Bluetooth Threat Taxonomy
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Nokia N81 8GB & Nokia N81 Data Sheet
Nokia N81 8GB & Nokia N81 Data Sheet Nokia Nseries Experiences Music Nokia N81 8GB: up to 8GB internal mass memory Planned Market Introduction Nokia N81: support for compatible microSD cards Q4 2007 Digital music player for high quality music playback High quality stereo speakers Category 3.5 mm stereo headphone plug (Nokia AV Connector) Multimedia Computer Bluetooth wireless technology A2DP profile (Bluetooth stereo Technical Profile audio) System: Slide Support for MP3/AAC/AAC+/eAAC+/WMA/M4A with playlists and Nokia N81 8GB (8GB variant), and equalizer Nokia N81 (microSD card variant): Easily synchronize music with a compatible version of WCDMA2100/EGSM850/900/1800/1900 MHz Microsoft’s Windows Media Player or Nokia Music Manager User Interface: S60 3rd Edition Search, browse and purchase songs online in Nokia Music Store Dimensions: 102 x 50 x 17.9 mm (L x W x H) – support for Windows Media DRM protected files Weight: 140 g (for Nokia Music Store availability, visit www.music.nokia.com) Standby time: Up to 16 days GSM, 17 days WCDMA Find and listen to podcasts on the go Talk time: Up to 4 hours GSM, 3 hours WCDMA Stereo FM radio with station directory and Visual Radio support Music playback: Up to 11.5 hours Games Display: 2.4 inch QVGA (240 x 320 pixels) with Landscape gaming with dedicated game keys up to 16.7 million colors N-Gage™ experience – expected to be available in 2H 2007 Battery: Nokia Battery (BP-6MT) inbox World-class game titles Memory: Nokia N81 8GB - up to 8GB internal mass Download and play high quality -

Manual Do Utilizador Do Nokia 5310 Xpressmusic
Manual do Utilizador do Nokia 5310 XpressMusic 9203503 Edição 1 DECLARAÇÃO DE CONFORMIDADE NOKIA CORPORATION declara que este RM-303 está conforme com os requisitos essenciais e outras disposições da Directiva 1999/5/CE. É possível obter uma cópia da Declaração de Conformidade no endereço http://www.nokia.com/phones/declaration_of_conformity/. © 2007 Nokia. Todos os direitos reservados. Nokia, Nokia Connecting People, Visual Radio e Navi são marcas comerciais ou marcas registadas da Nokia Corporation. Nokia tune é uma marca sonora da Nokia Corporation. Os nomes de outros produtos e empresas mencionados neste documento poderão ser marcas comerciais ou nomes comerciais dos respectivos proprietários. É proibido reproduzir, transferir, distribuir ou armazenar a totalidade ou parte do conteúdo deste documento, seja sob que forma for, sem a prévia autorização escrita da Nokia. US Patent No 5818437 and other pending patents. T9 text input software Copyright © 1997-2007. Tegic Communications, Inc. All rights reserved. Includes RSA BSAFE cryptographic or security protocol software from RSA Security. Java and all Java-based marks are trademarks or registered trademarks of Sun Microsystems, Inc. This product is licensed under the MPEG-4 Visual Patent Portfolio License (i) for personal and noncommercial use in connection with information which has been encoded in compliance with the MPEG-4 Visual Standard by a consumer engaged in a personal and noncommercial activity and (ii) for use in connection with MPEG-4 video provided by a licensed video provider. No license is granted or shall be implied for any other use. Additional information, including that related to promotional, internal, and commercial uses, may be obtained from MPEG LA, LLC. -

Mini Bluetooth Keyboard User’S Guide
IRXON Mini Bluetooth Keyboard User’s Guide The nicely designed Mini Bluetooth Keyboard is a palm-sized wireless keyboard consisting of 83 keys. It gives you all the advantages of a full-size standard keyboard and can connect via Bluetooth to almost any information appliance, including: PCs, Tablet PCs, Laptops, PDAs, Smartphones and Series 60 mobilephones, with the use of appropriate driver. It is specially designed for people who have connected their PC to big screen TV or projector, the highly compact keyboard makes it easy to access your Home Theater PC (HTPC) remotely from anywhere in the room. System requirement • Windows 2000, Windows XP, Windows Vista; Mac OS X 10.3 or higher, either with a built-in Bluetooth component, or via an external Bluetooth adapter. • Series 60 phones: - S60 3rd FP1/FP2: NOKIA: 5320XM, 5700, 6110N, 6120C, 6122C, 6210S, 6220C, 6290, 6650F, E51, E62, E63, E66, E71, E90, N76, N78, N79, N81, N82, N85, N95, N95 8GB, N96 SAMSUNG: G810, G818, 400, i408, i450, i458, i550, i558, i560, i568, i8510, L870, L878 - S60 3rd: NOKIA 3250, 5500, E50, E60, E61, E61i, E65, E70, N71, N73, N75, N77, N80, N91, N93, N93i - S60 2nd: NOKIA 3230, 6260, 6630, 6670, 6680, 6681, 7610, N70 MUSIC, N72, N90 • Windows Mobile 5.0 and higher smartphone and PocketPC that support Bluetooth wireless technology Quick Start Guide 1, Open battery cover of the Mini keyboard by pressing the cover and sliding to the direction of arrow. 2, Insert two AAA batteries into battery compartment. Ensure that the correct polarity is observed when inserting batteries.Do not mix batteries of different types, brands, or ages. -

Nokia 3250 User's Guide
Nokia 3250 User’s Guide DECLARATION OF CONFORMITY Hereby, NOKIA CORPORATION declares that this RM-38 product is in compliance with the essential requirements and other relevant provisions of Directive 1999/5/EC. A copy of the Declaration of Conformity can be found at http://www.nokia.com/phones/declaration_of_conformity/ 0434 Copyright © 2006 Nokia. All rights reserved. Reproduction, transfer, distribution or storage of part or all of the contents in this document in any form without the prior written permission of Nokia is prohibited. Nokia, Visual Radio, Nokia Connecting People, and Pop-Port are trademarks or registered trademarks of Nokia Corporation. Other product and company names mentioned herein may be trademarks or tradenames of their respective owners. Nokia tune and Visual Radio are sound marks of Nokia Corporation. This product includes software licensed from Symbian Software Ltd. © 1998-2006. Symbian and Symbian OS are trademarks of Symbian Ltd. Includes RSA BSAFE cryptographic or security protocol software from RSA Security. Java™ and all Java-based marks are trademarks or registered trademarks of Sun Microsystems, Inc. US Patent No 5818437 and other pending patents. T9 text input software Copyright © 1997-2006. Tegic Communications, Inc. All rights reserved. Copyright © 2006 Nokia. All rights reserved. 1 This product is licensed under the MPEG-4 Visual Patent Portfolio License (i) for personal and noncommercial use in connection with information which has been encoded in compliance with the MPEG-4 Visual Standard by a consumer engaged in a personal and noncommercial activity and (ii) for use in connection with MPEG-4 video provided by a licensed video provider. -

Nokia 5310 Xpressmusic Data Sheet
Nokia 5310 XpressMusic Data Sheet Planned Market Introduction: Q4 2007 Mobile Phones Category: Xpress Technical Profile: System: Tri-band GSM 850/1800/1900 and 900/1800/1900 GPRS, EGPRS User Interface: Series 40 3rd Edition Dimensions: 103.8 mm x 44.7 mm x 9.9 mm (L x W x H) Volume: 44.8 cc Weight: 70.2 g Standby time: up to 12.5 days Inbox Color Available: Talk time: up to 5 hours Red, Blue Music playback time: up to 18 hours Display: 2.0”QVGA, up to Standard Sales Package Includes: 16.7 million colors • Nokia 5310 Xpress Music handset Battery: BL-4CT Battery, 860mAh, Li-Ion • Nokia Battery (BL-4CT) • Nokia Charger (AC-3) Music Features: • MicroUSB cable (CA-101) • Up to 3,000 songs with optional 4GB MicroSD card • Wired Stereo Headset (HS-45) • Play songs purchased from Nokia Music Store (WMDRM) • Remote Control (AD-57) • Hi-Fi audio with dedicated audio chip (DAC-33) • MicroSD card • FM Stereo Radio with RDS •User Guide • 3.5 mm connector for wide choice of Hi-Fi headphones •CD-ROM • Dedicated music keys Camera: • Music player supporting MP3, AAC, AAC+, eAAC+, M4A and WMA Resolution of images: 1600 x 1200 pixels • Bluetooth stereo audio Resolution of videos: QCIF (177 x 144 pixels) •Flight mode Image capture: JPEG (up to 65,536 colors) • Music player supporting album art Video Capture: H.263 Music Synchronization: Nokia Original Enhancements: Windows Media Player 10 and 11, Drag and Drop, Headsets: Nokia Bluetooth Stereo Headset (BH-5) Nokia PC Client (available Q4) Music: Nokia Minispeakers (MD-4) Additional Features: Connectivity: •2 megapixelcamera Bluetooth, MicroUSB, 3.5 mm AV Copyright © 2007 Nokia. -

Nokia 5310 Xpressmusic - Felhasználói Kézikönyv
Nokia 5310 XpressMusic - Felhasználói kézikönyv 9203518 1. kiadás MEGFELELŐSÉGI NYILATKOZAT A NOKIA CORPORATION kijelenti, hogy a(z) RM-303 jelű készülék mindenben megfelel az alapvető követelményeknek, valamint az 1999/5/EC irányelv egyéb vonatkozó rendelkezéseinek. A Megfelelőségi nyilatkozat egy példánya megtalálható a http:// www.nokia.com/phones/declaration_of_conformity/ címen. © 2007 Nokia. Minden jog fenntartva. A Nokia, a Nokia Connecting People, a Nokia Care, a Visual Radio és a Navi a Nokia Corporation védjegye, illetve bejegyzett védjegye. A Nokia tune a Nokia Corporation hangvédjegye. Az említett egyéb termékek és cégek neve tulajdonosuk védjegye lehet. A dokumentum vagy bármely része nem másolható, nem továbbítható, nem terjeszthető és nem tárolható a Nokia előzetes írásbeli engedélye nélkül. US Patent No 5818437 and other pending patents. T9 text input software Copyright © 1997-2007. Tegic Communications, Inc. All rights reserved. Includes RSA BSAFE cryptographic or security protocol software from RSA Security. Java and all Java-based marks are trademarks or registered trademarks of Sun Microsystems, Inc. This product is licensed under the MPEG-4 Visual Patent Portfolio License (i) for personal and noncommercial use in connection with information which has been encoded in compliance with the MPEG-4 Visual Standard by a consumer engaged in a personal and noncommercial activity and (ii) for use in connection with MPEG-4 video provided by a licensed video provider. No license is granted or shall be implied for any other use. Additional information, including that related to promotional, internal, and commercial uses, may be obtained from MPEG LA, LLC. See http:// www.mpegla.com. A terméket az MPEG-4 Visual Patent Portfolio License (i) személyes, nem üzleti célú felhasználásra engedélyezi olyan adatok tekintetében, amelyeket a vevő mint magánszemély az MPEG-4 képi szabványnak megfelelően, nem üzleti célból kódolt, valamint (ii) engedélyezett videoszolgáltató által kínált MPEG-4 formátumú videofilmekkel kapcsolatos felhasználásra. -

PRESS RELEASE Nokia Reports Fourth Quarter 2005 Net Sales Of
PRESS RELEASE 1 (24) January 26, 2006 Nokia reports fourth quarter 2005 net sales of EUR 10.3 billion, EPS of EUR 0.25 Nokia reports 2005 net sales of EUR 34.2 billion, EPS of EUR 0.83 Device market share gains in Q4 and 2005 drive 16% annual sales growth and 20% EPS growth Nokia’s Board of Directors will propose a dividend of EUR 0.37 per share for 2005 (EUR 0.33 per share for 2004) NOKIA Q4 and 2005 EUR million Q4/2005 Q4/2004 Change 2005 2004 Change (*revised) (%) (*revised) (%) Net sales 10 333 9 456 9 34 191 29 371 16 Mobile Phones 6 217 5 871 6 20 811 18 521 12 Multimedia 2 024 1 272 59 5 981 3 676 63 Enterprise Solutions 153 295 -48 861 839 3 Networks 1 951 2 031 -4 6 557 6 431 2 Operating profit 1 368 1 450 -6 4 639 4 326 7 Mobile Phones 1 060 1 107 -4 3 598 3 786 -5 Multimedia 310 168 85 836 175 Enterprise Solutions -136 -44 -258 -210 Networks 268 306 -12 855 884 -3 Common Group Expenses -134 -87 -392 -309 Operating margin (%) 13.2 15.3 13.6 14.7 Mobile Phones (%) 17.1 18.9 17.3 20.4 Multimedia (%) 15.3 13.2 14.0 4.8 Enterprise Solutions (%) -88.9 -14.9 -30.0 -25.0 Networks (%) 13.7 15.1 13.0 13.7 Financial income and expenses 78 116 -33 322 405 -20 Profit before tax and minority interests 1 453 1 556 -7 4 971 4 705 6 Net profit 1 073 1 083 -1 3 616 3 192 13 EPS, EUR Basic 0.25 0.24 4 0.83 0.69 20 Diluted 0.25 0.24 4 0.83 0.69 20 All reported Q4 and 2005 figures can be found in the tables on pages (10-13) and (19-23) SPECIAL ITEMS Fourth quarter 2005 special items - EUR 29 million charge for Enterprise Solutions restructuring -

Dension's BTA 1500
Phone Compatibility Phone HFP A2DP Phone Book Phone HFP A2DP Phone Book Connectivity iPhone ok - ok Nokia 6680 ok - - iPhone 3G ok ok Nokia 7390 ok - - LG KE 970 ok ok ok Nokia 7500 ok ok ok Motorola L6 ok - ok Nokia 8800 ok ok ok Motorola L7 ok - ok Nokia E61i ok - - Motorola V3 ok - ok Nokia E90 ok - - Motorola V3i ok - ok Nokia N Series ok - - Nokai 6233 ok - ok Samsung E250 V ok ok ok Nokia 3109 ok ok ok Samsung SGH D Series ok ok - Nokia 3230 ok - - Samsung SGH E series ok ok ok Nokia 3250 ok - - Samsung SGH F210 ok - - 2009 Nokia 3300 ok - - Samsung SGH F300 ok ok - Nokia 5310 Xpression ok ok - Samsung SGH J600 ok - - Nokia 5500 ok - - Samsung SGH P300 ok - - Nokia 6021 ok - ok Samsung SGH U600 ok ok - Nokia 6103 ok - - Samsung SGH Z400 ok ok - Nokia 6110 ok ok - Samsung SGHX820 ok - - Nokia 6151 ok ok - Siemens SX1 ok - - Nokia 6280 ok - ok Sony Ericcson K Series - ok ok BTA 1500 Nokia 6300 ok ok ok Sony Ericcson P800 ok - - Nokia 6310 ok - - Sony Ericcson W Series ok - - Nokia 6600 ok - - T-mobile MDA ok ok ok Nokia 6630 ok - - Car Compatibility Class Type Code MY HU Mercedes CL C215 2005-2006 Comand. Audio 20 Audio 50 CL C216 2006- CLS W219 2004- E W211 2003- S W220 2003-2005 S W221 2006- SL R230 2005- SLK R171 2004- A W169 2005- Comand. Audio 20 Audio 50 B W245 2005- C W203 2004-2007 CLK W209 2005- G W463 2005- M W164 2005- R V251 2006- BMW 1 Series E87 2004- i-Drive 3 Series E90/E91 2005- 5 Series E60/E61 2004- 6 Series E63/E64 2004- 7 Series E65/E66 2004- Porsche Carrera n/a 2003- PCM2, PCM2.1 Cayenne n/a 2005-2008 Audi A5 coupe 2007-2008 MMI2 - colour and basic A6 saloon/estate 2004-2008 Q7 4x4 2004-2008 *For details of all compatibility please visit www.dension.com for more information. -

Integrating Usability Models Into Pervasive Application Development
Integrating Usability Models into Pervasive Application Development Paul Holleis München 2008 Integrating Usability Models into Pervasive Application Development Paul Holleis Dissertation an der Fakultät für Mathematik, Informatik und Statistik der Ludwig-Maximilians-Universität München vorgelegt von Paul Holleis aus Bad Reichenhall München, den 15.12.2008 Erstgutachter: Prof. Dr. Albrecht Schmidt Zweitgutachter: Prof. Dr. Heinrich Hußmann Externer Gutachter: Prof. Dr. Antonio Krüger Tag der mündlichen Prüfung: 19.01.2009 To my dad, who would have enjoyed reading this thesis. Table of Contents vii Table of Contents 1 INTRODUCTION AND STRUCTURE .......................................................................................................... 1 1.1 GOALS AND CONTRIBUTIONS .......................................................................................................................... 1 1.2 STRUCTURE ................................................................................................................................................. 2 2 DEVELOPING PERVASIVE APPLICATIONS ................................................................................................ 3 2.1 PERVASIVE COMPUTING ................................................................................................................................. 3 2.1.1 Brief History and Overview .............................................................................................................. 3 2.1.2 Applications and Related Terms ..................................................................................................... -

Manual Do Utilizador Do Nokia 3250
Manual do Utilizador do Nokia 3250 9244348 2ª Edição DECLARAÇÃO DE CONFORMIDADE NOKIA CORPORATION, declara que este RM-38 está conforme com os requisitos essenciais e outras disposições da Directiva 1999/5/CE. É possível obter uma cópia da Declaração de Conformidade no endereço http://www.nokia.com/phones/declaration_of_conformity/. 0434 O símbolo do contentor de lixo barrado com uma cruz significa que, no interior da União Europeia, o produto deve ser objecto de recolha selectiva no final do respectivo ciclo de vida. Esta norma aplica-se ao seu dispositivo, assim como a quaisquer acessórios marcados com este símbolo. Não deposite estes produtos nos contentores municipais, como se se tratasse de resíduos urbanos indiferenciados. Para obter mais informações, consulte a Declaração Ecológica ou informações específicas para cada país, em www.nokia.com. Copyright © 2006 Nokia. Todos os direitos reservados. É proibido reproduzir, transferir, distribuir ou armazenar a totalidade ou parte do conteúdo deste documento, seja sob que forma for, sem a prévia autorização escrita da Nokia. Nokia, Visual Radio, Nokia Connecting People e Pop-Port são marcas comerciais ou marcas registadas da Nokia Corporation. Os nomes de outros produtos e empresas mencionados neste documento poderão ser marcas comerciais ou nomes comerciais dos respectivos proprietários. Nokia tune e Visual Radio são marcas sonoras da Nokia Corporation. This product includes software licensed from Symbian Software Ltd. © 1998-2006. Symbian and Symbian OS are trademarks of Symbian Ltd. Includes RSA BSAFE cryptographic or security protocol software from RSA Security. Java™ and all Java-based marks are trademarks or registered trademarks of Sun Microsystems, Inc. -

7. 3G/3.5G Mobile Phone/PDA Support
7. 3G/3.5G Mobile Phone/PDA Support To streaming from 3/3.5G mobile phone or PDA, you have to open the mobile port of DVR, the default setting is 7050, which may be changed, please refer to 5.5.5 PPPoE/DDNS(Net- Second Page] or IE 6.5 Device Parameters Settings ServerÆNetwork setting, video system For limited upload bandwidth of internet that DVRs connect, or limited streaming capability of some mobile phone/PDA, you have to adjust bandwidth of DVR to internet, please refer to 5.3.8 Dual Streaming for Network(Record- Advanced Setting) or 6.5 Device Parameters Settings - ChannelÆ Camera setting, Sub Bitstream, Subcode (from IE) for more details You may find the Windows Mobile 5.0/6.0/6.1 PDA(amplayersetup.CAB) and Symbian S60 3rd (P2P_S60_3rd_0113.sis) and S60 5th(P2P_S60_5Th_20090112.sis) softwares from the CD inside the DVR package or visit your DVR website to download by IE – http://xxx.xxxx.xxxx/download.html Note: User’s mobile phone must apply internet connection service at first, such as 3G or 3.5G service. Please contact mobile company for detail. 7. 1 Windows Mobile PDA Open accessory CD and find the “amplayersetup.CAB” for the surveillance software. Please refer to PDA user manual, copy *.cab into windows mobile pda Double click on *.cab can start install software into PDA. After install completed, user can find QQEYE in the application list. Execute QQEYE program and click to setup IP address of remote DVR. - 60 - Input user name 〖Admin〗and password. IP address of DVR and port:7050 for streaming data. -
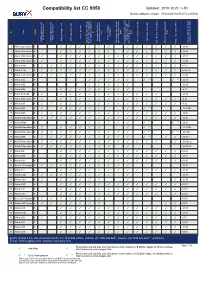
BURY Compatibility List Generator
Compatibility list CC 9050 Updated: 2010-12-21 / v.51 Device software version: APP:04.03.02/ DSW:01.02.0f/ BTS:01.47.12 (CC 9051M V06b) on No key keys Card Type tags) Profile activation service provider Phone s REDIAL A2DP from phone A2DP from device / private mode with Battery charge level Activation Bluetooth GSM-signal strength Call lists Missed calls A2DP supported start A2DP supported start connection with device Call lists Received calls Bluetooth connection to used to test/ Comments after ignition is switched Access to mobile phone Phone book entries SIM voice-dial function (voice the last connected phone Call lists Dialled numbers Phone book entries Bluetooth device / phones Possibility to switch car kit Version of phone software 1 Nokia 2323 classic hf ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ v 06.46 2 Nokia 2330 classic hf ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ v 06.46 3 Nokia 2700 classic hf ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ v 07.15 4 Nokia 2730 classic hf ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ v 10.40 5 Nokia 3109c hf ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ v07.21 6 Nokia 3110c hf ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ vp sk4.80 7 Nokia 3120 classic hf ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ v 10.00 8 Nokia 3230 hf ✓ ✓ ✓ ✓ ✓ ✓ ** ✓ ** v 04.14 9 Nokia 3250 hf ✓ ✓ ✓ ✓ ✓ v 03.24 10 Nokia 3650 hf ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ v 4.17 11 Nokia 3710 fold hf ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ v 03.80 12 Nokia 3720 classic hf ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ v 3.92 13 Nokia 5200 hf ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ v 3.92 14 Nokia 5230 hf ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ** v 12.0.089 15 Nokia 5300 hf ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ ✓ v 03.92 16 Nokia 5310 XpressMusic