail v1.0.0 MIT License Ethereum v1.5.0 BSD 3-clause "New" or "Revised" License zerolog v1.12.0 MIT License cadvisor v0.28.2 Apache License 2.0 Go programming language 0.0~git20170629.0.5ef0053 BSD 3-clause "New" or "Revised" License golang-github-docker-go-connections-dev 0.4.0 Apache License 2.0 docker 18.06.1 Apache License 2.0 mattn-go-isatty 20180120-snapshot MIT License Docker Moby v1.1.0 Apache License 2.0 cadvisor v0.23.4 Apache License 2.0 docker v17.12.1-ce-rc2 Apache License 2.0 Kubernetes v1.15.0-alpha.2 Apache License 2.0 projectcalico/calico-cni 20170522-snapshot Apache License 2.0 Kubernetes v1.7.0-alpha.3 Apache License 2.0 Kubernetes v1.2.0-alpha.6 Apache License 2.0 Kubernetes v1.4.0-alpha.2 Apache License 2.0 Go programming language v0.2.0 BSD 3-clause "New" or "Revised" License kubevirt v1.7.0 Apache License 2.0 certificate-transparency 1.0.21 Apache License 2.0 kubernetes/api kubernetes-1.15.0 Apache License 2.0 cadvisor v0.28.1 Apache License 2.0 Go programming language v0.3.0 BSD 3-clause "New" or "Revised" -

(PDF) What Can Cloud Native Do for Csps?
What Can Cloud Native Do for CSPs? Cloud Native Can Improve…. Development Cloud native is a way of approaching the development and deployment of applications in such a way that takes account of the characteristics and nature of the cloud—resulting in processes and workflows that fully take advantage of the platform. Operations Cloud native is an approach to building and running software applications that exploits the advantages of the cloud computing delivery model. Cloud-native is about how applications are created and deployed, not where. Infrastructure Cloud native platforms available “as a service” in the cloud can accommodate hybrid and multi-cloud environments. What are Cloud Native Core Concepts? Continuous Integration DevSecOps Microservices Containers and Deployment Not My Problem Release Once Every Tightly Coupled Directly Ported to a VM Separate tools, varied 6 Months Components Monolithic application incentives, opaque process More bugs in production Slow deployment cycles unable to leverage modern waiting on integrated tests cloud tools teams Shared Responsibility Release Early Loosely Coupled Packaged for Containers Common incentives, tools, and Often Components Focus on business process and culture Higher quality of code Automated deploy without software by leveraging waiting on individual the platform ecosystem components What are the Benefits of Cloud Native? Business Optimization Microservices architecture enables flexibility, agility, and reuse across various platforms. CAPEX and OPEX Reduction Service-based architecture allows integration with the public Cloud to handle overload capacity, offer new services with less development, and take advantage of other 3rd party services such as analytics, machine learning, and artificial intelligence. Service Agility Common services can be shared by all network functions deployed on the Cloud-Native Environment (CNE). -

Clúster, Cloud Y Devops
Clúster, Cloud y DevOps Remo Suppi Boldrito PID_00212475 GNUFDL • PID_00212475 Clúster, Cloud y DevOps Índice Introducción .......................................................... 5 Objetivos ............................................................... 8 1. Clusterización ..................................................... 9 1.1. Virtualización ................................................. 9 1.1.1. Plataformas de virtualización ......................... 10 1.2. Beowulf ....................................................... 12 1.2.1. ¿Cómo configurar los nodos? ......................... 14 1.3. Beneficios del cómputo distribuido ........................... 15 1.3.1. ¿Cómo hay que programar para aprovechar la concurrencia? ........................................ 17 1.4. Memoria compartida. Modelos de hilos (threading) ........... 19 1.4.1. Multihilos (multithreading)............................ 19 1.5. OpenMP ...................................................... 23 1.6. MPI, Message Passing Interface ................................. 27 1.6.1. Configuración de un conjunto de máquinas para hacer un clúster adaptado a OpenMPI ................ 28 1.7. Rocks Cluster ................................................. 31 1.7.1. Guía rápida de instalación ............................ 32 1.8. FAI ............................................................ 33 1.8.1. Guía rápida de instalación ............................ 34 1.9. Logs ........................................................... 36 1.9.1. Octopussy ........................................... -

A Complete Introduction to Monitoring Kubernetes with New Relic the Fundamentals You Need to Know to Effectively Monitor Kubernetes Deployments Table of Contents
White Paper A Complete Introduction to Monitoring Kubernetes with New Relic The fundamentals you need to know to effectively monitor Kubernetes deployments Table of Contents Introduction 03 Monitoring Kubernetes with New Relic 04 Getting started 04 Exploring clusters with the Kubernetes cluster explorer 05 Benefits of monitoring with the cluster explorer 06 Kubernetes Observability 07 Visualizing services 07 Monitoring cluster health and capacity 07 Correlating Kubernetes events with cluster health 12 Integrating with APM data 13 Integrating with Prometheus metrics 15 Using Prometheus data in New Relic 15 Monitoring logs in context 16 Investigating end-user experience 17 Scaling Kubernetes with Success: A Real-World Example 18 02 A Complete Introduction to Monitoring Kubernetes with New Relic Introduction Before Kubernetes took over the world, cluster adminis- • Automatic scheduling of pods can cause capacity trators, DevOps engineers, application developers, and issues, especially if you’re not monitoring resource operations teams had to perform many manual tasks availability. in order to schedule, deploy, and manage their contain- erized applications. The rise of the Kubernetes con- In effect, while Kubernetes solves old problems, it can tainer orchestration platform has altered many of these also create new ones. Specifically, adopting containers responsibilities. and container orchestration requires teams to rethink and adapt their monitoring strategies to account for the Kubernetes makes it easy to deploy and operate applica- new infrastructure layers introduced in a distributed tions in a microservice architecture. It does so by creating Kubernetes environment. an abstraction layer on top of a group of hosts, so that development teams can deploy their applications and let With that in mind, we designed this guide to highlight the Kubernetes manage: fundamentals of what you need to know to effectively monitor Kubernetes deployments with New Relic.