The Extended Euclidean Algorithm
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Role of the Interval Domain in Modern Exact Real Airthmetic
The Role of the Interval Domain in Modern Exact Real Airthmetic Andrej Bauer Iztok Kavkler Faculty of Mathematics and Physics University of Ljubljana, Slovenia Domains VIII & Computability over Continuous Data Types Novosibirsk, September 2007 Teaching theoreticians a lesson Recently I have been told by an anonymous referee that “Theoreticians do not like to be taught lessons.” and by a friend that “You should stop competing with programmers.” In defiance of this advice, I shall talk about the lessons I learned, as a theoretician, in programming exact real arithmetic. The spectrum of real number computation slow fast Formally verified, Cauchy sequences iRRAM extracted from streams of signed digits RealLib proofs floating point Moebius transformtions continued fractions Mathematica "theoretical" "practical" I Common features: I Reals are represented by successive approximations. I Approximations may be computed to any desired accuracy. I State of the art, as far as speed is concerned: I iRRAM by Norbert Muller,¨ I RealLib by Branimir Lambov. What makes iRRAM and ReaLib fast? I Reals are represented by sequences of dyadic intervals (endpoints are rationals of the form m/2k). I The approximating sequences need not be nested chains of intervals. I No guarantee on speed of converge, but arbitrarily fast convergence is possible. I Previous approximations are not stored and not reused when the next approximation is computed. I Each next approximation roughly doubles the amount of work done. The theory behind iRRAM and RealLib I Theoretical models used to design iRRAM and RealLib: I Type Two Effectivity I a version of Real RAM machines I Type I representations I The authors explicitly reject domain theory as a suitable computational model. -

Division by Fractions 6.1.1 - 6.1.4
DIVISION BY FRACTIONS 6.1.1 - 6.1.4 Division by fractions introduces three methods to help students understand how dividing by fractions works. In general, think of division for a problem like 8..,.. 2 as, "In 8, how many groups of 2 are there?" Similarly, ½ + ¼ means, "In ½ , how many fourths are there?" For more information, see the Math Notes boxes in Lessons 7.2 .2 and 7 .2 .4 of the Core Connections, Course 1 text. For additional examples and practice, see the Core Connections, Course 1 Checkpoint 8B materials. The first two examples show how to divide fractions using a diagram. Example 1 Use the rectangular model to divide: ½ + ¼ . Step 1: Using the rectangle, we first divide it into 2 equal pieces. Each piece represents ½. Shade ½ of it. - Step 2: Then divide the original rectangle into four equal pieces. Each section represents ¼ . In the shaded section, ½ , there are 2 fourths. 2 Step 3: Write the equation. Example 2 In ¾ , how many ½ s are there? In ¾ there is one full ½ 2 2 I shaded and half of another Thatis,¾+½=? one (that is half of one half). ]_ ..,_ .l 1 .l So. 4 . 2 = 2 Start with ¾ . 3 4 (one and one-half halves) Parent Guide with Extra Practice © 2011, 2013 CPM Educational Program. All rights reserved. 49 Problems Use the rectangular model to divide. .l ...:... J_ 1 ...:... .l 1. ..,_ l 1 . 1 3 . 6 2. 3. 4. 1 4 . 2 5. 2 3 . 9 Answers l. 8 2. 2 3. 4 one thirds rm I I halves - ~I sixths fourths fourths ~I 11 ~'.¿;¡~:;¿~ ffk] 8 sixths 2 three fourths 4. -
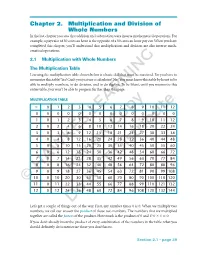
Chapter 2. Multiplication and Division of Whole Numbers in the Last Chapter You Saw That Addition and Subtraction Were Inverse Mathematical Operations
Chapter 2. Multiplication and Division of Whole Numbers In the last chapter you saw that addition and subtraction were inverse mathematical operations. For example, a pay raise of 50 cents an hour is the opposite of a 50 cents an hour pay cut. When you have completed this chapter, you’ll understand that multiplication and division are also inverse math- ematical operations. 2.1 Multiplication with Whole Numbers The Multiplication Table Learning the multiplication table shown below is a basic skill that must be mastered. Do you have to memorize this table? Yes! Can’t you just use a calculator? No! You must know this table by heart to be able to multiply numbers, to do division, and to do algebra. To be blunt, until you memorize this entire table, you won’t be able to progress further than this page. MULTIPLICATION TABLE ϫ 012 345 67 89101112 0 000 000LEARNING 00 000 00 1 012 345 67 89101112 2 024 681012Copy14 16 18 20 22 24 3 036 9121518212427303336 4 0481216 20 24 28 32 36 40 44 48 5051015202530354045505560 6061218243036424854606672Distribute 7071421283542495663707784 8081624324048566472808896 90918273HAWKESReview645546372819099108 10 0 10 20 30 40 50 60 70 80 90 100 110 120 ©11 0 11 22 33 44NOT 55 66 77 88 99 110 121 132 12 0 12 24 36 48 60 72 84 96 108 120 132 144 Do Let’s get a couple of things out of the way. First, any number times 0 is 0. When we multiply two numbers, we call our answer the product of those two numbers. -

The Division Algorithm We All Learned Division with Remainder At
The Division Algorithm We all learned division with remainder at elementary school. Like 14 divided by 3 has reainder 2:14 3 4 2. In general we have the following Division Algorithm. Let n be any integer and d 0 be a positive integer. Then you can divide n by d with remainder. That is n q d r,0 ≤ r d where q and r are uniquely determined. Given n we determine how often d goes evenly into n. Say, if n 16 and d 3 then 3 goes 5 times into 16 but there is a remainder 1 : 16 5 3 1. This works for non-negative numbers. If n −16 then in order to get a positive remainder, we have to go beyond −16 : −16 −63 2. Let a and b be integers. Then we say that b divides a if there is an integer c such that a b c. We write b|a for b divides a Examples: n|0 for every n :0 n 0; in particular 0|0. 1|n for every n : n 1 n Theorem. Let a,b,c be any integers. (a) If a|b, and a|cthena|b c (b) If a|b then a|b c for any c. (c) If a|b and b|c then a|c. (d) If a|b and a|c then a|m b n c for any integers m and n. Proof. For (a) we note that b a s and c a t therefore b c a s a t a s t.Thus a b c. -

Three Methods of Finding Remainder on the Operation of Modular
Zin Mar Win, Khin Mar Cho; International Journal of Advance Research and Development (Volume 5, Issue 5) Available online at: www.ijarnd.com Three methods of finding remainder on the operation of modular exponentiation by using calculator 1Zin Mar Win, 2Khin Mar Cho 1University of Computer Studies, Myitkyina, Myanmar 2University of Computer Studies, Pyay, Myanmar ABSTRACT The primary purpose of this paper is that the contents of the paper were to become a learning aid for the learners. Learning aids enhance one's learning abilities and help to increase one's learning potential. They may include books, diagram, computer, recordings, notes, strategies, or any other appropriate items. In this paper we would review the types of modulo operations and represent the knowledge which we have been known with the easiest ways. The modulo operation is finding of the remainder when dividing. The modulus operator abbreviated “mod” or “%” in many programming languages is useful in a variety of circumstances. It is commonly used to take a randomly generated number and reduce that number to a random number on a smaller range, and it can also quickly tell us if one number is a factor of another. If we wanted to know if a number was odd or even, we could use modulus to quickly tell us by asking for the remainder of the number when divided by 2. Modular exponentiation is a type of exponentiation performed over a modulus. The operation of modular exponentiation calculates the remainder c when an integer b rose to the eth power, bᵉ, is divided by a positive integer m such as c = be mod m [1]. -

Number Theory Learning Module 3 — the Greatest Common Divisor 1
Number Theory Learning Module 3 — The Greatest Common Divisor 1 1 Objectives. • Understand the definition of greatest common divisor (gcd). • Learn the basic the properties of the gcd. • Understand Euclid’s algorithm. • Learn basic proofing techniques for greatest common divisors. 2 The Greatest Common Divisor Classical Greek mathematics concerned itself mostly with geometry. The notion of measurement is fundamental to ge- ometry, and the Greeks were the first to provide a formal foundation for this concept. Surprisingly, however, they never used fractions to express measurements (and never developed an arithmetic of fractions). They expressed geometrical measurements as relations between ratios. In numerical terms, these are statements like: 168 is to 120 as 7 is to 4, (2.1) which we would write today as 168{120 7{5. Statements such as (2.1) were natural to greek mathematicians because they viewed measuring as the process of finding a “common integral measure”. For example, we have: 168 24 ¤ 7 120 24 ¤ 5; so that we can use the integer 24 as a “common unit” to measure the numbers 168 and 120. Going back to our example, notice that 24 is not the only common integral measure for the integers 168 and 120, since we also have, for example, 168 6 ¤ 28 and 120 6 ¤ 20. The number 24, however, is the largest integer that can be used to “measure” both 168 and 120, and gives the representation in lowest terms for their ratio. This motivates the following definition: Definition 2.1. Let a and b be integers that are not both zero. -

1.3 Division of Polynomials; Remainder and Factor Theorems
1-32 CHAPTER 1. POLYNOMIAL AND RATIONAL FUNCTIONS 1.3 Division of Polynomials; Remainder and Factor Theorems Objectives • Perform long division of polynomials • Perform synthetic division of polynomials • Apply remainder and factor theorems In previous courses, you may have learned how to factor polynomials using various techniques. Many of these techniques apply only to special kinds of polynomial expressions. For example, the the previous two sections of this chapter dealt only with polynomials that could easily be factored to find the zeros and x-intercepts. In order to be able to find zeros and x-intercepts of polynomials which cannot readily be factored, we first introduce long division of polynomials. We will then use the long division algorithm to make a general statement about factors of a polynomial. Long division of polynomials Long division of polynomials is similar to long division of numbers. When divid- ing polynomials, we obtain a quotient and a remainder. Just as with numbers, if a remainder is 0, then the divisor is a factor of the dividend. Example 1 Determining Factors by Division Divide to determine whether x − 1 is a factor of x2 − 3x +2. Solution Here x2 − 3x +2is the dividend and x − 1 is the divisor. Step 1 Set up the division as follows: divisor → x − 1 x2−3x+2 ← dividend Step 2 Divide the leading term of the dividend (x2) by the leading term of the divisor (x). The result (x)is the first term of the quotient, as illustrated below. x ← first term of quotient x − 1 x2 −3x+2 1.3. -

Primality Testing for Beginners
STUDENT MATHEMATICAL LIBRARY Volume 70 Primality Testing for Beginners Lasse Rempe-Gillen Rebecca Waldecker http://dx.doi.org/10.1090/stml/070 Primality Testing for Beginners STUDENT MATHEMATICAL LIBRARY Volume 70 Primality Testing for Beginners Lasse Rempe-Gillen Rebecca Waldecker American Mathematical Society Providence, Rhode Island Editorial Board Satyan L. Devadoss John Stillwell Gerald B. Folland (Chair) Serge Tabachnikov The cover illustration is a variant of the Sieve of Eratosthenes (Sec- tion 1.5), showing the integers from 1 to 2704 colored by the number of their prime factors, including repeats. The illustration was created us- ing MATLAB. The back cover shows a phase plot of the Riemann zeta function (see Appendix A), which appears courtesy of Elias Wegert (www.visual.wegert.com). 2010 Mathematics Subject Classification. Primary 11-01, 11-02, 11Axx, 11Y11, 11Y16. For additional information and updates on this book, visit www.ams.org/bookpages/stml-70 Library of Congress Cataloging-in-Publication Data Rempe-Gillen, Lasse, 1978– author. [Primzahltests f¨ur Einsteiger. English] Primality testing for beginners / Lasse Rempe-Gillen, Rebecca Waldecker. pages cm. — (Student mathematical library ; volume 70) Translation of: Primzahltests f¨ur Einsteiger : Zahlentheorie - Algorithmik - Kryptographie. Includes bibliographical references and index. ISBN 978-0-8218-9883-3 (alk. paper) 1. Number theory. I. Waldecker, Rebecca, 1979– author. II. Title. QA241.R45813 2014 512.72—dc23 2013032423 Copying and reprinting. Individual readers of this publication, and nonprofit libraries acting for them, are permitted to make fair use of the material, such as to copy a chapter for use in teaching or research. Permission is granted to quote brief passages from this publication in reviews, provided the customary acknowledgment of the source is given. -

Fast Integer Division – a Differentiated Offering from C2000 Product Family
Application Report SPRACN6–July 2019 Fast Integer Division – A Differentiated Offering From C2000™ Product Family Prasanth Viswanathan Pillai, Himanshu Chaudhary, Aravindhan Karuppiah, Alex Tessarolo ABSTRACT This application report provides an overview of the different division and modulo (remainder) functions and its associated properties. Later, the document describes how the different division functions can be implemented using the C28x ISA and intrinsics supported by the compiler. Contents 1 Introduction ................................................................................................................... 2 2 Different Division Functions ................................................................................................ 2 3 Intrinsic Support Through TI C2000 Compiler ........................................................................... 4 4 Cycle Count................................................................................................................... 6 5 Summary...................................................................................................................... 6 6 References ................................................................................................................... 6 List of Figures 1 Truncated Division Function................................................................................................ 2 2 Floored Division Function................................................................................................... 3 3 Euclidean -

1. the Euclidean Algorithm the Common Divisors of Two Numbers Are the Numbers That Are Divisors of Both of Them
1. The Euclidean Algorithm The common divisors of two numbers are the numbers that are divisors of both of them. For example, the divisors of 12 are 1, 2, 3, 4, 6, 12. The divisors of 18 are 1, 2, 3, 6, 9, 18. Thus, the common divisors of 12 and 18 are 1, 2, 3, 6. The greatest among these is, perhaps unsurprisingly, called the of 12 and 18. The usual mathematical notation for the greatest common divisor of two integers a and b are denoted by (a, b). Hence, (12, 18) = 6. The greatest common divisor is important for many reasons. For example, it can be used to calculate the of two numbers, i.e., the smallest positive integer that is a multiple of these numbers. The least common multiple of the numbers a and b can be calculated as ab . (a, b) For example, the least common multiple of 12 and 18 is 12 · 18 12 · 18 = . (12, 18) 6 Note that, in order to calculate the right-hand side here it would be counter- productive to multiply 12 and 18 together. It is much easier to do the calculation as follows: 12 · 18 12 = = 2 · 18 = 36. 6 6 · 18 That is, the least common multiple of 12 and 18 is 36. It is important to know the least common multiple when adding two fractions. For example, noting that 12 · 3 = 36 and 18 · 2 = 36, we have 5 7 5 · 3 7 · 2 15 14 15 + 14 29 + = + = + = = . 12 18 12 · 3 18 · 2 36 36 36 36 Note that this way of calculating the least common multiple works only for two numbers. -

The Pollard's Rho Method for Factoring Numbers
Foote 1 Corey Foote Dr. Thomas Kent Honors Number Theory Date: 11-30-11 The Pollard’s Rho Method for Factoring Numbers We are all familiar with the concepts of prime and composite numbers. We also know that a number is either prime or a product of primes. The Fundamental Theorem of Arithmetic states that every integer n ≥ 2 is either a prime or a product of primes, and the product is unique apart from the order in which the factors appear (Long, 55). The number 7, for example, is a prime number. It has only two factors, itself and 1. On the other hand 24 has a prime factorization of 2 3 × 3. Because its factors are not just 24 and 1, 24 is considered a composite number. The numbers 7 and 24 are easier to factor than larger numbers. We will look at the Sieve of Eratosthenes, an efficient factoring method for dealing with smaller numbers, followed by Pollard’s rho, a method that allows us how to factor large numbers into their primes. The Sieve of Eratosthenes allows us to find the prime numbers up to and including a particular number, n. First, we find the prime numbers that are less than or equal to √͢. Then we use these primes to see which of the numbers √͢ ≤ n - k, ..., n - 2, n - 1 ≤ n these primes properly divide. The remaining numbers are the prime numbers that are greater than √͢ and less than or equal to n. This method works because these prime numbers clearly cannot have any prime factor less than or equal to √͢, as the number would then be composite. -

RSA and Primality Testing
RSA and Primality Testing Joan Boyar, IMADA, University of Southern Denmark Studieretningsprojekter 2010 1 / 81 Outline Outline Symmetric key ■ Symmetric key cryptography Public key Number theory ■ RSA Public key cryptography RSA Modular ■ exponentiation Introduction to number theory RSA RSA ■ RSA Greatest common divisor Primality testing ■ Modular exponentiation Correctness of RSA Digital signatures ■ Greatest common divisor ■ Primality testing ■ Correctness of RSA ■ Digital signatures with RSA 2 / 81 Caesar cipher Outline Symmetric key Public key Number theory A B C D E F G H I J K L M N O RSA 0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 RSA Modular D E F G H I J K L M N O P Q R exponentiation RSA 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 RSA Greatest common divisor Primality testing P Q R S T U V W X Y Z Æ Ø Å Correctness of RSA Digital signatures 15 16 17 18 19 20 21 22 23 24 25 26 27 28 S T U V W X Y Z Æ Ø Å A B C 18 19 20 21 22 23 24 25 26 27 28 0 1 2 E(m)= m + 3(mod 29) 3 / 81 Symmetric key systems Outline Suppose the following was encrypted using a Caesar cipher and the Symmetric key Public key Danish alphabet. The key is unknown. What does it say? Number theory RSA RSA Modular exponentiation RSA ZQOØQOØ, RI. RSA Greatest common divisor Primality testing Correctness of RSA Digital signatures 4 / 81 Symmetric key systems Outline Suppose the following was encrypted using a Caesar cipher and the Symmetric key Public key Danish alphabet.