Data Source Registration in the Virtual Laboratory
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Steps for Downloading And/Or Installing Java SE 7, the JMF, Apache Tomcat & Eclipse
Steps for Downloading and/or Installing Java SE 7, the JMF, Apache Tomcat & Eclipse Java SE 7 The download instructions below refer to the latest version of the Java Standard Edition (Java SE), which (at the time of writing) is Java SE 7 Update 5. The Java SE Development Kit (JDK) includes the Java Runtime Environment (JRE) and command-line development tools. It is actually the JDK that you are downloading, but we shall be referring only to the Java SE. 1. Go to http://www.oracle.com/technetwork/java/javase/downloads/index.html. 2. Click on the Download button underneath JDK, which is to the right of the text heading showing the latest version of Java. 3. In the table heading halfway down the page, click on the radio button to accept the licence agreement. 4. Click on the filename that appears alongside Windows x86. (This should have the format jdk- 7u<Update version>-windows-i586.exe, where <Update version> is replaced with a number that is either 5 or one slightly higher. 5. Click on the Save button and navigate to a suitable location for the download file (probably the top level of your drive C) and then click the next Save button. (File takes up 87.95MB or more.) 6. After downloading to a suitable location, click on the Open Folder button. 7. Double-click on the executable file that has either been downloaded or been copied from the CD. 8. Click on the Run button. 9. Click on the Next> button (when it becomes available). 10. -

Media Rate Allocation
MEDIA RATE ALLOCATION A PROJECT REPORT Submitted by P.BALASUBRAMANIAN (32205205004) R.VIGNESWARAN (32205205302) in the partial fulfillment for the award of the degree of BACHELOR OF TECHNOLOGY In INFORMATION TECHNOLOGY DHANALAKSHMI SRINIVASAN COLLEGE OF ENGINEERING AND TECHNOLOGY: Mamallapuram ANNA UNIVERSITY: CHENNAI 600025 APRIL 2009 1 ANNA UNIVERSITY: CHENNAI 600 025 BONAFIDE CERTIFICATE Certified that this project report “MEDIA RATE ALLOCATION” is the bonafide work of “P.BALASUBRAMANIAN (32205205004), R.VIGNESWARAN (32205205302)” who carried out the project work under my supervision. SIGNATURE SIGNATURE Ms.D.Jansi Rani Ms.T.Yogeswari HEAD OF THE DEPARTMENT SUPERVISOR Department of Information Technology Department of Information Technology Dhanalakshmi Srinivasan Dhanalakshmi Srinivasan College of Engineering and Technology, College of Engineering and Technology, Mamallapuram. Mamallapuram. Submitted for the project viva voce examination held on ____________ INTERNAL EXAMINER EXTERNAL EXAMINER 2 ACKNOWLEDGEMENT We are glad to take this opportunity to cordially acknowledge a number of people who provide me with great support in these six months. First, we would like to thank Mr.A.Srinivasan, our Chairman who allowed me to do the project in the college campus. We are also thankful to Dr.R.Ponraj M.Tech Ph.D., our Principal, for his constant support in selecting the project. We wish to express my sincere gratitude to our respected Vice Principal, Mr.Pon.Arivanandham M.E, PhD., for his continued encouragement and support. We are grateful to Lecturer Ms.D.Jansi Rani M.Tech., our Head of the Department, who expressed her interest in my work and supplied me with some of her recent works. We would like to thank Lecturer Ms.T.Yogeswari B.E., for following my project with interest and for giving me constant support. -
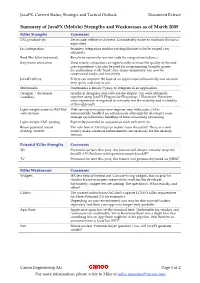
Javafx Strengths and Weaknesses
JavaFX: Current Status; Strategic and Tactical Outlook Document Extract Summary of JavaFX (Mobile) Strengths and Weaknesses as of March 2009 Killer Strengths Comments DSL productivity Terse code; reflective of intent. Considerably easier to maintain than Java equivalent. Java integration Seamless integration enables existing libraries to be leveraged very efficiently. Bind (the killer keyword) Results in extremely succinct code (in comparison to Java.) Key-frame animation Used wisely, animation can significantly increase the quality of the end- user experience. Can also be used for programming (simple) games. In combination with “bind”, key-frame animations can now be constructed easily and intuitively. Java2D effects Effects can improve the look of an application substantially and are now very quick and easy to use. Multimedia Multimedia is finally (!) easy to integrate in an application. Designer / developer Graphical designers and software developers can work efficiently workflow together using JavaFX Plugins for Photoshop / Illustrator. However, more experience is required to seriously test the viability and scalability of this approach. Light-weight access to RESTful Web-service invocation now requires very little code. Call is web services automatically handled asynchronously although the developer must manage asynchronous handling of time-consuming processing. Light-weight XML parsing Especially powerful in conjunction with web-services. Reuse potential across The rule here is: Develop for mobile from the outset! Then, in a new desktop/mobile project, make whatever enhancements are necessary for the desktop version. Potential Killer Strengths Comments 3D Promised for later this year, this feature will almost certainly wrap the Java3D API. But how will it perform under JavaME? TV Promised for later this year, this feature will presumably build on JSR927 Killer Weaknesses Comments Widgets JFX text field of limited use. -

JCP at Javapolis 2007
Javapolis News ❙ 14 December 2007 ❙ Nr 5 ❙ Published by Minoc Business Press 54 www.nonillion.com Parleys Want to become a NONILLIONAIRE ? mail us at : [email protected] Building Rich Internet Applications with Flex and JavaFX “There’s a well thought out com- an online environment using Adobe AIR. “Even when you ponent model for Flex”, he said. are offl ine, you still can update data. When the connec- “And there’s a thriving market tion comes back on, the system synchronizes automati- for components out there, both cally.” Open Source and commercial. So there are literally hundreds JavaPolis founder Stephan Janssen was next to explain of components available to how he decided to have Parleys.com rewritten using Flex. use in Flex.” And no, Flex isn’t Parleys.com offers a massive amount of Java talks – from there for fun and games only. JavaPolis, JavaOne and other Java events from all over “There are already a great the world – combining video images with the actual pres- number of business applica- entation slides of the speakers. Janssen programmed the tions running today, all built application for fun at fi rst, but with over 10 TB of streamed with Flex.” Eckel backed up video in just under a year, it’s clear Parleys.com sort of his statement with an ex- started to lead its own life. “The decision to write a new ample of an interface for an version was made six months ago”, he said. “It was still intranet sales application. too early to use JavaFX. And Silverlight? No thanks.” “Some people think Flex Flex allowed him to leverage the Java code of the earlier isn’t the right choice to version of Parleys.com and to resolve the Web 2.0 and make for business applica- AJAX issues he had en- countered while programming tions, because the render- the fi rst version. -

Using the ELECTRIC VLSI Design System Version 9.07
Using the ELECTRIC VLSI Design System Version 9.07 Steven M. Rubin Author's affiliation: Static Free Software ISBN 0−9727514−3−2 Published by R.L. Ranch Press, 2016. Copyright (c) 2016 Static Free Software Permission is granted to make and distribute verbatim copies of this book provided the copyright notice and this permission notice are preserved on all copies. Permission is granted to copy and distribute modified versions of this book under the conditions for verbatim copying, provided also that they are labeled prominently as modified versions, that the authors' names and title from this version are unchanged (though subtitles and additional authors' names may be added), and that the entire resulting derived work is distributed under the terms of a permission notice identical to this one. Permission is granted to copy and distribute translations of this book into another language, under the above conditions for modified versions. Electric is distributed by Static Free Software (staticfreesoft.com), a division of RuLabinsky Enterprises, Incorporated. Table of Contents Chapter 1: Introduction.....................................................................................................................................1 1−1: Welcome.........................................................................................................................................1 1−2: About Electric.................................................................................................................................2 1−3: Running -

Design of a Distributed Architecture for Enriching Media Experience in Home Theaters
Design of a distributed architecture for enriching media experience in home theaters Citation for published version (APA): Hu, J. (2006). Design of a distributed architecture for enriching media experience in home theaters. Technische Universiteit Eindhoven. https://doi.org/10.6100/IR611954 DOI: 10.6100/IR611954 Document status and date: Published: 01/01/2006 Document Version: Publisher’s PDF, also known as Version of Record (includes final page, issue and volume numbers) Please check the document version of this publication: • A submitted manuscript is the version of the article upon submission and before peer-review. There can be important differences between the submitted version and the official published version of record. People interested in the research are advised to contact the author for the final version of the publication, or visit the DOI to the publisher's website. • The final author version and the galley proof are versions of the publication after peer review. • The final published version features the final layout of the paper including the volume, issue and page numbers. Link to publication General rights Copyright and moral rights for the publications made accessible in the public portal are retained by the authors and/or other copyright owners and it is a condition of accessing publications that users recognise and abide by the legal requirements associated with these rights. • Users may download and print one copy of any publication from the public portal for the purpose of private study or research. • You may not further distribute the material or use it for any profit-making activity or commercial gain • You may freely distribute the URL identifying the publication in the public portal. -

Puneet Lakhina
PUNEET LAKHINA 1. PERSONAL INFORMATION • Address: 182 Kailash Hills,Near East of Kailash, New Delhi – 10065, India • E-Mail: [email protected] • Phone: 00919818069803 2. AREAS OF INTEREST Distributed Systems, Peer to Peer Systems, Software Engineering, Information Retrieval, Computer Networks, Databases. 3. EDUCATION • Bachelor of Technology in Information Technology, Vellore Institute of Technology University, November 2006 CGPA: 9.23 Scale: 10 Rank: 5th (Class Strength: 65) 4. ACADEMIC INTERNSHIPS/FELLOWSHIPS • Position: Project Trainee (January 2006 – May 2006) Institution: Kanwal Rekhi School of Information Technology, Indian Institute Of Technology Bombay Mentor: Dr. Deepak. B. Phatak • Position: Summer Intern (June 2005-August 2005) Institution: Kanwal Rekhi School of Information Technology, Indian Institute Of Technology Bombay Mentor: Dr. Deepak B. Phatak 5. PROFESSIONAL WORK EXPERIENCE • Position: Associate System Engineer (June 2006 – Present) Institution: IBM India Private Limited. 6. PROJECTS • Virtualization: Executed at: IBM India Pvt. Ltd Team Size: 25 Abstract: Virtualization is a SOA based platform, that allows integration of multiple type of bearers (USSD, Web, SMS, IVR, Kiosk etc.) with service platform (network elements) providing scalable, flexible and easily configurable solutions. Virtualization is a key part of the Prepaid transformation that allows IT system to manage the increasing subscriber base (from current 45 million to projected 157 million by 2013) and can be applied for any telecom scenario. My role in the project was to manage the transport layer based on IBM Websphere MQ™ for service request processing. This involved development of a Listener Framework for allowing a business logic plugging without regard to the nature of the transport layer. I was also the lead for load testing and optimization group, whereby the performance target of 43 service requests processing per second was achieved. -

Digital Synthesis by Plug-In Method in Java Media Framework Environment
Proceedings of the COST G-6 Conference on Digital Audio Effects (DAFX-01), Limerick, Ireland, December 6-8, 2001 DIGITAL SYNTHESIS BY PLUG-IN METHOD IN JAVA MEDIA FRAMEWORK ENVIRONMENT Jiri Schimmel Rostislav Fitz Department of Telecommunications Department of Computer Science and Engineering FEECS FEECS Brno University of Technology Brno University of Technology [email protected] [email protected] ABSTRACT JMF requires the appropriate input and output devices such as microphones, cameras, speakers, and monitors. This paper deals with the implementation of real-time digital Data sources and players are integral parts of JMF's high-level musical sound synthesizers by the Plug-In method in the Sun API for managing the capture, presentation, and processing of Microsystems Java Media Framework environment. This time-based media. JMF also provides a lower-level API that environment use the Plug-In technology as well as the DirectX or supports the seamless integration of custom processing VST environments, but the implementation methods are different. components and extensions. This layering provides Java developers with an easy-to-use API for incorporating time-based media into Java programs while maintaining the flexibility and extensibility required supporting advanced media applications 1. JAVA MEDIA FRAMEWORK and future media technologies. Java is object-oriented multi-platform programming language developed by the Sun Microsystems company that is used mainly for Internet applet production. The Java Media Framework (JMF) is an application programming interface (API) for incorporating time-based media into Java applications and applets. The JMF 1.0 API (the Java Media Player API) enabled programmers to develop Java programs that presented time-based media. -

Java Core Technologies (Part III)
Extreme Java G22.3033-007 Session 5 - Main Theme Java Core Technologies (Part III) Dr. Jean-Claude Franchitti New York University Computer Science Department Courant Institute of Mathematical Sciences 1 Agenda • Summary of Previous Session / Epilogue • Java Media APIs •Java 2D API • Java Media Framework • XBeans and Visual XBeans •JNI • Java Generative Programming Technology • Language Features •Threads • Readings 2 1 Summary of Previous Session • Summary of Previous Session • Java AWT and Swing components • Drag and Drop • Graphics and Multimedia Components (JavaMedia) • JavaBeans • Readings • Class Project & Assignment #2b 3 Java Technologies/Features in Scope • Technologies: • Collections Framework • Input Method Framework • Swing • Drag and Drop • JavaBeans •JNI • Security • Language Features: • Threads • Assertions 4 2 Part I Session 4 Epilogue 5 Drag and Drop (http://java.sun.com/j2se/1.4/docs/guide/swing/1.4/dnd.html) • See Session 4 Handout on Drag and Drop Data Transfer • Adding Drag and Drop to a JTree • In J2SE 1.4, JTree supports Drag but developers must implement and install a custom TransferHandler to fully support imports of data on Drop targets • http://www.javaworld.com/javaworld/javatips/jw-javatip97.html • http://www.javaworld.com/javaworld/javatips/jw-javatip114.html • http://sourceforge.net/projects/ijtree/ 6 3 JavaBeans and JAF (http://java.sun.com/j2se/1.4/docs/guide/beans/changes14.html) • See Session 4 Handout on Component Modeling with JavaBeans • Download the BeanBuilder • http://java.sun.com/products/javabeans/beanbuilder/index.html -

The Java Tree Withers
IN DEVELOPMENT The Java Tree Withers Doug Lyon Fairfield University, Fairfield, Connecticut The Java report card: infrastructure gets a D, code reuse gets an F. omputer languages are PREDICTION IS HARD, neglect and deprecation. Deprecation uniquely positioned ESPECIALLY WHEN IT’S warnings aren’t generally deemed as a case study in the ABOUT THE FUTURE serious, as programs continue to run. C development of man’s If we establish a good reason for However, sometimes entire JVMs are most complex and powerful techno Java’s ascendancy, perhaps we can deprecated. The biggest threat to artifact—the programming language. come up with a prognosis for its Java is Apple’s banning of Java on the The most popular of these languages future. iPhone and the deprecation of the new is now Java. One of Java’s key strengths is its JVM on the Mac OS. In 15 years, my Java project portability. The Java virtual machine Java provides a way to isolate has grown from 667 lines of code (JVM) is a high-performance, portable, and manage API instability using (LOC) to 633,436 LOC. During this and successful substrate. However, JavaBeans. The bean embodies the time, I’ve had to struggle to keep up the tectonic shift in Java ownership promise of Java code-reuse via inter- with API deprecations and defunct (from Sun to Oracle) has caused changeable parts—known as com- frameworks. Some code will no longer aftershocks, destabilizing Java ponent software development (CSD). run. What will become of Java? APIs. This has been exacerbated by Historically, the technology of interchangeable parts enabled an industrial revolution—among other things, it helped the Springfield Armory produce more than 1 million model 1861 rifles during the Civil War. -

Computer Vision Processing Using Webcams with Java in Eclipse 3
Software Installation Guide for L2Bot * Jan 21, 2011 (*) This Guide has been tested under Windows XP and Windows 7 1. Webcam driver 2. JMF 2.1.1.1.e 3. Eclipse setup for Webcam 4. Java comm API 5. Configure Eclipse for comm API 6. Let’s drive L2Bot! 0. Install JDK (Java Development Kit) and Eclipse Check if you are using a 64-bit Operating System. (Right click “Computer” on the desktop and slect property to get the information.) L2Bot requires 32 bit software. Download the newest version of 32 bit JDK (Java Development Kit) from: http://www.oracle.com/technetwork/java/javase/downloads Note that 32 bit system is also called x86. If you already have 64 bit JDK version, it is fine to have 32 bit JRE (Java Runtime Environment) in addition on your computer. By default, it will be installed under c:\Program Files (x86)\Java. Download the newest version of the Eclipse IDE (either for Developers or Classic) from http://www.eclipse.org/downloads You do not need to install 32 bit Eclipse, when you have 64 bit OS. Find the downloaded Eclipse zip file, and extract it to a location. Inside the extracted Eclipse folder, you should find the Eclipse application. You may want to make a shortcut of this onto your desktop. At least “Hello World” program using Eclipse must be tested before beginning the following installations. 1. Webcam driver installation If your laptop has built in webcam, then skip this section 1. Usually the driver is already installed. Any webcams (or camcorders) can be used for the L2Bot. -

Learning Java an Introduction to Real-World Programming with Java
EditionFifth Learning Java An Introduction to Real-World Programming with Java Marc Loy, Patrick Niemeyer & Daniel Leuck FIFTH EDITION Learning Java An Introduction to Real-World Programming with Java Marc Loy, Patrick Niemeyer, and Daniel Leuck Beijing Boston Farnham Sebastopol Tokyo Learning Java by Marc Loy, Patrick Niemeyer, and Daniel Leuck Copyright © 2020 Marc Loy, Patrick Niemeyer, Daniel Leuck. All rights reserved. Printed in the United States of America. Published by O’Reilly Media, Inc., 1005 Gravenstein Highway North, Sebastopol, CA 95472. O’Reilly books may be purchased for educational, business, or sales promotional use. Online editions are also available for most titles (http://oreilly.com). For more information, contact our corporate/institutional sales department: 800-998-9938 or [email protected]. Acquisitions Editor: Suzanne McQuade Indexer: Angela Howard Developmental Editor: Amelia Blevins Interior Designer: David Futato Production Editor: Beth Kelly Cover Designer: Karen Montgomery Copyeditor: Sonia Saruba Illustrator: Rebecca Demarest Proofreader: Christina Edwards May 2000: First Edition July 2002: Second Edition May 2005: Third Edition June 2013: Fourth Edition March 2020: Fifth Edition Revision History for the Fifth Edition 2020-03-27: First Release See http://oreilly.com/catalog/errata.csp?isbn=9781492056270 for release details. The O’Reilly logo is a registered trademark of O’Reilly Media, Inc. Learning Java, the cover image, and related trade dress are trademarks of O’Reilly Media, Inc. While the publisher and the authors have used good faith efforts to ensure that the information and instructions contained in this work are accurate, the publisher and the authors disclaim all responsibility for errors or omissions, including without limitation responsibility for damages resulting from the use of or reliance on this work.