US20100040231A1.Pdf
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

(12) United States Patent (10) Patent No.: US 8.422,684 B2 Jin Et Al
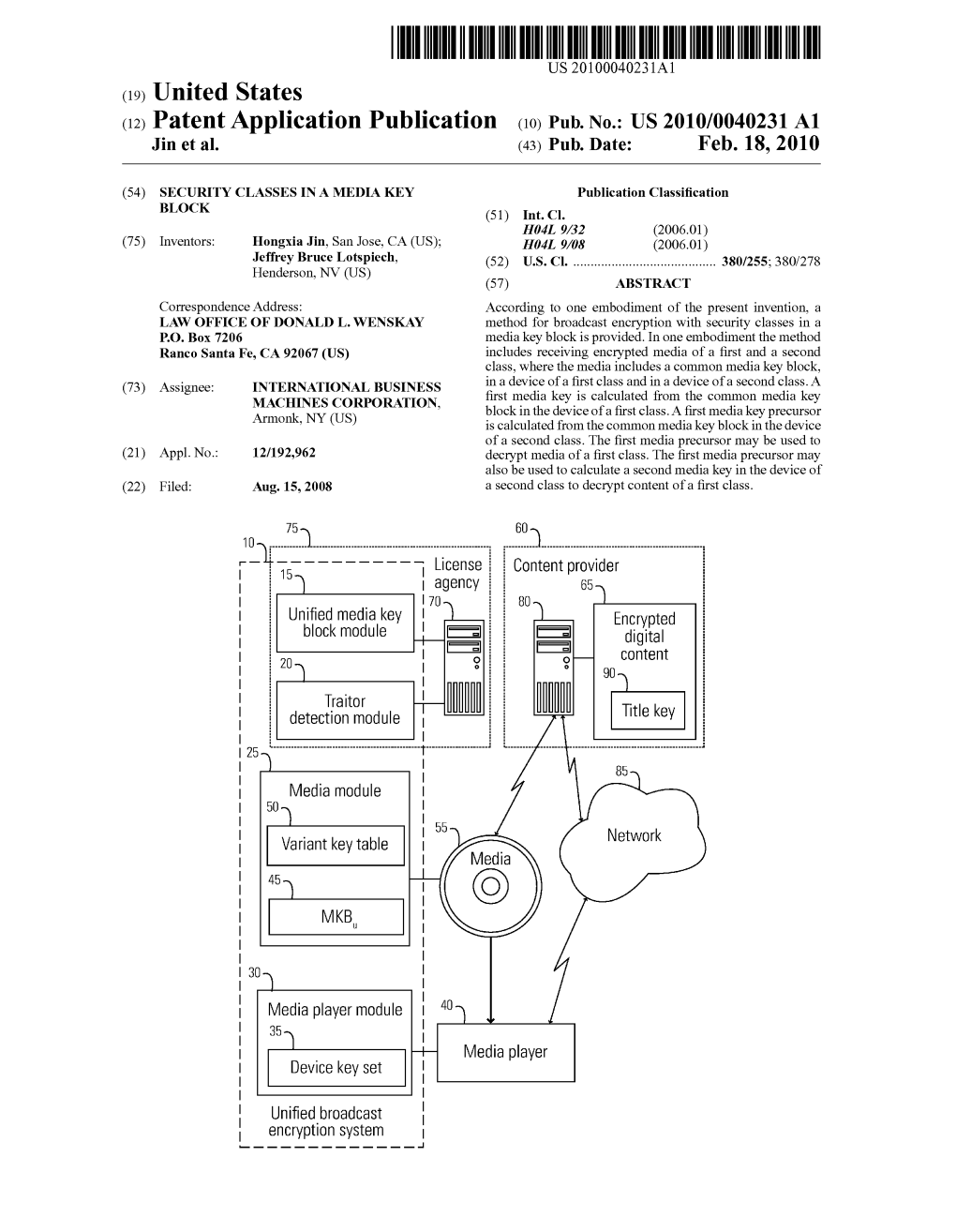
USOO8422684B2 (12) United States Patent (10) Patent No.: US 8.422,684 B2 Jin et al. (45) Date of Patent: Apr. 16, 2013 (54) SECURITY CLASSES IN A MEDIA KEY 5,345,505 A 9, 1994 Pires BLOCK 5,412,723 A 5/1995 Canetti et al. 5,592,552 A 1, 1997 Fiat (75) Inventors: Hongxia Jin, San Jose, CA (US); 2. A 8. E" al. Jeffrey Bruce Lotspiech, Henderson, 5,651,064 A 7, 1997 Newell NV (US) 5,668,873. A 9, 1997 Yamauchi 5,680,457 A 10, 1997 Bestler et al. (73) Assignee: International Business Machines (Continued) Corporation, Armonk, NY (US) FOREIGN PATENT DOCUMENTS (*) Notice: Subject to any disclaimer, the term of this WO WO99, 19822 4f1999 patent is extended or adjusted under 35 WO WOOOf 48190 8, 2000 U.S.C. 154(b) by 892 days. WO WOO1/22406 3, 2001 (21) Appl. No.: 12/192,962 OTHER PUBLICATIONS U.S. Appl.pp No. 12/131,073, filed Mayy 31, 2008, Bellwood et al. (22) Filed: Aug. 15, 2008 U.S. Appl. No. 12/131,074, filed May 31, 2008, Lotspiech. (65) Prior Publication Data (Continued) US 201O/OO4O231 A1 Feb. 18, 2010 Primary Examiner — Jung Kim Assistant Examiner — Thomas Ho (51) Int. Cl (74) Attorney, Agent, or Firm — Donald L. Wenskay; H04L 9/00 (2006.01) Moh ed Kashef (52) U.S. Cl USPC ............................................. 380/277; 380/45 (57) ABSTRACT (58) Field of Classification Search .................. 380/277,38O/45 According to one embodiment of the present invention, a See application file for complete search histo method for broadcast encryption with security classes in a pp p ry. -

Copy Protection
Content Protection / DRM Content Protection / Digital Rights Management Douglas Dixon November 2006 Manifest Technology® LLC www.manifest-tech.com 11/2006 Copyright 2005-2006 Douglas Dixon, All Rights Reserved – www.manifest-tech.com Page 1 Content Protection / DRM Content Goes Digital Analog -> Digital for Content Owners • Digital Threat – No impediment to casual copying – Perfect digital copies – Instant copies – Worldwide distribution over Internet – And now High-Def content … • Digital Promise – Can protect – Encrypt content – Associate rights – Control usage 11/2006 Copyright 2005-2006 Douglas Dixon, All Rights Reserved – www.manifest-tech.com Page 2 1 Content Protection / DRM Conflict: Open vs. Controlled Managed Content • Avoid Morality: Applications & Technology – How DRM is impacting consumer use of media – Awareness, Implications • Consumers: “Bits want to be free” – Enjoy purchased content: Any time, anywhere, anyhow – Fair Use: Academic, educational, personal • Content owners: “Protect artist copyrights” – RIAA / MPAA : Rampant piracy (physical and electronic) – BSA: Software piracy, shareware – Inhibit indiscriminate casual copying: “Speed bump” • “Copy protection” -> “Content management” (DRM) 11/2006 Copyright 2005-2006 Douglas Dixon, All Rights Reserved – www.manifest-tech.com Page 3 Content Protection / DRM Content Protection / DRM How DRM is being applied • Consumer Scenarios: Impact of DRM – Music CD Playback on PC – Archive Digital Music – Play and Record DVDs – Record and Edit Personal Content • Industry Model: Content -
![(12) United States Patent (10) Patent N0.: US 7,882,367 B2 Tachikawa Et A]](https://docslib.b-cdn.net/cover/3775/12-united-states-patent-10-patent-n0-us-7-882-367-b2-tachikawa-et-a-1303775.webp)
(12) United States Patent (10) Patent N0.: US 7,882,367 B2 Tachikawa Et A]
US007882367B2 (12) United States Patent (10) Patent N0.: US 7,882,367 B2 Tachikawa et a]. (45) Date of Patent: Feb. 1, 2011 (54) INFORMATION RECORDING AND 2005/0016284 A1 1/2005 Bernhard REPRODUCING APPARATUS AND METHOD 2005/0038997 A1 2/2005 Kojima et a1. 2008/0154633 A1* 6/2008 Ishibashi et a1. ............. .. 705/1 (75) Inventors: Takayuki TachikaWa, Hamura (JP); 2009/0222929 A1* 9/2009 Noguchi et a1. ............. .. 726/27 Hiroyuki Kamio, TachikaWa (JP) FOREIGN PATENT DOCUMENTS EP 1 659 584 A1 5/2006 (73) Assignee: Kabushiki Kaisha Toshiba, Tokyo (JP) JP 2005-039480 2/2005 WO 03/049106 A2 6/2003 ( * ) Notice: Subject to any disclaimer, the term of this WO 2006/074987 A2 7/2006 patent is extended or adjusted under 35 U.S.C. 154(b) by 914 days. OTHER PUBLICATIONS Intel Corporation et al., “Advanced Access Content System (AACS) (21) App1.N0.: 11/806,602 Recordable J/ldeo Book”, Feb. 17, 2006, Revision 0.91, pp. 1-13. Intel Corporation et al., “Advanced Access Content System (AACS) (22) Filed: Jun. 1, 2007 HD DVD Recordable Book”, Apr. 26, 2006, Revision 0.92, pp. 1-57. European Search Report corresponding to Application No. EP 07 10 (65) Prior Publication Data 7517 dated Sep. 18,2007. US 2008/0002828 A1 Jan. 3, 2008 * cited by examiner Primary ExamineriChristopher A Revak (30) Foreign Application Priority Data (74) Attorney, Agent, or FirmiPillsbury Winthrop ShaW Jun. 12, 2006 (JP) ........................... .. 2006-162669 Pittman, LLP (51) Int. Cl. (57) ABSTRACT H04L 9/14 (2006.01) According to one embodiment of the invention, there is pro H04L 9/30 (2006.01) vided an information recording and reproducing apparatus (52) US. -

Advanced Access Content System (AACS)
Advanced Access Content System: Blu-ray Disc Recordable Book Advanced Access Content System (AACS) Blu-ray Disc Recordable Book Intel Corporation International Business Machines Corporation Matsushita Electric Industrial Co., Ltd. Microsoft Corporation Sony Corporation Toshiba Corporation The Walt Disney Company Warner Bros. Revision 0.921 August 5, 2008 Revision 0.921 Page 1 Advanced Access Content System: Blu-ray Disc Recordable Book This page is intentionally left blank. Page 2 Revision 0.921 Advanced Access Content System: Blu-ray Disc Recordable Book Preface Notice THIS DOCUMENT IS PROVIDED "AS IS" WITH NO WARRANTIES WHATSOEVER, INCLUDING ANY WARRANTY OF MERCHANTABILITY, NONINFRINGEMENT, FITNESS FOR ANY PARTICULAR PURPOSE, OR ANY WARRANTY OTHERWISE ARISING OUT OF ANY PROPOSAL, SPECIFICATION OR SAMPLE. IBM, Intel, Matsushita Electric Industrial Co., Ltd., Microsoft Corporation, Sony Corporation, Toshiba Corporation, The Walt Disney Company and Warner Bros. disclaim all liability, including liability for infringement of any proprietary rights, relating to use of information in this specification. No license, express or implied, by estoppel or otherwise, to any intellectual property rights are granted herein. This document is subject to change under applicable license provisions. Copyright © 2005-2008 by Intel Corporation, International Business Machines Corporation, Matsushita Electric Industrial Co., Ltd., Microsoft Corporation, Sony Corporation, Toshiba Corporation, The Walt Disney Company, and Warner Bros. Third-party brands and names are the property of their respective owners. Intellectual Property Implementation of this specification requires a license from AACS LA LLC. Contact Information Please address inquiries, feedback, and licensing requests to AACS LA LLC: • Licensing inquiries and requests should be addressed to [email protected]. -

Content Protection for Recordable Media Specification SD Memory
Content Protection for Recordable Media Specification SD Memory Card Book SD- Video Part Intel Corporation International Business Machines Corporation Mutsushita Electric Industrial Co., Ltd. Toshiba Corporation Revision 0.9 March 24,2003 CPRM Specification: SD Memory Card Book SD-Video Part, Revision 0.9 This page is intentionally left blank. Page ii 4C Entity, LLC CPRM Specification: SD Memory Card Book SD-Video Part, Revision 0.9 Preface Notice THIS DOCUMENT IS PROVIDED "AS IS" WITH NO WARRANTIES WHATSOEVER, INCLUDING ANY WARRANTY OF MERCHANTABILITY, NONINFRINGEMENT, FITNESS FOR ANY PARTICULAR PURPOSE, OR ANY WARRANTY OTHERWISE ARISING OUT OF ANY PROPOSAL, SPECIFICATION OR SAMPLE. IBM, Intel, MEI, and Toshiba disclaim all liability, including liability for infringement of any proprietary rights, relating to use of information in this specification. No license, express or implied, by estoppel or otherwise, to any intellectual property rights are granted herein. This document is an intermediate draft and is subject to change without notice. Adopters and other users of this specification are cautioned that products based on it may not be interoperable with the final version or subsequent versions thereof. Copyright 0 1999-2003 by International Business Machines Corporation, Intel Corporation, Matsushita Electric Industrial Co., Ltd., and Toshiba Corporation. Third-party brands and names are the property of their respective owners. Intellectual Property Implementation of this specification requires a license from the 4C Entity, LLC. Contact Information Please address inquiries, feedback, and licensing requests to the 4C Entity, LLC: Licensing inquiries and requests should be addressed to c~rm-licensin~@4Centit~.com. Feedback on this specification should be addressed to c~rm-comment@,4Centitv.com. -

Broadcast Encryption for Differently Privileged
Broadcast Encryption for Differently Privileged Hongxia Jin1 and Jeffery Lotspiech2 1 IBM Almaden Research Center San Jose, CA, 95120 [email protected] 2 Lotspiech.com, Henderson, Nevada [email protected] Abstract. Broadcast encryption is a primary technology that has been used for content protection. It enables a broadcaster to distribute content to a set of users so that only a privileged subset of users can access the content and another subset of revoked users cannot access the content. The main enabling block in a broadcast encryption scheme is the session key block, which each authorized user processes differently, but each gets the same valid session key. Currently all existing broad- cast encryption schemes have assumed that the content and authorized users are equally privileged. There are emerging scenarios that demand protection for con- tent with different privileges and for users with different privileges. In this paper we shall present a new broadcast encryption scheme that continues to employ single session key blocks but provides different privileged protections for differ- ent content and users. In particular we will expand the elegant subset-cover-based broadcast encryption scheme. We shall introduce a new concept called “security class” into the session key blocks. We use keys derived from a chain of one-way functions. Our approach is simple, efficient and secure. 1 Introduction This paper is concerned with protection of copyrighted digital content. Piracy is becom- ing a more and more serious concern in the movie and music industries, since digital copies are perfect copies. Broadcast encryption is an important cryptographic key man- agement approach, especially useful in content protection systems. -

Advanced Access Content System (AACS) Recordable Video Book
Advanced Access Content System (AACS) Recordable Video Book Intel Corporation International Business Machines Corporation Microsoft Corporation Panasonic Corporation Sony Corporation Toshiba Corporation The Walt Disney Company Warner Bros. Final Revision 0.953 Final October 26, 2012 Advanced Access Content System: Recordable Video Book This page is intentionally left blank. Final Revision 0.953 Page ii Advanced Access Content System: Recordable Video Book Preface Notice THIS DOCUMENT IS PROVIDED "AS IS" WITH NO WARRANTIES WHATSOEVER, INCLUDING ANY WARRANTY OF MERCHANTABILITY, NONINFRINGEMENT, FITNESS FOR ANY PARTICULAR PURPOSE, OR ANY WARRANTY OTHERWISE ARISING OUT OF ANY PROPOSAL, SPECIFICATION OR SAMPLE. Intel Corporation, International Business Machines Corporation, Microsoft Corporation, Panasonic Corporation, Sony Corporation, Toshiba Corporation, The Walt Disney Company and Warner Bros. disclaim all liability, including liability for infringement of any proprietary rights, relating to use of information in this specification. No license, express or implied, by estoppel or otherwise, to any intellectual property rights are granted herein. This document is subject to change under applicable license provisions. Copyright © 2005-2012 by Intel Corporation, International Business Machines Corporation, Microsoft Corporation, Panasonic Corporation, Sony Corporation, Toshiba Corporation, The Walt Disney Company and Warner Bros. Third-party brands and names are the property of their respective owners. Intellectual Property Implementation of this specification requires a license from AACS LA LLC. Contact Information Please address inquiries, feedback, and licensing requests to AACS LA LLC: Licensing inquiries and requests should be addressed to [email protected]. Feedback on this specification should be addressed to [email protected]. The URL for the AACS LA LLC web site is http://www.aacsla.com. -

Cryptography and DRM Martin Persson & Alexander Nordfelth
Cryptography and DRM Martin Persson & Alexander Nordfelth Cryptography, spring 2008 Uppsala Universitet Table of contents: Introduction 2 Brief History 2 How it is used 3 CSS (Content Scrambling System) 4 AACS (Advanced Access Content System) 4 Fairplay 6 Windows Vista DRM 8 Conclusions 9 1 Introduction The concept of Digital Rights Management is a broad one. It encompasses business models, national and international laws and technology. For us to be able to look at DRM in a fairly short amount of pages we need to limit ourselves. Following a brief historic overview, we will strictly look at the technical side of DRM. We will delve into a few common areas where DRM is implemented today and we will look at what algorithms and structures that are used. We will also look at a few cases when DRM has been broken and what methods the attackers have employed. Brief History For as long as there has been physical media, there has been attempts to acquire said media illegally. Copyright holders have become increasingly concerned with this theft over the past decades as the means to make copies of the media has become increasingly easy. In the past, the quality of the physical media, deteriorated with each copy being made and the "pirate" was only able to produce a finite amount of copies. Today copyright holders face the threat of a single "pirate" being able to make an infinite number of perfect copies with little or no effort. Adding to this, the ease of sharing content through broadband-internet connections, the need for a sophisticated content protection system has become obvious. -

Before the Federal Communications Commission Washington, DC 20554
Before the Federal Communications Commission Washington, DC 20554 In the matter of: ) ) Closed Captioning of Internet Protocol- ) MB Docket No. 11-154 Delivered Video Programming: Implementation ) Of the Twenty-First Century Communications ) And Video Accessibility Act of 2010 ) Comments of the Advanced Access Content System Licensing Administrator, LLC Bruce H. Turnbull Counsel and Co-Manager, AACS LA, LLC Turnbull Law Firm, PLLC 5335 Wisconsin Avenue, NW Washington, DC 20015 (202) 274-1801 [email protected] Donald Leake, Jr. Co-Manager AACS LA, LLC 3855 SW 153rd Drive Beaverton, OR 97006 November 4, 2013 These comments are submitted by Advanced Access Content System Licensing Administrator, LLC (“AACS LA”) in relation to the Further Notice of Proposed Rulemaking, 78 Fed. Reg. 39691 (July 2, 2013). In these comments, AACS LA brings to the Commission’s attention the reasons why analog outputs for AACS-protected motion picture content on prerecorded Blu-ray Discs are scheduled to “sunset” for Blu-ray Disc players (“BD players”) that are distributed after December 31, 2013 and why requiring analog outputs for BD players is neither necessary nor desirable. By way of background, AACS LA is a limited liability company established by eight companies (IBM, Intel, Microsoft, Panasonic, Sony, Walt Disney, Toshiba, and Warner Bros.) from three different industries – motion picture content providers, consumer electronics, and information technology – to develop and license content protection technology to protect high definition motion picture content from unauthorized reproduction and distribution. AACS LA’s technology has been applied to prerecorded Blu-ray Discs distributed in the United States and around the world since February 2006. -

Blu-Ray Disc Recordable Book
Advanced Access Content System (AACS) Blu-ray Disc Recordable Book Intel Corporation International Business Machines Corporation Microsoft Corporation Panasonic Corporation Sony Corporation Toshiba Corporation The Walt Disney Company Warner Bros. Revision 0.953 Final October 26, 2012 Advanced Access Content System: Blu-ray Disc Recordable Book This page is intentionally left blank. Page ii Final Revision 0.953 Advanced Access Content System: Blu-ray Disc Recordable Book Preface Notice THIS DOCUMENT IS PROVIDED "AS IS" WITH NO WARRANTIES WHATSOEVER, INCLUDING ANY WARRANTY OF MERCHANTABILITY, NONINFRINGEMENT, FITNESS FOR ANY PARTICULAR PURPOSE, OR ANY WARRANTY OTHERWISE ARISING OUT OF ANY PROPOSAL, SPECIFICATION OR SAMPLE. IBM, Intel, Microsoft Corporation, Panasonic Corporation, Sony Corporation, Toshiba Corporation, The Walt Disney Company and Warner Bros. disclaim all liability, including liability for infringement of any proprietary rights, relating to use of information in this specification. No license, express or implied, by estoppel or otherwise, to any intellectual property rights are granted herein. This document is subject to change under applicable license provisions. Copyright © 2005-2012 by Intel Corporation, International Business Machines Corporation, Microsoft Corporation, Panasonic Corporation, Sony Corporation, Toshiba Corporation, The Walt Disney Company, and Warner Bros. Third-party brands and names are the property of their respective owners. Intellectual Property Implementation of this specification requires a license from AACS LA LLC. Contact Information Please address inquiries, feedback, and licensing requests to AACS LA LLC: Licensing inquiries and requests should be addressed to [email protected]. Feedback on this specification should be addressed to [email protected]. The URL for the AACS LA LLC web site is http://www.aacsla.com. -

Advanced Access Content System (AACS) Introduction and Common
Advanced Access Content System (AACS) Introduction and Common Cryptographic Elements Book Intel Corporation International Business Machines Corporation Microsoft Corporation Panasonic Corporation Sony Corporation Toshiba Corporation The Walt Disney Company Warner Bros. Revision 0.951 Final September 28, 2009 Advanced Access Content System: Introduction and Common Cryptographic Elements This page is intentionally left blank. Final Revision 0.951 Page ii Advanced Access Content System: Introduction and Common Cryptographic Elements Preface Notice THIS DOCUMENT IS PROVIDED "AS IS" WITH NO WARRANTIES WHATSOEVER, INCLUDING ANY WARRANTY OF MERCHANTABILITY, NONINFRINGEMENT, FITNESS FOR ANY PARTICULAR PURPOSE, OR ANY WARRANTY OTHERWISE ARISING OUT OF ANY PROPOSAL, SPECIFICATION OR SAMPLE. IBM, Intel, Microsoft Corporation, Panasonic Corporation, Sony Corporation, Toshiba Corporation, The Walt Disney Company and Warner Bros. disclaim all liability, including liability for infringement of any proprietary rights, relating to use of information in this specification. No license, express or implied, by estoppel or otherwise, to any intellectual property rights are granted herein. This document is subject to change under applicable license provisions. Copyright © 2005-2009 by Intel Corporation, International Business Machines Corporation, Microsoft Corporation, Panasonic Corporation, Sony Corporation, Toshiba Corporation, The Walt Disney Company, and Warner Bros. Third-party brands and names are the property of their respective owners. Intellectual Property Implementation of this specification requires a license from AACS LA LLC. Contact Information Please address inquiries, feedback, and licensing requests to AACS LA LLC: • Licensing inquiries and requests should be addressed to [email protected]. • Feedback on this specification should be addressed to [email protected]. The URL for the AACS LA LLC web site is http://www.aacsla.com. -

An Overview of the Advanced Access Content System (AACS)
An Overview of the Advanced Access Content System (AACS) Kevin Henry, Jiayuan Sui, Ge Zhong David R. Cheriton School of Computer Science University of Waterloo Waterloo, ON, N2L 3G1, Canada {k2henry, jsui, gzhong}@cs.uwaterloo.ca Abstract The Advanced Access Content System (AACS) is a content distribution system for record- able and pre-recorded media, currently used to protect HD-DVD and Blu-Ray content. AACS builds off of its predecessors, the Content Scramble System (CSS) and Content Protection for Pre-recorded/Recordable media (CPRM/CPPM), adding more robust key distribution and re- vocation capabilities. In this paper, a concise summary of the lengthy AACS specification for pre-recorded media is provided, with emphasis on how the AACS keys are organized, distributed, and revoked using subset difference trees. A description of the AACS mechanisms for recordable content and on-line content is also provided. 1 Introduction The Advanced Access Content System (AACS) is a content distribution system for recordable and pre-recorded media. Most notably, the AACS is used to protect high definition video content on Blu- Ray and HD-DVD discs. The current AACS technical specifications span nearly 550 pages spread across seven documents [3-9], and provide an overview of the system, as well as specific implemen- tations for pre-recorded and recordable media for both Blu-Ray and HD-DVD formats. The goal of this paper is to provide a concise summary of the information contained within these specifications, with extra attention given to the broadcast encryption scheme used. Over the entire specification, only two or three pages are dedicated to how a device’s cryptographic keys are distributed and revoked, however this mechanism, described in Section 2.3, is the core upon which the rest of the system is built.