Can Compression Reduce Forensic Image Time?
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Optimizing and Protecting Hard Drives ‐ Chapter # 9
Optimizing and Protecting Hard Drives ‐ Chapter # 9 Amy Hissom Key Terms antivirus (AV) software — Utility programs that prevent infection or scan a system to detect and remove viruses. McAfee Associates’ VirusScan and Norton AntiVirus are two popular AV packages. backup — An extra copy of a file, used in the event that the original becomes damaged or destroyed. boot sector virus — An infectious program that can replace the boot program with a modified, infected version of the boot command utilities, often causing boot and data retrieval problems. buffer — A temporary memory area where data is kept before being written to a hard drive or sent to a printer, thus reducing the number of writes to the devices. chain — A group of clusters used to hold a single file. child, parent, grandparent backup method — A plan for backing up and reusing tapes or removable disks by rotating them each day (child), week (parent), and month (grandparent). cross-linked clusters — Errors caused when more than one file points to a cluster, and the files appear to share the same disk space, according to the file allocation table. defragment — To “optimize” or rewrite a file to a disk in one contiguous chain of clusters, thus speeding up data retrieval. differential backup — Backup method that backs up only files that have changed or have been created since the last full backup. When recovering data, only two backups are needed: the full backup and the last differential backup. disk cache — A method whereby recently retrieved data and adjacent data are read into memory in advance, anticipating the next CPU request. -

Lab 13A: Configuring Disk Compression
Lab 13A: Configuring Disk Compression Objectives After completing this lab, you will be able to: !" Configure an NTFS volume for compression. !" Move files with the compression attribute set. !" Copy files with the compression attribute set. Prerequisites Before working on this lab, you must have: !" Knowledge of the NTFS file system. !" Knowledge of file compression. Estimated time to complete this lab: 15 minutes 2 Lab 13A: Configuring Disk Compression Exercise 1 Configuring Disk Compression In this exercise, you will enable disk compression and view the effects of compression on the Documents and Settings folder and subfolders. Scenario To provide the maximum storage capacity for your client computers, the IT manager has decided that NTFS disk compression will be enabled for folders on client computers that are low on disk space. You have been tasked with enabling disk compression for specified folders on your client computers. Tasks Detailed steps 1. Log on as Administrator a. Log on as Administrator with the password of password. with the password of b. Open Explorer, and then on the Tools menu click Folder Options. password and configure c. In the Folder Options dialog box, on the View tab, select the Show Microsoft® Windows® Explorer to display encrypted or compressed NTFS files in color check box, and then compressed files and folders click OK. in another color. 2. Compress the Documents a. In the left pane, expand Local Disk (C:), right-click Documents and and Settings folder Settings, and then click Properties. hierarchy. What are the Size and Size on disk values for the Documents and Settings folder? Answers will vary. -

Softnas Deployment Guide for High- Performance SQL Storage
SoftNAS Deployment Guide for High- Performance SQL Storage Introduction SoftNAS cloud NAS systems are based on an innovative, memory-centric storage architecture that delivers unparalleled NAS performance, efficiency, and value. They incorporate a hybrid disk storage technology that tailors the usage of data disks, log solid- state cache drives (SSDs), and read cache SSDs to the data share's specific needs. Additional features include variable storage record size, data compression, and multiple connectivity options. As a Cloud NAS solution, SoftNAS cloud NAS systems provide an excellent base for Microsoft Windows Server deployments by providing iSCSI or Fibre Channel block storage for Microsoft SQL Server, and network file system (NFS) or server message block (SMB) file storage for Microsoft Windows client access. This document covers the best practices to follow when deploying Microsoft SQL Server on a SoftNAS cloud NAS system. The intended audience is storage administrators and Microsoft SQL Server database administrators. Maintaining High Availability As with any business-critical application, high availability is a crucial design criterion to be considered when deploying a Microsoft SQL Server installation. Microsoft SQL Server 2016 can be installed on local and/or shared file systems, and SoftNAS cloud NAS systems can satisfy both of these options. Local file systems (from the Microsoft Windows Server perspective) are hosted as block volumes—iSCSI and/or Fibre-Channel-connected LUNs and file systems as SMB and/or NFS volumes. High availability starts with the network connectivity supporting the storage and server interconnectivity. Any design for the storage infrastructure should avoid single points of failure. Because many white papers and publications cover storage-area networking and network-attached storage resilience, those topics are not covered in detail in this paper. -

United States Patent 19 11 Patent Number: 5,907,703 Kronenberg Et Al
USOO5907703A United States Patent 19 11 Patent Number: 5,907,703 Kronenberg et al. (45) Date of Patent: May 25, 1999 54) DEVICE DRIVER FOR ACCESSING “Compact -Notes,” “Compact,” “Expand,” “Create More COMPUTER FILES Disk Space by Using Disk Compression on NTFS Vol umes,” Microsoft Windows NT 4.0 Help file, 1996. 75 Inventors: Pierre-Michel Kronenberg, Middleton; Mark Nelson and Jean-Loup Gailly, “The Data Compres Derek T. Zahn, Madison, both of Wis. sion Book,” M & T Books, Second Edition 1996, pp. 73 Assignee: Mijenix Corporation, Boulder, Colo. 209-212. Ruediger R. Asche, “The Little Device Driver,” Microsoft Development Network Technology Group. Technical 21 Appl. No.: 08/643,454 Articles: Windows: Drivers, Microsoft Developer Network 22 Filed: May 8, 1996 Library CD, Apr. 1996. 51) Int. Cl. ............................ G06F 15/163; G06F 9/00; “Introduction to Windows 95 Device Drivers,” DDK. Win G06F 9/46 dows 95 Device Driver Kit, Microsoft Developer Network 52 U.S. Cl. .................... 395/681; 395/828; 364/222.81; Library CD, Apr. 1996. 364/955 “DOS/Win32 Installable File System Specifications' DDK. 58 Field of Search ..................................... 395/680, 682, Windows 95 Device Driver Kit, Microsoft Developer Net 395/681 work Library CD, Apr. 1996. “StuffIt SpacerSaver User's Guide,” Aladdin System, Inc., 56) References Cited Sep. 1994, pp. 19-28. U.S. PATENT DOCUMENTS Primary Examiner Lucien U. Toplu 5,414,850 5/1995 Whiting .................................. 395/682 ASSistant Examiner-Peter Stecher 5,457,681 10/1995 Gaddis et al.. 5,572,209 11/1996 Farmer et al. ............................ 341/67 Attorney, Agent, or Firm Arnold White & Durkee 5,628,010 5/1997 Ooishi et al. -

DR DOS for the Zfx86
DR DOS for the ZFx86 Cost Effective, Reliable, Rapid Deployment of Embedded Systems w DR DOS on the ZFx86 gets products to market quickly at the lowest development and ownership cost. w Thousands of compatible applications, drivers and utilities available free or at minimal cost. w Full documentation available. DR DOS 7.03 Key Features of DR DOS Online Manual - DRDOS is supplied with a complete The ideal embedded DOS system, online manual that contains detailed information about all designed for out-of-the-box of the features of the operating system including the basic implementation into ROM or Flash commands, and the advanced utilities. It also has online ROM with tools and associated help available for all its commands. documents available in the DRDOS Memory Management - Memory management features OEM Documentation Kit. include a set of device drivers and commands that enable w 100% MS-DOS 6.22 compatible.. you to manage memory efficiently and make as much memory as possible available to your applications. w Comprehensive DOS utility set DOS Protected Mode Services - DOS Protected Mode w Multitasking, with API for developers Services (DPMS) interface allows specially-implemented w DPMS memory manager in addition to DPMI device drivers and TSRs to operate in extended memory. w Stacker disk compression This makes more memory within the first megabyte w NWCACHE - disk caching program available to applications and other conventionally-written drivers and TSRs. Both Stacker* (the disk compression w EMM386 memory manager program), and NWCACHE (the disk cache) use DPMS. w DOS Protected Mode Services (DPMS) Disk Compression - The disk compression component w Multitasking enables you to store more information by compressing the w DR-DOS provides a full multitasking environment data. -

Ms-Dos / Pc-Dos Ms-Dos / Pc-Dos Ms-Dos / Pc-Dos Ms
MS-DOS / PC-DOS CSC414 Forensic Overview: Computer Microsoft Disk Operating System System MS-DOS - PC-DOS was IBM's version for its PC Fundamentals and Programs usually self-contained - Programs were segregated Windows 3.11 - Program files in a single directory - Copy program directory to another system and run it Digital Forensics Center Boot Disks only need three files Department of Computer Science and Statics THINK BIG WE DO - command.com U R I - config.sys http://www.forensics.cs.uri.edu - io.sys MS-DOS / PC-DOS MS-DOS / PC-DOS Single user system File names limited to 8 - Only one program could run at a time characters with 3 character - Terminate and stay resident (TSR) extension programs were an exception - No strong association between file - Utilities, viruses, key-loggers extension and type Simple Operating System - Users could use extension for Environment filename or initials - No shared device drivers - Could not search for .doc for *all* - Device drivers integrated in to programs documents - No shared .dll files (Dynamically Some common applications Linked Library) - No Windows registry - Lotus 1-2-3, Microsoft Multiplan - Each program used a .ini or .cfg file - Word Perfect, Microsoft Word MS-DOS / PC-DOS Windows 3.11 Digital Forensics didn't exist Provided a GUI interface to DOS - No special forensics tools - Not it's own operating system - Had to relay on system tools and - GUI replaces command line interface programs Windows 3.11 - Icons were short-cuts to programs - UNDELETE, UNFORMAT - Files represented as icons or -

Acronis Os Selector As a Boot Manager
User's Guide OS Selector 8.0 Compute with confidence www.acronis.com Copyright © SWsoft, 2000-2002. All rights reserved. Linux is a registered trademark of Linus Torvalds. OS/2 is a registered trademarks of IBM Corporation. UNIX is a registered trademarks of The Open Group. Windows and MS-DOS are registered trademarks of Microsoft Corporation. All other trademarks and copyrights referred to are the property of their respective owners. Distribution of substantively modified versions of this document is prohibited without the explicit permission of the copyright holder. Distribution of the work or derivative work in any standard (paper) book form for commercial purposes is prohibited unless prior permission is obtained from the copyright holder. DOCUMENTATION IS PROVIDED «AS IS» AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. END-USER LICENSE AGREEMENT BY ACCEPTING, YOU (ORIGINAL PURCHASER) INDICATE YOUR ACCEPTANCE OF THESE TERMS. IF YOU DO NOT WISH TO ACCEPT THE PRODUCT UNDER THESE TERMS YOU MAY CHOOSE NOT TO ACCEPT BY SELECTING "I decline..." AND NOT INSTALLING THE SOFTWARE. The OS Selector (the Software) is copyright © 2000-2002 by SWsoft. All rights are reserved. The ORIGINAL PURCHASER is granted a LICENSE to use the software only, subject to the following restrictions and limitations. 1. The license is to the original purchaser only, and is not transferable without prior written Permission from SWsoft. 2. The Original Purchaser may use the Software on a single computer owned or leased by the Original Purchaser. -

Archiving.Pdf
Archiving Zip. Compression. Stuff like that. Written by Dan Gookin Published by Quantum Particle Bottling Co., Coeur d’Alene, ID, 83814 USA Copyright ©2008 by Quantum Particle Bottling Co., Inc. All Rights Reserved. This work cannot be reproduced or distributed without written permission of the copyright holder. Various copyrights and trademarks may or may not appear in this text. It is assumed that the trademark or copyright is owned by whoever owns it, and the use of that material here is in no way considered an infringement or abuse of the copyright or trademark. Further, there is. Oh, wait. Never mind. I’m just making all this up anyway. I’m not a lawyer. I hate lawyers. For additional information on this or other publications from Quantum Particle Bottling Co., please visit http://www. wambooli.com/ Second Edition December, 2008 Table of Contents Archiving .........................................................................................................2 What the Heck is Archiving? ............................................................................4 Historical Nonsense About Compressed Folders and ZIP Files ..........................5 The Bad Old Modem Days .............................................................................6 Packing Multiple Files Into a Single Library ..................................................6 Better than Library Files, Compressed Archives ............................................7 Enter the ARC file format ..............................................................................8 -
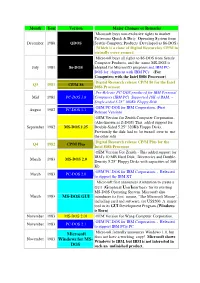
Microsoft Windows for MS
Month Year Version Major Changes or Remarks Microsoft buys non-exclusive rights to market Pattersons Quick & Dirty Operating System from December 1980 QDOS Seattle Computer Products (Developed as 86-DOS) (Which is a clone of Digital Researches C P/M in virtually every respect) Microsoft buys all rights to 86-DOS from Seattle Computer Products, and the name MS-DOS is July 1981 86-DOS adopted for Microsoft's purposes and IBM PC- DOS for shipment with IBM PCs (For Computers with the Intel 8086 Processor) Digital Research release CP/M 86 for the Intel Q3 1981 CP/M 86 8086 Processer Pre-Release PC-DOS produced for IBM Personal Mid 1981 PC-DOS 1.0 Computers (IBM PC) Supported 16K of RAM, ~ Single-sided 5.25" 160Kb Floppy Disk OEM PC-DOS for IBM Corporation. (First August 1982 PC-DOS 1.1 Release Version) OEM Version for Zenith Computer Corporation.. (Also known as Z-DOS) This added support for September 1982 MS-DOS 1.25 Double-Sided 5.25" 320Kb Floppy Disks. Previously the disk had to be turned over to use the other side Digital Research release CP/M Plus for the Q4 1982 CP/M Plus Intel 8086 Processer OEM Version For Zenith - This added support for IBM's 10 MB Hard Disk, Directories and Double- March 1983 MS-DOS 2.0 Density 5.25" Floppy Disks with capacities of 360 Kb OEM PC-DOS for IBM Corporation. - Released March 1983 PC-DOS 2.0 to support the IBM XT Microsoft first announces it intention to create a GUI (Graphical User Interface) for its existing MS-DOS Operating System. -

Blade of Destiny REALMS
REALMS of ARKANIA Blade of Destiny 1 Passwords Page Line Word Password Page Line Word Password 3 1 3 TRIBES 39 2 1 SPELL 3 4 1 HISTORY 39 4 6 INFORMATION 11 1 4 APPLY 39 5 2 ARCANE 11 6 5 GROUNDS 43 1 7 SOULS 11 9 1 TUNNELS 43 4 4 MISSIONS 14 3 4 UNLIKE 47 1 4 BEST 14 9 2 BUTTON 47 7 2 DIVINE 17 1 7 NEGATIVE 51 2 4 PASSAGE 17 2 1 POSITIVE 51 3 8 VESSELS 17 3 5 SEVEN 51 6 2 HARBOR 20 3 5 LUCK 60 2 6 LIFE 20 5 1 CHARACTER 60 4 1 SOMETIMES 23 1 6 VALUES 63 1 6 PARRY 23 3 8 MISSILE 63 2 2 MOMENTUM 23 7 1 EVENLY 63 7 9 MONSTER 27 1 6 HECTIC 76 1 3 RITUALS 27 6 2 POINTS 76 3 1 PERMANENT 31 2 9 RIVERS 88 1 6 REGULARE 31 5 3 CLICK 88 3 3 STRENGTH 31 7 1 SATISFACTION 88 6 1 LEVEL 35 1 1 LOCATION 94 2 3 HERBS 35 3 4 REPORTS 94 4 3 THEIR 36 1 4 SHAKERS 96 1 3 INFECTION 36 5 3 MEMBER 96 5 5 MATTER 36 9 3 CURRENT 96 9 1 SKILL 2 Table of Contents: Installation ....................................................................................................... 4 1. Before you install ...................................................................................... 4 2. Installing Realms of Arkania ...................................................................... 4 3. Starting Realms of Arkania ........................................................................ 4 4. Music and Sound Effects ........................................................................... 5 5. Main Program or Generation ..................................................................... 5 Troubleshooting .............................................................................................. 6 Adventuring Screen Summary ......................................................................... 8 The Main Screen ........................................................................................... -

71. Ralf Brown's Interrupt List
“Charm can fool you.” Ralf Brown’s Interrupt 71 List Ralf Brown is a well-known authority for maintaining both documented and undocumented BIOS interrupts, DOS interrupts, memory map and other system-oriented information. Because of him only, the world came to know so many officially undocumented interrupts and system specific information. His work is appreciated throughout the world by thousands of DOS Programmers. The entire Ralf Brown’s Interrupt List is available on CD . The complete list runs up to thousands of pages! Because of space constraint, I provide only a part of Ralf Brown’s Interrupt List. Ralf Brown’s sources are used with his special permission. Many thanks to Dr. Ralf Brown! 71.1 Notations To save spaces, RBIL (Ralf Brown’s Interrupt List) uses few notations. So we have to understand those notations before using RBIL. If it is marked "internal" or undocumented, you should check it carefully to make sure it works the same way in your version of the software. Information marked with "???" is known to be incomplete or guesswork. FLAGS The use of -> instead of = signifies that the indicated register or register pair contains a pointer to the specified item, rather than the item itself. Register pairs (such as AX:BX) indicate that the item is split across the registers, with the high-order half in the first register. CATEORIES The ninth column of the divider line preceding an entry usually contains a classification code (the entry has not been classified if that character is a dash). The codes currently in use are: A - applications, -

Configuring Disks
Mastering Microsoft® Windows® 7 Administration by William Panek and Tylor Wentworth Copyright © 2010 Wiley Publishing, Inc. Chapter 4 Configuring Disks When you install Windows 7, you designate the initial configuration for your disks. Through Windows 7’s utilities and features, you can change that configuration and perform disk-management tasks. Some of the tasks and decisions that you need to consider when you configure disks are file system configuration and disk type configuration. In this chapter, we’ll discuss how to configure these by using Disk Management. For file system configuration, we recommend that you use NTFS, although you could also format the disk drive as FAT32. You can also update a FAT32 partition to NTFS. This chapter covers the features of each file system and how to use the Convert utility to upgrade to NTFS. Another task in disk management is choosing the configuration for your physical drives. Windows 7 supports basic, dynamic, and the GUID partition table (GPT) disks. When you install Windows 7 or upgrade from Windows 7 using basic disks, the drives are configured as basic disks. Dynamic disks are supported by Windows 7, Windows Vista, Windows XP Professional, Windows 2000 (all versions), Windows Server 2003, and Windows Server 2008 and allow you to create simple volumes, spanned volumes, and striped volumes. After you decide how your disks should be configured, you implement the disk configu- rations through the Disk Management utility. This utility helps you view and manage your physical disks and volumes. In this chapter, you’ll learn how to manage both types of storage and how to upgrade from basic storage to dynamic storage.